Further Identification of Applications
For example, If we wanted to identify endpoints which had Chrome installed, we could filter on pluginID = 20811, with a Plugin Output = *chrome* (asterisk specifies a wildcard element).
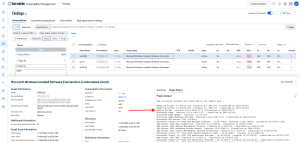
Begin by navigating to the Findings page in Tenable Vulnerability Management, or the Analysis Page within Tenable Security Center, and apply the above filter, then view the details and the plugin output. Results similar to the following screenshot will be displayed.
Note: For Tenable Security Center, the process has the following differences. From the Analysis tab, filter on pluginID = 20811, with a Vulnerability Text contains chrome (REGEX can also be used if REGEX is selected in lieu of “Contains” from the dropdown) and we would get results similar to the screenshot below, which shows results for all the hosts which have Chrome installed.
The plugin output contains the version of Google Chrome and the date the application was installed. Additional searches can be performed using specific application version searches if so desired. Filters created here to refine search results, can also be used to refine vulnerability results displayed within components.
Restrict Unnecessary or Unauthorized Browser and Email Client Extensions
Organizations need to determine which browser extensions are authorized, and which ones are not. Once this determination is made, restrict either through uninstalling or disabling any unauthorized or unnecessary browser or email client plugins, extensions, and add-on applications.
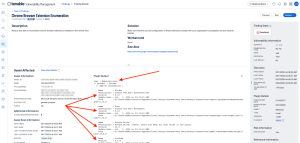
There are Tenable Nessus plugins, which detect or enumerate extensions, such as plugin 96533 - Chrome Browser Extension Enumeration and 133180 Chrome Browser Extension Enumeration (macOS). If the proper credentials are utilized, these plugins will enumerate Chrome extensions for all users.
In the example below (Tenable Vulnerability Management shown), the plugin output contains information regarding the:
-
User who has the extension installed
-
The Name of the Extension
-
The Version of the Extension
-
The date of the Last Update
-
The installation Path
This allows analysts reviewing the information and the administrator or operational staff to have the most complete and reliable information needed to take corrective action.
The plugin output contains the version of Google Chrome and the date the application was installed. Additional searches can be performed using specific application version searches if so desired. Filters created here to refine search results, can also be used to refine vulnerability results displayed within components.
AI/LLM Detection
In an era of rapidly evolving Artificial Intelligence/Large Language Model (AI/LLM) technologies, cybersecurity practitioners face significant challenges in monitoring unauthorized AI solutions, detecting AI vulnerabilities, and identifying unexpected AI/LLM development. Tenable leverages advanced detection technologies - agents, passive network monitoring, dynamic application security testing, and distributed scan engines - to surface AI/LLM software, libraries, and browser plugins. The risk managers utilize this data to begin a comprehensive review of the AI/LLM packages in systems and web applications, along with associated vulnerabilities, mitigating risks of exploitation, data leakage, and unauthorized resource consumption.
The Nessus AI/LLM Software Report plugin (196906) reports a summary of all AI/LLM software detected on the remote host. This plugin detects AI/LLM usage in 3 ways: browser extensions, applications, and file paths all common to AI/LLM implementations. AI/LLM vulnerabilities discovered in web applications are identified using the Web Application Scanner, alongside network traffic analysis using the Nessus Network Monitor (NNM). By combining all methods of data collection, the risk managers are able to identify problem areas and other risks associated with AI/LLM.
AI/LLM technologies are promising and can transform many industries and businesses, offering new innovation and efficiency opportunities. However, the technology represents a huge security challenge at many layers and this impact should not be overlooked. By using Tenable Security Center and Tenable Web App Scanning the organization is able to take a security-first approach. When combined with best practices and robust governance policies, the organizations can harness the power of AI/LLM and mitigate the associated emerging threats.
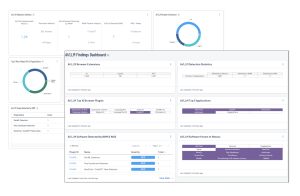
The AI/LLM Findings dashboard for Tenable Security Center and Tenable Vulnerability Management (both displayed below) provides detailed information on AI/LLM findings in web browser extensions and applications.
Anti-Malware Protections
Malicious software or “malware”, is software designed to cause harm to information systems and is one of the biggest challenges organizations face in maintaining cyber hygiene. Malware exploits weaknesses and vulnerabilities to make software or hardware perform actions not originally intended. Malware is constantly evolving and the software used to detect the presence of malware must be kept up-to-date to ensure accurate and efficient detection of emerging threats from malicious code. Anti-malware software includes both signature and non-signature methods of detection, and is frequently updated to leverage new advances in technology, such as machine learning and artificial intelligence. New malware is created and released almost daily. Keeping anti-malware software up-to-date involves applying patches when they become available to fix bugs or vulnerabilities and to update to the latest stable version to leverage the latest features. Any signature based anti-malware rules must be updated with the latest signatures from the vendor to ensure the latest known malware is detected.
For more information on malware detection, visit the Malware Defenses Cyber Exposure Study.