CIS Control 13: Data Protection
The focus of this control is to ensure that all data is classified and protected in accordance with established data classifications. To establish these data classifications, organizations should develop a list of the key data types and define the overall importance to the organization. This can be used to create a data classification scheme for the organization. Labels, such as “Sensitive,” “Business Confidential”, and “Public,” should be used. The information owners need to be aware of the classification policy and the tools, procedures, and controls on said data.
The CIS states this Control is critical:
“Data resides in many places. Protection of that data is best achieved through the application of a combination of encryption, integrity protection, and data loss prevention techniques. As organizations continue their move towards cloud computing and mobile access, it is important that proper care be taken to limit and report on data exfiltration while also mitigating the effects of data compromise.
Some organizations do not carefully identify and separate their most sensitive and critical assets from less sensitive, publicly accessible information on their internal networks. In many environments, internal users have access to all or most of the critical assets. Sensitive assets may also include systems that provide management and control of physical systems, such as Supervisory Control and Data Acquisition (SCADA). Once attackers have penetrated such a network, they can easily find and exfiltrate important information, cause physical damage, or disrupt operations with little resistance. For example, in several high-profile breaches over the past few years, attackers were able to gain access to sensitive data stored on the same servers with the same level of access as far less important data. There are also examples of using access to the corporate network to gain access to, then control over, physical assets and cause damage.”
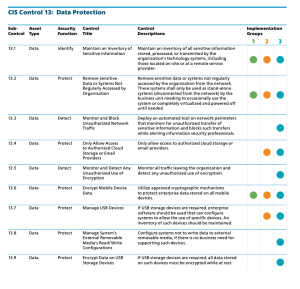
The journey of implementing the CIS Controls continues with the prevention of data exfiltration, mitigating the effects of exfiltrated data, and ensuring the privacy and integrity of sensitive information. As with many of the CIS controls, the first step is establishing an asset inventory. With data files, this can feel like an insurmountable task. This is where knowing what is stored on the network, and where, is extremely important. Properly storing the data at rest or on mobile systems is critical to the security and tracking of the data. This control helps guide the organization through this review process. The three specific sub-controls that are part of Implementation Group 1 (IG1) are:
For CIS Control 13, Tenable products allow security operations teams to use Tenable Security Center Continuous View to analyze and search large amounts of data files for sensitive data. Located on the Tenable download portal and in Tenable Security Center feed, the security team can download and install audit files for sensitive data. Using these audit templates, file systems can be scanned and checked for sensitive data. For many organizations, these files need to be customized for optimum effectiveness. The Tenable Professional Services team can help with customization.
There are 4 existing dashboards that are designed to work with these audit files. These templates can be used to get started in using Tenable Security Center to assist IG1 organizations with Control 13.