Customize Trail Flow Queries
The Trail Flow allows you to extend Tenable Identity Exposure capabilities beyond the default monitoring of Indicators of Exposure and Indicators of Attack. You can create custom queries to retrieve data quickly and also use the query as a custom alert that Tenable Identity Exposure can send to your Security Information and Event Management (SIEM).
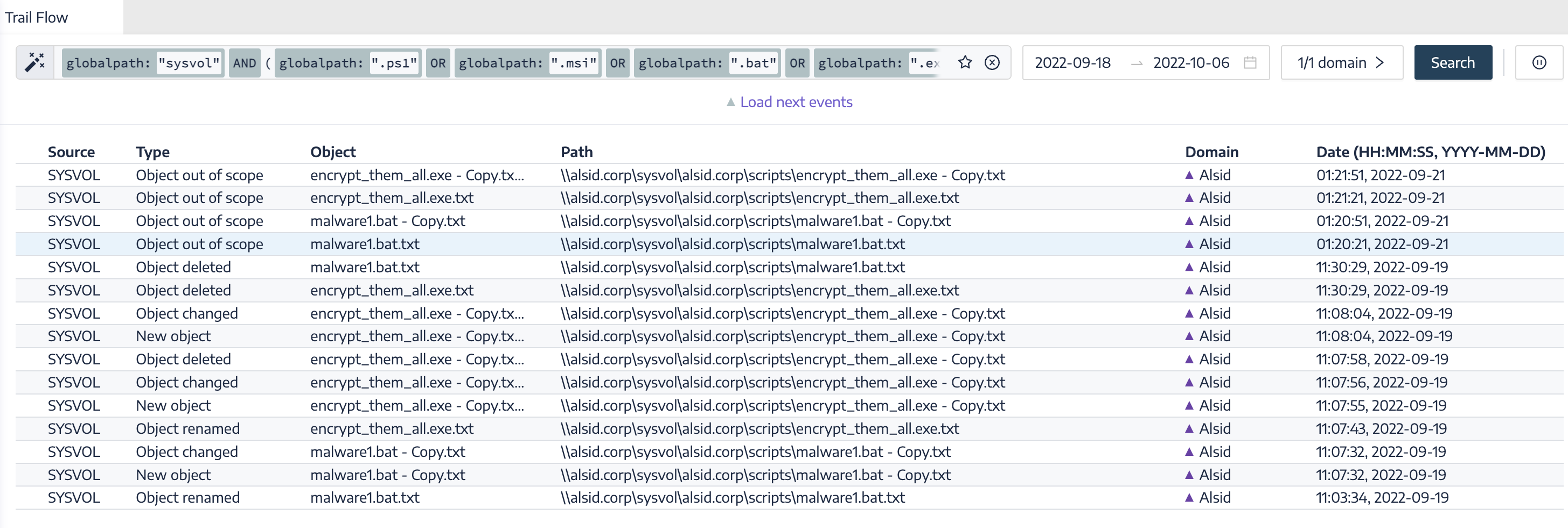
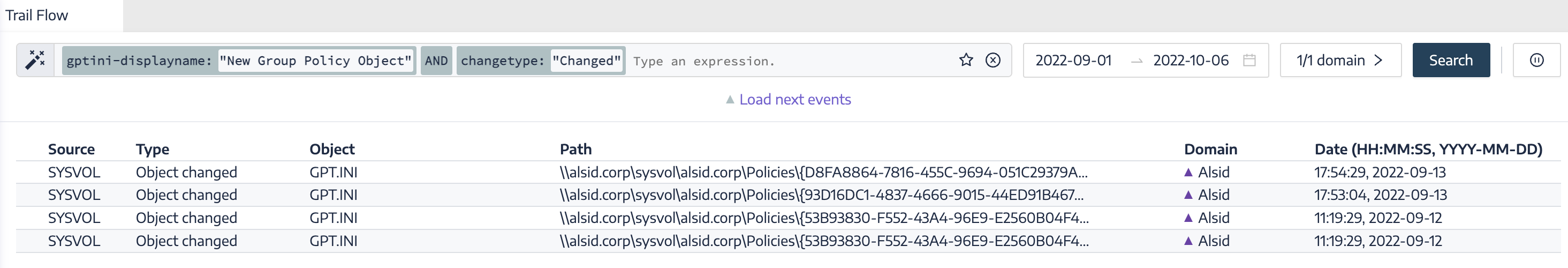
The following examples show practical custom queries in Tenable Identity Exposure.
| Use Case | Description | |
|---|---|---|
| GPO Startup and Shutdown binaries and Global SYSVOL path monitoring | Monitors for scripts in the boot startup path and/or the Global SYSVOL replication path. Attackers often use these scripts to abuse native AD services to proliferate ransomware quickly across an environment. | |
| Modifications of GPO Configuration | Monitors for modifications to GPO configurations. Attackers often use this method to downgrade security settings to aid in persistence and/or account takeover. | |
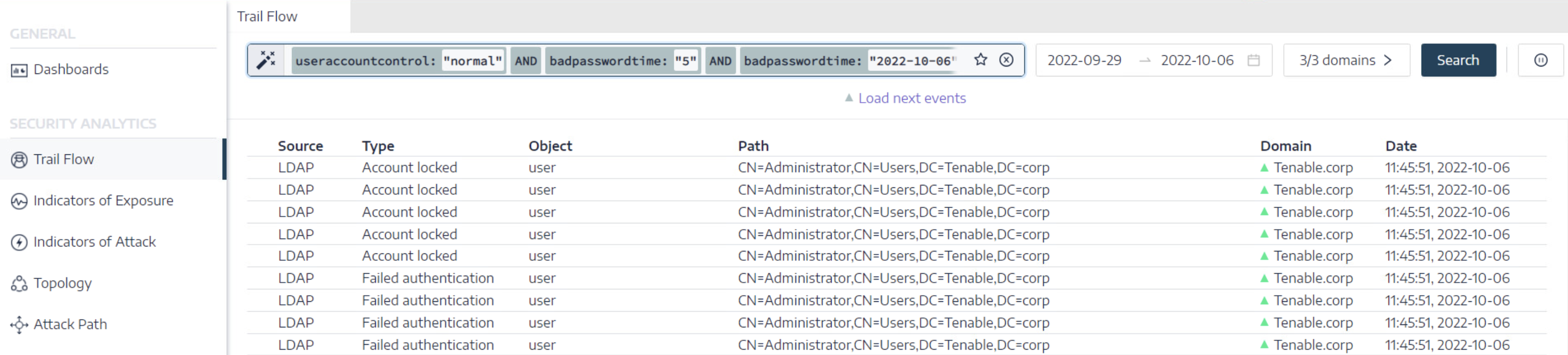
| Failed Authentication and Password Reset |
Monitors for multiple failed attempts to authenticate resulting in a lockout, which can act as an early warning flag for brute-force attempts. Note: You must set the lockout policy and date/time variables. For more information, see Authentication Using a Tenable Identity Exposure Account.
|
|
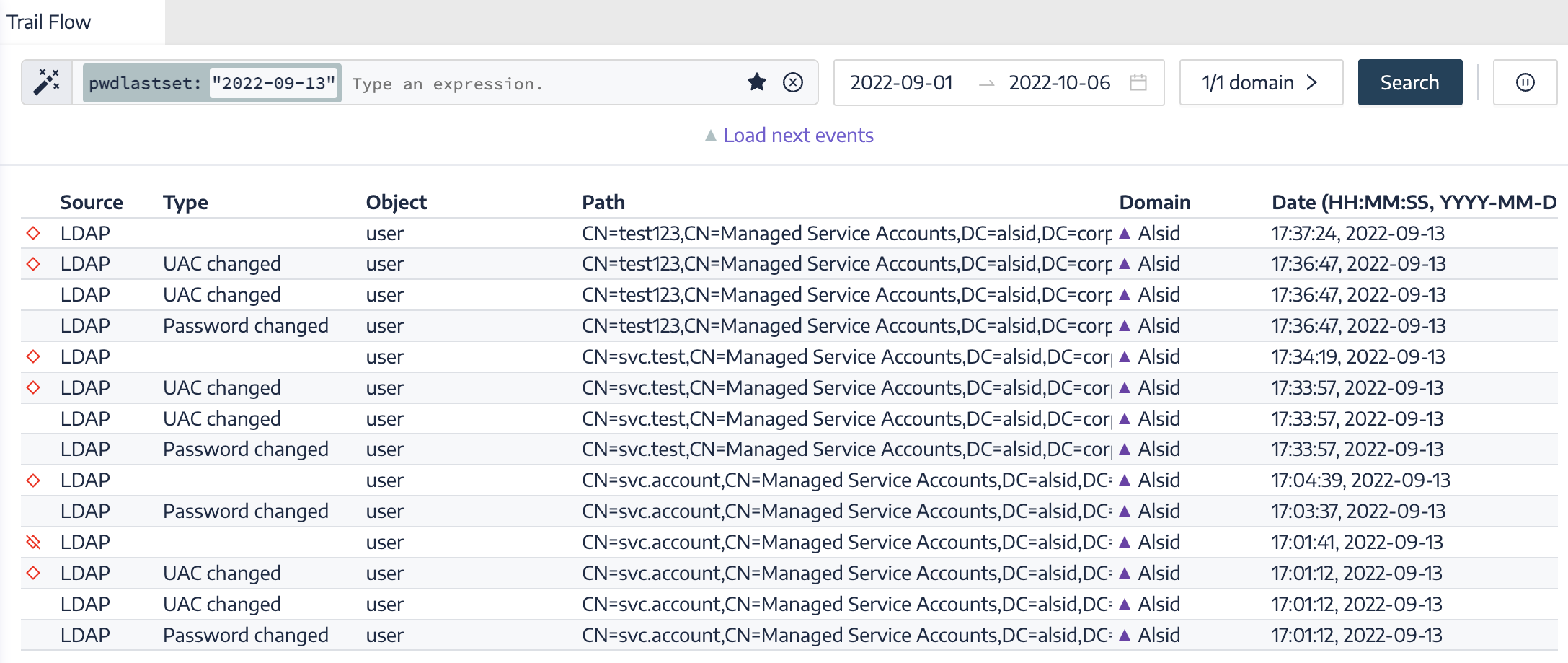
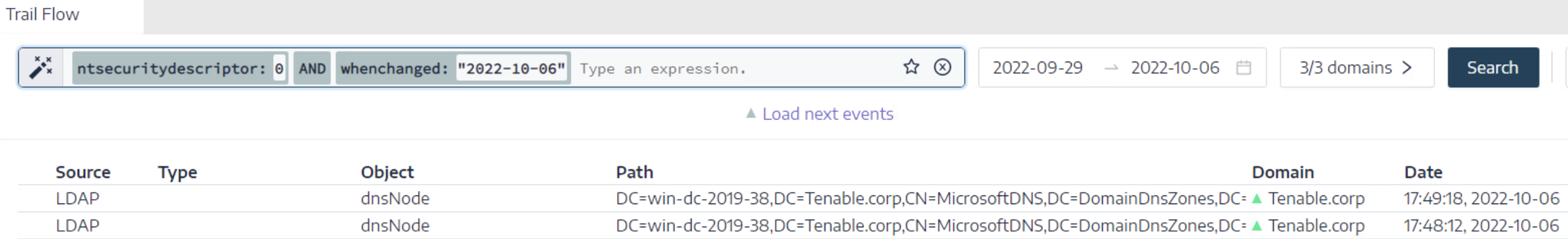
| Object Permissions Added, Removed, or Changed |
Monitors for unauthorized modifications to ACL rights and related object permission sets. Attackers abuse this method to elevate permissions. Note: You must supply the date/time variable.
|
|
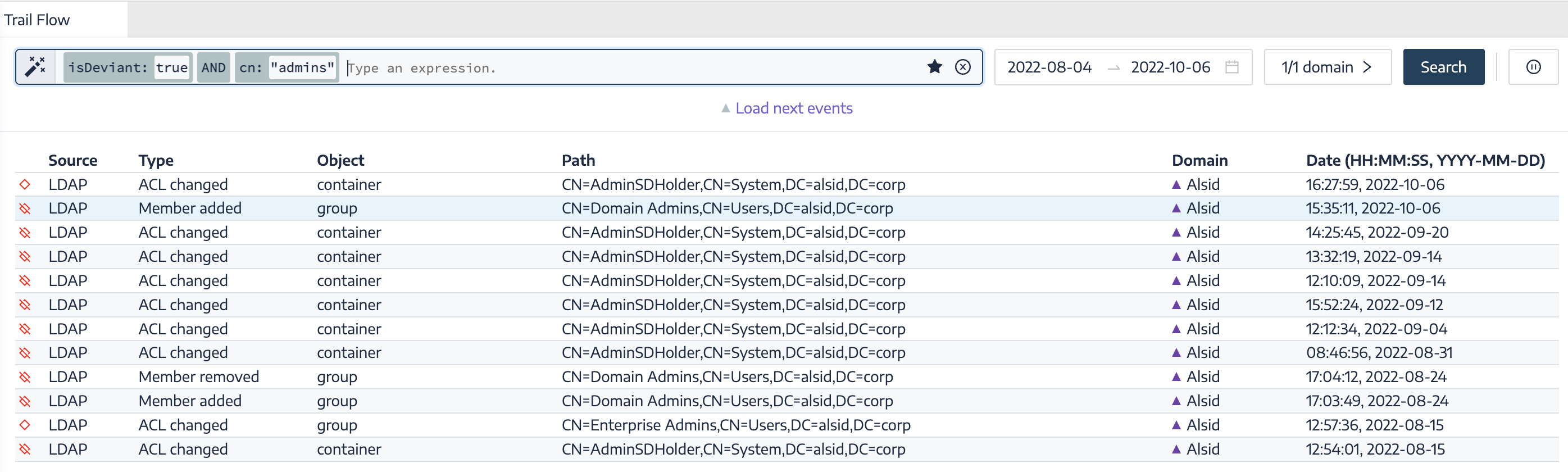
| Changes to Admins Resulting in a Deviance |
Built-in Administrative groups and custom groups are sensitive groups that require close monitoring for deviances or configuration changes that can introduce risk. This query lets you quickly review recent changes that could have adversely affected security settings within the admins group. |
|
See also