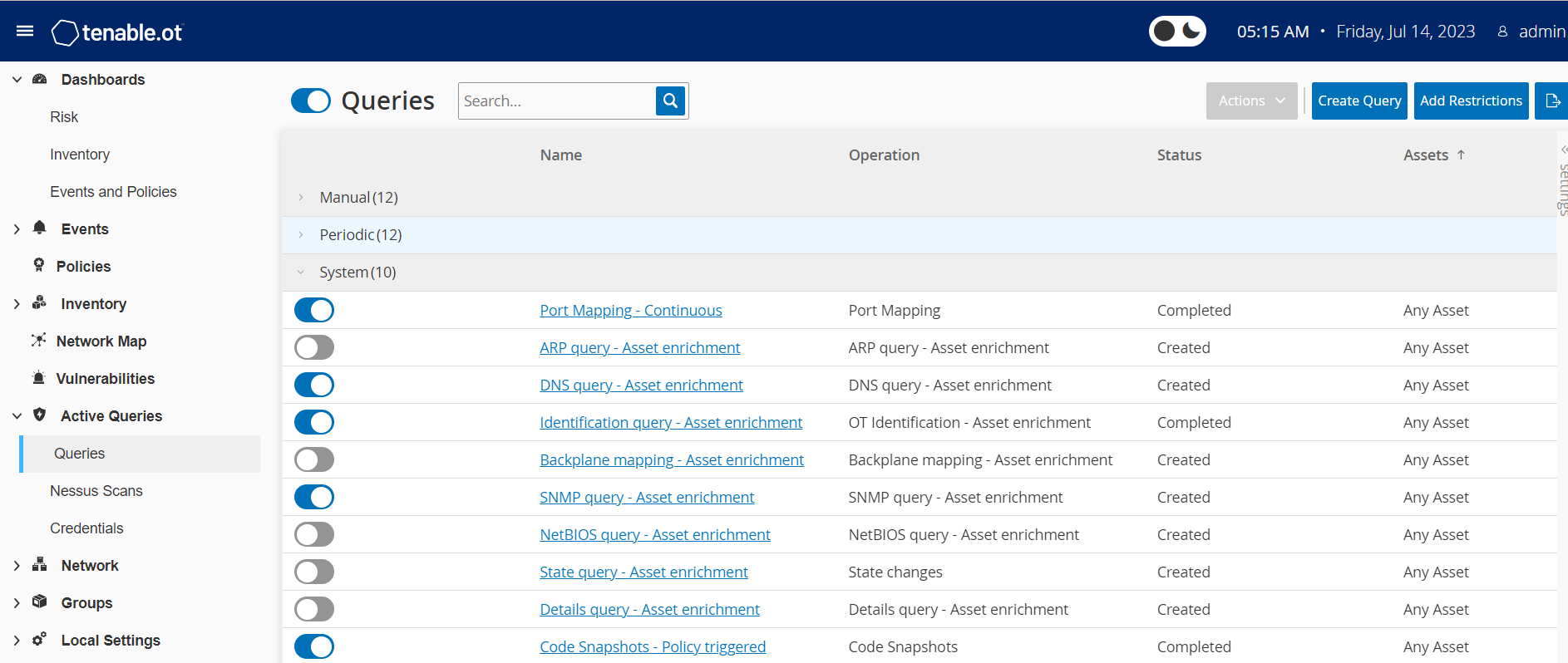
Active Queries
The OT Security Queries window allows you to configure and activate the queries features. For a general explanation of the Queries technology, see OT Security Technologies. As part of the initial setup, Tenable recommends that you activate all query capabilities. At any time, you can activate/de-activate any query functions. You can also adjust the settings for when and how to execute the queries.
In addition to the automatic queries that run periodically, you can initiate queries on demand by clicking the toggle next to the query.
You can activate and configure queries from the Active Queries > Queries page. There are three options available to control Active Queries in a granular manner: Manual, Periodic, and System.
Manual — This controls queries that you can execute when reviewing a single asset by using the Resync option for that asset. Manual queries allow you to control the product functionality for specific kinds of queries when reviewing a single monitored asset. Enabling the options for resync allow you to perform those queries when reviewing an asset. For more information about the Resync option, see Perform Resync.
Periodic — These are queries that run on a regular time interval that you set. Once enabled, the query performs according to the schedule that you specify in the Repeats column on this page. You can run all periodic queries on-demand by right-clicking them and selecting Run Now. Doing so does not affect the schedule or time set for the next query. All queries that you create manually have the periodic setting.
System — These are queries that OT Security handles automatically based on certain criteria or conditions. For example, Asset Enrichment-based queries occur whenever Tenable initially observes a device passively or actively. With Asset Enrichment, OT Security fingerprints and identifies the device as soon as it appears on the network. Asset Enrichment also controls the Policy Triggered Snapshots under the control of the policy configuration for controller-based events.
- Port Mapping — Continuous
- Identification Query — Asset enrichment
The Queries table shows the following information:
| Column | Description |
|---|---|
| Enable or Disable toggle | Click the toggle next to the query name to enable or disable the query. |
| Name | Name of the query. |
| Operation | The type of query: Discovery, Periodic, or System query. |
| Status | The status of the query: Created, Ongoing, Preparing, Completed, and Failed. |
| Assets |
The asset groups that this query must poll. Note: You can build your own asset groups to use in the queries that you configure.
|
Create Query
You can create queries for different projects and functions to control which query runs and when it runs.
For example, you can configure custom queries for the following scenarios:
-
Different maintenance times for different parts of the plant.
-
Different projects and criticality for different assets.
-
Different queries for OT functions and IT functions.
To create a query:
-
Go to Active Queries > Queries.
The Queries window appears.
-
Click Create Query.
The Create Query panel appears.
-
Select the required Query type from one of the following options:
-
Discovery — These are queries that detect live assets in the network that OT Security monitors.
-
Asset Discovery leverages Internet Control Message Protocol (ICMP) or ping to detect live and responding IP addresses.
-
Active Asset Tracking regularly attempts to ping a known, monitored asset to ensure that it is still up and available.
-
Controller Discovery sends a set of multicast packets to the network to provoke controllers or ICS devices to reply directly to OT Security with their information.
-
-
IT — These are queries to fetch additional data points from monitored IT-type assets that OT Security observed. With the exception of NetBIOS, these IT-type queries require credentials.
-
NetBIOS query attempts to discover any devices listening for NetBIOS in the broadcast range of OT Security Sensoror OT Security itself. This type of query is suitable for identifying nearby Windows devices.
-
SNMP query uses SNMP v2 or SNMP v3 credentials solicit network infrastructure or networked devices supporting SNMP for their identification details. OT Security queries for SNMP system description and other parameters to help add asset context and assist with fingerprinting.
-
WMI details query fetches a variety of important data points from Windows-based systems. This requires the queried system to have a Windows account (local or domain) with sufficient permissions to poll the Windows Management Instrumentation (WMI) service.
-
WMI USB State queries determine if removable media like USB-drives or portable hard-drives are connected to the Windows device, such as an engineering workstation or server. This query is closely related to the policy Change in USB Configuration on Windows Machines as it is a prerequisite for this policy to work correctly.
-
-
OT — These are queries designed to poll controllers and embedded devices safely for more information using their proprietary protocols. OT Security performs read-only queries to gather device information. In some cases, OT Security queries more than just device identification details and can show information, such as PLC running state, or other modules connected to the backplane. OT Security attempts to query devices that are listening for proprietary protocols that OT Security supports.
-
-
Click Next.
The Query definition panel appears.
-
In the Name box, type a name for the query.
-
In the Description box, type a description about the query.
-
In the Assets drop-down box, select the assets.
Note: You can also use the Search box to search for a specific asset. -
In the Repeats Every section, type a number and select Days or Weeks from the drop-down box, . For certain queries, you can also set Minutes and Hours.
If you select Weeks, indicate the days of the week to run the queries.
-
In the At box, set the time of day to run the queries (in HH:MM:SS) by clicking on the clock icon and selecting the time, or by typing the time manually.
-
Click the Query State toggle to enable the query.
-
(Only for Asset Discovery) In the IP Ranges box, type the IP addresses of assets.
-
(Only for Discovery Queries) In the Number of Assets to poll simultaneously drop-down box, select the number of assets. Available options are: 10 Assets, 20 Assets, or 30 Assets.
-
(Only for Discovery Queries) In the Time Between Discovery Queries drop-down box, select the time between the discovery queries. Available options are: 1 second, 2 second, or 3 second.
Add Restrictions
You can block queries from running on specific assets, such as IP ranges, OT servers, Tablets, Medical Devices, Domain Controllers, and so on.
To add restrictions:
-
Go to Active Queries > Queries.
The Queries window appears.
-
In the Blocked Assets drop-down box, select the required assets to block.
Note: You can use the search box to search for specific assets. -
In the Restricted Clients drop-down box, select the required clients.
-
In the Blackout Period drop-down box, select the duration for which you want to block the assets. Available options are: None, Working Hours.
-
Click Save.
OT Security applies the restrictions on the specific clients and assets.
View Query
To view details of a query:
-
Go to Active Queries > Queries.
The Queries window appears.
-
In the row of the query you want to view, do one of the following:
-
Right-click the query and select View.
-
Select the query, then from the Actions menu, select View.
A window appears with the details of the query.
-
Edit Query
To edit details of a query:
-
Go to Active Queries > Queries.
The Queries window appears.
-
From the list of queries, select the one you want to edit and do one of the following:
-
Right-click the query and select Edit.
-
Select the query and select Edit from the Actions menu.
The Edit Query panel appears.
Note: You can also edit a query from the Query Details page. -
-
Modify the query as needed.
-
Click Save.
Duplicate a Query
-
Go to Active Queries > Queries.
The Queries window appears.
-
From the list of queries, select the one you want to create a copy and do one of the following:
-
Right-click the query and select Duplicate.
-
Select the query and then from the Actions menu, select Duplicate.
The Duplicate Query panel appears with details of the query.
Note: You can also create a duplicate of a query from the Query Details page. -
-
Rename the query and modify the details as needed.
-
Click Save.
OT Security saves the query in the Queries Table.
Run a Query
You can run periodic queries when needed.
To run a query:
-
Go to Active Queries > Queries.
The Queries window appears.
-
From the list of queries, select the one you want to run and do one of the following:
-
Right-click the query and select Run now.
-
Select the query, then from the Actions menu, select Run now.
A message asks for confirmation to run the query.
-
-
Click Ok.
OT Security runs the selected query.