Tenable Vulnerability Management New Data Format: Relocate Open Port Findings
Last Revised: February 12, 2024
If you are responsible for the administration of Tenable Vulnerability Management and related products in your organization, use the following guide to investigate and validate the impact that the new Relocate Open Port Findings configuration has on your organization, if any, and act accordingly.
Background
Tenable Nessus scanners and Tenable Nessus Agents produce large volumes of repetitive Info-level findings per assessed host. High-traffic Info plugins, such as port scans, can produce more than 40% of all data processed through the Tenable platform pipeline and export volume.
To decrease the total amount of data processed and greatly improve the processing time, query time, and export time on the platform, Tenable has consolidated port scan findings for 10 specific plugins and has relocated the results as an asset property. This data format is available now via the Relocate Open Port Findings setting, which is described in this document.
The first stage of this change was made available to all platform customers on May 26, 2023, via the High-Traffic Info Plugins setting. To date, the High-Traffic Info Plugins setting has improved approximately 30% of all customer scan job results. Some customers have experienced end-to-end scan time reductions of up to 60%.
At a later date, Tenable will move findings for the following ten plugins to the Asset Details page that appears when you select a host asset on the Assets workbench.
-
34220 — Netstat Portscanner (WMI)
-
34252 — Microsoft Windows Remote Listeners Enumeration (WMI)
-
11219 — Nessus SYN Scanner
-
14272 — Netstat Portscanner (SSH)
-
25221 — Remote listeners enumeration (Linux / AIX)
-
10736 — DCE Services Enumeration
-
99265 — macOS Remote Listeners Enumeration
-
10335 — Nessus TCP scanner
-
14274 — Nessus SNMP Scanner
-
34277 — Nessus UDP Scanner
Before this update occurs, you can turn the Relocate Open Port Findings setting on to enable this new data format. Tenable recommends enabling this setting to minimize the impact of future data reformatting.
Findings and Assets Data Structure Change
The Relocate Open Port Findings data format change combines all individual findings per plugin, per host, and per port into a single plugin finding per host. The single, consolidated finding is available in the Assets user interface to query, tag, and export on.
Important: The new data structure change only applies to the Info plugin output for the 10 affected plugins. This does not apply to the port data associated with every reported vulnerability; the port data remains intact and unchanged. All Tenable Vulnerability Management views and reports already exclude the data that these 10 plugins produce from view. If you are not explicitly requesting this data or performing post-processing on individual port results, this data format change may not affect your organization.
Assess and Prepare for Relocate Open Port Findings
To enable the new data structure changes, you must enable the Relocate Open Port Findings setting in the Tenable Vulnerability Management user interface. Before doing so, use the following steps to assess whether your organization is ready to switch to the new data structures:
-
If you do not use open port Info plugins or findings to query or export, and they are not integrated with your external systems, proceed to enable Relocate Open Port Findings immediately.
-
If you use open port Info findings to query or export through the user interface only (in other words, not through the API or integrations), learn and use the new filter features. Then, proceed to enable Relocate Open Port Findings.
Tip: As of December 5, 2023, if you enabled Relocate Open Port Findings in the user interface, you can see open port data for Info-level findings in your asset export API data. For more information, see the Asset Export Open Port Findings for Info-level Plugins API changelog.
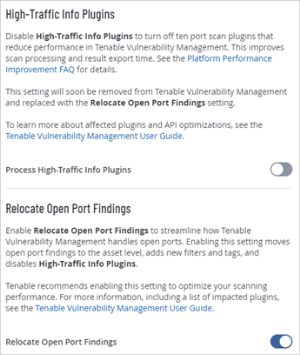
Note: When you enable Relocate Open Port Findings, the old findings format is disabled by default. However, you can revert to the old format by enabling the High-Traffic Info Plugins setting. Tenable only recommends doing so for testing purposes.
Enable Relocate Open Port Findings
To enable the new data structure configuration, navigate to Settings -> General -> Scanning in the Tenable Vulnerability Management user interface and enable the Relocate Open Port Findings toggle. Once you enable Relocate Open Port Findings, the High-Traffic Info Plugins toggle disables by default.
User Interface Changes
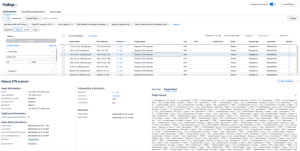
When you enable Relocate Open Port Findings, Tenable Vulnerability Management moves your open port information from the Findings workbench to the Open Ports tab on the Asset Details page. In addition, new features appear to help you view and manage your open ports. The following table explains the features that are added or removed.
| Added | Removed |
|---|---|
|
Findings for your open ports no longer appear on the Findings workbench. View your open ports in the Open Ports tab instead. |
New Relocate Open Port Findings Features
Enabling Relocate Open Port Findings introduces a new query filter and views for tags, assets, and findings:
-
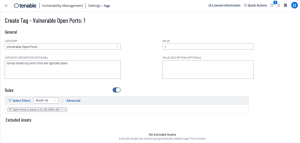
You can create tags with an Open Port rule, which enables asset grouping by individual open ports or ranges.
-
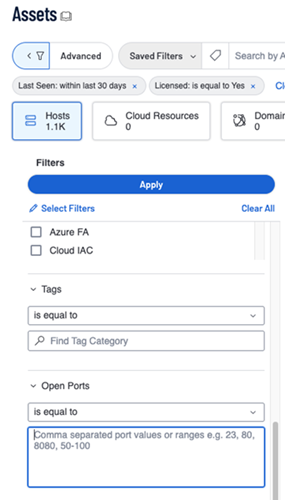
You can view and export assets based on an Open Ports filter.
-
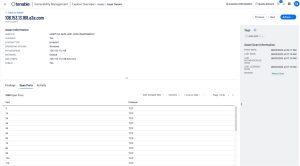
The Asset Details page now shows all the open ports found for that asset in the latest scan results in the Open Ports tab.
-
Port scanning Info plugins now combine all open port results into a single finding. This single finding has all port results combined into the plugin output.
The port for a single combined finding is set to N/A because there are no longer individual findings per port. You must adapt plugin output searching and Info finding processing to the new plugin output format.
The following is an example of the new plugin output format:
{"listening":[{"port":3,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":14,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":24,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":34,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":44,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":54,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":64,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":74,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":84,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":94,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":104,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":115,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":126,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":137,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":148,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":159,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":170,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":181,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":192,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":203,"protocol":"TCP","interfaces":null,"all_interfaces":false},{"port":214,"protocol":"TCP","interfaces":null,"all_interfaces":false}],"closed":{}}
Future Improvements
Tenable plans to release additional features to leverage the new format further, such as state-change dates and stale data clean up for legacy data that your scan configurations do not age out.