Ransomware
Ransomware attacks that use Active Directory (AD) to propagate or perform reconnaissance require privileged access to the directory. Many organizations do not properly restrict or manage the use of privileged AD accounts, leaving systems exposed to ransomware and other types of attacks. Ensure that AD does not contain critical misconfigurations that allow attackers to deploy payloads through vulnerable systems.
-
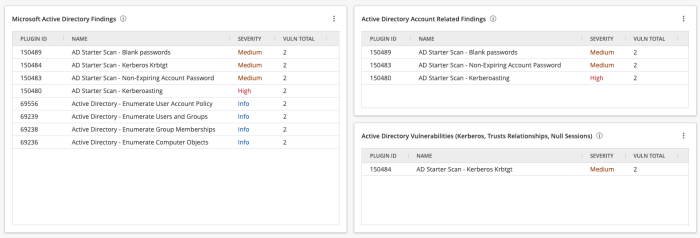
The Active Directory Account Related Findings widget in Tenable Vulnerability Management uses the Plugin ID filter for the account-related plugins contained in the Active Directory Starter Scan template: 150483,150481,150487,150480,150482,150489,150485.
-
The Active Directory Vulnerabilities (Kerberos, Trust Relationships, Null Sessions) widget uses the Plugin ID filter for the vulnerability-related plugins contained in the Active Directory Starter Scan template: 150488,150484,150486.
-
The Microsoft Active Directory Findings widget uses the CPE contains microsoft:active_directory filter to display all plugins that match the CPE.
-
All three widgets use the Severity filter for Info, Low, Medium, High, and Critical to ensure that Info plugins are displayed. The image below displays a couple Info Severity plugins for AD.
For information about how to identify AD exposures, see the AD section of the Ransomware Tenable Cyber Exposure Study and the Active Directory is Now in the Ransomware Crosshairs Tenable Blog.