Patch Management
The primary objective of a patch management program is to prioritize vulnerabilities based on the full business context, including a comprehensive analysis of vulnerability characteristics and criticality rating for each asset.
Not all vulnerabilities are created alike. Some pose an immediate risk to the organization, while others pose little to no risk at all. The problem with legacy vulnerability management practices is that they rely solely on Common Vulnerability Scoring System (CVSS) ratings to prioritize remediation. CVSS returns mountains of vulnerability data—with many rated “critical” or “high,” even if they don’t pose an actual risk to the organization.
Most legacy methods employ the CVSS to prioritize which vulnerabilities to remediate first. For example, a typical organizational policy is to remediate all vulnerabilities with a CVSS score of 7 and above. This method has become commonplace among most security teams, yet it’s proven to be inefficient and ineffective when taken in isolation. This is because while v3 of CVSS has certainly made some improvements over past versions, CVSS still suffers from significant problems — not least of which is the fact its risk unaware. Since most CVSS scores are assigned within two weeks of vulnerability discovery, the score only employs a theoretical view of the risk a vulnerability could potentially introduce. This leads security teams to waste the majority of their time chasing after the wrong issues, while missing many of the most critical vulnerabilities posing the greatest risk to the business.
Another major problem is that most teams only use the CVSS base score which never changes, irrespective of the changes in the threat landscape. That’s because the base score doesn’t have any degree of context from which to understand the actual risk a vulnerability poses to the business. While CVSSv3 introduced environmental and temporal scores to supplement the base score, these two additional components are often difficult to understand and haven’t proven to be terribly effective for measuring risk. As a result, the majority of organizations opt to simply continue to use the base score exclusively.
Understanding which assets are affected by critical vulnerabilities is as important as locating the vulnerabilities themselves. However, the combination of the organization's most important assets, along with having those assets contain high risk vulnerabilities, makes patching these assets the highest priority. For example, if a vulnerability was identified with a criticality rating of 9.0 (on a scale of 1 to 10, with 10 being the most severe) on a secondary file server. However, should the same vulnerability occur on a server that houses all the companies financial and sensitive customer information, the latter should take a higher priority and be patched first.
Identifying assets running EOL applications is an important part of assessing and minimizing organizational risk since patches, updates, and security fixes are no longer available. The Center for Internet Security (CIS) states that organizations must ensure only software applications or operating systems currently supported and receiving vendor updates are added to the organization’s authorized software inventory. Organizations need to tag all unsupported software in the asset inventory.
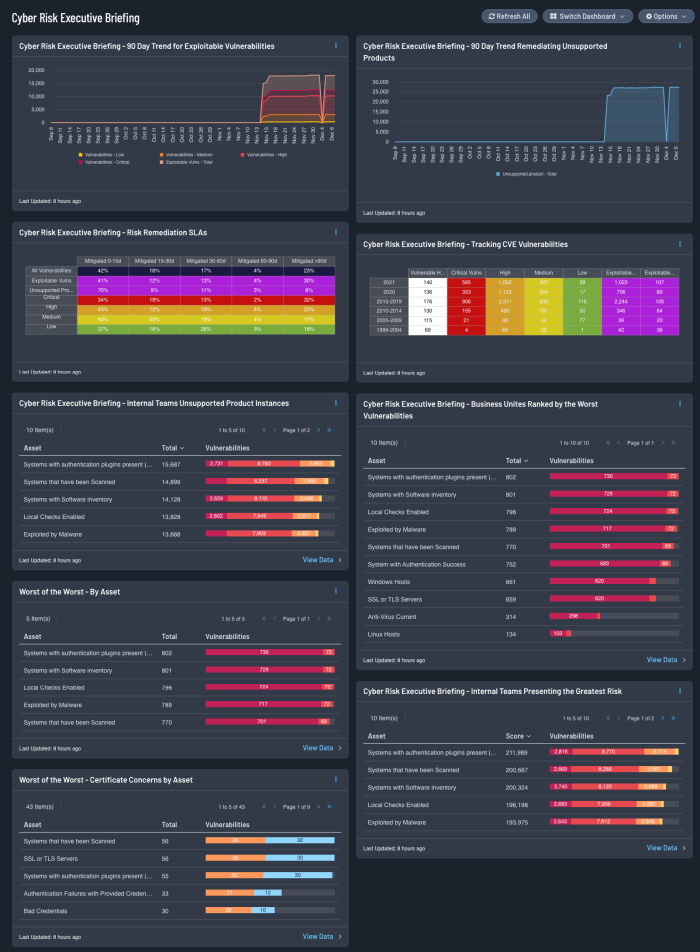
The Cyber Risk Executive Briefing dashboard for Tenable Security Center assists cyber security leaders who are building or strengthening a vulnerability management program to better visualize the modern attack surface.
The Information presented focuses on the findings organizations should prioritize and mitigate first, by leveraging the Vulnerability Priority Rating (VPR). The VPR score is an output of Predictive Prioritization, which allows cyber security leaders to focus on items that help drive key performance indicators, by combining research insights, threat intelligence, and vulnerability ratings to reduce noise. Effective vulnerability remediation becomes easier as vulnerabilities are presented in a manner that helps visualize vulnerability remediation programs and provide measures against established goals and SLAs.
The prioritized data establishes a measurable reference point used by cyber security leaders to create actionable mitigation tasks based on VPR and improve the risk reduction timelines. When not using VPR as a filter to focus on the most significant concerns, noise increases and the large number of critical and high vulnerabilities, as determined most often by Common Vulnerability Scoring System (CVSS) rating, become cumbersome and difficult to sort. The dashboard is laid out to provide a high-level risk summary in a visual manner allowing business leaders to gain insight into their vulnerability management programs quickly and effectively. Risk is measured between customer lines of business, locations, etc. and fosters healthy team competition to not be at the top of the proverbial wall-of-shame.
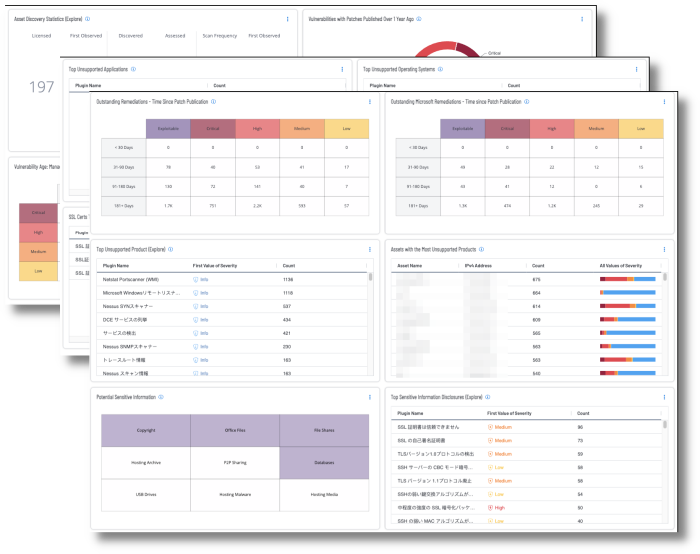
Key areas of concern are unsupported products, asset management/vulnerability remediation, and secure communications for sensitive information. Tenable Vulnerability Management helps to address these issues with the Fundamental Cyber Hygiene Report Card dashboard.
A recent publication from the U.S. Cybersecurity Infrastructure Security Agency (CISA) outlines their Strategic Plan FY2023 - 2026 to provide a vision for the future of cybersecurity and helps to ensure technology products are safe and secure by design. This dashboard provides an overall picture of an organization’s fundamental cyber hygiene. The three goals identified in the Strategic Plan FY2023 - 2026 plan are:
-
Address Immediate Threats
-
Harden the Terrain
-
Drive Security at Scale
Unsupported products, operating systems, and applications are a major cause of data breaches. The proliferation of unsupported and end-of-life (EOL) products is a common security problem experienced across all organizations. As applications and operating systems reach EOL, vendors stop offering support, causing security and stability to decrease over time. A comprehensive summary of unsupported products in the environment is provided via the Top Unsupported Product widget within the dashboard.
Another major concern is visibility into the assets in the environment and how effectively vulnerabilities on those assets are managed. As vulnerabilities are identified, remediation must be prioritized and tracked in accordance with organizational goals and Service Level Agreements (SLAs). Reviewing remediated vulnerabilities and the remediation timeframe provides valuable information to the organization on the effectiveness of the risk remediation program. Vulnerabilities that are known to be exploitable are particularly dangerous, since there are exploit frameworks readily available to exploit them. Details are included on vulnerabilities where a patch to remediate the exposure was available more than a year ago.
Data on secure communication controls for sensitive information is provided within the Fundamental Cyber Hygiene Report Card dashboard. The status on SSL certificates that are aged out or soon to be aged out is displayed, along with SSL and TLS insecure communication exposures in the environment. Information about exposure of various types of potentially sensitive information is provided. Many organizations are unaware how much sensitive information is exposed, which enables attackers to tailor an attack path specifically targeting the organization, leading to data loss exposures.