Verifying Data Protection Controls
The National Institute of Standards (NIST) Special Publication 800-53 provides comprehensive guidance for a secure infrastructure. This section describes NIST guidance for data protection controls and how Tenable solutions help validate that appropriate encryption controls are implemented within the organization.
The NIST Cybersecurity Framework (CSF) is a control framework, whose high level controls align with ISO 27001, NIST SP 800-53, and others. The Cybersecurity Framework’s prioritized, flexible, and cost-effective approach helps to promote the protection and resilience of critical infrastructure and other sectors important to the economy and national security. Many regulating bodies accept evidence documentation of compliance with the NIST CSF as assurance that the organization has effective controls in place to meet their security requirements. The HIPAA Security Rule Crosswalk to NIST Cybersecurity Framework is an example of alignment with NIST.
Tenable audit checks contain a reference field that points to specific controls in a standard (ISO 27001), framework (NIST Cybersecurity Framework), or regulation (HIPAA) and is used by nearly all plugins. Any external reference can be identified using the Cross References field. References can be used to search or filter in Tenable Security Center. For example, the following References define requirements for the encryption of data at rest:
- 800-171 - 3.13.16
- 800-53 - SC-28
Security Requirement 3.13.16 in the NIST Special Publication 800-171 Revision 2 provides guidance to protect the confidentiality of Controlled Unclassified Information (CUI) at rest and maps to Security Control SC-28 of NIST Special Publication 800-53, which provides guidance for Protection of Information at Rest. Security Requirements specify what action needs to be taken. For example, HIPAA requires that Personal Health Information (PHI) be encrypted when traversing internal networks. Security controls specify how to meet the requirement, such as “enable switch to switch encryption on internal network segments.”
Data at rest is data that is stored on a device and not in process or transmission. Encryption requirements for data at rest depend on the sensitivity of the data and other protection controls that may be in place. For example, data stored on mobile devices has a greater risk since the device is exposed to unsecured networks. Data stored on secure servers in a protected data center has a lower risk of unauthorized access. NIST Special Publication 800-171 provides recommended requirements to protect the confidentiality of controlled unclassified information.
The 800-53:SC-28 mapping aligns with the following regulatory controls:
- 800-171: NIST 800-171 (Standard)
- csf: NIST Cybersecurity Framework (CSF) (Framework)
- hipaa: HIPAA (Regulation applying a standard)
- isoiec-27001: ISO 27001 (Standard)
- pci-dss: PCI-DSS (Standard)
- cobit5: COBIT (Standard)
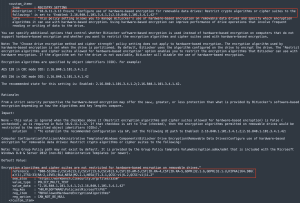
Control mappings, shown as “reference” in the following audit check image, identify encryption algorithms and cipher suites that the audit check verifies. Audit checks can map to multiple controls across multiple standards. For example, the audit check shown in the image below verifies compliance with the following controls:
- NIST SP 800-53 - RA-2
- CIS Critical Security Controls (CSC) v6 - 13.2
- CSC v7 - 13.6
- CSC v8 -3.6
- CSF - ID.AM-5,ID.RA-4,ID.RA-5
- General Data Protection Regulation (GDPR) - 32.1, 32.1.d
- HIPAA - 164.306(a)(1)
- Overview of IT Security Risk Management: A Lifecycle Approach (ITSG-33) - RA-2
- LEVEL|BitLocker Automated (BLA)
- National Electronic Security Authority (NESA) - M2.2.1, T1.3.1
- QCSC-v1|6.2
- QCSC-v1|11.2"
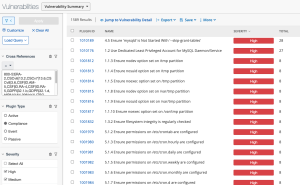
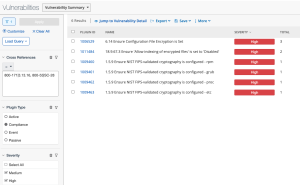
The Data Protection - Confidentiality of Protected Information Concerns Tenable Security Center dashboard component template uses the Cross References mentioned above in the filters for the component, shown in the next two images:
- Cross References = 800-53|RA-2,CSCv6|13.2,CSCv7|13.6,CSCv8|3.6,CSF|ID.AM-5,CSF|ID.RA-4,CSF|ID.RA-5,GDPR|32.1.b,GDPR|32.1.d,HIPAA|164.306(a)(1),ITSG-33|RA-2,LEVEL|BLA,NESA|M2.2.1,NESA|T1.3.1,QCSC-v1|6.2,QCSC-v1|11.2
- Plugin Type: Compliance
- Severity: High, Medium
The table below displays the Cross Reference display formats in Tenable Security Center and Tenable Vulnerability Management:
| In Tenable Security Center, the Cross References are displayed in Scan Results and Vulnerability Analysis in the format Type:ID: | In Tenable Vulnerability Management, the Cross References are displayed in a Reference Information table under Host Audit Details: |
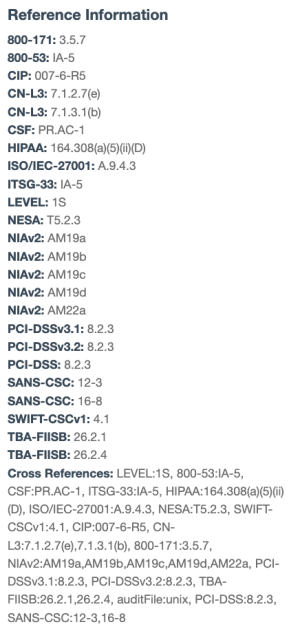
|

|
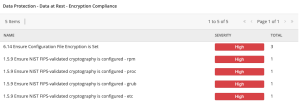
The expected filter format syntax for searching, filtering, and querying in Tenable Security Center <XREF TYPE>|<XREF ID> uses a pipe, “|”, rather than a colon, “:”. In the GUI the XREF Type and ID are separated by a ":". Please note in the filter, you must use a pipe, "|". Using an example from above, 800-171 is the XREF Type, and 3.13.16 is the XREF ID. A search with proper syntax in Tenable Security Center that matches any item in the comma separated list is shown below, as used in the Data Protection - Data at Rest - Encryption Compliance Tenable Security Center dashboard component template.
Note: Spaces can be included or omitted after commas.
- Cross References = 800-171|3.13.16, 800-53|SC-28
- Plugin Type: Compliance
- Severity: Medium, High
The following table displays valid Cross References that can be found in Tenable Vulnerability Management and Tenable Security Center:
| Non-Compliance | Compliance |
|---|---|
|
ALAS,ALSA,APPLE-SA,AUSCERT,BID,CERT,CERT-CC, |
800-171,800-53,8500.2,BSI-100-2,CAT,CCE,CCI,CCM-3,CIP,CIS_RECOMMENDATION,CN-L3,COBIT5,CSCV6,CSCV7,CSCV8,CSF,DISA_BENCHMARK,GDPR,GROUP-ID,HIPAA,ISOIEC-27001,ITSG-33,LEVEL,NESA,NIAV2,OPENSTACK,PCI,PCI-DSS,PCI-DSS-2.0,PCI-DSS-3.0,PCI-DSSV3.1,PCI-DSSV3.2,QCSC-V1,RULE-ID,SANS-CSC,STIG-ID,STIG-LEGACY,SWIFT-CSCV1,TBA-FIISB,VMWARE-ID,VMWARE-PROFILE,VULN-ID |
Below are some Cross Reference search examples that can be used in Tenable Security Center (xref refers to the Cross References filter):
- xref = 800-53|AC*
- Would be a match for AC-1, AC-2, etc.
- xref = 800-53|AC-1
- Would be a match for AC-1, but not AC-11
- xref = 800-53|AC-1*
- Would be a match for AC-1, AC-11, AC-12, etc.
- xref = 800-53|SC-7 (5),800-53|SC-8
- Would match 800-53|SC-7 (5) and 800-53|SC-8
- xref = 800-53|SC-7*
- Would match 800-53|SC-7 (5), 800-53|SC-7, 800-53|SC-71, etc.
- xref = 800-53|*
- Would match anything with 800-53 any xref ID
- xref = 800-53|*7
- Would match anything with XREF ID ending in 7
- xref = 800-53|S*-7
- Would match anything with XREF ID beginning with S and ending with "-7"