Prioritize Using Prediction
Not everything can or should be patched. Take advantage of real-time threat intelligence to understand the latest attack paths used by ransomware groups to guide the organization’s remediation strategy. Vulnerabilities targeted by ransomware exploits tend to cluster around specific types of weaknesses and asset categories. Savvy defenders can predict which vulnerabilities will likely be exploited in ransomware attacks and proactively address the risk before there is a business impacting event.
Predicting Likelihood of Vulnerability Exploitation
A Vulnerability Priority Rating (VPR) is expressed as a number from 0.1 to 10, with higher values corresponding to a higher likelihood of the vulnerability leading to a compromise of the asset. Based on these values, vulnerabilities can be rated in terms of impact to the asset, including Low (0.1-3.9), Medium (4.0-6.9), High (7.0-8.9), and Critical (9.0-10.0).
Note: The VPR is a machine-generated score based on the vulnerability alone, without regard to the environment where the vulnerability is found. Therefore, the VPR is not subject to user-specific considerations and cannot be changed or customized.
VPR is the output of the Predictive Prioritization process and is continually updated to accommodate the evolving threat landscape. Following the initial scan of an asset on the network, Tenable computes an initial VPR using a machine-learning algorithm that analyzes more than 150 different aspects of each vulnerability to determine the level of risk. The value is calculated within 24 hours of a vulnerability’s initial disclosure in the National Vulnerability Database (NVD), providing security teams with early indicators of risk often days, weeks, and sometimes months before a CVSS value is assigned.
VPR is designed specifically for threat prioritization, unlike CVSS, which was designed to provide a static measure of technical severity. Relying on CVSS alone to prioritize vulnerabilities slows the assimilation of emerging threats, giving potential attackers an advantageous head start.
Key drivers that are used to calculate VPR include, but are not limited to, the following:
| Key Driver | Description |
|---|---|
| Vulnerability Age | The number of days since the NVD published the vulnerability. |
| CVSSv3 Impact Score | The NVD-provided CVSSv3 impact score for the vulnerability. If the NVD did not provide a score, Tenable Vulnerability Management displays a Tenable-predicted score using the text from the security advisory as an input. |
| Exploit Code Maturity | The relative maturity of a possible exploit for the vulnerability based on the existence, sophistication, and prevalence of an exploit in various databases and frameworks, such as ReversingLabs, Exploit DB, Metasploit, Canvas, and more. The possible values (High, Functional, PoC, or Unproven) parallel the CVSS Exploit Code Maturity categories. |
| Product Coverage | The relative number of unique products affected by the vulnerability in the wild or in the current environment: Low, Medium, High, or Very High. |
| Threat Sources | A list of all sources, such as social media channels and the dark web, where threat events related to this vulnerability have occurred. If the system did not observe a related threat event in the past 28 days, the system displays No recorded events. |
| Threat Intensity | The relative intensity based on the number and frequency of recently observed threat events related to this vulnerability: Very Low, Low, Medium, High, or Very High. |
| Threat Recency | The number of days (0-730) since a threat event occurred for the vulnerability. |
VPR integrates a broad range of dynamic risk factors to elevate the few vulnerabilities that require immediate attention, based on the level of risk for each vulnerability. Vulnerability overload has long been a pitfall of CVSS-based prioritization, which rates more than half of the vulnerabilities as “High” or “Critical." VPR, by comparison, rates very few vulnerabilities as “High” or “Critical," providing a more actionable basis for remediation planning. In fact, VPR is 18 times more efficient than CVSS in spotting vulnerabilities that are exploited by attackers. Tenable recommends resolving vulnerabilities with the highest VPR score first.
| VPR Severity | VPR Score |
|---|---|
|
Critical |
9.0 to 10.0 |
|
High |
7.0 to 8.9 |
|
Medium |
4.0 to 6.9 |
| Low |
0.1 to 3.9 |
Note: Vulnerabilities without CVEs in the NVD, such as many vulnerabilities with the Info severity, do not receive a VPR. Tenable recommends remediating these vulnerabilities according to their CVSS-based severity.
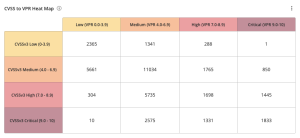
The CVSS to VPR Heat Map widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, provides a correlation between CVSSv3 scores and VPR scores for the vulnerabilities present in the organization. Each cell consists of a cross-mapping of CVSS & VPR scores. The widget uses a heat map approach, with the upper left corner containing the vulnerabilities with the lowest risk. Moving lower and to the right in the matrix, the colors change from yellow to red as the risk levels increase. Tenable recommends mitigating risks shown in the lower right cells and working towards the upper left cells, since the lower right cells represent the highest risk.
VPR is a key filter to prioritize the areas of the most significant concerns. Effective vulnerability remediation becomes easier as vulnerabilities that will cause the most significant impact float to the top. VPR ratings can change over time, as threat intelligence information changes, which enables teams to focus on what is important right now. CVSS Vector filters are also used to prioritize returned results. Specific CVSS base metric options capture the characteristics of how a vulnerability is accessed and additional conditions that must exist to exploit the vulnerability. The following CVSS Vectors are used:
-
Access Complexity (AC) of Low (L) means that the attack can be performed manually and requires little skill or information gathering to accomplish.
-
Access Vector (AV) of Network (N) means that a vulnerability exploitable with Network Access is bound to the network stack and the attacker does not require local network or local access. This type of attack is commonly referred to as "remotely exploitable."
-
Authentication (Au) of None (N) means Authentication is not required to exploit the vulnerability.
Combined with additional filters which focus on severity ratings and whether a vulnerability is exploitable or not, organizations become better equipped to see, predict, and take action to reduce risk across their entire attack surface. In addition to the above filters, the Vulnerability Published filter is used to filter vulnerability information related to vulnerabilities that have been identified as published in the last 30 days.
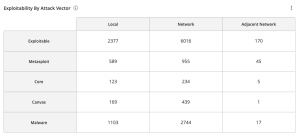
The Exploitability By Attack Vector widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays exploitable vulnerabilities by the CVSS Exploitability Metric Vectors: AV:N (Network), AV:A (Adjacent Network), and AV:L (Local). There is a row for each exploit framework. The CVSS metric vector specifies if the vulnerability is locally or remotely exploitable. The description for “Attack Vector” can be found in the First.org CVSS Specification Document.
Vulnerabilities that can be exploited remotely are a greater risk, since there is a global threat vector. Vulnerabilities that can be exploited locally require local access to the system through another mechanism, such as actions by an authorized user or access through a remote-execution vulnerability. Threat vectors are designated as Network (AV:N), Adjacent (AV:A), and Local (AV:L), as described below:
- Network (AV:N) Vulnerabilities that can be exploited with Network access are those where the vulnerable component is bound to the network stack and the attacker's path is through OSI layer 3 (the network layer). Such vulnerabilities are termed "remotely exploitable" and can exploited from one or more network hops away (i.e., across layer 3 boundaries from routers). An example of a network attack is an attacker causing a denial of service (DoS) by sending a specially crafted TCP packet from the public Internet. See also CVE-2004-0230.
- Adjacent (AV:A) Vulnerabilities that can be exploited with Adjacent network access are those where the vulnerable component is bound to the network stack. However, the attack is limited to the same shared physical network (such as Bluetooth, IEEE 802.11) or logical network (such as local IP subnet) and cannot be performed across an OSI layer 3 boundary, such as a router. An example of an Adjacent attack is an ARP (IPv4) or neighbor discovery (IPv6) flood leading to a denial of service on the local LAN segment. See also CVE-2013-6014.
- Local (AV:L) Vulnerabilities that can be exploited with Local network access are those where the vulnerable component is not bound to the network stack and the attacker’s path is through read/write/execute capabilities. The attacker may be logged in locally to exploit the vulnerability or trick a user into executing malware.