Benchmarks
Tenable is partnered with two major organizations which provide and maintain compliance benchmarks, the Center for Internet Security (CIS) and Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIG). CIS developed a series of best practice benchmarks for a variety of applications, operating systems, servers, and databases used within organizations today. Each benchmark contains recommended security settings designed to harden systems and applications from attack while maintaining overall system functionality. Tenable has been certified by CIS to perform a wide variety of platform and application audits based on the best practice consensus benchmarks developed by CIS. Tenable submits example test cases for all of the criteria within each unique benchmark, and then submits our results to CIS personnel for official certification. Tenable has developed audit files based on the CIS Benchmarks tested on systems, and has been approved and certified by CIS staff members.
DISA’s selection of Tenable as the foundation of its Assured Compliance Assessment Solution (ACAS) cements Tenable’s standing as the undisputed leader in vulnerability management in the U.S. Federal government. The ACAS mission is simple: Assess DoD enterprise networks and connected IT systems against DoD standards, as well as identify any known system vulnerabilities.
For DISA and its constituents, ACAS, powered by Tenable, provides the sophistication and flexibility needed to satisfy the wide variety of security needs the Department of Defense must support, and provides the most comprehensive and integrated view of security posture to reduce risk and exceed DoD compliance. Both Tenable Security Center and Tenable Vulnerability Management support the creating, running, and importing of Policy Compliance scans.
Tenable Security Center CIS / DISA:
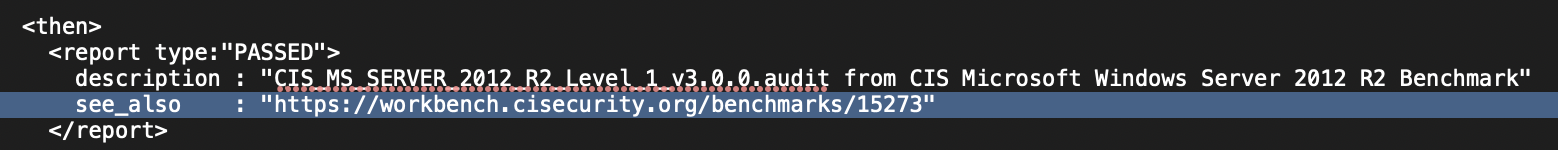
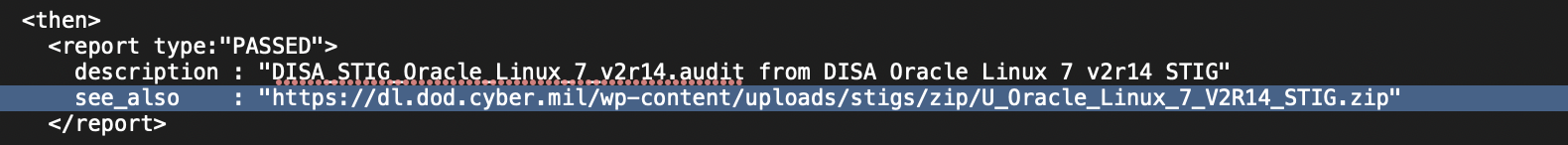
Tenable Security Center’s CIS and DISA reports and widgets utilize the Vulnerability Text filter to parse through the policy compliance scan results for a specific tag called “see_also." The “see_also” tag is present in the audit files used in the policy compliance scans used and the tag describes the benchmark that the audit file relates to. The CIS MS Server 2012 R2 Level 1 v3.0.0 audit file and the DISA STIG Oracle Linux 7 v2r14 audit file snippets show what the see_also tag looks like.
Reports and widgets also use severity filters to differentiate between the three possible result types of the benchmark. A passed benchmark result carries an Info level severity while a failed benchmark result carries a High level severity. The third and last benchmark result type is Manual; these are represented using Medium level severity and are given when the benchmark test requires manual verification. When manual verification is needed the actions required to follow are in the “Steps to remediate” section of the plugin followed by an “Information” section which gives some background on the benchmark.
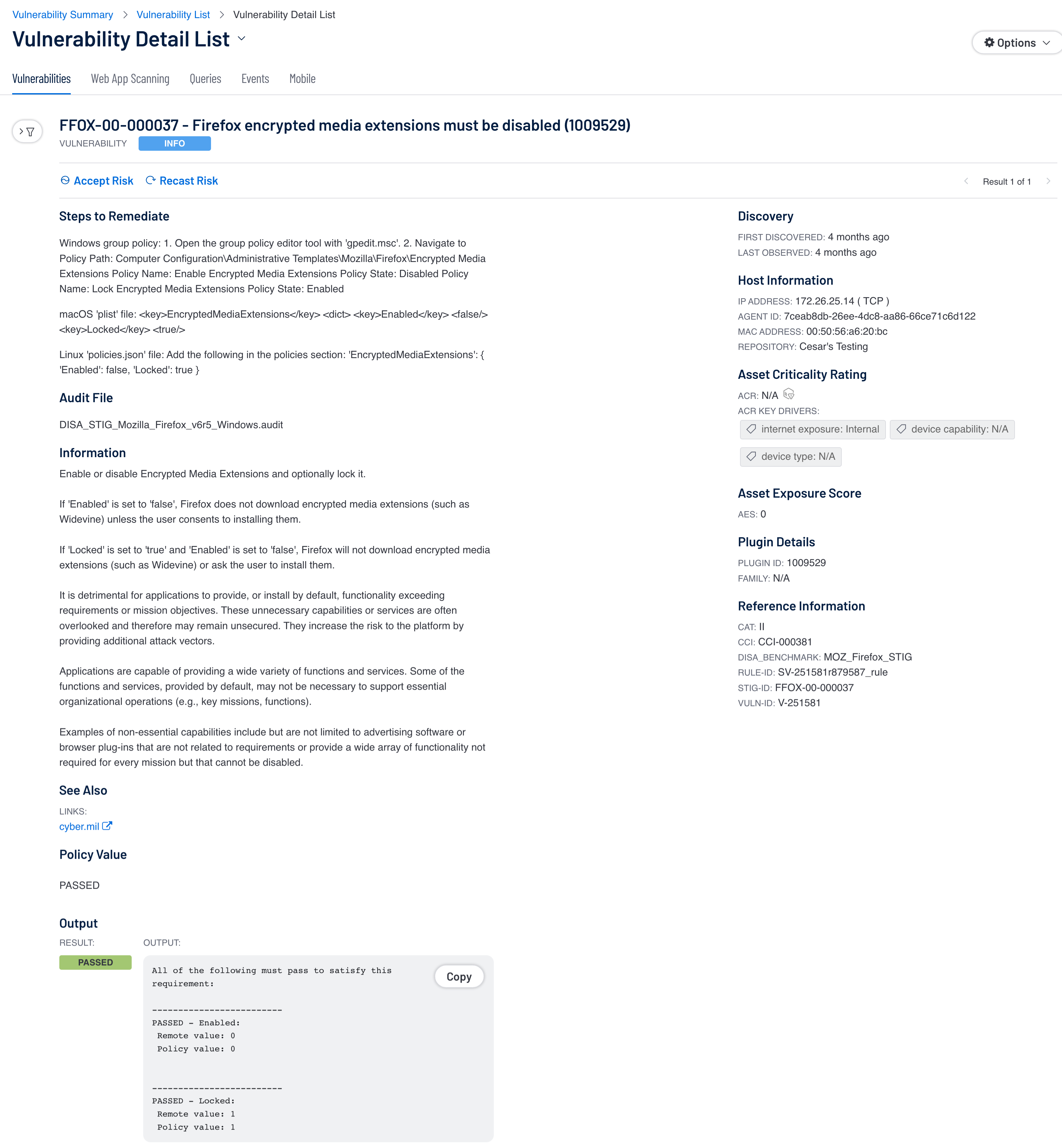
In the Vulnerability Detail List View one can also see the steps to remediate for Passed, Failed, and Manual results.
For results that are Passed or Failed, an Output section is at the bottom and shows the values found. For Manual verification results, represented as Medium level severity, there is no Output as the user needs to follow the Steps to Remediate to verify compliance with the benchmark.
Tenable Vulnerability Management CIS / DISA:
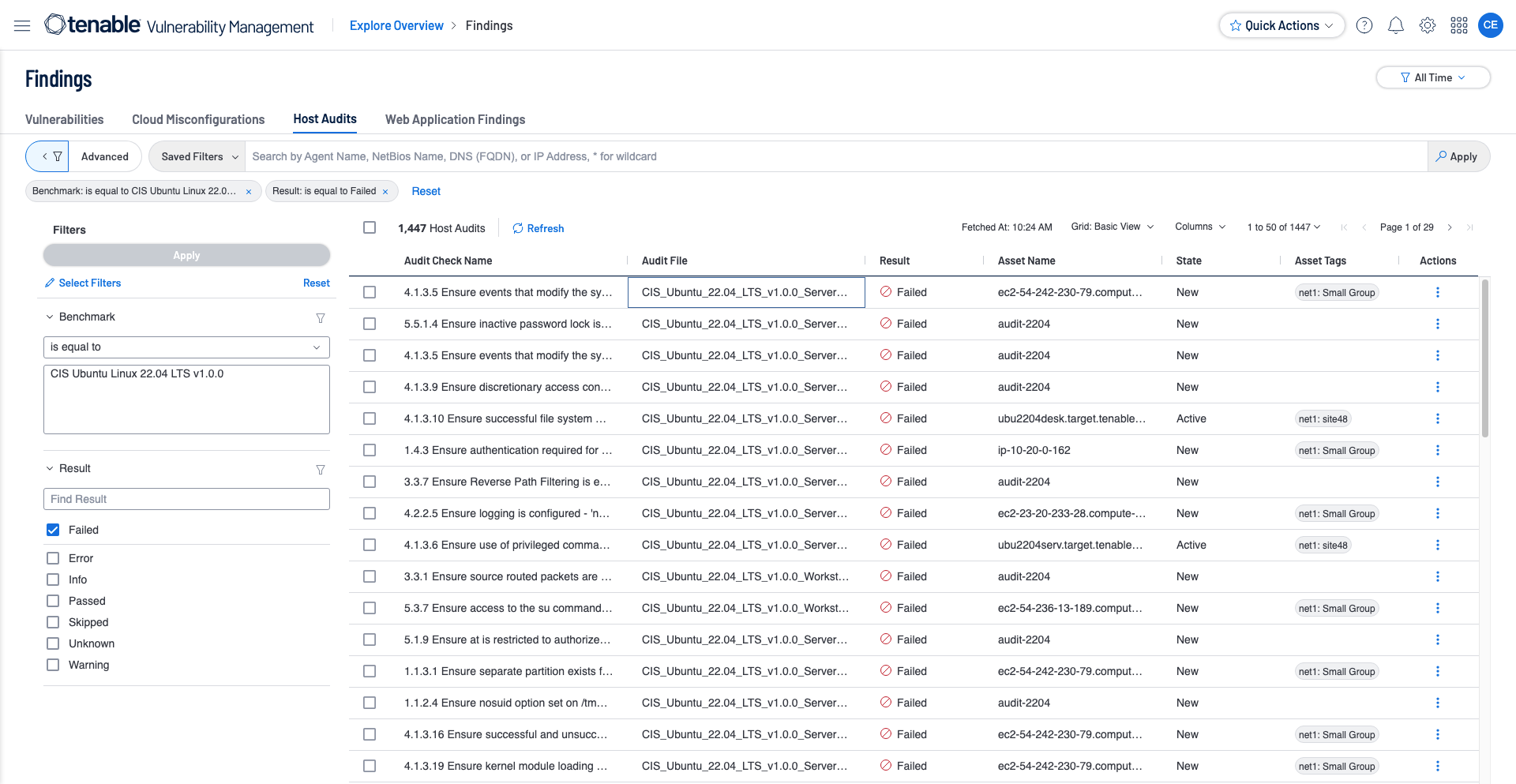
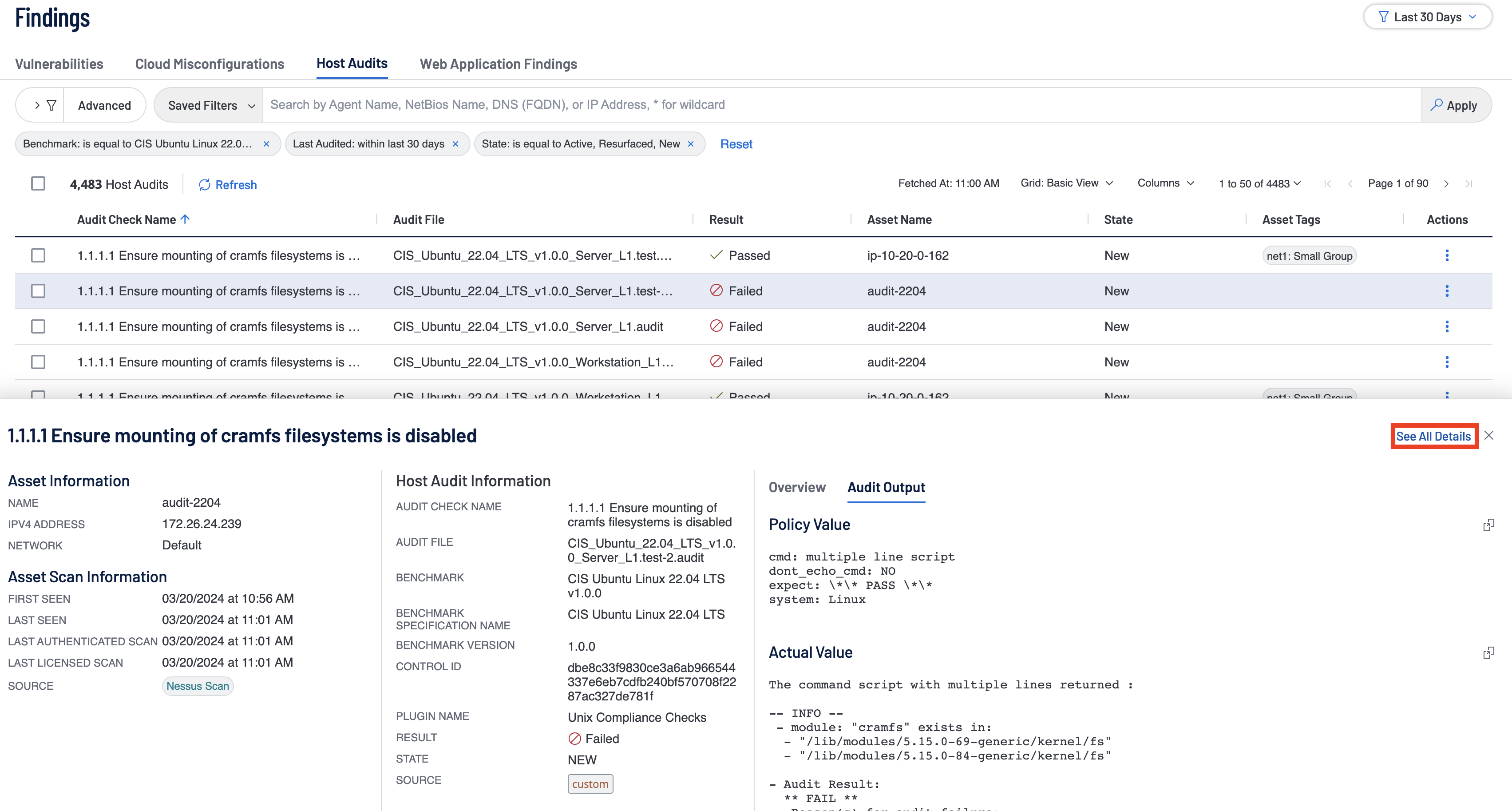
Tenable Vulnerability Management Host Audit reports, chapters, and widgets utilize the Compliance Benchmark filter to search for the specific audit file or benchmark used in the scan. Compliance chapters and reports by default also filter on compliance benchmarks last observed within the last 90 days. The last observed filter means if the policy compliance scan was completed more than 90 days in the past, the result will not show up in the chapter or report being run. The Tenable Vulnerability Management Findings View can be used to look at compliance results easily by using the Benchmark filter.
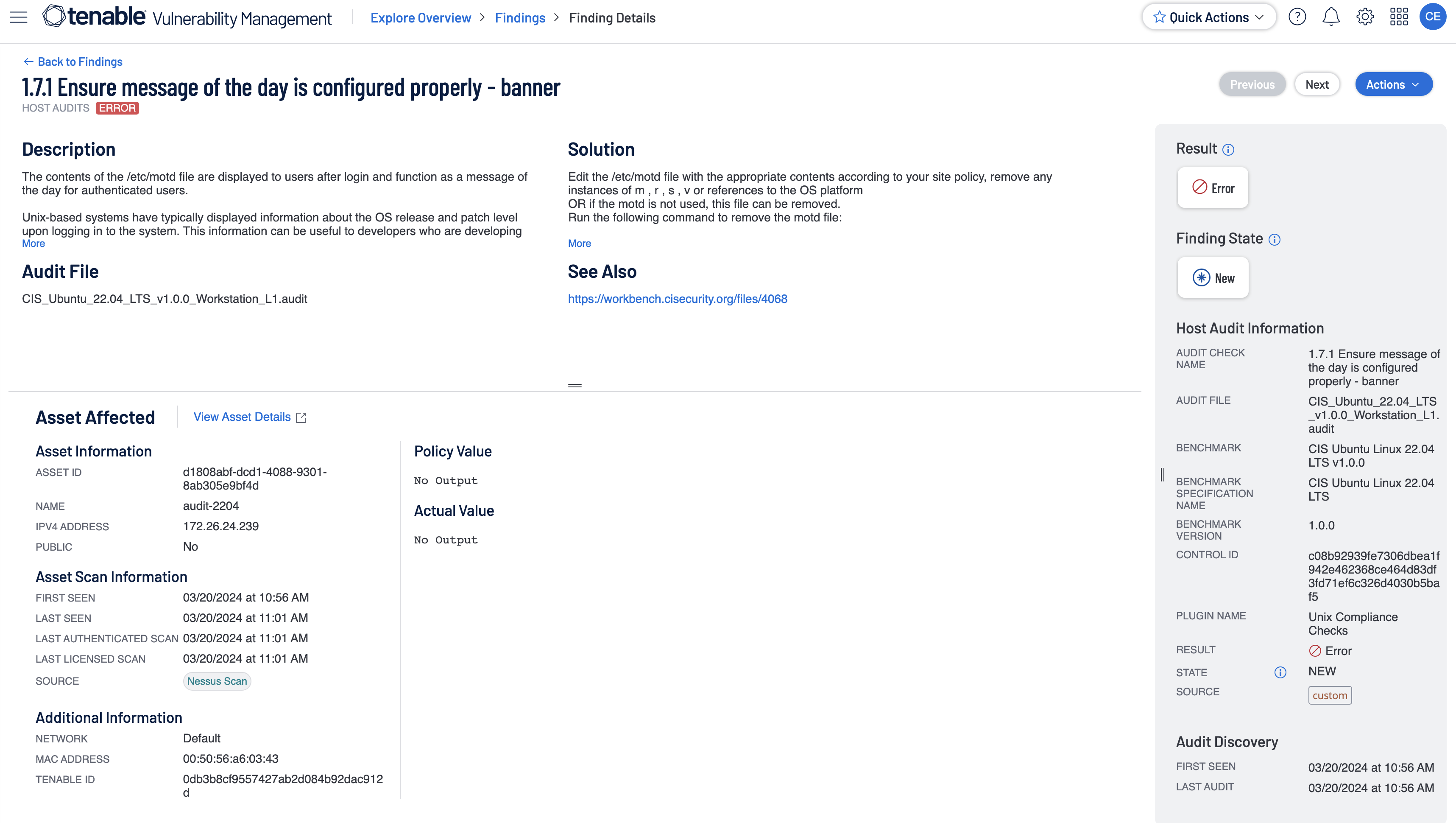
The user is able to further drill within the Findings -> Host Audits page into the results by selecting one from the list given and then clicking on ‘See All details.' This action pulls up all the details of the selected audit check.
Within the Finding Details page, a user is able to view all relevant information about the selected audit check. The Solution section is present for all result types and can be used to correct any failed audit checks as well as manually verify checks that were neither passed or failed.