Using Tenable.ad to Identify Active Directory Exposures
Ransomware attacks that use Active Directory (AD) to propagate or perform reconnaissance require privileged access to the directory. Many organizations do not properly restrict or manage the use of privileged AD accounts, leaving systems exposed to ransomware and other types of attacks. Ensure that AD does not contain critical misconfigurations that allow attackers to deploy payloads through vulnerable systems. For information about how to identify AD exposures, see the Tenable blog, How to Protect Active Directory Against Ransomware Attacks.
Reduce Privileged AD Group Membership
Microsoft recommends reducing the use of privileged accounts in an AD domain to the bare minimum. Limit membership to groups such as Domain Admins, Enterprise Admins, and Schema Admins to only staff who require privileged access, and review these groups on a regular basis.
Example: Enumerate Users and Groups
Plugin 69239 - Active Directory, Enumerate Users and Groups
Queries Active Directory for a list of Users and their Group Memberships by retrieving a list of Users and Groups via ADSI.
Tip: Audit the membership of privileged AD groups to limit membership levels.
Restrict the Use of Privileged AD Accounts
There are some technologies in Windows that can help reduce the exposure of privileged AD credentials, such as the Protected Users and Windows Defender Credential Guard groups. Follow Microsoft’s recommendations and limit the use of privileged AD accounts to devices that are secured for the purpose of administering AD.
Example: Account Operators Group
Plugin: 10901 - Microsoft Windows 'Account Operators' Group User List
Members of this group can create or modify local user accounts but cannot modify or create administrative accounts or edit user rights.
Tip: Create a set of Privileged Access Workstations (PAW) used exclusively for performing administrative tasks that require privileged access to AD.
Manage End-User Devices Using a Local Account
Organizations generally grant remote access to clients using a domain user account. Microsoft’s Local Administrator Password Solution (LAPS) tool provides a more secure method for remote support by randomizing and periodically changing the local administrator password on devices. Using a local account to support end user devices makes it difficult for attackers to compromise AD.
Example: Windows Local Administrators Group
10902 - Microsoft Windows 'Administrators' Group User List
Members of this group have complete access to the system.
Tip: Audit local administrator account passwords to make sure that each device has a unique local administrator account password. Do not use domain accounts for remote support.
Protect Privileged AD Accounts with Multi-Factor Authentication
Many organizations rely on passwords alone to protect privileged AD accounts. According to Microsoft, Multi-Factor Authentication (MFA) is proven to block 99.9% of automated attacks. MFA requires users to provide something in addition to their password, such as a biometric gesture or one-time passcode generated by an authenticator app.
Tip: Add MFA to Windows Server Active Directory. Azure MFA and other products can be used to add MFA to AD.
Following Microsoft’s security advice is a good starting point to secure AD and to stop attackers from using AD to spread ransomware. However, the server management tools built into Windows Server do not provide a way to monitor AD in real time, nor do they supply the threat intelligence needed to automate responses in an evolving threat landscape. Tenable.ad can identify security issues within AD before attackers exploit the flaws and spread ransomware. The built-in knowledge and threat intelligence helps organizations mitigate issues and remediate threats. Tenable.ad integrates with SIEMs and other security tools to proactively improve AD security, providing dynamic dashboards to provide insights that would not exist without specialized security software.
Monitor AD for Unusual Activity
Just as anti-malware software scans Windows for unusual files and processes, AD must be monitored for unusual activity. The Windows Event Log contains a great deal of information that could reveal misuse of privileged accounts and other malicious behavior. With the right data, organizations can proactively stop the spread of ransomware attacks via AD. SIEM products can be used to collect information forwarded from the Windows Server Event Log and other systems. Threat intelligence can provide an automated way for organizations to identify threats in the data collected from security events. Neither Windows Logs nor SIEM products are sufficient when used on their own.
Tip: Deploy a SIEM with threat intelligence to proactively block ransomware and other types of malware before infection of the entire network occurs.
Implement a Tiered Administration Model for AD
Microsoft recommends using a secure tiered model to organize AD resources. The model defines three tiers that serve as buffers to separate the administration of high-risk devices, such as end-user PCs and valuable servers, such as domain controllers. Tier 0 includes resources such as privileged AD accounts, domain controllers, and Privileged Access Workstations (PAWs). Tier 1 is used for member services and applications. Tier 2 is used for end-user PCs and the objects in AD that are used to manage PCs, such as help desk user accounts.
Tip: Using a phased approach, reorganize AD so that a tiered administration model is used.
AD changes, syslog changes, and Windows event logs can be correlated with threat intelligence to reveal misuse of privileged accounts and active misconfiguration exploits. This technology enables incident response teams to proactively prevent ransomware attacks from spreading via AD. Integrate this data with a SIEM to collect information forwarded from the Windows Server event logs and other systems.
AD Plugins, Scan Templates, Widgets, and Dashboards
The Active Directory Starter Scan Template contains 10 hygiene checks that are often exploited by attackers to navigate target ADs. These plugins focus on the two most common attack paths to help prevent attackers from guessing or cracking accounts, impersonating other users, and limits the ability for attackers to escalate privileges and move across domains. Specifically, these checks help organizations to identify attacks that are difficult to detect, such as Golden Ticket attacks. Along with legacy protocols, weak passwords, and accounts with elevated privileges, Golden Ticket Attacks are the most common attack against AD servers. Golden Ticket attacks, such as Kerberoasting, center around Kerberos and KRBTGT (Kerberos Ticket Granting Ticket), which are typically launched from inside the network. Kerberoasting is an attack that enables privilege exploitation, furthering the ability of an attacker to move laterally in the network.
These attacks are dangerous because the attacker does not require administrative rights. An attacker can simply request a service ticket from the Domain Controller and use password cracking tools offline to retrieve plain text credentials from vulnerable hashes. AD vulnerabilities that can be a benefit to attackers are also identified, such as Null Sessions, Primary Group ID, Weak Encryption, and Dangerous Trust Relationships.
The following plugins are part of the Active Directory Starter Scan Template and are intended to be used for preliminary analysis of AD hosts.
-
150480 AD Starter Scan – Kerberoasting A privileged account is vulnerable to the Kerberoasting attack.
-
150481 AD Starter Scan – Weak Kerberos Encryption A weak Kerberos algorithm is configured on a user account.
-
150482 AD Starter Scan – Kerberos Pre-Authentication Validation Kerberos pre-authentication is disabled on a user account.
-
150483 - AD Starter Scan - Non-Expiring Account Password Accounts with never expiring passwords.
-
150484 - AD Starter Scan - Kerberos Krbtgt KDC last password change is too old.
-
150485 AD Starter Scan – Unconstrained Delegation Dangerous Kerberos delegation is set.
-
150486 AD Starter Scan - Dangerous Trust Relationship A dangerous configuration on an outbound trust relationship is configured.
-
150487 AD Starter Scan - Primary Group Identity A potential backdoor using the Primary Group ID attribute has been found on a user account.
-
150488 AD Starter Scan – Null Sessions The Anonymous or Everyone foreign security principal is part of the Pre-Windows 2000 Compatible Access group.
-
150489 AD Starter Scan – Blank Passwords An account may have an empty password.
For more information about the issues discovered by the Active Directory Starter Scan plugins, please refer to the Tenable Blog, Find and Fix These 10 Active Directory Misconfigurations.
In addition to the AD plugins and scan template, the Getting Started with Active Directory Tenable Vulnerability Management Dashboard, is available to quickly discover and analyze basic AD weaknesses. The AD plugins and scan template are available in Nessus Essentials, Nessus Professional, Tenable Security Center, Tenable Vulnerability Management, and Tenable One.
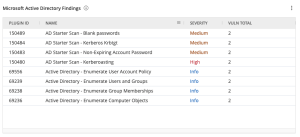
The Microsoft Active Directory Findings widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays Active Directory vulnerabilities using the CPE filter for cpe:/a:microsoft:active_directory.