Findings
Use the Findings page to review the list of individual instances of vulnerabilities that affect your environment per asset. The Findings page allows you to do the following:
-
View detailed evidence for each specific “hit” of a vulnerability in your environment.
-
Filter the list of vulnerabilities by either properties of the plugin, the affected asset, the specific instance such as Status, Last hit, or any combination of the properties.
-
Export the filtered list of findings to assign them for remediation.
To access the Findings page:
-
In the left navigation menu, go to Risks > Findings.
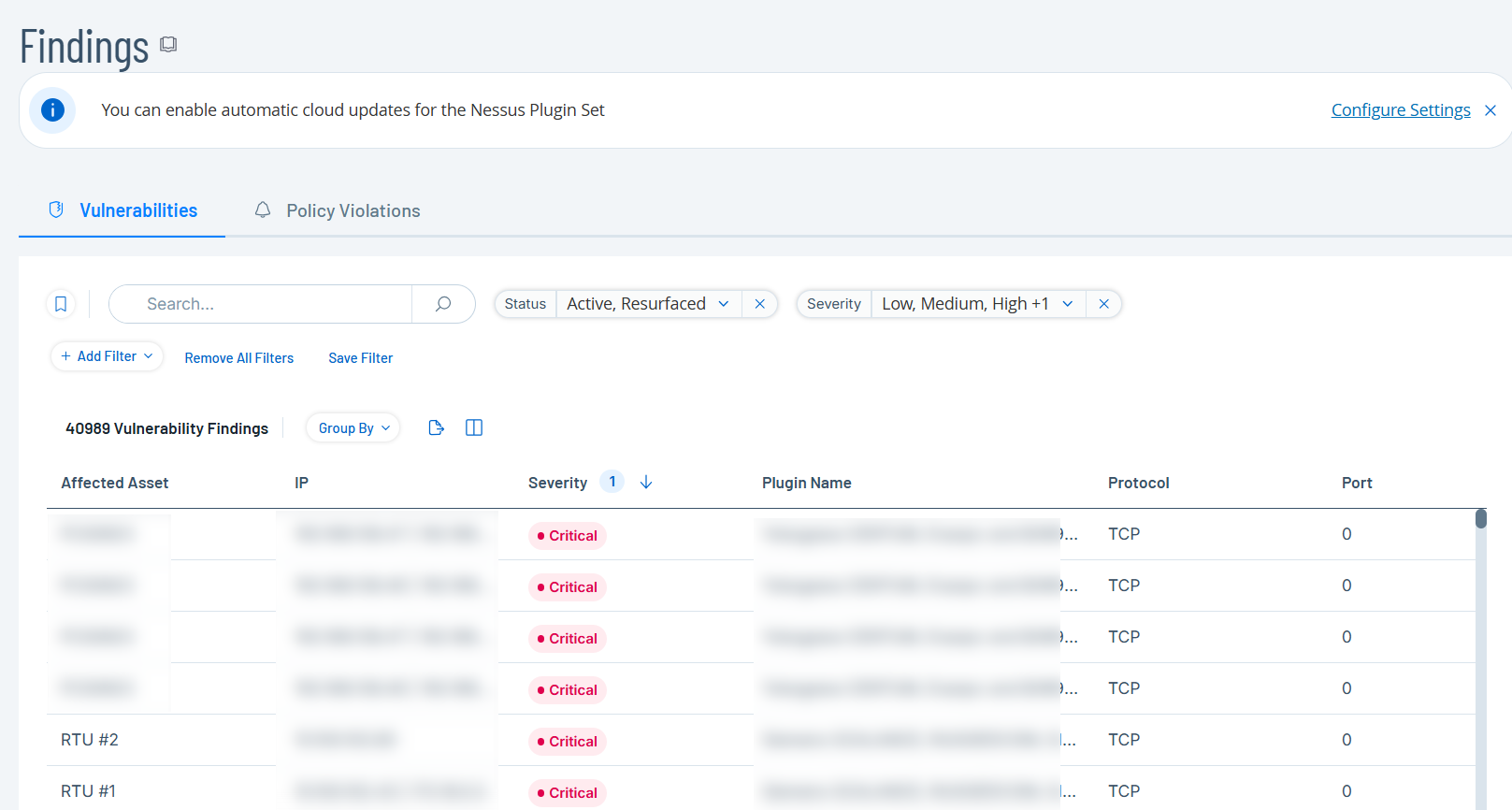
The Findings page appears with the vulnerabilities in a table format.
The Findings table includes the following details:
Column Description Affected Asset The asset where the vulnerability is detected. IP The IP address of the asset. Severity The severity of the vulnerability: Critical, Medium, Low, or Info. Plugin Name The plugin that detected the vulnerability. Plugin ID The ID of the plugin. Port The port where the vulnerability is detected. Protocol The protocol used to communicate with the asset. VPR Vulnerability Priority Rating for the vulnerability. Status The status of the vulnerability. The possible values are:
Active — Indicates that the vulnerability continuously appeared since its initial detection.
Fixed — Indicates that the vulnerability initially appeared and disappeared and not resurfaced.
Resurfaced — Indicates that the vulnerability appeared and disappeared and then reappeared.
Plugin Source The plugin source. First Hit The time when the vulnerability was first detected. Last Hit The time when the vulnerability was last detected. Asset Tags The tags associated with the asset. See Asset Tags & Groups. Fixed at The time when the vulnerability was remediated. Plugin Family The family of the plugin. Asset Type The asset type, such as PLC and OT device. Asset Risk Score The risk score of the asset. Asset Category The category to which the asset belongs to, such as Controller, Network Assets. Asset Vendor The name of the vendor of the asset. Asset Criticality The criticality of the asset based on the severity of the vulnerability: High Criticality, Medium Criticality, or Low Criticality. Asset Family The family of the asset. Asset Model The model of the asset. Firmware The firmware of the asset. OS The operating system that the asset runs on. Asset State The current state of the asset. Purdue Level The purdue level of the asset. Network Segment The network segment that the asset belongs to. Location The asset's location. Backplane Name The name of the backplane where the vulnerability was detected.
View Findings Details
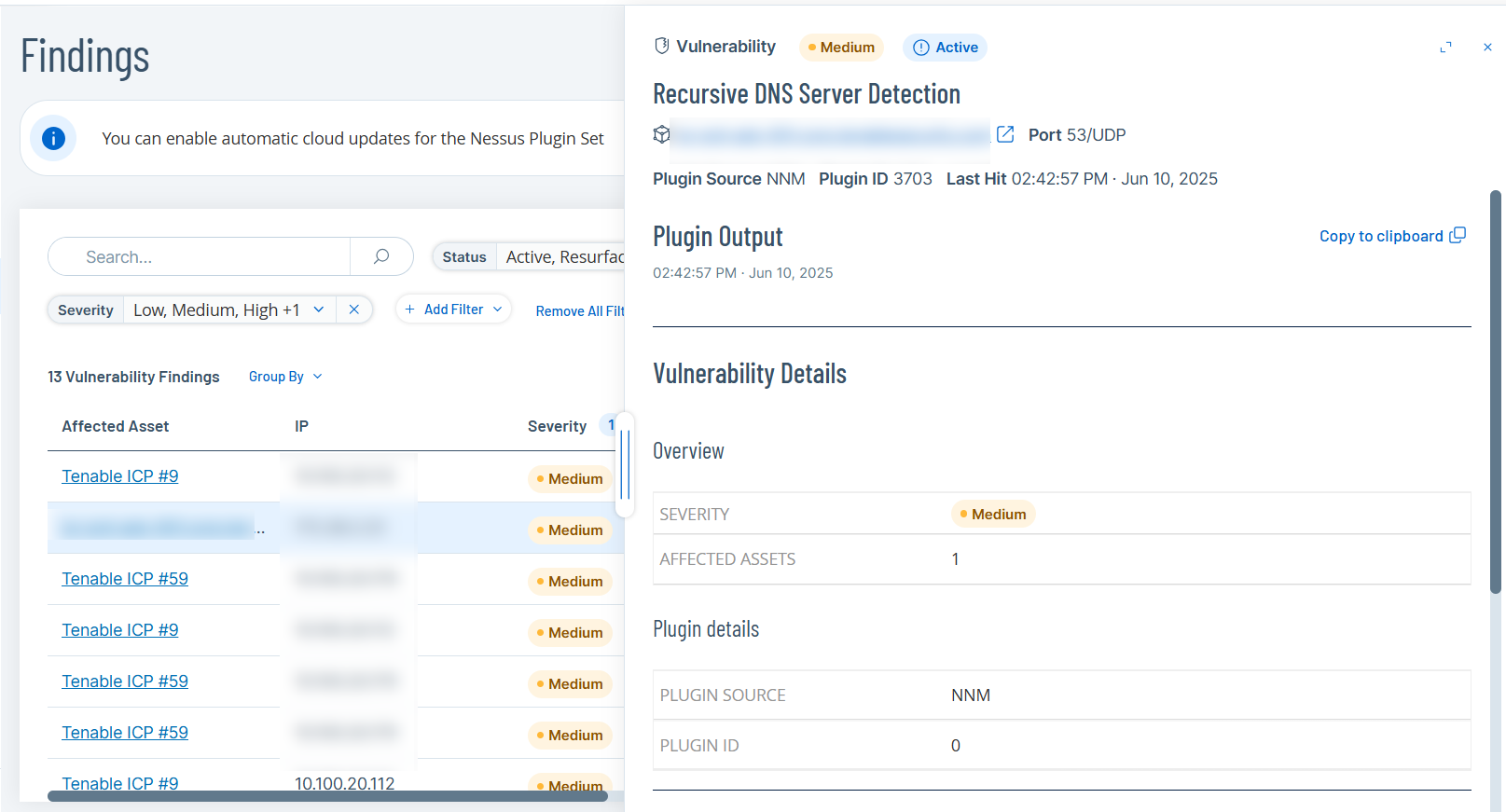
The Findings details comprises the following:
-
Plugin Output
-
Vulnerability Details
-
Affected Asset Details
To view the findings details:
-
On the Findings page, click the link in the Affected Assets or the Plugin Name column.
The Vulnerability Details panel appears.
You can view the following details:
-
Severity
-
Affected Assets
-
Plugin Source
-
Plugin ID
-
Affected Asset details such as Name, Type, Criticality, Risk Score, IP Address, Purdue Level.
-
-
To expand the Vulnerability Details panel, click the
 button in the upper-right corner.
button in the upper-right corner. -
To close the panel, click the
 button in the upper-right corner.
button in the upper-right corner. -
To view the complete asset details, in the Affected Asset section, click View Full Asset Details
 .
. -
OT Security opens a separate browser tab with the Inventory page with the single asset details.