Risk Prioritization
Asset Criticality Rating (ACR) establishes the priority of each asset based on indicators of business value and criticality. ACR is based on several key metrics such as business purpose, asset type, location, connectivity, capabilities and third-party data. ACRs range from 0 to 10. Assets with a low ACR are not considered business critical. Assets with a high ACR are considered to be the organization’s most critical and carry the greater business impact if compromised. This section displays risk by ACR, Common Vulnerability Scoring System (CVSS), exploitability by Attack Vector and Framework.
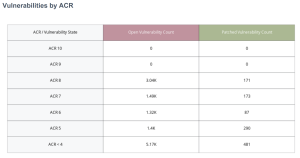
Vulnerabilities by ACR
The Vulnerabilities by ACR widget enables organizations to view risks that are currently open, along with those that have been patched. The information is ranked by ACR score to demonstrate progress of risk remediation efforts, with the most critical assets at the top of the table along with a count of open and patched vulnerabilities. A large count of open vulnerabilities on critical assets indicates that the organization presents a higher risk of a data breach. A high count of patched vulnerabilities demonstrates that the organization is addressing cyber risk promptly, and has a mature vulnerability management program.
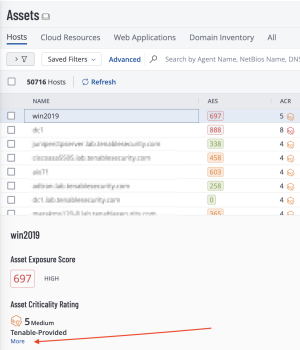
To view the ACR key driver information for any asset, Navigate to the Assets page and select an asset to view the asset details. In the lower left corner of the assets details page reference the Asset Criticality Rating information and click More.
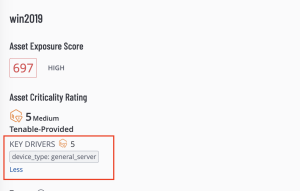
The key drivers will be displayed.
Tenable assigns an ACR to each asset on the network to represent the relative criticality of the asset as an integer from 1 to 10 . A higher ACR indicates higher criticality. Lumin customers have the ability to adjust the default Tenable ACR to more accurately reflect organizational risk. Please refer to the Edit an ACR Manually page for more information.
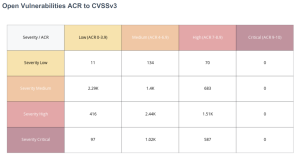
Open Vulnerabilities ACR to CVSSv3
Leveraging ACR with CVSS provides an improved risk-based view of the attack surface, and a more accurate representation and prioritization of risk. In the Open Vulnerabilities ACR to CVSSv3 widget, CVSS Base Score is supplemented with ACR. CVSSv3 Base Scores and ACR Scores are used in this heat map with the bottom-right corner containing the most critical concerns. Organizations with a robust vulnerability management program will have the highest counts in the top left portion, indicating that vulnerabilities identified have the least severity, and least potential impact to the organization. Vulnerabilities in the last row and far right column represent the most severe concerns, with the bottom right indicating the highest priority concerns. These numbers can help drive prioritization efforts in compliance with SLAs.
The Common Vulnerability Scoring System (CVSS) is a metric from 0 to 10 that is assigned by the product vendor or the National Vulnerability Database (NVD) to indicate the severity of a vulnerability. CVSS scores are produced by the entity or organization that produces and maintains the product or a third party scoring on their behalf. CVSS Base Scores alone are not a measure of business risk nor do CVSS values account for real-world risk or asset criticality within an organization’s specific environment as scores are not likely to change once published.
Tenable recommends supplementing CVSS Base Scores with another temporal or environmental score to more accurately measure severity and rank threats. Such factors may include the risk of monetary loss due to breach, risks of damage or threat to life or property.
Temporal metrics are metrics that change over time. Factors that can alter the Temporal score are: Exploit Code Maturity, Remediation Level, and Report Confidence. If a vendor has created a patch that is widely available, the Temporal score will be lower, likewise if known exploits are widely available, the score will be higher. Environmental metrics are specific to the organization, and include attributes related to business criticality of the exposed asset, and any mitigation measures or compensating controls that are in place. Organizations can modify Environmental attributes if compensating controls are in place, thereby modifying the overall CVSS Score. The core concern is that incorrectly used Environmental score changes will have a significant impact. For example:
A vulnerability with a CVSS Base Score of 9.9 (Critical) and a CVSS Temporal Score of 9.9 (also Critical) will have an overall score of 9.9. Combine these scores with CVSS Environmental score of 3.2 and the Overall Score will be reduced to 3.2 (Low). This is an extreme example, but illustrates what may occur if the CVSS Environmental score is modified incorrectly.
These critical pieces of information are included in ACRs, and help organizations to effectively prioritize remediation and enhance CVSS Base scores.