Defending Against Ransomware (ACT) Dashboard Widgets
| Widget Description | Widget Image |
|---|---|
|
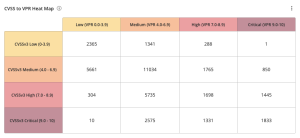
The CVSS to VPR Heat Map widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, provides a correlation between CVSSv3 scores and VPR scores for the vulnerabilities present in the organization. Each cell consists of a cross-mapping of CVSS & VPR scores. The widget uses a heat map approach, with the upper left corner containing the vulnerabilities with the lowest risk. Moving lower and to the right in the matrix, the colors change from yellow to red as the risk levels increase. Tenable recommends mitigating risks shown in the lower right cells and working towards the upper left cells, since the lower right cells represent the highest risk. |
|
|
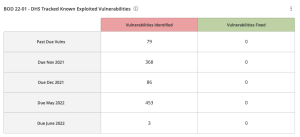
The BOD 22-01 - DHS Tracked Known Exploited Vulnerabilities widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and the Tenable Vulnerability Management widget library, displays vulnerabilities derived from the CISA Known Exploited Vulnerabilities Catalog. The widget uses the CVE filter to exactly match the Active and Fixed vulnerabilities that match the CVEs included in the CISA Known Exploited Vulnerabilities Catalog. For more information, please see the full Binding Operational Directive 22-01. |
|
|
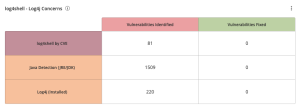
The log4shell - Log4j Concerns widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and the Tenable Vulnerability Management widget library, uses the Vulnerability State filter with the CVE filter to display Active and Fixed Log4j and Java vulnerabilities. This matrix alerts organizations to potential concerns regarding the Log4j vulnerability. Displayed are the vulnerabilities that are directly associated with the log4shell CVEs: CVE-2021-44228, CVE-2021-44832, CVE-2021-45046, CVE-2021-4104, and CVE-2021-45105, and Log4j installations. Since installing Java v8 is also a requirement to address this exploit, a row of vulnerabilities that are associated with Java, JRE, and JDK is displayed. |
|
|
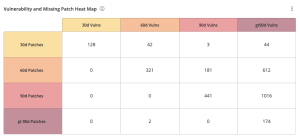
The Vulnerability and Missing Patch Heat Map widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, uses the Vulnerability Published date filter cross mapped with the Patch Published date filter to show the organization's current vulnerability state. The Patch Published dates indicate when a vendor published a patch for the vulnerability, while the Vulnerability Published date is the date when the vulnerability was first published (for example, the date the CVE was published to NVD). Each cell consists of a cross-mapping of Patch Publication and Vulnerability Publication. The widget uses a heat map approach, with the upper left corner containing the vulnerabilities and patches that have been published in the last 30 days. Moving lower and to the right in the matrix, the colors change from yellow to red as the risk levels increase. Tenable recommends mitigating risks shown in the lower right cells and working towards the upper left cells, since the lower right cells represent missing patches associated with vulnerabilities that have been present within the organization for a longer time period. Vulnerabilities displayed in this table are based on the plugins in the Local Security Checks plugin families for each Operating System. Tenable provides a comprehensive collection of plugins for a large variety of operating systems to check for security issues, which are enumerated on the Tenable Plugins Page. |
|
|
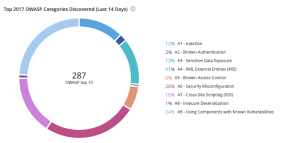
The Top 2017 OWASP Categories Discovered in the Last 14 days widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays the percentages of active Web Application vulnerabilities from Tenable Web App Scanning by OWASP category. |
|
|
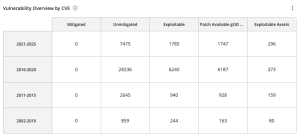
The Vulnerability Overview by CVE Widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays a count of the following:
|
|
|
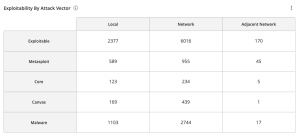
The Exploitability By Attack Vector widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays exploitable vulnerabilities by the CVSS Exploitability Metric Vectors: AV:N (Network), AV:A (Adjacent Network), and AV:L (Local). There is a row for each exploit framework. The CVSS metric vector specifies if the vulnerability is locally or remotely exploitable. The description for “Attack Vector” can be found in the First.org CVSS Specification Document. |
|
|
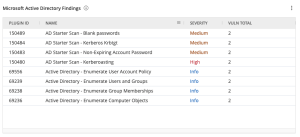
The Microsoft Active Directory Findings widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays Active Directory vulnerabilities using the CPE filter forcpe:/a:microsoft:active_directory. |
|
|
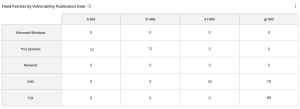
The Fixed Patches by Vulnerability Publication Date widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays counts of fixed vulnerabilities grouped by the patch publication date. This matrix assists organizations with mapping mitigation progress and presents data to determine whether organizational SLAs are being met. Each cell contains a count of fixed vulnerabilities grouped by Microsoft Windows systems, *nix systems, Network devices, and vulnerabilities specified in the DHS BOD 22-01 and Tenable's 2021 Threat Landscape Retrospective with a patches published 0-30, 31-60, 61-90, and more than 90 days ago. |
|