CIS Control 20: Penetration Tests and Red Team Exercises
As a final testament to a good security program, the CIS Control 20 recommends the organization test all the security controls. These exercises are very beneficial to training and security awareness. Many times well intended measures can be exploited. For example, a really strict password policy can result in users taping passwords to their keyboard. A great technical control, thwarted by a forgetful user and an observant adversary. Many times developers find protocols they find useful, and never realize there is an inherent security flaw, for example FTP and Telnet, are great tools. But in both cases, all credential exchanges are in clear text, allowing passwords and other information to be captured easily. Many chat programs use a form of HTTP and not HTTPS, again data is exchanged in the clear. With wireless technologies, many times with a simple wireless receiver, anyone can monitor the full exchanges of information. Penetration tests and red team exercises help to bring this information to the forefront of the security conversation.
CIS Control 20 states:
“Test the overall strength of an organization’s defense (the technology, the processes, and the people) by simulating the objectives and actions of an attacker.
Why Is This CIS Control Critical?
Attackers often exploit the gap between good defensive designs and intentions and implementation or maintenance. Examples include: the time window between announcement of a vulnerability, the availability of a vendor patch, and actual installation on every machine. Other examples include: well-intentioned policies that have no enforcement mechanism (especially those intended to restrict risky human actions); failure to apply good configurations to machines that come on and off of the network; and failure to understand the interaction among multiple defensive tools, or with normal system operations that have security implications.
A successful defensive posture requires a comprehensive program of effective policies and governance, strong technical defenses, and appropriate action by people. In a complex environment where technology is constantly evolving, and new attacker tradecraft appears regularly, organizations should periodically test their defenses to identify gaps and to assess their readiness by conducting penetration testing.”
Tenable Security Center and Nessus are often good tools to use to aid in pre-assessment activities. Many red team members use Nessus as a network discovery tool. By using tools that do similar tasks conducted by the adversaries, organizations are able to better detect and remediate the risk before the system is breached or compromised.
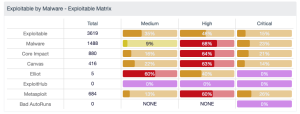
Referring back to the Basic Controls (CIS Control 1 - 6) these are the initial steps the red team will perform. The first step is to scan the network and identify hardware, then software. Now the red team has targets, they will then begin to enumerate vulnerabilities and test for baseline configurations, and so on. After a good list of vulnerabilities are collected, the fundamental controls will be tested. The vulnerabilities discovered by Tenable Security Center have an attribute called, exploitable. With this attribute the organization can easily see the low hanging fruit and plan to take the required mitigation efforts.
Shown in the “Exploitable by Malware - Exploitable Matrix” the organization can quickly see which popular attack tools their environment is most exploitable by. In these cases there are well known and widely used tools to exploit vulnerable systems. The red team will often use these tools to illustrate the likelihood a system could be compromised. Many attackers may use the same tools, or develop their own, but in either case if the organization has several exploitable systems, then there is a lot of work needed before a penetration test will be valuable. Once a majority of these vulnerabilities are mitigated, then the red team should be engaged.
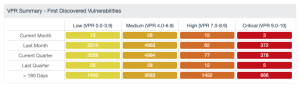
While Exploitable is a great attribute to use, in some cases an exploitable attribute may require a perfect storm condition. As this is the case, Tenable created the Vulnerability Priority Rating (VPR). VPR is the output of Tenable Predictive Prioritization, and helps organizations improve their remediation efficiency and effectiveness by rating vulnerabilities based on severity level, technical impact, and threat. The technical impact measures the impact on confidentiality, integrity and availability following exploitation of a vulnerability and is equivalent to the CVSSv3 impact subscore. The threat component reflects both recent and potential future threat activity against a vulnerability. Factors that influence VPR are public proof-of-concept (PoC) research, reports of exploitation on social media, and many others. These are primary factors used by the organization to prioritize mitigation efforts before the red team arrives, and these are the vulnerabilities that will have attempts at exploitation first. Tenable Security Center is a good source to help prepare plans to mitigate risk and complete the final control in the CIS CAS.