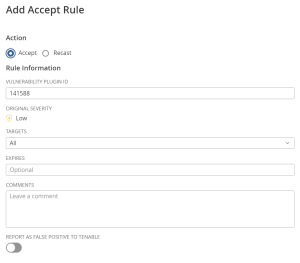
Create an Accept Rule for a Plugin
Required User Role: Administrator
To create an accept rule:
- View the Recast/Accept Rules page.
- In the upper-right corner, click the
 Add Rule button.
Add Rule button.The Add Rule plane appears.
- In the Action section, select Accept.
- In the Vulnerability box, type the ID of the plugin that you want to recast. For example, 51192.
Note: If the plugin ID corresponds to a Tenable Nessus plugin, the Original Severity indicator changes to match the default severity of the vulnerability. The Original Severity indicator does not change if another type of plugin is used.
-
In the Targets drop-down box, do one of the following:
- To target all assets, select All. This is the default target.
- To target a custom set of assets:
- Select Custom.
A Target Hosts box appears.
- In the Target Hosts box, type one or more targets for the rule. You can type a comma-delimited list that includes any combination of IP addresses, IP ranges, CIDR, and hostnames.
Caution: You can only specify 1000 comma-separated custom entries. If you want to target a larger number of custom entries, create multiple rules.
- Select Custom.
- (Optional) In the Expires box, set an expiration date for the rule. This action is only necessary if you want the rule to expire. By default, the rule applies indefinitely.
- (Optional) In the Comments box, type a description of the rule. The text you type in this box is only visible if the rule is modified and has no functional effect.
- (Optional) To report the vulnerability as a false positive:
- Enable the Report as false positive toggle.
A Message To Tenable box appears.
- In the Message to Tenable box, type a description of the false positive to send to Tenable.
- Enable the Report as false positive toggle.
-
Click Save.
Tenable Vulnerability Management starts applying the rule to existing vulnerabilities. This process may take some time, depending on the system load and the number of matching vulnerabilities. The affected vulnerability is hidden on your workbench.
Note: To view vulnerabilities hidden from your workbench, use the Recast & Accept advanced filter.