Create Nessus Plugin Scans
The Nessus Plugin Scan launches an advanced Nessus scan that executes a user-defined list of plugins on the assets specified in the list of CIDRs and IP addresses.
The OT Security executes the scan on responsive assets within the designated CIDRs. However, to protect your OT devices, OT Security scans only confirmed network assets in the given range (non-PLCs). OT Security excludes assets of the type Endpoint from the scan.
Starting from OT Security 4.1, you can create new scans with the following options:
-
Perform Thorough Tests — This option allows Nessus to perform a detailed scan that includes plugins that may increase the scan duration, but helps uncover in-depth details such as JAR files or installed Python libraries.
-
High Verbosity Processing — This option enables the scan to provide additional details about the vulnerability that you can use to troubleshoot a scan finding. This option also allows Attack Path Analysis to leverage the Nessus scan connections data.
-
Network Timeout (In seconds) — The maximum time that Nessus must wait until it gets a response from the host. If you are scanning over a slow host, you can increase the number of seconds. The default is 15 seconds.
-
Max Simultaneous Checks Per Host — The maximum number of checks that Nessus must perform against the host. The default number of checks is 2.
-
Max Simultaneous Hosts Per Scan — The maximum number of hosts that Nessus can scan simultaneously. The default number of hosts is 10.
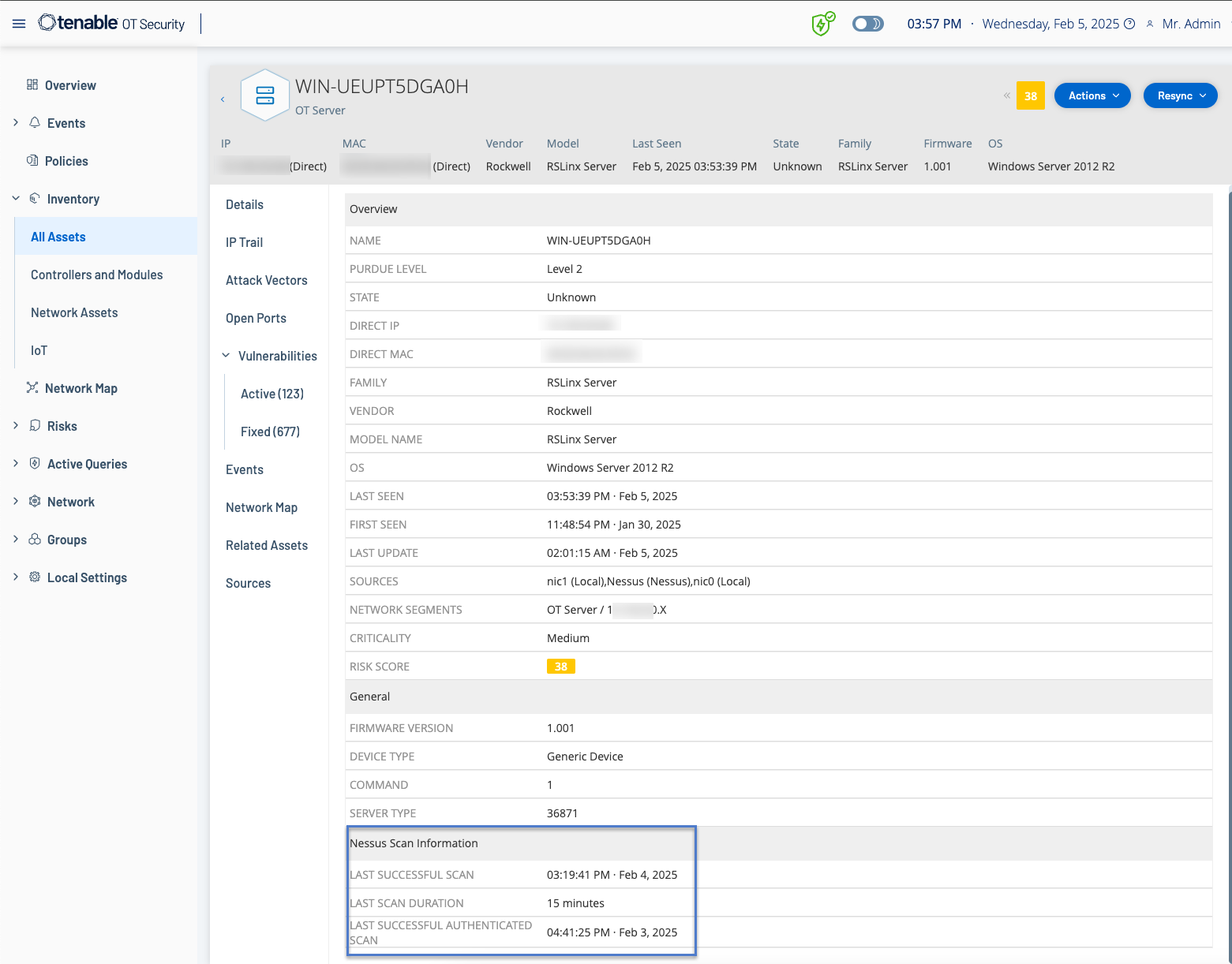
The Nessus Scan Information for a credentialed scan includes the following details:
-
Last Successful Scan
-
Last Scan Duration
-
Last Successful Authenticated Scan
The Nessus scan information helps you:
-
Understand assessed and unassessed assets.
-
Understand if your assets are targeted with credentialed or non-credentialed scans.
-
Perform best practices with scanning and vulnerability management. For example, performing vulnerability assessment scans against IT type assets running Windows, Linux. Scanning, whether with or without credentials, helps assess how much of your organization's attack surface is exposed both internally and externally.
The Nessus scan in OT Security uses the same policy settings as a basic network scan in Tenable Nessus, Tenable Security Center, and Tenable Vulnerability Management. The only difference is the performance options in OT Security. The following are the performance options for the Nessus scan in OT Security. These options also apply to the Nessus Basic scan you launch from the Inventory > All Assets page.
-
5 simultaneous hosts (max)
-
2 simultaneous checks per hosts (max)
-
15 second network read timeout
To run a basic Nessus scan on any one asset, see Perform Asset-Specific Tenable Nessus Scan.
Create a Nessus Plugin Scan
To create a Nessus Plugin Scan:
-
Go to Active Queries > Queries Management.
The Active Queries Management page appears.
-
Go to Data Collection > Active Queries.
The Active Queries Management page appears.
-
Click the Nessus Scans tab.
The Nessus Scans page appears.
-
In the upper-right corner, click Create Scan.
The Create Nessus Plugin List Scan panel appears.
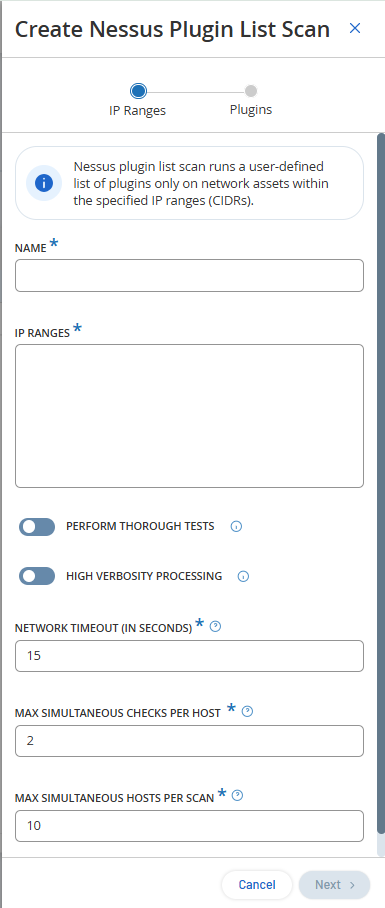
Note: The image shows the default values for creating a new Nessus scan. If you opt to run the scan with the default values, the scans run with the same configuration as the earlier scans. -
In the Name box, type a name for the Nessus scan.
-
In the IP Ranges box, type a range of IPs or CIDRs.
-
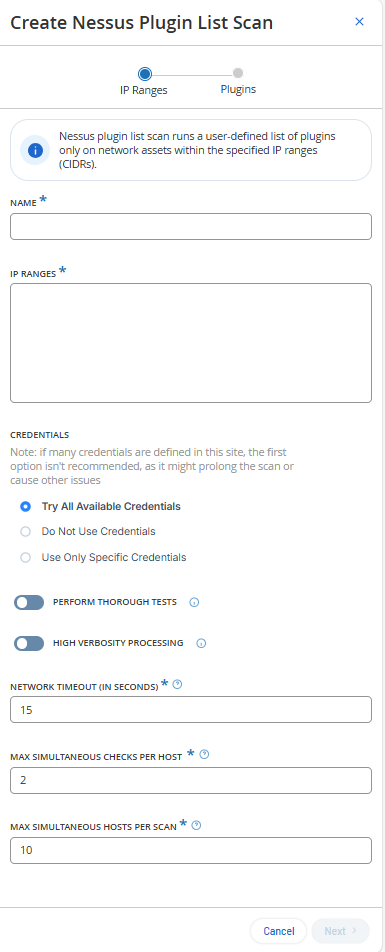
Select one of the options to assign credentials for the Nessus scan:
-
Do not use credentials — Select this option if no credentials are configured for the site.
Tip: Skip this option if you have several configured credentials, as selecting it may prolong the scan. -
Try All Available Credentials — Select this option if you want the scan to try all available credentials.
-
Use Only Specific Credentials
-
If you select Use Only Specific Credentials, select the required credentials from the available list of credentials.
-
-
-
(Optional) Click the Thorough Tests toggle to enable a detailed scan.
Note: The Thorough Tests options include plugins that may increase the scan duration, but enabling the option helps the Nessus scan uncover in-depth details such as JAR files or installed Python libraries. -
(Optional) Click the Higher Verbosity toggle to enable the scan to provide additional details about the vulnerability.
Note: Enabling Higher Verbosity allows the scan to provide additional details about the vulnerability or help troubleshoot a scan finding. This option also allows Attack Path Analysis to leverage the Nessus scan connections data. -
In the Network Timeout (In Seconds) box, type the maximum time that Nessus must wait until it gets a response from the host. If you are scanning over a slow host, you can increase the number of seconds. The default timeout is 15 seconds.
-
In the Max Simultaneous Checks Per Host, type the maximum number of checks that Nessus must perform against the host. The default number of checks is 2.
-
In the Max Simultaneous Hosts Per Scan box, type the maximum number of hosts that Nessus can scan simultaneously. The default number of hosts is 10.
-
Click Next.
The Plugins pane appears.
Note: OT Security lists only those plugins that are specific to the device. Your license must be up to date to receive new Plugins. To update your license, see Update the License. -
In the Plugin Family Name column, select the required Plugin Families to include them in the scan. In the right column, clear the checkboxes for individual plugins as needed.
Note: For more information about Tenable Nessus Plugin Families, see https://www.tenable.com/plugins/nessus/families. -
Click Save.
The new Nessus scan appears on the Nessus Scans page.
Note: To edit or delete an existing Tenable Nessus scan, right-click the scan, then select Edit or Delete.
Run a Nessus Plugin Scan
To run a Nessus Plugin Scan:
-
On the Nessus Scans page, do one of the following:
-
Right-click the scan, then select Run now.
-
Select the scan you want to run, then click Actions > Run now.
The Approve Nessus Scan dialog appears.
-
-
If you know there are no OT devices included in the scan, click Proceed Anyway.
The dialog closes and OT Security saves the scan.
-
To run the scan, right-click the scan row again and select Run now.
The Approve Nessus Scan dialog appears again.
-
Click Proceed Anyway.
OT Security now runs the scan. You can pause/resume, stop, or kill scans depending on their current status.