Removable Media Controls
Data stored on removable media is susceptible to unauthorized disclosure and needs to be secured. Removable media, by design, is designed to be portable and is particularly susceptible to data loss. This section describes security concerns for removable media and how Tenable products can determine if controls are in place that align with the organization’s policy on removable media.
Removable media has both “read” and “write” access controls. Many organizations restrict write access to prevent data from being written to removable media. Exceptions may be made on a case by case basis.
If write access is permitted, encryption can be enforced at the file or device level, depending on the solutions in place and the company policy. The NIST Special Publication 800-111, “Guide to Storage Encryption Technologies for End User Devices,” provides guidance for encrypting data on removable media.
Data Loss Prevention controls can be used to prevent particular types of data (such as credit card numbers) from being written to removable media, even if write access is permitted.
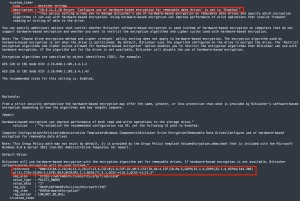
The following image displays an audit check from the CIS_MS_Windows_10_Enterprise_Bitlocker audit file, which ensures that hardware-based encryption for removable data drives is enabled.
Unix-based systems support file system mount options that can provide additional security controls, such as ‘nodev,’ ‘noexec,’ and ‘nosuid,’ as described below:
-
nodev – Restricts character and blocks special devices from being accessed on the filesystem. Character and block special devices are those that permit access to a file that is attached to a device that is not part of the file system, such as a USB drive. Use the ‘nodev’ mounting option for filesystems that contain sensitive data to prevent data exfiltration. Removable media containing character or block special devices could be used to bypass security controls by allowing non-root users to access sensitive device files such as /dev/kmem or raw disk partitions.
-
noexec – Prevents executable files from running on a file system. Use the ‘noexec’ option for removable media to prevent malware from being run when the media is attached to the system.
-
nosuid – Disables the ability to elevate privileges on a file system. Use the ‘nosuid’ option for world-writable file systems and removable media.
The Data Protection - Removable Media noexec, nosuid, nodev Compliance Tenable Security Center dashboard component template uses the following filters:
-
Plugin Type: Compliance
-
Plugin Name Regex Match (nodev.*[Rr]emovable [Mm]edia)|([Rr]emovable [Mm]edia.*nodev)|(noexec.*[Rr]emovable [Mm]edia)|([Rr]emovable [Mm]edia.*noexec)|(nosuid.*[Rr]emovable [Mm]edia)|([Rr]emovable [Mm]edia.*nosuid)
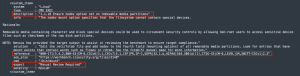
The following image displays an audit check from the CIS_CentOS_8_Server audit file, which displays the mount options that are used on the file system.
Note: This is a manual check, requiring a review of the output by IT staff who are familiar with the correct settings for the system. See "Manual Review Required" in the expect section of the image.
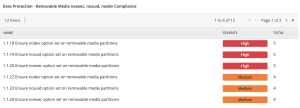
Tenable provides dashboard component templates in the Tenable Security Center feed, such as the Removable Media and Content Audits - CDROM, Floppy, Other Storage Audit component shown below.
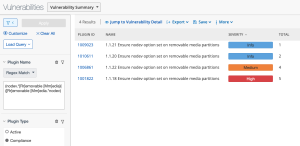
In Tenable Security Center, the audit check name corresponds to the Plugin Name, so searches can be performed using the Plugin Name filter. For example, the search below can be used in Tenable Security Center to find results from audit scans [also called compliance scans] with check names containing ‘removable media’ and ‘nodev’ from various audit files.
-
Plugin Name Regex Match (nodev.*[Rr]emovable [Mm]edia)|([Rr]emovable [Mm]edia.*nodev)
-
Plugin Type: compliance
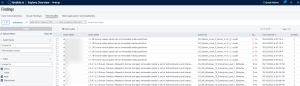
In the Tenable Vulnerability Management Host Audits Findings, the Audit Name filter can be used to display results from various audit files. For example, the search below displays any scan results from audit checks containing "Removable Media."
-
Audit Name is equal to *Removable media*