Prioritising Risk
One of the hardest tasks to accomplish is proper risk prioritisation and communication of risks and vulnerabilities. In addition to the Articles previously listed, the following DORA Articles are related to risk prioritisation efforts including risk based vulnerability management:
-
Article 8.3, Financial entities, other than microenterprises, shall perform a risk assessment upon each major change in the network and information system infrastructure
-
Article 9.4(b), Financial entities shall follow a risk-based approach, establish a sound network and infrastructure management structure using appropriate techniques, methods and protocols
-
Article 16.1 (d), allow sources of ICT risk and anomalies in the network and information systems to be promptly identified and detected
In this section the following Tenable products will be highlighted:
-
Lumin Exposure View
-
Tenable Security Center
-
Tenable Vulnerability Management
Lumin Exposure View
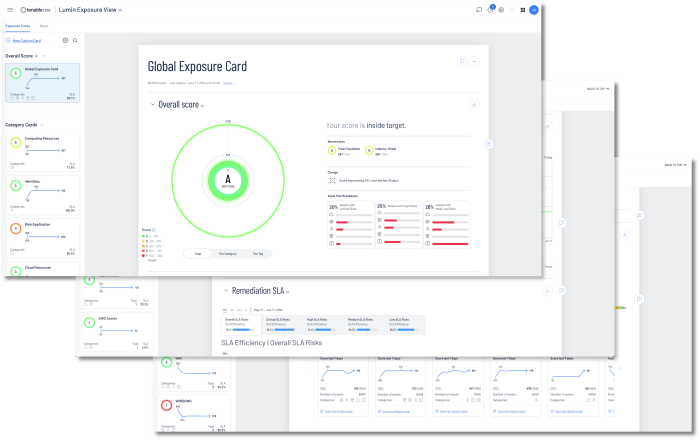
Tenable Lumin Exposure View provides at-a-glance insight into all weaknesses and exposures. Tenable Lumin Exposure View combines data sources from all Tenable solutions, including IT assets, identity systems, cloud resources, web applications, and your OT infrastructure. Lumin Exposure View provides the exposure cards, which allows easy identification of problem areas so resources can be applied properly where needed. An exposure card represents incoming data from configured tags and data sources. This data is aggregated and normalised to provide a visual representation of your Cyber Exposure Score (CES) and other metrics. Note: Exposure cards can be customised or Tenable provided cards can be used.
The CES is presented under the letter grade, in the form of a number such as 167/1000. The CES score is a value from 0-1000, with higher values indicating higher exposure and higher risk.
For more in-depth information on prioritising risk with Lumin Exposure view, refer to the following Risk Assessment section of the NIS 2 Cyber Exposure Study. Also, you can follow this link for more information on Lumin Exposure View.
Risk Based Vulnerability Management
Risk-Based Vulnerability Management (RBVM) is a process that reduces vulnerabilities across the attack surface by prioritising remediation based on the risks they pose to the organisation. Unlike legacy vulnerability management, risk-based vulnerability management goes beyond discovering vulnerabilities, by helping organisations understand vulnerability risks, by introducing threat context and insight into potential business impact.
RBVM eliminates guesswork, by taking a risk-based approach to vulnerability management, security teams can focus on the vulnerabilities and assets that matter most and address the organization’s true business risk instead of wasting valuable time on vulnerabilities attackers may not likely exploit. If you’re new to risk-based vulnerability management, check out this comparison guide. The guide breaks down the differences between legacy vulnerability management and risk-based vulnerability management with insight into how a risk-approach can make your organisation's vulnerability management program more efficient and effective. In addition to the Articles previously listed, the following DORA Articles are related to vulnerability management efforts:
-
Article 8.2, Financial entities shall, on a continuous basis, identify all sources of ICT risk
-
Article 8.3,Financial entities shall identify all information assets and ICT assets, including those on remote sites, network resources and hardware equipment
-
Article 9.1, Financial entities shall continuously monitor and control the security and functioning of ICT systems and tools
-
Article 10.1, Financial entities shall have in place mechanisms to promptly detect anomalous activities
-
Article 16.1 (b), continuously monitor the security and functioning of all ICT systems
In this section the following Tenable products will be highlighted:
-
Tenable Security Center
-
Tenable Vulnerability Management
With the principles of Cyber Exposure Management in mind, dashboards, such as the InfoSec Team - One Stop Shop Comprehensive Attack Surface dashboard for Tenable Security Center helps the organisation team maintain a high level of awareness and vigilance. The filters and components are tailored to guide teams in detecting, predicting, and acting to reduce risk across their entire attack surface. Information security teams are empowered to analyse findings, remediate identified risks, track progress, and measure success against the organisation's charter and SLAs.
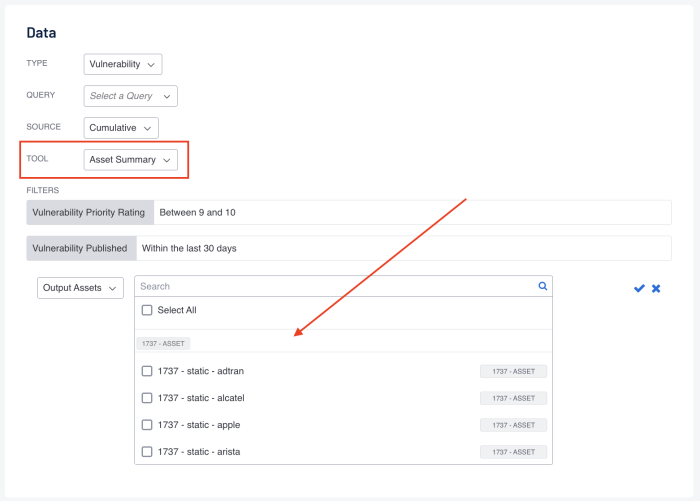
Organizations often have teams that focus on the detailed information relevant to the teams' assets; or operational focus areas, such as Windows, Linux, databases, or network infrastructure. However, organisations with teams that focus on a specific group of assets benefit from using custom asset lists. Information security teams can visualise findings against assets that are "owned by" or "assigned to" specific teams within the organisation using this method. Additionally, an Output Assets filter can be set to provide greater insight into where additional resources need to be allocated to mitigate vulnerabilities.
The Output Assets filter is only available when using the Asset Summary Tool. When this tool is selected, you have the option to refine the filters to include specific Asset information.
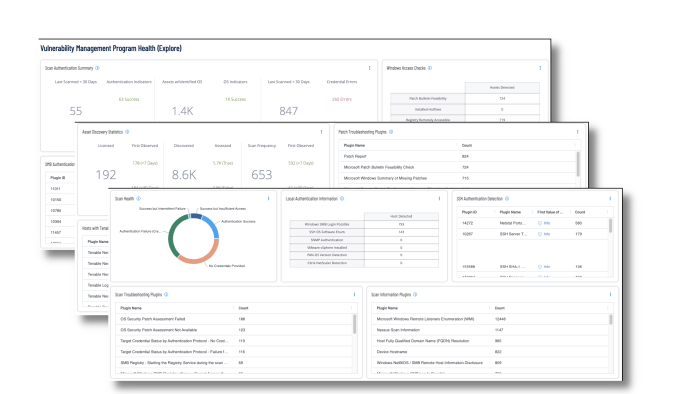
For Tenable Vulnerability Management, dashboards such as the Vulnerability Management Program Health dashboard shown in the following image, helps security operations teams ensure their scanning program is appropriately maintained for an evolving operational technology landscape aligned with business strategy.
There are many factors that can adversely affect the scope and accuracy of scan data, such as failed credentials, network problems, or licence limitations. This dashboard provides security analysts comprehensive information to monitor the health of their scanning program.
Analysts can drill into the summary information displayed in the dashboard to troubleshoot upstream scanning problems that can adversely impact downstream reporting to stakeholders.
For more information, see the Vulnerability Management Cyber Exposure Study.