Risk-Based Vulnerability Management
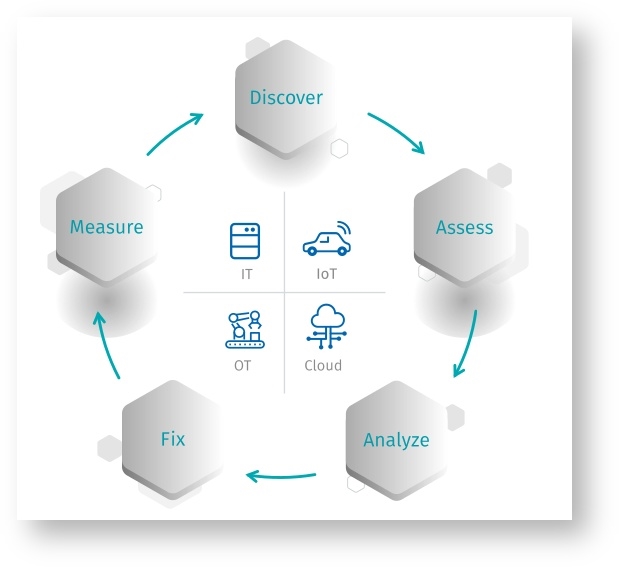
Risk-Based Vulnerability Management (RBVM) is a process that reduces vulnerabilities across the attack surface by prioritizing remediation based on the risks they pose to the organization. Unlike legacy vulnerability management, risk-based vulnerability management goes beyond discovering vulnerabilities, by helping organizations understand vulnerability risks, by introducing threat context and insight into potential business impact.
RBVM uses machine learning to correlate asset criticality, vulnerability severity, and threat actor activity. This helps organizations cut through vulnerability overload so teams can focus on the relatively few vulnerabilities that pose the most risk to the enterprise. Legacy vulnerability management solutions weren't designed to handle the modern attack surface and the increasing threats.
The attack surface is no longer just traditional IT assets. Included are mobile devices, web applications, cloud infrastructure, containers, Internet of Things (IoT) devices, and operational technology (OT) assets. In these modern networks, legacy vulnerability management tools can’t deliver complete and timely insights into all of the devices across the entire attack surface. This leaves uncertainty and increases Cyber Exposure. Instead, these legacy tools are limited to a theoretical view of the risk a vulnerability could potentially introduce, which can cause security teams to chase after the wrong issues while missing many of the most critical vulnerabilities posing the greatest risk to your business.
What’s even more frustrating are the mountains of vulnerability data generally returned from legacy vulnerability management processes. How do organizations identify which vulnerabilities to fix first? How do administrators know which weaknesses pose the greatest threats to the organization?
RBVM eliminates guesswork, by taking a risk-based approach to vulnerability management, security teams can focus on the vulnerabilities and assets that matter most and address the organization’s true business risk instead of wasting valuable time on vulnerabilities attackers may not likely exploit. If you’re new to risk-based vulnerability management, check out this comparison guide. The guide breaks down the differences between legacy vulnerability management and risk-based vulnerability management with insight into how a risk-approach can make your organization's vulnerability management program more efficient and effective.
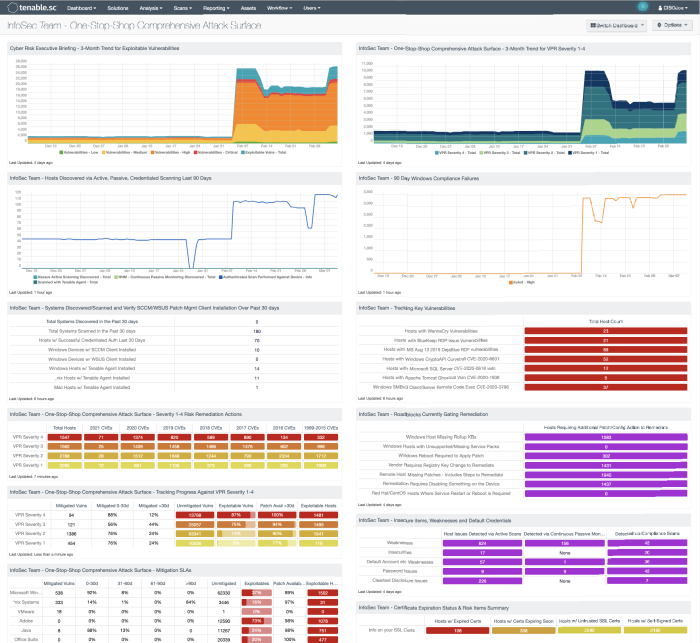
With the principles of Cyber Exposure Management in mind, dashboards, such as the InfoSec Team - One Stop Shop Comprehensive Attack Surface dashboard for Tenable Security Center helps the organization team maintain a high level of awareness and vigilance. The filters and components are tailored to guide teams in detecting, predicting, and acting to reduce risk across their entire attack surface. Information security teams are empowered to analyze findings, remediate identified risks, track progress, and measure success against the organization's charter and SLAs.
Organizations often have teams that focus on the detailed information relevant to the teams' assets; or operational focus areas, such as Windows, Linux, databases, or network infrastructure. The InfoSec Team – One-Stop Shop Comprehensive Attack Surface dashboard, shown in the following image, contains components that do not require specific asset list filters to be applied before use.
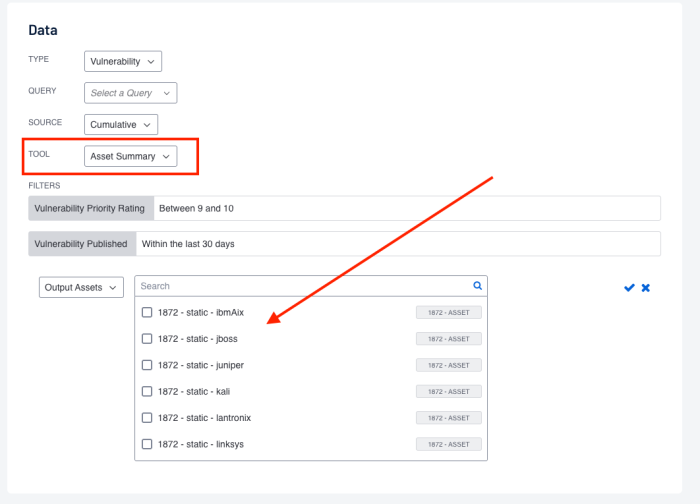
However, organizations with teams that focus on a specific group of assets benefit from using custom asset lists. Information security teams can visualize findings against assets that are "owned by" or "assigned to" specific teams within the organization using this method. Additionally, an Output Assets filter can be set to provide greater insight into where additional resources need to be allocated to mitigate vulnerabilities.
The Output Assets filter is only available when using the Asset Summary Tool. When this tool is selected, you have the option to refine the filters to include specific Asset information.
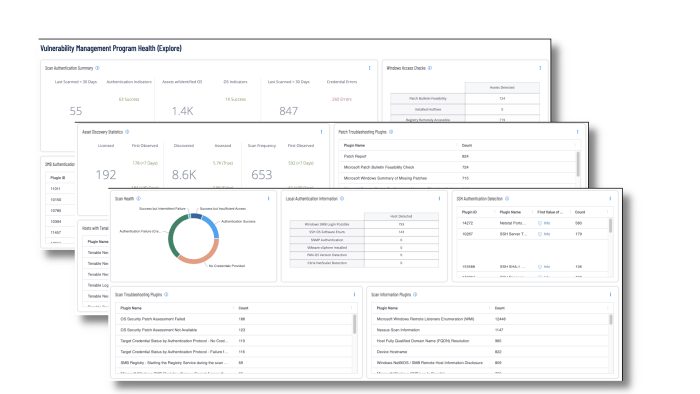
For Tenable Vulnerability Management, dashboards such as the Vulnerability Management Program Health dashboard shown in the following image, helps security operations teams ensure their scanning program is appropriately maintained for an evolving operational technology landscape aligned with business strategy.
There are many factors that can adversely affect the scope and accuracy of scan data, such as failed credentials, network problems, or license limitations. This dashboard provides security analysts comprehensive information to monitor the health of their scanning program.
Analysts can drill into the summary information displayed in the dashboard to troubleshoot upstream scanning problems that can adversely impact downstream reporting to stakeholders.