Vulnerability Assessment/Scanning
Vulnerability assessment is a process that identifies and evaluates network vulnerabilities by constantly scanning and monitoring your organization's entire attack surface for risks. This is the first step in defending your network against vulnerabilities that may threaten your organization.
Authenticated vs. Unauthenticated Scanning
Authenticated (credentialed) and unauthenticated (non-credentialed) scans offer different approaches to vulnerability assessments. They primarily differ in the level of access and permissions granted to the Tenable Nessus scanner. Credentialed scans can perform a wider variety of checks than non-credentialed scans, which can result in more accurate scan results. However, there are benefits to an unauthenticated scan as well. The choice between the two methods depends on the specific goals of the assessment. Often a combination of both will provide the most comprehensive view of a system's vulnerabilities.
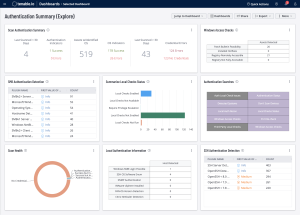
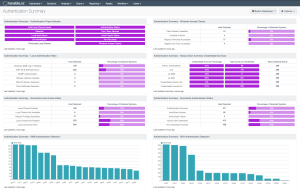
The Authentication Summary dashboard for Tenable Vulnerability Management and the Authentication Summary dashboard for Tenable Security Center brings together all the plugins used to verify successful authentication of assets during vulnerability scans, providing security administrators visibility into areas of concern so the appropriate actions can be taken.
Authentication is a process of connecting to a system by providing credentials to gain access. Systems are scanned using different network protocols (SSH, SMB, HTTPS, SNMP, etc.) to gain access to the target asset. For example, logging into a remote host via SSH using a username and password is a method of authentication. Each asset can allow authentication using several protocols. Assets with more than one available authentication protocol (for example, a Windows server running a SQL server) could report both authentication success and failure. Understanding this fact during analysis is key to determining if the system was successfully scanned or not. While in many cases the successful authentication of an asset may seem binary, there are many examples of successfully scanned systems with authentication failures. Tenable recommends system administrators review all of the failures and investigate the services which are enabled on the asset for a complete analysis.
Local checks are required to ensure the scans are complete and accurate. Users enable local checks by providing credentials with elevated privileges, administrative access, or by deploying Tenable Agents. Tenable Security Center and Tenable Vulnerability Management requires privileged access to provide a comprehensive assessment of risk on an asset. The more access to a system Tenable Security Center and Tenable Vulnerability Management has, the more complete the vulnerability detection.
Authenticated Scan
In the authenticated scan, the Tenable Nessus scanner is provided with a set of valid credentials which are used to access the target systems. The scanner runs with elevated privileges allowing a greater level of access. Authenticated scans provide a more comprehensive and accurate view of a system's vulnerabilities.
Unauthenticated Scan
In the unauthenticated scan, the Nessus scanner does not have valid credentials to access the target system. The scanner can only operate as an external entity and can only attempt to identify vulnerabilities without privileged access. The advantage is that the Nessus scanner mimics the perspective of an external attacker. This could help identify vulnerabilities that could be exploited without authentication. The significant disadvantage, which is typically most associated with a poorly configured scanner or bad credentials, is that a complete picture of the vulnerabilities on the target system will not be identified.
Identifying and Troubleshooting Authentication Problems
Cyber Exposure requires the data collected by the vulnerability scanner to be trusted and verifiable.
Authentication can be defined by connecting to a system and providing credentials in order to gain access to the system. Nessus scans systems by using different network protocols (SSH, SMB, HTTPS, SNMP, etc.) in order to gain access to the remote target asset. For example, logging into a remote host via SSH using a username and password is a method of authentication. Each remote asset can be authenticated using several protocols. Assets with more than one authenticatable protocol (for example, a Windows server running a SQL server) could report both an authentication success and failure. Understanding this fact during analysis is key to understanding if the system was successfully scanned or not. While in many cases the successful authentication of an asset may seem binary, there are many examples of successfully scanned systems with authentication failures. The system administrator should review all the failures and understand the services which are enabled on the asset for a complete analysis.
Local checks are a feature in Tenable Nessus scans, which enable the scanner to perform security checks on the target asset. Different authentication protocols may allow for general checks to be performed locally, but when all possible checks are completed, Tenable Nessus does a more detailed local check. The local check always requires authentication and often requires elevated privileges. Local checks for major operating systems with security advisories numbering in the thousands are often grouped into their own plugin family, but local checks plugins also exist in other families such as Firewalls or Misc.
Enabling local checks is much more complex than authentication and occurs after successful authentication has been established. In order to enable local checks, the following criteria must be satisfied:
-
The target device or operating system must be identified.
-
Local checks must be available in Tenable Nessus plugins for the identified device or operating system.
-
The information needed to enable local checks for that particular device or operating system must be obtained from the remote host.
Except in particular circumstances, such as scanning localhost, remote authentication must first be successful before local checks can be enabled - but the threshold to enable local checks is higher than the threshold for successful authentication.
To ensure the scans report the most complete and accurate information, local checks are a requirement. Users can enable local checks by providing credentials with elevated privileges and/or administrative access or deploying Tenable Agent. Without elevated access, the ability for Tenable Nessus to successfully identify risk on a system is diminished. The more access to a system Tenable Nessus has, the more complete the risk analysis is.
The following Tenable Nessus plugin IDs are useful in the identification and troubleshooting of scan-related concerns.
Local Authentication
There are a number of useful plugins used to authenticate to the remote host which assist in determining the health of the vulnerability scanning program. These plugins gather the information necessary for local checks, and enable local checks. These plugins can be used to troubleshoot authentication problems. Their output and audit trails provide details of any problems that were encountered. These are:
-
97993 - OS Identification and Installed Software Enumeration over SSH v2 (Using New SSH Library): Enables local checks over SSH.
-
12634 - Authenticated Check : OS Name and Installed Package Enumeration: Enables local checks over SSH.
-
10394 - Microsoft Windows SMB Login Possible: Enables local checks over SMB.
-
19762 - SNMP settings: Enables local checks over SNMP.
-
73204 - Citrix NetScaler Version Detection: Enables local checks over SSH, SNMP, or NTP.
-
72816 - Palo Alto Networks PAN-OS Version Detection: Enables local checks over HTTP if not already enabled over SSH.
-
57399 - VMware vSphere Installed Patches: This gathers info over HTTPS SOAP API which triggers other plugins to enable local checks.
-
57400 - VMware vSphere Installed VIBs: This gathers info over HTTPS SOAP API which triggers other plugins to enable local checks.
Summarize Specific Auth / Local Checks Issues.
The following plugins provide summaries of particular types of auth / local checks issues that have been reported by other plugins and report the plugins that encountered these issues:
-
102094 - SSH Commands Require Privilege Escalation: Reports commands failed due to lack of privilege escalation or due to failed privilege escalation. Commands reported here may not have prevented local checks from running, but may have caused the plugin associated with each command to fail to produce the expected output. This causes authentication to report as successful, but with insufficient access.
-
110695 - Authentication Success - Local Checks Not Available: Reports local checks were unavailable for the identified device or operating system and includes the report of the plugin that logged the unavailability of local checks.
Successful Login: Windows
-
24269 - WMI Available
-
10394 - Microsoft Windows SMB Login Possible
-
10400 - Microsoft Windows SMB Registry Remotely Accessible
-
10428 - Microsoft Windows SMB Registry Not Fully Accessible Detection
-
57033 - Microsoft Patch Bulletin Feasibility Check
-
20811 - Microsoft Windows Installed Software Enumeration (credentialed check)
-
26921 - Windows Service Pack Out-of-Date
-
34252 - Microsoft Windows Remote Listeners Enumeration (WMI)
-
35703 - SMB Registry : Start the Registry Service during the scan
-
35704 - SMB Registry : Stop the Registry Service after the scan
-
24272 - Network Interfaces Enumeration (WMI)
-
19506 - Nessus Scan Information (Settings)
Note: For 19506, look for "Credentialed Checks: yes" for a successful scan.
Successful Login: Linux
-
22869 - Software Enumeration (via SSH) (General)
-
12634 - Authenticated Check: OS Name and Installed Package Enumeration (Settings)
-
25221 - Remote listener enumeration (Linux/AIX)
-
33851 - Manually compiled network daemons
-
19506 - Nessus Scan Information (Settings)
Note: For 19506, look for "Credentialed Checks: yes" for a successful scan.
Login Failure/Permission Failure
-
11149 - HTTP login failure (preference): Provides a means for HTTP login info, but also returns login failures when an error happens.
-
21745 - OS Security Patch Assessment Failed: See following note.
-
24786 - Nessus Windows Scan Not Performed with Admin Privileges: This means the account provided for Windows did not have administrator privileges on the scanned host.
-
26917 - Nessus Cannot Access the Windows Registry: This means the target's registry was not available. This is most likely caused by the Remote Registry not set correctly either in the scan policy or on the target.
-
35705 - SMB Registry : Starting the Registry Service during the scan failed: Indicates failure to start remote registry access
-
35706 - SMB Registry : Stopping the Registry Service after the scan failed: Indicates failure to start remote registry access
More information for plugin 21745 - OS Security Patch Assessment Failed
The plugin 21745 error "unable to create a socket" indicates Nessus was unable to connect to the system. In this case, Nessus was unable to successfully complete the TCP handshake on port 445. This could be for a number of reasons:
-
Nessus is unable to connect due to network issues
-
A network or host-based firewall is blocking the connection attempts
-
Due to network latency, a timeout is reached before the connection occurs
-
The user that started the scan does not have permission to scan the given host and/or port
If the user sees this error in plugin 21745 every time authentication fails for a given host, Nessus is having connection issues due to one of the conditions listed above. Nessus users have no restrictions by default, so this can only happen if an admin explicitly puts any kind of restrictions on users. To determine if this is the case, view the rules file.
To find the rules file:
-
Log into Nessus as an administrator.
-
Select Configuration > Advanced Settings.
-
Scroll down to the rules setting.
Note: If Nessus has too many open sockets during a scan, an error message indicates this problem in nessusd.dump or nessusd.messages.
Summarize Specific Auth / Local Checks Issues
These plugins provide summaries of particular types of auth / local checks issues that have been reported by other plugins and report the plugins that encountered these issues:
-
102094 - SSH Commands Require Privilege Escalation: Reports commands that failed due to lack of privilege escalation or due to failed privilege escalation. Commands reported here may not have prevented local checks from running, but may have caused the plugin associated with each command to fail to produce the expected output. This causes authentication to report as successful, but with insufficient access.
-
110695 - Authentication Success - Local Checks Not Available: Reports local checks were unavailable for the identified device or operating system and includes the report of the plugin that logged the unavailability of local checks.
Summarize Authentication Status
These plugins provide summaries of the overall authentication status for the target. A given target should trigger at least one of these plugins:
-
141118 - Target Credential Status by Authentication Protocol - Valid Credentials Provided: Reports protocols with successful authentication. This plugin reports per protocol, possibly valid credentials can be provided for one protocol and not another. For example, authentication may succeed via SSH but fail via SMB, while no credentials were provided for an available SNMP service.
-
110095 - Target Credential Issues by Authentication Protocol - No Issues Found: Reports protocols with successful authentication and no reported privilege/access issues.
-
110385 - Target Credential Issues by Authentication Protocol - Insufficient Privilege: Reports protocols with successful authentication that also had privilege/access issues logged for the successful credentials.
-
104410 - Target Credential Status by Authentication Protocol - Failure for Provided Credentials: Reports protocols with only authentication failures.
-
110723 - Target Credential Status by Authentication Protocol - No Credentials Provided: Reports protocols that were detected in the scan as available for authentication, but did not have credentials provided for authentication attempts.
-
117885 - Target Credential Issues by Authentication Protocol - Intermittent Authentication Failure: Reports protocols with successful authentication that also had subsequent authentication failures logged for the successful credentials.
-
A given target usually triggers at least one of these unless no services are detected supporting protocols Nessus uses for authentication. Audit trails should indicate this.
-
Authentication status is reported per protocol. This means that if there are multiple authentication protocols available on the target with different authentication statuses, possibly both Authentication Success and Authentication Failure can be seen.
-
For a given protocol, if both access/privilege problems were encountered and service/authentication problems were encountered, possibly both plugins 110385 and 117885 can be seen.
Summarize Local Checks Status
These plugins provide summaries of overall local checks status for the target. In the case of issues or errors logged by previous plugins, these plugins provide a list of the issues/errors logged along with the reporting plugin and protocol if available.
-
21745 - OS Security Patch Assessment Failed: Reports local checks were not enabled due to an error/failure and lists the details of the errors/failures. Focus on "Local Checks Not Run" rather than the "Authentication Failure" section. While authentication failure is one failure that can cause local checks to be disabled, there are many other types of errors and failures that prevent enabling local checks.
-
117886 - OS Security Patch Assessment Not Available: Reports local checks were not enabled for an informational reason and lists informational reason details.
-
117887 - OS Security Patch Assessment Available: Reports local checks were enabled. If available, this includes the account and protocol used for local checks.
Additional Resources
An additional list of plugins useful for troubleshooting Tenable Nessus scans can be found here.
Internal Asset Scanning
For more information on getting started with Tenable Nessus, refer to the product documentation.
Externally Exposed Asset Scanning
For more information on getting started with Tenable Web App Scanning, refer to the product documentation.