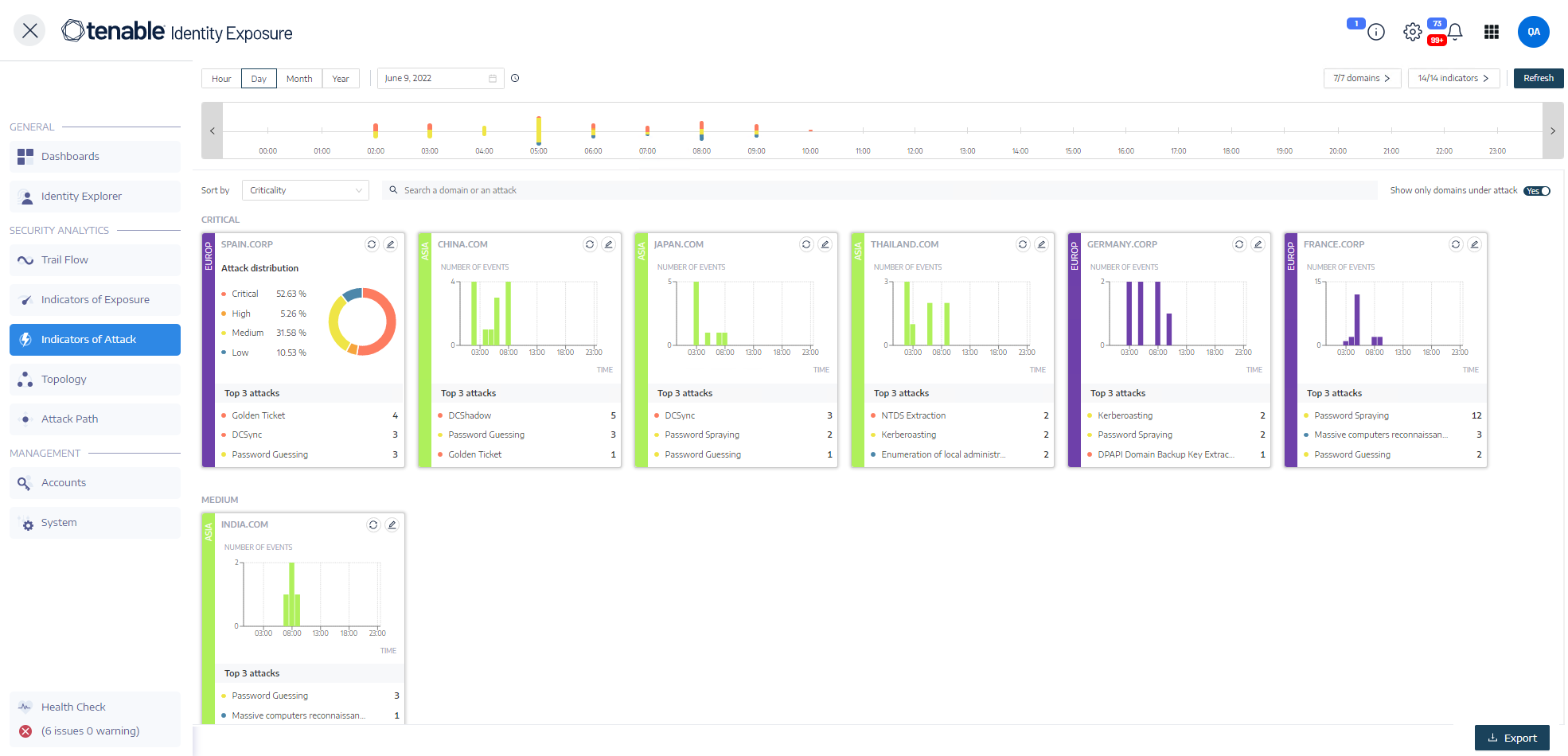
Indicators of Attack
Tenable Identity Exposure 's Indicators of Attack (IoA) give you the ability to detect attacks on your Active Directory (AD).
A consolidated view of Indicators of Attack shows a timeline and the top 3 incidents that impacted your AD in real time and the attack distribution in a single pane. You can do the following:
-
Visualize every threat from an accurate attack timeline.
-
Analyze in-depth details about an AD attack.
-
Explore MITRE ATT&CK descriptions directly from detected incidents.
For more information about specific IoAs, see the Indicators of Attack Reference Guide (requires Tenable Downloads site login.)
To show Indicators of Attack:
-
In Tenable Identity Exposure, click Indicators of Attack in the navigation pane.
The Indicator of Attacks pane opens.
-
By default, Tenable Identity Exposure shows all your AD forests and domains. To adjust this view, do any of the following:
-
Select the time period to show — Click on Hour, Day (default), Month, or Year.
-
Move along the timeline — Click on the left or right arrow to go forward or backward on the timeline.
-
Select a specific time — Click on the date picker to choose an hour, day, month, or year.
Return to current date and time — Click the
icon next to the date picker.
Select the domains — Click on n/n domains.
In the Forest and Domains pane, select the domains.
Click Filter on selection.
Tenable Identity Exposure updates the view.
Select the IoAs — Click on n/n indicators.
In the Indicators of Attack pane, select the IoAs.
Click Filter on selection.
Tenable Identity Exposure updates the view.
Sort the IoA tiles — In the Sort by box, click the arrow to show a drop-down list of choices: Domain, Criticality, or Forest.
Search for a domain or attack — In the Search box, type the domain name or attack.
Show only domains under attack — Click the Show only domains under attack toggle to Yes.
Export an attack report — Click Export.
The Export Cards pane appears.
In the Export format box, click the drop-down list arrow to select a format: PDF, CSV, or PPTX.
Click Export.
Tenable Identity Exposure downloads the report to the local machine.
Level of Severity
Tenable Identity Exposure detects and assigns severity levels to attacks:
| Level | Description |
|---|---|
| Critical — Red | Detected a proven post-exploitation attack that requires domain dominance as a prerequisite. |
| High — Orange | Detected a major attack that allows an attacker to reach domain dominance. |
| Medium — Yellow | The IoA is related to an attack that could lead to a dangerous escalation of privileges or allow access to sensitive resources. |
| Low — Blue | Alerts to suspicious behaviors related to reconnaissance actions or low-impact incidents. |
See also