Authentication Using LDAP
Tenable Identity Exposure allows you to authenticate using Lightweight Directory Access Protocol (LDAP).
To enable LDAP authentication, you must have the following:
-
A preconfigured service account with a user and password to access the Active Directory.
-
A preconfigured Active Directory group.
After you set up LDAP authentication, the LDAP option appears in a tab on the login page.
To configure LDAP authentication:
-
In Tenable Identity Exposure, click Systems > Configuration.
The configuration pane appears.
-
Under the Authentication section, click LDAP.
-
Click the Enable LDAP authentication toggle to enabled.
An LDAP information form appears.
-
Provide the following information:
In the Address of the LDAP server box, type the LDAP server's IP address beginning with ldap:// and ending with the domain name and port number.
Note: If you use an LDAPS server, type its address beginning with ldaps:// and ending with the domain name and port number. Use this procedure to complete the configuration for LDAPS.
In the Service account use to query the LDAP server box, type the Distinguished Name (DN), SamAccountName, or UserPrincipalName that you use to access the LDAP server.
In the Service account password box, type the password for this service account.
In the LDAP search base box, type the LDAP directory that Tenable Identity Exposure uses to search for users who attempt to connect, beginning with DC= or OU=. This can be a root directory or a specific organizational unit.
In the LDAP search filter box, type the attribute that Tenable Identity Exposure uses to filter users. A standard attribute for authentication in Active Directory is sAMAccountname={{login}}. The value for login is the value that user provides during authentication.
-
For Enable SASL bindings, do one of the following:
-
If you use SamAccountName for the service account, click the Enable SASL bindings toggle to enabled.
-
If you use the Distinguished Name or UserPrincipalName for the service account, leave the Enable SASL bindings as disabled.
Important Consideration for Windows Server 2025:There is a limitation in Windows Server 2025 where LDAP configuration with SASL bindings disabled only works if LDAPS is enabled.
To ensure proper functionality:
If using UPN or DN for the Tenable service account, you can enable SASL bindings in the LDAP configuration, and it will work correctly.
If you prefer to keep SASL bindings disabled, you must enable LDAPS for LDAP to function properly.
-
-
Under the Default Profile and Roles section, click Add an LDAP group to specify the groups allowed to authenticate.
An LDAP group information form appears.
-
In the LDAP group name box, type the distinguished name of the group (example: CN=TAD_User,OU=Groups,DC=Tenable,DC=ad)
-
In the Default profile drop-down box, select the profile for the allowed group.
-
In the Default roles box, select the roles for the allowed group.
-
-
If necessary, click on + to add a new allowed group.
-
Click Save.
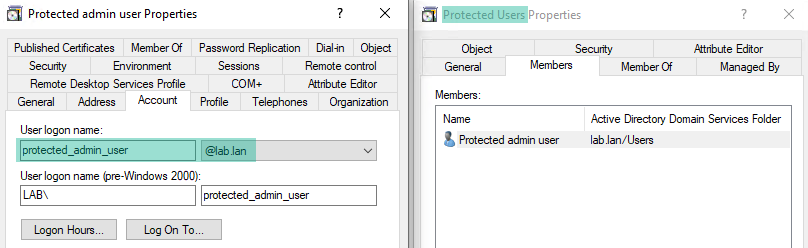
To use LDAP with members of the "Protected Users" group in AD:
Since members of the Protected Users group cannot use NTLM, you must ensure that you configure LDAP authentication correctly to use Kerberos instead.
-
Prerequisites: You must have already configured a User Principal Name (UPN) in Microsoft Active Directory. This is a username format used similar to an email address. It typically follows the format [email protected], where "username" is the user's account name and "domain.com" is the domain where the account is located.
-
Log in to Tenable Identity Exposure with your credentials.
-
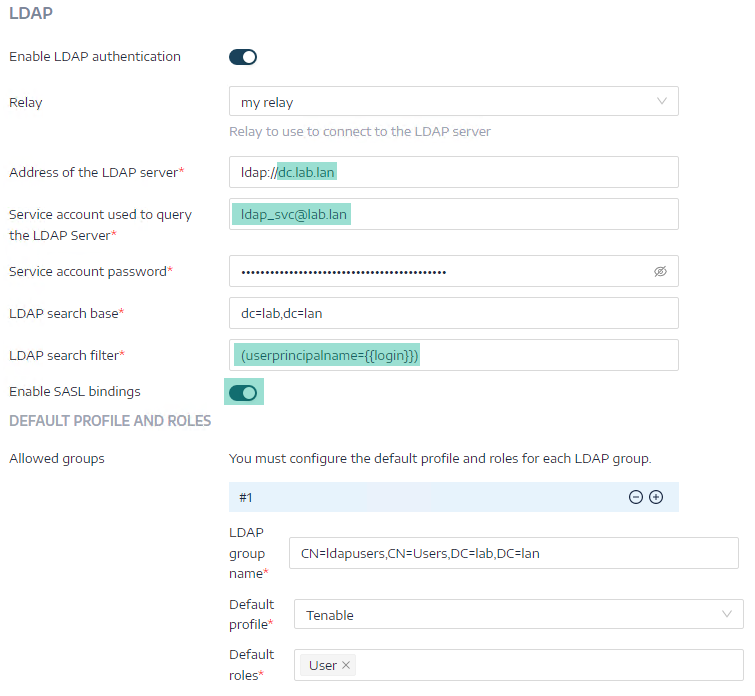
Configure the following LDAP options:
-
Use FQDN for the address of the LDAP server (ensure Secure Relay can resolve it).
-
Use a service account in UPN format (e.g. [email protected]).
-
Set the LDAP search filter to "(userprincipalname={{login}})"
-
Set SASL bindings to "on."
-
-
Log in to Tenable Identity Exposure using LDAP credentials as a member of the 'Protected Users' group with the User Principal Name syntax.
To add a custom trusted Certificate Authorities (CA) certificate for LDAPS:
-
In Tenable Identity Exposure, click Systems.
-
Click the Configuration tab to display the configuration pane.
-
Under the Application Services section, click Trusted Certificate Authorities.
-
In the Additional CA certificates box, paste your company's PEM-encoded trusted CA certificate for Tenable Identity Exposure to use.
-
Click Save.
LDAP Authentication Issues
After you complete and save the configuration, the LDAP option should appear on the login page. To confirm that the configuration is valid, you must be able to login using an LDAP account.
Error Messages
Two error messages can happen at this point:
-
An error has occurred during the authentication process. Please try again.
-
In this case there is a problem with the configuration.
-
Double check the complete configuration.
-
Check that the server hosting Tenable Identity Exposure is able to reach the LDAP server.
-
Check that the account used for the search is able to bind on the LDAP server.
-
For more details, check the application logs.
-
-
Your login or password is incorrect.
-
Verify that CAPS LOCK is not on and then retype your tested login and password.
-
This can be due to a problem with the group filter, the search filter or the search base fields.
-
Try to remove any group filtering temporarily. For more details, check the application logs.
-
For more information about security profiles and roles, see: