Indicators of Attack Incidents
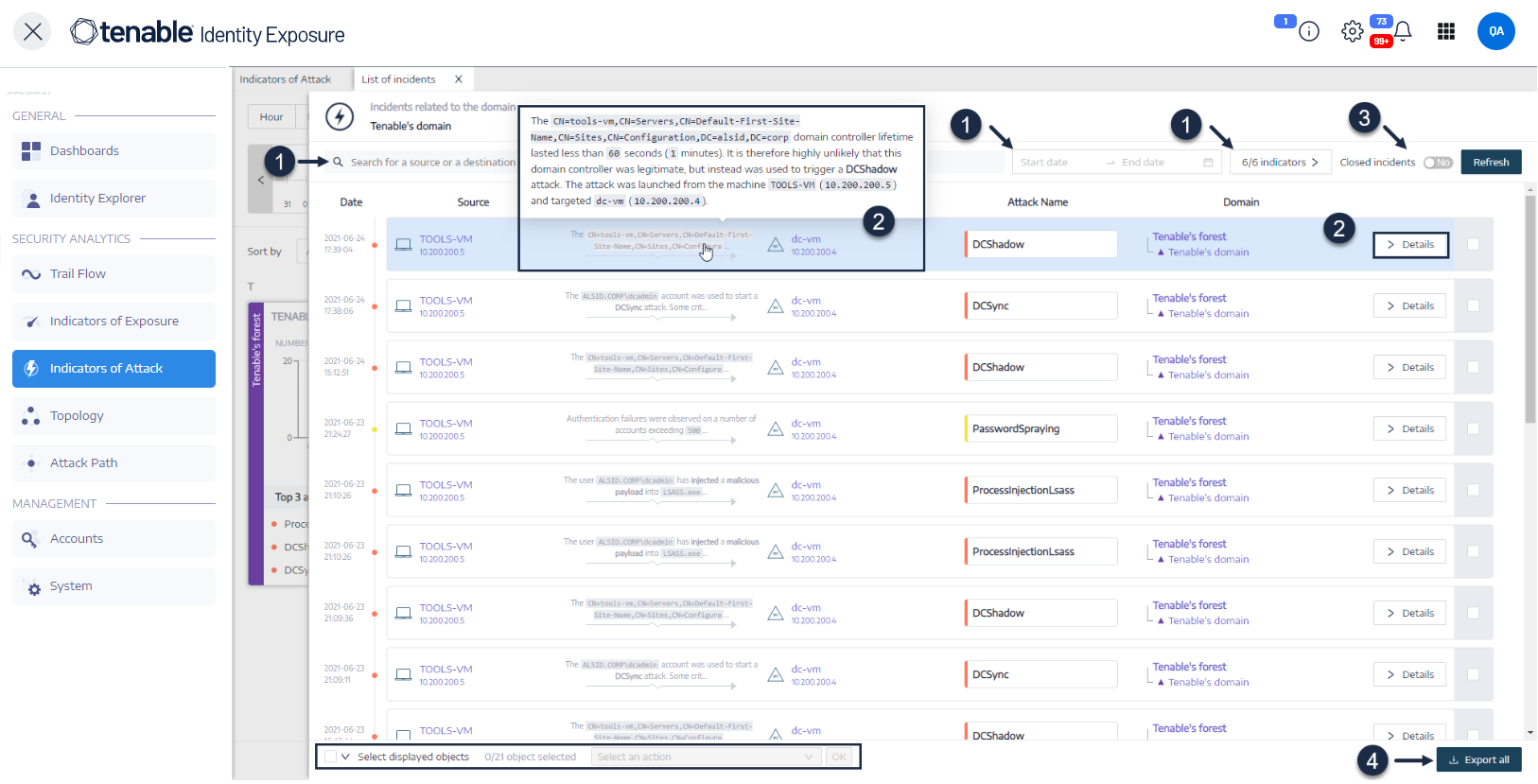
The Indicators of Attack (IoA) list of incidents provides detailed information about specific attacks on your Active Directory (AD). This allows you to take the required action depending on the IoA's severity level.
To view attack incidents:
-
In Tenable Identity Exposure, click Indicators of Attack in the navigation pane.
The Indicator of Attacks pane opens.
-
Click on any domain tile.
The List of incidents pane appears with a list of incidents that occurred on the domain.
-
From this list, you can do any of the following:
-
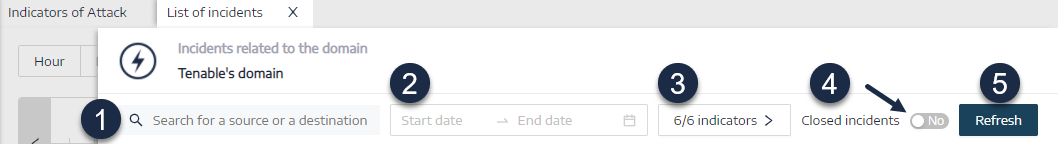
Define search criteria to search for specific incidents (1).
-
Access detailed explanations on the attacks affecting the AD (2).
-
Close or reopen an incident (3).
-
Download a report showing all incidents (4).
-
To search for an incident:
-
In the Search box, type the name of a source or destination.
-
Click the date picker to select a start/end date and the hour/minute time range for the incident:
-
Click n/n Indicators to select the related indicators.
-
Click the Closed Incidents toggle to Yes to limit the search to closed incidents.
-
Click Refresh.
Tenable Identity Exposure updates the list with the matching incidents.
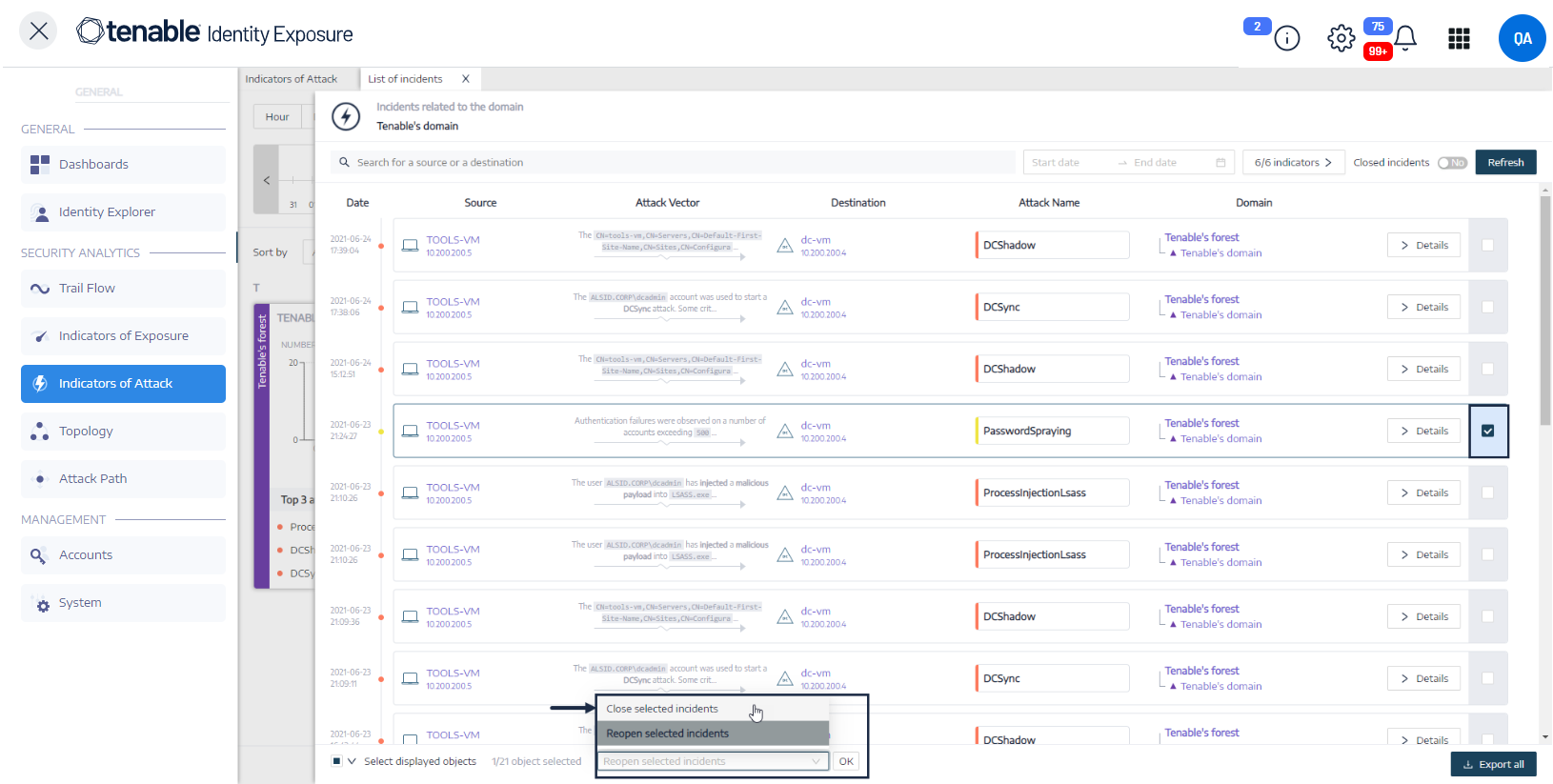
To close an incident:
-
At the bottom of the pane, click the drop-down menu and select Close selected incident.
-
Click OK.
A message asks you to confirm the closure.
-
Click Confirm.
A message confirms that Tenable Identity Exposure closed the incident and no longer shows it.
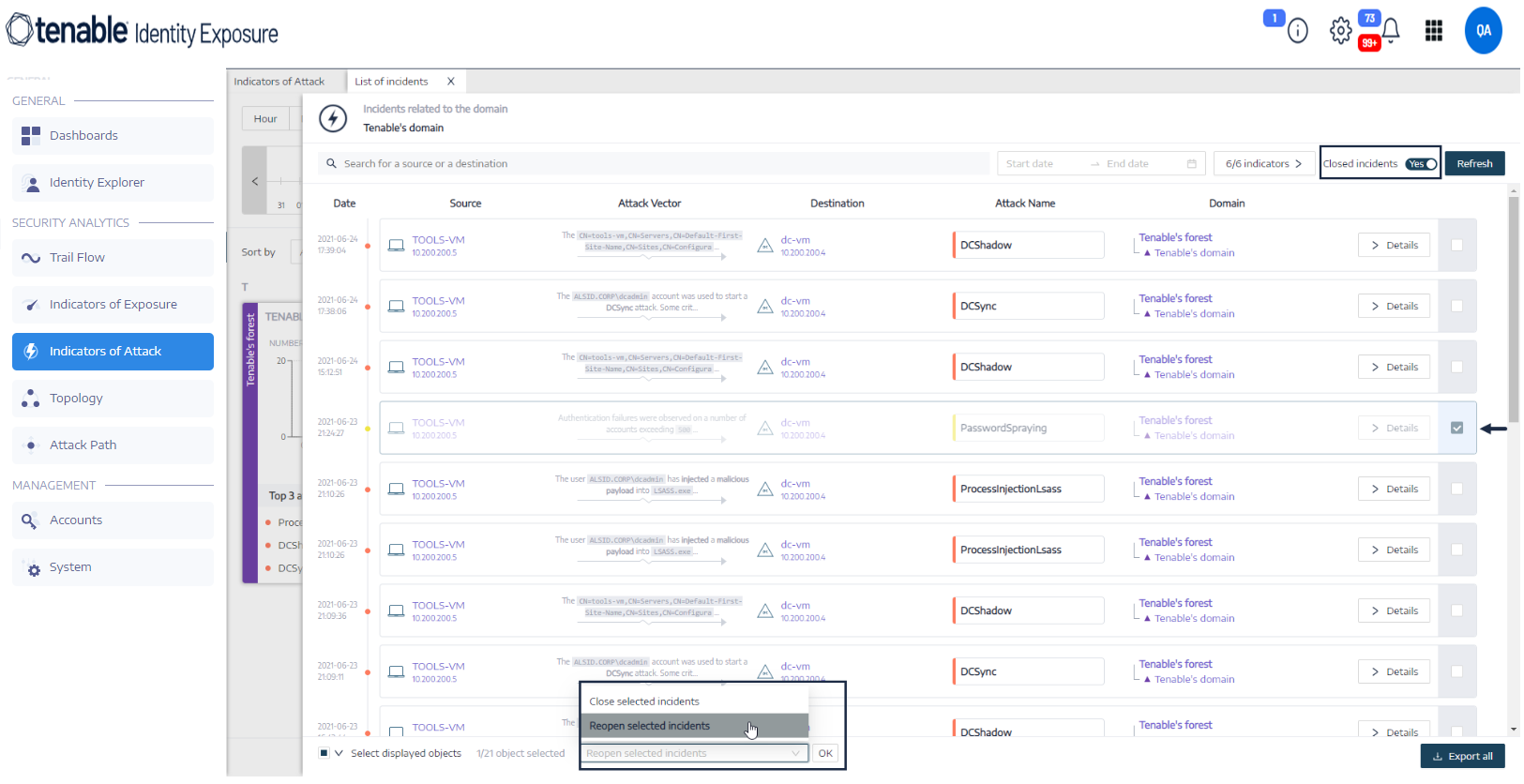
To reopen an incident:
-
In the List of incidents pane, click the Closed incidents toggle to Yes.
Tenable Identity Exposure updates the list with closed incidents.
-
Select the incident to reopen.
-
At the bottom of the pane, click the drop-down menu and select Reopen selected incident.
-
Click OK.
A message confirms that Tenable Identity Exposure reopened the incident.
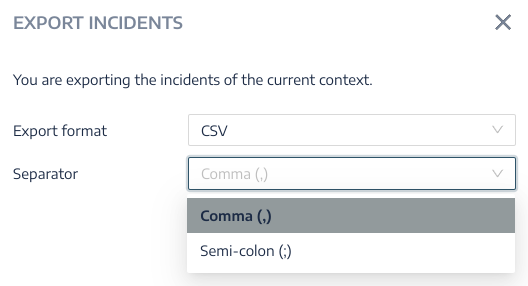
To export incidents:
-
In the List of incidents pane, click the Export All button at the bottom.
The Export Incidents side panel opens.
-
From the Separator drop-down list box, select a separator for the exported data: comma or semicolon.
Tenable Identity Exposure exports the data in CSV format for download.
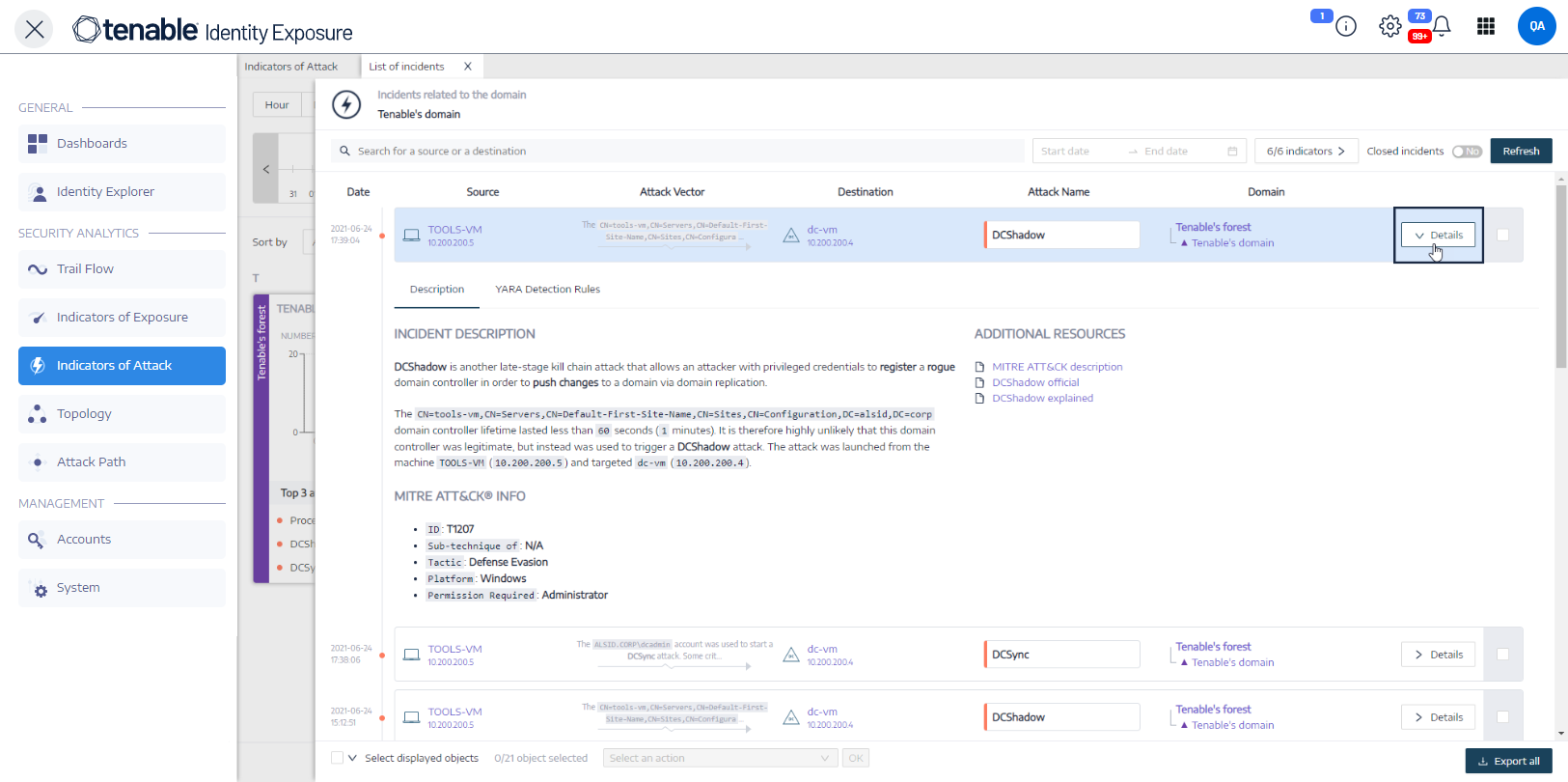
Incident Details
Each entry in the list of incidents shows the following information:
-
Date — The date when the incident triggering the IoA occurred. Tenable Identity Exposure shows the most recent at the top of the timeline.
-
Source — The source where the attack originated and its IP address.
-
Attack Vector — An explanation about what happened during the attack.
Tip: Hover over the attack vector to see more information about the IoA. -
Destination — The target of the attack and its IP address.
-
Attack Name — The technical name of the attack.
-
Domain — The domains that the attack impacted.
Tip: Tenable Identity Exposure can show a maximum of five panes when you click on several interactive elements (links, action buttons, etc.) in the List of incidents. To close all panes simultaneously, click anywhere on the page.
Attack Details
From the list of incidents, you can drill down on a specific attack and take necessary action to remediate.
To show attack details:
-
From the list of incidents, select an incident to drill down for details.
-
Click Details.
Tenable Identity Exposure displays the details associated with that attack:
Description
The Description tab contains the following sections:
Incident Description — Provides a short description of the attack.
MITRE ATT&CK Info — Gives technical information retrieved from the Mitre Att&ck (Adversarial Tactics, Techniques, and Common Knowledge) knowledge base. Mitre Att&ck is a framework that classifies adversary attacks and describes the actions that attackers take after they compromise a network. It also provides standard identifiers for security vulnerabilities to ensure a shared understanding by the cybersecurity community.
Additional Resources — Provides links to websites, articles, and whitepapers for more in-depth information on the attack.
YARA Detection Rules
The YARA Detection Rules tab describes the YARA rules that Tenable Identity Exposure uses to detect AD attacks at the network level to strengthen Tenable Identity Exposure's detection chain.
Note: YARA is the name of a tool primarily used in malware research and detection. It provides a rule-based approach to create descriptions of malware families based on textual or binary patterns. A description is essentially a YARA rule name, where these rules consist of sets of strings and a Boolean expression (source: wikipedia.org.)See also