Additional Resources: Exposure Management
Exposure Management is the process of identifying, assessing, and mitigating risks and vulnerabilities within an organisation's environment to protect against threats. By adopting exposure management, organisations stay ahead of evolving threats and maintain operational resilience. This is critical in environments where there is a mix of on-premises, cloud, and IoT systems.
In this section the following Tenable products will be highlighted:
-
Tenable One
-
IoT and Tenable One
-
Tenable Vulnerability Management
-
Tenable Security Center
Tenable One
Tenable One is an exposure management platform, designed to allow customers to gain visibility across the entire modern attack surface. Tenable One focuses efforts to prevent likely attacks, and accurately communicate cyber risk to optimise business performance.
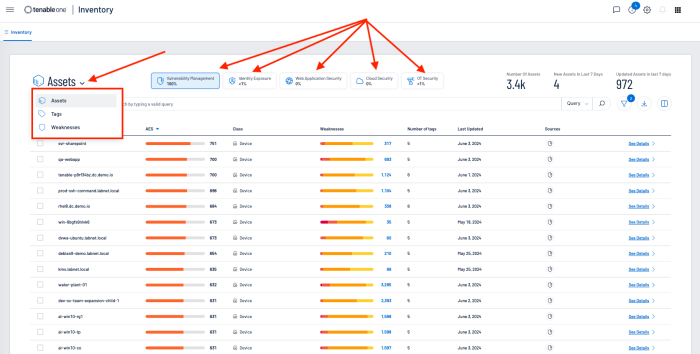
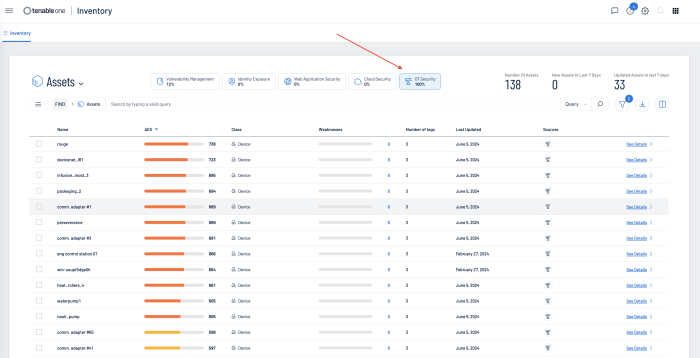
Tenable One Asset Inventory provides a comprehensive view of all assets across the entire attach surface. Sensors pull data from multiple applications across the platform, providing details on all known systems. At the highest level on the Asset Inventory page is shown the Number of Assets identified, New Assets identified in the last 7 days, and assets that have been updated in the last 7 days. Buttons allow you to select any combination of assets (Vulnerability Management, Identity Exposure, Web Application Security, Cloud Security, OT Security).
Displayed in the main body of the page is the Asset, the Asset Exposure Score, Class of device, Weakness, Tags, Last Update Date, Source, and Details. Selecting the Asset drop-down also allows all assets to be displayed by Tag or by Weakness. Weakness is a Common Vulnerability and Exposure (CVE), which is a reference method for publicly known vulnerabilities, maintained by the MITRE Corporation, and funded by the US National Cyber Security Division and the US Department of Homeland Security. Assets can be grouped together, or displayed separately within Vulnerability Management, Identity Exposure, Web Application Security, Cloud Security, and OT Security, by selecting (or deselecting the corresponding icon).
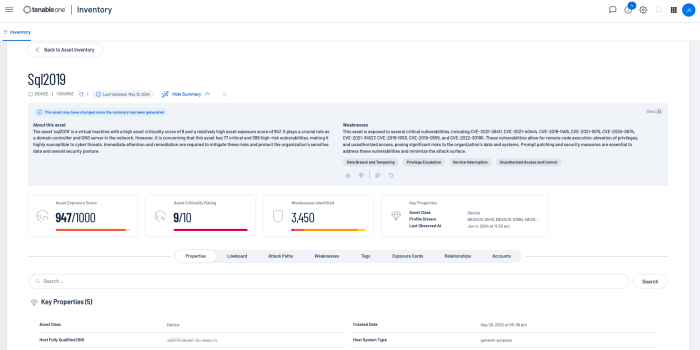
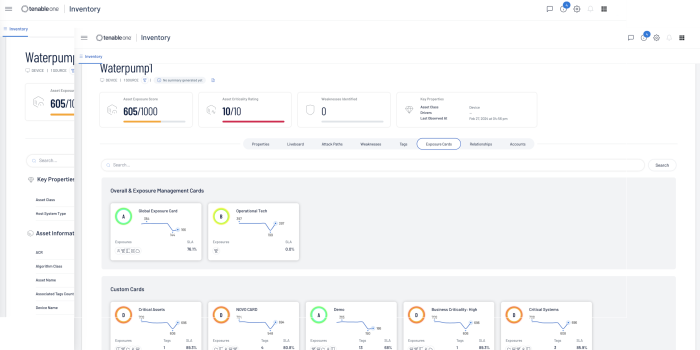
Drilling down into the Asset details provides a wealth of information, including insights into the assets properties, Attack Paths, Weaknesses, Exposure Cards, Relationships, and Accounts. For more information on Tenable One features and benefits, go here.
For more information on Tenable One, click here.
IoT and Tenable One
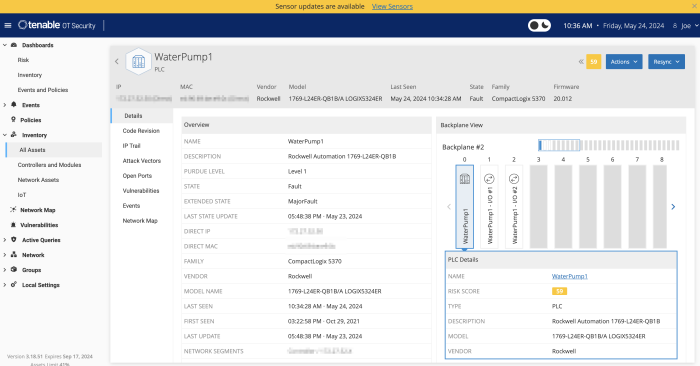
Tenable OT Security maps out assets as well as communication paths. A complete visibility of assets across the environment (IT and OT) is available. Tenable OT Security uses active sensors that can be deployed deep within network segments, to sniff packets and identify the devices communicating on the wire. Once there is an inventory of the assets on the network, Tenable OT Security sends active queries in a safe and secure manner to discover the remaining dormant devices. This discovery process is called hybrid discovery and Tenable is the first to use this methodology for effective asset inventory and mapping.
Information Technology (IT) primarily deals with data processing and communications. Operational Technology (OT) generally refers to the hardware and software that is used to monitor and control devices and processes within industry, manufacturing, energy, transportation, and utility environments. OT can also include industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, programmable logic controllers (PLC), and other devices used to monitor and control industrial processes.
As technology advances and IT-OT systems converge, new challenges are created and these systems become more vulnerable to cyber threats. Safety and security become increasingly important. Security teams can now get visibility into device make and model, as well as firmware version and status.
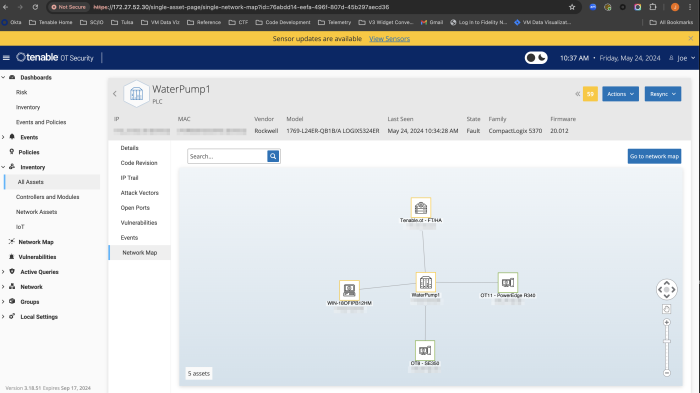
Connections can also be mapped to other devices on the network.
Utilising Tenable One, OT Assets can be displayed by selecting the OT Security icon.
Clicking on the See Details link to the right of the page presents additional information on the asset, such as properties, Attack Paths, Weaknesses, Exposure Cards and more.
Digital Operational Resilience Testing
Digital Operational Resilience Testing refers to the practices and procedures implemented to ensure that systems and infrastructure can withstand, recover, and adapt to disruptions, cyber attacks, and other challenges. In addition to the Articles previously listed, the following DORA Articles are related to Digital Operational Resilience Testing efforts:
CHAPTER IV, Digital operational resilience testing
-
The digital operational resilience testing programme shall include a range of assessments, tests, methodologies, practices and tools to be applied in accordance with Articles 25 and 26:
-
Article 24.3, Financial entities, other than microenterprises, shall follow a risk-based approach.
-
Article 25.1, the execution of appropriate tests, such as vulnerability assessments and scans, open source analyses, network security assessments, gap analyses, physical security reviews, questionnaires and scanning software solutions, source code reviews where feasible, scenario-based tests, compatibility testing, performance testing, end-to-end testing and penetration testing.
-
Article 26.2, Financial entities shall identify all relevant underlying ICT systems, processes and technologies supporting critical or important functions and ICT services.
-
Periodic risk assessment is the primary tool for engineers and security analysts to manage risks by maintaining good cyber hygiene, reducing operational downtime and mitigating the potential impact of threats.
A risk assessment is a systematic process of identifying and evaluating identified risks that may impact organisations operations or assets. There are five main steps to performing a risk assessment: Identification of the hazards, Assessing the risks, Controlling the risks, Recording the findings, and Reviewing the controls. Once the vulnerabilities have been identified, the organisation needs to assess the identified risks, and prioritise the remediation efforts. Vulnerabilities should be assessed on their potential impact, and strategies should be developed to mitigate or manage these risks effectively.
Risk assessments are critical for helping organisations make informed decisions, prioritising resources, and proactively managing risks, while minimising potential negative impacts. While the vulnerability management section deals specifically with identification aspects, this section provides guidance to organisations on how to assess and prioritise risks which have been identified within the environment.
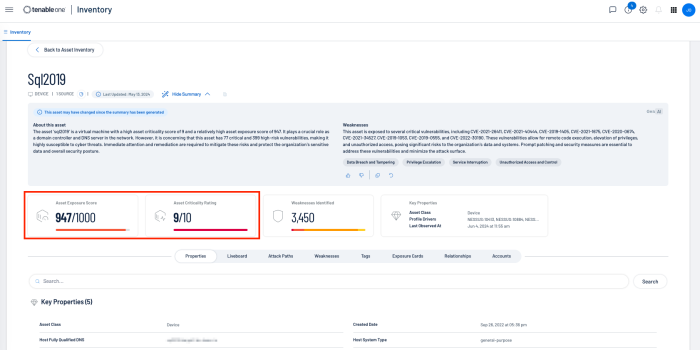
When dealing directly with assets, Tenable assists organisations prioritise risk by assigning an Asset Criticality Rating (ACR), and Asset Exposure Score (AES). When dealing with vulnerabilities a Vulnerability Priority Rating (VPR) is assigned. The ACR establishes the priority of each asset based on indicators of business value and criticality. ACR is based on several key metrics such as business purpose, asset type, location, connectivity, capabilities, and third-party data.
Within Tenable One, AES and ACR can be best viewed from the See Details link on the Assets page.
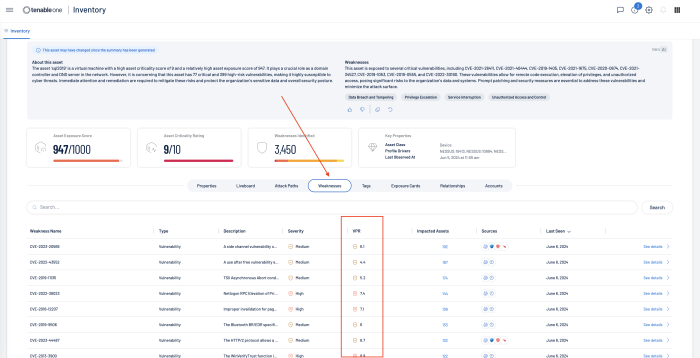
Tenable VPR scores can be best viewed from the See Details link on the Assets page, and then by selecting Weakness.
For more details on AES, ACR, and VPR, please see the Risk Assessment section of the NIS 2 Cyber Exposure study.
Scan Health
For more details on AES, ACR, and VPR, please see the Risk Assessment section of the NIS 2 Cyber Exposure study.
-
Article 9.1, Financial entities shall continuously monitor and control the security and functioning of ICT systems and tools
The Authentication Summary dashboard for Tenable Vulnerability Management and the Authentication Summary dashboard for Tenable Security Center brings together plugins used to verify successful authentication of assets during vulnerability scans, providing security administrators visibility into areas of concern so the appropriate actions can be taken.
Authentication is a process of connecting to a system by providing credentials to gain access. Systems are scanned using different network protocols (SSH, SMB, HTTPS, SNMP, etc.) to gain access to the target asset. For example, logging into a remote host via SSH using a username and password is a method of authentication. Each asset can allow authentication using several protocols. Assets with more than one available authentication protocol (for example, a Windows server running a SQL server) could report both authentication success and failure. Understanding this fact during analysis is key to determining if the system was successfully scanned or not. While in many cases the successful authentication of an asset may seem binary, there are many examples of successfully scanned systems with authentication failures. Tenable recommends system administrators review all of the failures and investigate the services which are enabled on the asset for a complete analysis.
Credentialed vulnerability scans are easier with Nessus Agents, because after the agents are installed, they don’t need on-going host credentials. When Nessus Agents are installed (either manually or with a software management system), they are installed under the local SYSTEM account in Windows or root on Unix-based operating systems. The agents then inherit the permissions of the account used for installation so they can perform credential scans, even if the credentials on the system have changed.
Tenable Nessus Agents are designed to have minimal impact on the system and the network, giving organisations the benefit of direct access to all hosts without disrupting your end users. Additionally Tenable Nessus Agents provide extended scan coverage and continuous security, eliminate the need for credential management, reduce network bandwidth, and minimise maintenance.
There are also cases where there is overlap in the intent of the check. For example, if you use OS fingerprinting without credentials in a network-based scan and query the system for the exact version of its OS in a credentialed scan, this overlap heightens the credential findings over the network, since the network version tends to be a best guess.
Local checks are required to ensure the scans are complete and accurate. Users enable local checks by providing credentials with elevated privileges, administrative access, or by deploying Tenable Nessus Agents. Tenable Security Center and Tenable Vulnerability Management requires privileged access to provide a comprehensive assessment of risk on an asset. The more access to a system Tenable Security Center and Tenable Vulnerability Management has, the more complete the vulnerability detection.
Additional information can be located in the Vulnerability Assessment/Scanning section of the Vulnerability Management Cyber Study.