Encryption of Data in Transit
Data in transit is considered to be data that is moving across a network. The NIST Special Publication titled “Guidelines for the Selection, Configuration, and Use of Transport Layer Security (TLS) Implementations” provides guidance to cryptographically protect data in transit. This Special Publication provides guidance for the selection and configuration of TLS protocol implementations, leveraging Federal Information Processing Standards (FIPS) and NIST-recommended cryptographic algorithms. This section discusses dashboard templates and plugins related to encryption of data in transit, such as certificates and protocols.
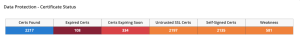
The Data Protection - Certificate Status Tenable Security Center dashboard component template uses many of the plugins described in this section to display certificate information for scanned assets.
Certificate Information: Displays the SSL certificate information.
-
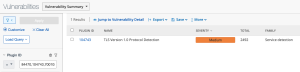
10863 | SSL Certificate Information
SSL Certificate Information Detection in Tenable Vulnerability Management
Protocol Detection: The remote service encrypts traffic using a protocol with known weaknesses.
- 8184 | TLS v1.2 Traffic Negotiation Detection
- 8185 | TLS v1.1 Traffic Negotiation Detection
- 8549 | SSLv3 Protocol Detection
- 9129 | SSLv2 Client Connection Request
- 20007 | SSL Version 2 and 3 Protocol Detection
- 56984 SSL / TLS Versions Supported
- 84470 | TLS Version 1.0 Protocol Detection (PCI DSS)
- 104743 | TLS Version 1.0 Protocol Detection
- 121010 | TLS Version 1.1 Protocol Detection
- 136318 | TLS Version 1.2 Protocol Detection
- 138330 | TLS Version 1.3 Protocol Detection
- 139414 | TLS Version 1.1 Protocol Detection (PCI DSS)
- 700105 | TLS 1.0 Detection
- 700106 | TLS 1.1 Detection
- 700107 | TLS 1.2 Detection
- 700108 | TLS 1.3 Detection
- 700110 | TLS 1.1 Detection (UDP)
- 700111 | TLS 1.2 Detection (UDP)
- 700112 | SSL/TLS Detection
- 700113 | SSL/TLS Detection (UDP)
Note: There are several non-informational plugins that detect deprecated TLS and SSL protocols, such as the following:
Note: The results from the following plugins can often help find hidden services running TLS.
- 22964 | Service Detection (HTTP Banner)
- 25221 | Remote listeners enumeration (Linux / AIX)
- 83875 | SSL/TLS Diffie-Hellman Modulus <= 1024 Bits (Logjam)
- 110483 | Unix / Linux Running Processes Information
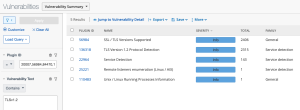
TLS Version 1.x Detection in Tenable Vulnerability Management
Certificate Issues & Concerns: Checks for common issues or concerns with certificates. Some issues, such as no certificate, Common Name, or Subject are not required, but offer broader compatibility if used. Other items, such as Self-Signed certificates, may present larger concerns if used in production environments.
- 35297 | SSL Service Requests Client Certificate
- 45410 | SSL Certificate 'commonName' Mismatch
- 45411 | SSL Certificate with Wrong Hostname
- 51356 | Well-known SSL Certificate Used in Remote Device
- 56284 | SSL Certificate Fails to Adhere to Basic Constraints / Key Usage Extensions
- 56471 | SSL Certificate Chain Not Sorted
- 56472 | SSL Certificate Chain Contains Unnecessary Certificates
- 57571 | SSL Certificate Chain Analysis
- 57582 | SSL Self-Signed Certificate
- 121008 | SSL / TLS Certificate Known Hard Coded Private Keys
- 139546 | Improper Check for Certificate Revocation (FG-IR-19-144)
- 139547 | Improper Check for Certificate Revocation (FG-IR-19-144)
- 159544 | SSL Certificate with no Common Name
- 159545 | SSL Certificate with no Subject
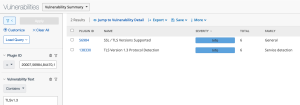
Certificate Issues & Concerns displayed in Tenable Vulnerability Management
Black Listed Certificate: An SSL certificate has been detected that is either fraudulent, no longer secure due to leaked or compromised private keys, or was issued from a Certificate Authority that is considered to be untrustworthy.
-
52963 | Blacklisted SSL Certificate
Certificate Expiration/Revocation: Certificates that are active that are not within their validity period, are expired, or will be expiring soon.
- 15901 | SSL Certificate Expiry
- 42980 | SSL Certificate Expiry - Future Validity
- 42981 | SSL Certificate Expiry - Future Expiry
- 72459 | Certificate Revocation List Expiry
- 83298 | SSL Certificate Chain Contains Certificates Expiring Soon
- 121009 | SSL Certificate Validity - Duration
Certificates that are not yet valid or have an invalid duration set
Certificates that will expire soon, or have expired
Certificate Weaknesses: Certificates that contain weak RSA keys, RSA keys with fewer than 2048 bits, are using a weak hashing algorithm, or are susceptible to spoofing.
- 35291 | SSL Certificate Signed Using Weak Hashing Algorithm
- 42053 | SSL Certificate Null Character Spoofing Weakness
- 60108 | SSL Certificate Chain Contains Weak RSA Keys
- 73459 | SSL Certificate Chain Contains RSA Keys Less Than 2048 bits (PCI DSS)
- 86067 | SSL Certificate Signed Using SHA-1 Algorithm
- 95631 | SSL Certificate Signed Using Weak Hashing Algorithm (Known CA)
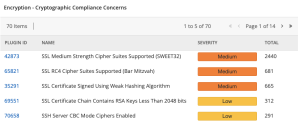
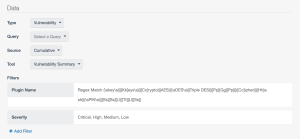
Tenable provides dashboard component templates in Tenable Security Center to identify deprecated cryptographic protocols of data in transit, such as the Encryption - Cryptographic Compliance Concerns component in the image below.
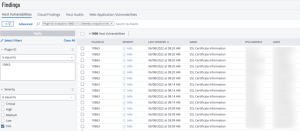
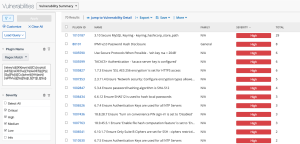
The Encryption - Cryptographic Compliance Concerns Tenable Security Center dashboard component template uses the filter combination below, as shown in the following two images:
- Plugin Name Regex Match (\skey\s)|([Kk]eys\s)|([Cc]rypto)|(AES)|(\sDES\s)|(TripleDES)|([Pp][Gg][Pp])|([Cc]ipher)|([Hh]ash)|(\sPIN\s)|([Ss][Ss][Ll)|[Tt][Ll][Ss])
- Severity: Critical, High, Medium, Low
Component Configuration for Encryption - Cryptographic Compliance Concerns:
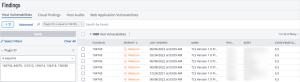
Details when clicking View Data from the Encryption - Cryptographic Compliance Concerns component:
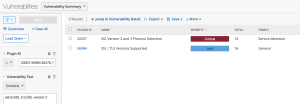
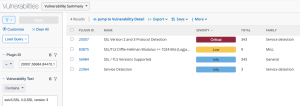
The SSL/TLS Discovery - SSL/TLS Vulnerabilities By Type dashboard component template in the Tenable Security Center feed displays a count of systems with SSLv2, SSLv3, and TLS discovered actively with Nessus and passively with Nessus Network Monitor.
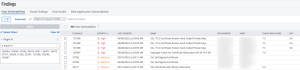
The following images show detailed results of the cells in the Systems column of the SSL/TLS Discovery - SSL/TLS Vulnerabilities by Type Tenable Security Center dashboard component displayed above. The Systems column displays the number of systems that meet the search criteria, rather than the total number of vulnerabilities that meet the search criteria. The Active and Passive columns display the number of vulnerabilities that meet the search criteria. These columns use the Plugin ID filters for only Active or Passive plugins, respectively. The Systems column uses both Active and Passive plugins to show all systems that meet the criteria.
SSLv2 [Systems Column]:
- Plugin ID = 20007,56984,84470,104743,22964,25221,83875,110483,121010,136318,138330,139414,8185,8184,8549,9129,700105,700106,700107,700108,700110,700111,700112,700113
- Vulnerability Text contains sslv2,SSL 2.0,SSL version 2
SSLv3 [Systems Column]:
- Plugin ID = 20007,56984,84470,104743,22964,25221,83875,110483,121010,136318,138330,139414,8185,8184,8549,9129,700105,700106,700107,700108,700110,700111,700112,700113
- Vulnerability Text contains sslv3,SSL 3.0,SSL version 3
TLS 1.0 (Deprecated) [Systems Column]:
-
Plugin ID = 84470,104743,700105
-
Vulnerability Text Contains TLSv1
TLS 1.1 [Systems Column]:
-
Plugin ID = 20007,56984,84470,104743,22964,25221,83875,110483,121010,136318,138330,139414,8185,8184,8549,9129,700105,700106,700107,700108,700110,700111,700112,700113
-
Vulnerability Text Contains TLSv1.1
TLS 1.2 [Systems Column]:
-
Plugin ID = 20007,56984,84470,104743,22964,25221,83875,110483,121010,136318,138330,139414,8185,8184,8549,9129,700105,700106,700107,700108,700110,700111,700112,700113
-
Vulnerability Text Contains TLSv1.2
TLS 1.3 [Systems Column]:
-
Plugin ID = 20007,56984,84470,104743,22964,25221,83875,110483,121010,136318,138330,139414,8185,8184,8549,9129,700105,700106,700107,700108,700110,700111,700112,700113
-
Vulnerability Text Contains TLSv1.3