ITSM Configuration and Schedule Import
This section describes how to configure Tenable for ITSM.
Note: The ServiceNow configuration only supports Tenable Security Center versions 5.7 and later.
The ITSM integration configuration allows ServiceNow to poll and retrieve vulnerability data from Tenable Vulnerability Management/Tenable Security Center.
Before you begin:
In ServiceNow, you must have the x_tsirm_tio_itsm.admin role to complete the setup.
Note: Configure and tune Service Graph Connector for Tenable for Assets to match Tenable Assets with ServiceNow CIs. If you do not do this first, you may have issues with ITSM.
To set up the ITSM integration configuration, you must:
- Configure the Tenable Connector
- Create the ServiceNow and Tenable for ITSM Connector
- Create an Incident Rule
Create the ServiceNow and Tenable for ITSM Connector
- Log in to ServiceNow.
- In the left-hand menu, click Tenable Connector.
-
In the sub-menu, click Connectors.
The Tenable Connectors page appears.
-
Click the Tenable connector you want to use: Tenable.io or Tenable Security Center.
The Tenable Connector page appears.
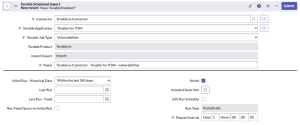
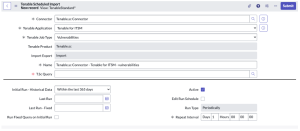
- In the Scheduled Jobs section, click New.
The Tenable Scheduled Import page appears. By default, the Tenable Product and Connector fields populate with the Tenable application/connector you selected in step 4.
-
From the Tenable Application drop-down box, select Tenable for ITSM.
Tenable Vulnerability Management
Tenable Security Center
-
If you are in a domain-separated environment, the Domain is set to the same value that is on the Connector record. If this value is not correct, create a new connector record in the correct domain.
- In the Name text box, type a name for the import.
-
Configure the options for your import.
Option Description T.sc Query (Only for Tenable Security Center) The Tenable Security Center query used for the import or export. Initial Run - Historical Data The amount of time (in days) of how far back you want to pull data. Last Run The date and time that the open/reopened import was last run. Last Run - Fixed The date and time that the fixed import was last run. Run Fixed Query on Initial Run Pulls fixed vulnerabilities on the first import. By default, this is set to deselected. Active If selected, an asset sync is automatically queued when you submit the import or export. Default setting: selected. Included Severities Specify the severities you want to be imported. By default, this is set to High, Critical Schedule Edit Run Schedule
Select this to edit the Run Type and Repeat Interval / Time
Run Type
The frequency with which you want the import to run.
Repeat Interval / Time The set time (hh/mm/ss) to run the import. - Click Update.
Create and enable Incident Rules so that the integration can create incidents. By default, a disabled example rule comes with the application.
-
From the left navigation pane, navigate to Tenable for ITSM > Configuration > Incident Rules.
The Incident Rules page appears.
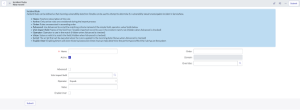
- Click New.
The New record page appears.
- In the Name text box, type a name for the matching rule.
- Select the Active check box.
-
(Option 1) If you want to use scripting to create this rule, click the Advanced check box, and type the desired script. Refer to the default rule provided for an example script.
 Incident rule field options
Incident rule field options
ServiceNow ITSM Vulnerability Import Set Field Tenable Security Center Vulnerability Analysis Field Tenable Vulnerability Management Vulnerability Export Field u_acceptriskrulecomment acceptRiskRuleComment u_acrscore acrScore u_agent_uuid uuid asset.agent_uuid u_asset_hostname Script - dnsName OR ip1 asset.hostname u_assetexposurescore assetExposureScore u_bios_uuid asset.bios_uuid u_ci CI SysID2 CI SysID3 u_connector Connector SysID4 Connector SysID5 u_description description description u_device_type asset.device_type u_first_found firstSeen first_found u_first_found_date firstSeen first_found u_fqdn dnsName asset.fqdn u_hasbeenmitigated hasBeenMitigated u_hostname Script - dnsName OR ip6 u_hostuniqueness hostUniqueness u_hostuuid hostUUID u_indexed indexed u_ip ip asset.ipv4 u_ips ip u_job_type “vuln_data”7 “vuln_data”8 u_keydrivers keyDrivers u_last_fixed last_fixed u_last_found lastSeen last_found u_last_found_date lastSeen last_found u_mac_address macAddress asset.mac_address u_netbios_name netbiosName asset.netbios_name u_operating_system operatingSystem asset.operating_system u_operatingsystem operatingSystem u_output pluginText output u_plugin_cve cve plugin.cve u_plugin_description description plugin.description u_plugin_family family.name plugin.family u_plugin_family_type family.type u_plugin_id pluginID plugin.id u_plugin_modification_date pluginModDate plugin.modification_date u_plugin_name pluginName plugin.name u_plugin_publication_date vulnPubDate plugin.publication_date u_plugin_solution solution plugin.solution u_plugin_synopsis synopsis plugin.synopsis u_pluginname pluginName u_port port u_port_port port port.port u_port_protocol protocol port.protocol u_priority Script - 1-49 Script - 1-410 u_product_type “tsc”11 “tio”12 u_recastriskrulecomment recastRiskRuleComment u_reopened Script - true/false13 Script - true/false14 u_repository_data_format repository.dataFormat u_repository_id repository.id u_repository_name repository.name u_risk_accepted acceptRisk u_risk_recasted recastRisk u_scan scan u_scan_completed_at scan.completed_at u_scan_started_at scan.started_at u_scan_uuid scan.uuid u_scunique Calculated Uniqueness15 u_severity severity.name severity u_severity_default_id severity_default_id u_severity_id severity.id severity_id u_severity_modification_type severity_modification_type u_source_name “Tenable.sc”16 “Tenable.io”17 u_state Script - OPEN/FIXED18 state u_substate Script19 Script20 u_tenable_plugin Generated Plugin SysID21 Generated Plugin SysID22 u_uniqueness uniqueness u_vpr_score vprScore vpr.score u_vprcontext vprContext u_xref xref - (Option 2) In the Vuln Import field text box, select the appropriate asset field for the rule.
- (Option 2) In the Operator text box, select the appropriate operator for the rule.
- (Option 2) In the Value text box, type the value for the rule.
-
To reorder the incident rule, update the value in the Order text box. Incident rules run in ascending order (lowest to highest).
If you are in a domain-separated environment, the incident rule is created in the current domain.
- Click Submit.
Plugins
To view plugins:
- Navigate to Tenable for ITSM > Plugins.
Vulnerabilities
To view vulnerabilities:
- Navigate to Tenable for ITSM > Vulnerabilities.
Incidents
To view incidents:
- Navigate to Tenable for ITSM > Incidents.