Tenable Web App Scanning
Tenable Web App Scanning is a dynamic application security testing application which crawls a running web application through the front end to create a site map containing all the pages, links, and forms. Once this site map is created, the data is interrogated to identify any vulnerabilities in the application, custom code, or third-party components.
Web application scanning is of critical importance because users typically access these applications from a browser over the internet. Web applications exist on remote servers or in cloud environments, and data is transmitted over public networks. Web application security is a critical aspect to ensure the confidentiality, integrity, and availability of web applications. Web applications are essential for businesses and individuals, making them lucrative targets for cyber criminals. Attackers focus on exploiting vulnerabilities within web applications to exfiltrate sensitive data, deface web sites, and launch denial of service attacks.
Web applications are commonly susceptible to Cross-Site scripting attacks (XSS), SQL Injections, Cross-Site Request Forgery (CSRF), Insecure Object Reference, and security misconfigurations. Web application security is an ongoing process and requires a multi-layered approach. As threats evolve over time, staying informed about the latest security best practices and keeping applications updated is crucial to protect both the organization and its users from potential harm.
The Open Web Application Security Project (OWASP) is a non-profit organization focused on improving the security of software. Their OWASP Top 10 list highlights the most critical web application security risks, providing guidance on how to prevent and mitigate these vulnerabilities. OWASP has dedicated itself to a release cadence of every three years to respond to the evolving web application security market and address the most common web application vulnerabilities.
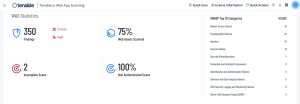
Tenable Web App Scanning analyzes web applications and provides deep-dive data on OWASP top 10 vulnerabilities, component vulnerabilities, injections, and in-depth informational details to help organizations identify security concerns in their web applications. The Tenable Web App Scanning landing page for Tenable Vulnerability Management includes some high-level statistics, as well as a readout of web application vulnerabilities as they apply to the OWASP Top 10 list.
In addition to the OWASP data, discovered domains are displayed in the Assets view and a new scan can be launched from any discovered domain record. The navigation bar at the top of every view enables users to quickly launch scans by clicking on the Quick Scan button or add a dashboard from the Quick Actions button. Web application assets support AES & ACR scoring, along with Tenable Vulnerability Priority Rating (VPR), which is a dynamic score that helps organizations to prioritize and strategize remediation based on the immediate risk a vulnerability poses. Updated scan export and new scan import capabilities enables users to import exported scans and see debugging information in web application scan exports to assist with troubleshooting.
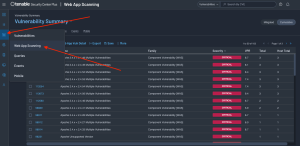
Tenable Web App Scanning vulnerability data within Tenable.sc is available by selecting the Analysis tab, then selecting Web App Scanning to view the web application vulnerability analysis tab.
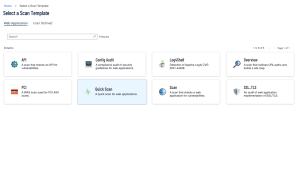
Tenable Web App Scanning contains pre-built templates that assist with common tasks such as:
-
Rapid discovery of common cyber-hygiene issues.
-
Detection of improperly issued or soon to expire SSL/TLS Certificates.
-
Identification of misconfigured web servers.
Summary of Web App Scanning Templates
-
Scan: The complete set of available checks; all other pre-built templates are a subset of this template, other than the API scan.
-
Overview: A scan that outlines URL paths and builds a site map.
-
PCI: A special template used as part of the attestation offering Tenable provides for the Payment Card Industry (PCI) security standards. Note: Only submissions to attestation consume PCI licenses, otherwise this operates as a simplified version of the “Scan” template.
-
SSL/TLS: A health check scan focused on the current state of the web server encryption settings and certificate state such as the remaining time on the certificate.
-
Config Audit (Tenable Vulnerability Management Only): A compliance audit providing detection of externally viewable web server settings, which external audit providers commonly review, to evaluate the health of a security program.
-
API Scan: A special template requiring additional configuration to describe the application programming interface (API), so that the scanner can successfully detect relevant vulnerabilities. This includes some of the same tests as the “Scan” template but adds others unique to API endpoints.
-
Quick Scan: A simplified version of the “Scan” template with several of the active tests removed to lower the impact and speed up the scan.
-
Log4Shell: A scan to specifically detect Apache Log4J (CVE-2021-44228).