Compliance Frameworks
In response to increased cyberthreats, governments are enacting mandates and legislation. For example, in the U.S., Executive Order 14028 focuses on improving the security of the software supply chain. In the European Union, the Cyber Resilience Act — published by the European Commission in September 2022 — looks to ensure hardware and software products are placed on the market with fewer vulnerabilities. Such measures not only place new requirements on government agencies, they extend broadly to the organizations these agencies do business with, including cloud service providers, software development organizations, software as a service (SaaS) providers, hardware manufacturers, and virtually any organization creating digital products and services.
The legislative and regulatory changes in the U.S. are not limited to the federal government — they’re also cascading down to state and local governments. Likewise, in addition to the E.U. regulations, nations within the union may also have their own requirements. In the United States, for example, 36 states have enacted new cybersecurity laws in the past two years, with many more in the works as the public sector looks to mitigate the risk of cyberthreats.
Adding to government regulations, industries have also begun to define their own mandates in an effort to improve security posture and minimize risk to consumers and investors. One example of this is PCI DSS in the payment card industry.
For the security teams that must implement these mandates, the challenge is in translating what are often general legislative guidelines and controls into specific policies, tools, and processes. Further, security teams are responsible for enforcing those policies in a scalable and consistent way across the enterprise. For security teams working in multinational enterprises, these challenges are compounded exponentially.
The regulatory environment impacts all aspects of cybersecurity, including traditional IT infrastructure and operational technology. In order to understand how the regulatory environment affects cloud security, you first need an understanding of which regulations apply to your particular business. The table below highlights several regulations with broad sweeping cloud security implications — and the risks that come with non-compliance. Regulations and penalties with cloud security implications.
CIS Critical Security Controls v8 (CSCv8)
Origin: On May 18, 2021 CIS published version 8 of their Critical Security Controls and they provide specific and actionable ways to protect against today's most pervasive and dangerous attacks.
Requirement: The Critical Security Controls are created for organizations of any size or sector.
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| Inventory and Control of Enterprise Assets |
CSCv8|1.* |
| Inventory and Control of Software Assets | CSCv8|2.* |
| Data Protection | CSCv8|3.* |
| Secure Configuration of Enterprise Assets and Software | CSCv8|4.* |
| Account Management | CSCv8|5.* |
| Access Control Management | CSCv8|6.* |
| Continuous Vulnerability Management | CSCv8|7.* |
| Audit Log Management | CSCv8|8.* |
| Email and Web Browser Protections | CSCv8|9.* |
| Malware Defenses | CSCv8|10.* |
| Data Recovery | CSCv8|11.* |
| Network Infrastructure Management | CSCv8|12.* |
| Network Monitoring and Defense | CSCv8|13.* |
| Security Awareness and Skills Training | CSCv8|14.* |
| Service Provider Management | CSCv8|15.* |
| Application Software Security | CSCv8|16.* |
| Incident Response Management | CSCv8|17.* |
General Data Protection Regulation (GDPR)
Origin: Approved by the European Union in 2016, GDPR looks to enforce data protection guidelines for the collection and processing of personal information for anyone living in the European Union.
Requirement: Applies to any entity with a website that attracts European visitor traffic, whether that entity is actively marketing to EU residents or not. Data breaches must be reported within 72 hours.
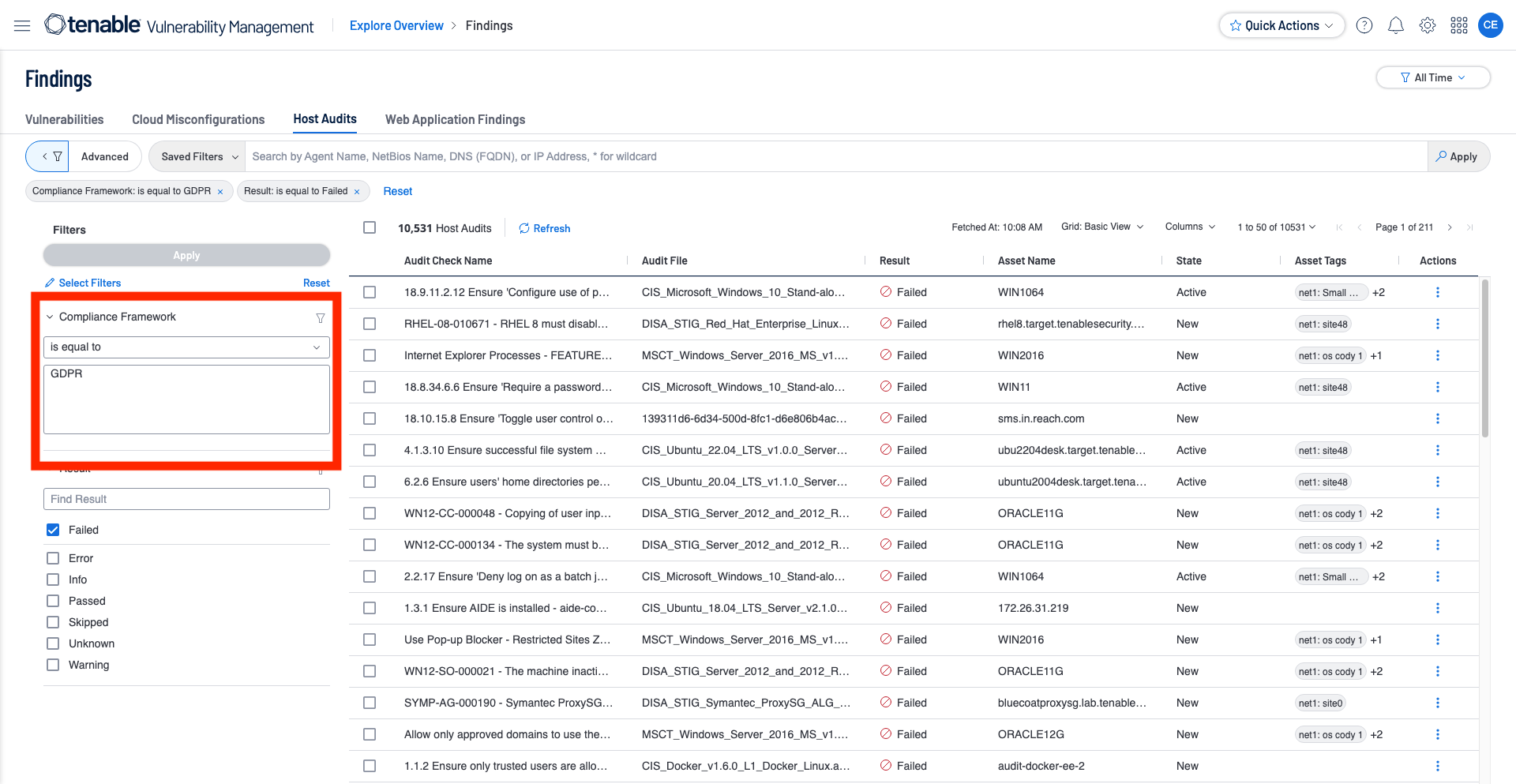
TVM Search Pattern: Compliance Framework = GDPR
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| 32 Security of processing |
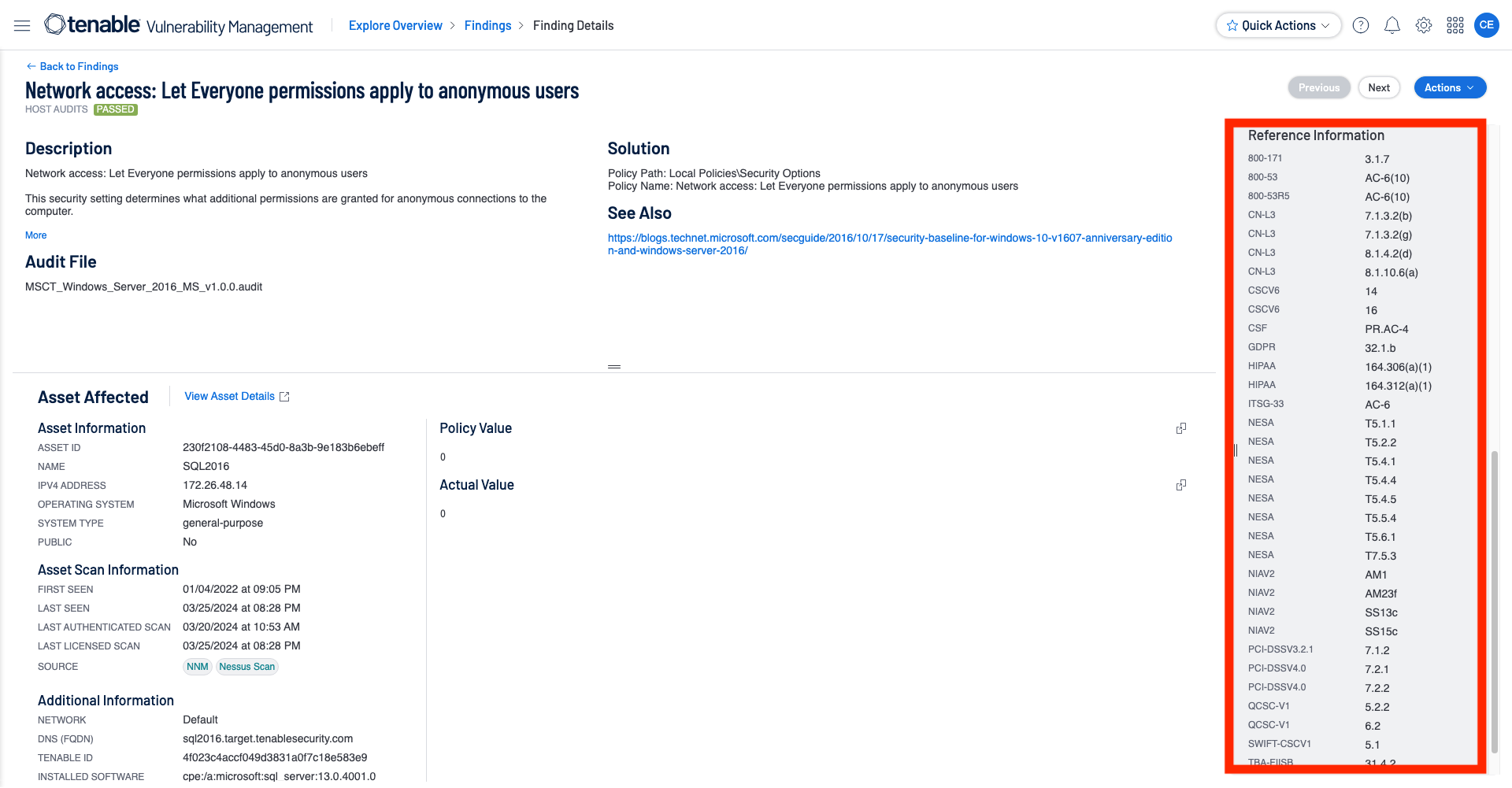
GDPR|32.* |
Health Insurance Portability and Accountability Act (HIPAA)
Origin: Passed by the U.S. Congress, the intent of the HIPAA Privacy Rule is to limit the use and disclosure of electronically protected healthcare information (ePHI), such as medical records, without explicit authorization by individuals.
Requirement: The regulation applies to healthcare providers, health plans, and healthcare clearinghouses that conduct healthcare transactions electronically.
TVM Search Pattern: Compliance Framework = HIPAA
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| 164.306 Security standards: General rules |
HIPAA|164.306* |
| 164.308 Administrative safeguards |
HIPAA|164.308* |
| 164.312 Technical safeguards |
HIPAA|164.312* |
ISO/IEC 27001
Origin: Many organizations, especially multinationals, have chosen to utilize ISO/IEC 27001/27002 frameworks to help them continually identify security gaps, comply with numerous compliance requirements and obtain international certification.
Requirement: The ISO 27001, a broadly recognized standard for information security management systems (ISMS). While not directly provided by ISO, organizations can obtain third-party certification of compliance with ISO 27001.
TVM Search Pattern: Compliance Framework = ISO/IEC-27001
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| A 6 - Organization of information security |
ISO/IEC-27001|A.6.* |
| A 8 - Asset management |
ISO/IEC-27001| A.8.* |
| A 9 - Access control |
ISO/IEC-27001| A.9.* |
| A10 - Cryptography |
ISO/IEC-27001| A.10.* |
| A11 - Physical and environmental security |
ISO/IEC-27001| A.11.* |
| A12 - Operations security |
ISO/IEC-27001| A.12.* |
| A13 - Communications security |
ISO/IEC-27001| A.13.* |
IT Security Risk Management: A Lifecycle Approach (ITSG-33)
Origin: Released in November 2012, the ITSG-33 publication describes the roles, responsibilities, and activities that help (Government of Canada) GC departments manage IT security risks.
Requirement: The ITSG-33 was developed as a series of guidelines for security practitioners to manage information technology (IT) security risks for Government of Canada (GC) information systems.
Search Pattern: Compliance Framework =
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| CONFIGURATION MANAGEMENT |
ITSG-33|CM* |
| AUDIT AND ACCOUNTABILITY |
ITSG-33|AU* |
| MEDIA PROTECTION |
ITSG-33|MP* |
| SYSTEM AND SERVICES ACQUISITION |
ITSG-33|SA* |
| MAINTENANCE |
ITSG-33|MA* |
| SECURITY ASSESSMENT AND AUTHORIZATION |
ITSG-33|CA* |
| SYSTEM AND COMMUNICATIONS PROTECTION |
ITSG-33|SC* |
| IDENTIFICATION AND AUTHENTICATION | ITSG-33|IA* |
| SYSTEM AND INFORMATION | ITSG-33|SI* |
| CONTINGENCY PLANNING (CONTINUITY PLANNING) | ITSG-33|CP* |
| RISK ASSESSMENT | ITSG-33|RA* |
| ACCESS CONTROL | ITSG-33|AC* |
| INCIDENT RESPONSE | ITSG-33|IR* |
| AWARENESS AND TRAINING | ITSG-33|AT* |
Payment Card Industry Data Security Standard (PCI DSS)
Origin: Released in December 2004, PCI DSS was an industry-led initiative created to better manage cardholder data and reduce credit card fraud. The Standard was defined by the PCI Security Standards Council (PCI SSC), which includes American Express, Visa, MasterCard, Discover, and others.
Requirement: While not a federal regulation, the industry standard is mandatory for all entities that store, process, and/or transmit cardholder data. The standard includes specific cloud computing guidelines which provide guidance on the use of cloud technologies and for maintaining controls in cloud environments.
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| Build and Maintain a Secure Network and Systems |
PCI-DSSV4.0|1.* |
| Protect Account Data |
PCI-DSSV4.0|3.* |
| Maintain a Vulnerability Management Program |
PCI-DSSV4.0|5.* |
| Implement Strong Access Control Measures |
PCI-DSSV4.0|7.* |
| Regularly Monitor and Test Networks |
PCI-DSSV4.0|10* |
NIST Cyber Security Framework (CSF)
Origin: Developed by the National Institute of Standards and Technology (NIST), the NIST Cybersecurity Framework (CSF) is composed of best practice guidelines to help organizations identify, implement, and enhance their cybersecurity practices and use a common language to communicate issues to stakeholders.
Requirement: All federal government agencies and any federal contractors handling government data must be NIST-compliant. Contractors that fail to meet NIST compliance (or have a history of NIST non-compliance) risk losing future contracts.
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| Protect |
CSF|PR.* |
| Respond |
CSF|RS.* |
| Recover |
CSF|RC.* |
| Detect |
CSF|DE.* |
| Identify |
CSF|ID.* |
NIST SP 800-171
Origin: NIST Special Publication 800-171, Protecting Controlled Unclassified Information (CUI) in Nonfederal Information Systems and Organizations, defines the type of security requirements service providers are likely to be contractually obligated to.
Requirement: The U.S. Government must safeguard Controlled Unclassified Information (CUI) and Covered Defense Information. Consequently, civilian agencies and the DoD contractually obligate many nonfederal organizations that process, store, or transmit protected information to comply with NIST SP 800-171. These nonfederal service providers must monitor and assess SP 800-171 controls to obtain permission to operate and safeguard CUI on an ongoing basis.
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| 3. 1 ACCESS CONTROL |
800-171|3.1.* |
| 3. 2 AWARENESS AND TRAINING |
800-171|3.2.* |
| 3. 3 AUDIT AND ACCOUNTABILITY |
800-171|3.3.* |
| 3. 4 CONFIGURATION MANAGEMENT |
800-171|3.4.* |
| 3. 5 IDENTIFICATION AND AUTHENTICATION |
800-171|3.5.* |
| 3. 6 INCIDENT RESPONSE | 800-171|3.6.* |
| 3. 7 MAINTENANCE | 800-171|3.7.* |
| 3. 8 MEDIA PROTECTION | 800-171|3.8.* |
| 3.11 RISK ASSESSMENT | 800-171|3.11.* |
| 3.12 SECURITY ASSESSMENT | 800-171|3.12.* |
| 3.13 SYSTEM AND COMMUNICATIONS PROTECTION | 800-171|3.13.* |
| 3.14 SYSTEM AND INFORMATION INTEGRITY | 800-171|3.14.* |
NIST SP 800-53r5
Origin: The NIST 800-53 provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations.
Requirement: Most U.S. federal information systems must base their security and privacy controls in NIST Special Publication (SP) 800-53, Security and Privacy Controls for Federal Information Systems and Organizations. However, compliance is not limited to the federal government. Many other organizations are required to comply with SP 800-53.
| TVM Compliance Family | TSC Cross Reference |
|---|---|
| AWARENESS AND TRAINING |
800-53|AT* |
| INCIDENT RESPONSE |
800-53|IR* |
| RISK ASSESSMENT |
800-53|RA* |
| ACCESS CONTROL |
800-53|AC* |
| IDENTIFICATION AND AUTHENTICATION |
800-53|IA* |
| SYSTEM AND COMMUNICATIONS PROTECTION | 800-53|SC* |
| CONTINGENCY PLANNING | 800-53|CP* |
| MAINTENANCE | 800-53|CA* |
| SECURITY ASSESSMENT AND AUTHORIZATION | 800-171|3.11.* |
| SYSTEM AND SERVICES ACQUISITION | 800-53|SA* |
| PLANNING | 800-53|PL* |
| CONFIGURATION MANAGEMENT | 800-53|CM* |
| AUDIT AND ACCOUNTABILITY | 800-53|AU* |
| MEDIA PROTECTION | 800-53|MP* |
| PROGRAM MANAGEMENT | 800-53|PM* |
| SYSTEM AND INFORMATION INTEGRITY | 800-53|SI* |
Fortunately, a number of federal and industry sponsored organizations have been established to help enterprise and government organizations improve their cybersecurity posture. These organizations collect best practices and define risk frameworks, as well as supporting cybersecurity controls and benchmarks.
Frameworks provide a set of processes, best practices, and specifications to help organizations assess and manage risk. They lay the foundation for effective cybersecurity programs.
Controls identify ‘what should happen’ in order to mitigate a specific category of risk. Inventory of software assets, data protection, and secure configuration are examples of control categories. Each control category has a set of safeguards outlining what steps should be taken.
Benchmarks take the concept of controls to the next level, providing prescriptive guidance on how to implement and configure specific technology, such as cloud instances, applications, and identities, in a secure way.
In Tenable Vulnerability Management, a user is able to filter their compliance data by compliance framework by using the Compliance Framework filter.
The Compliance Framework filter looks at the Reference Information section of the finding to determine which frameworks the audit check is related to.
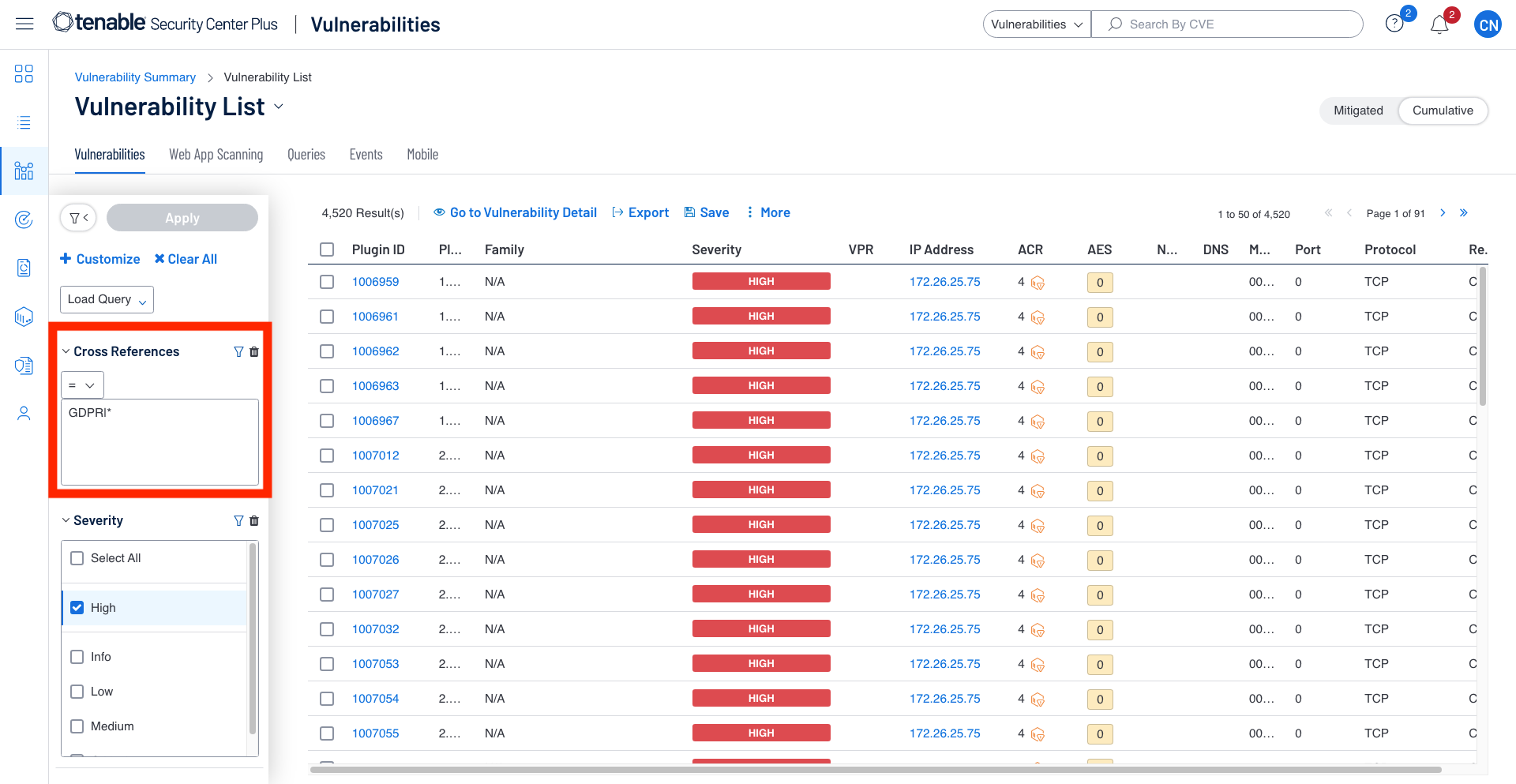
In Tenable Security Center, a user is able to filter their compliance data by compliance framework by using the Cross References filter.
Each of the audit file types has a corresponding plugin ID; however, in Tenable Security Center, the audit file plugin ID is not used. In Security Center when you install an audit file, a new plugin higher than plugin ID 1000000 is created for each check. To retain the audit file type, there is a cross reference called “auditFile." In the Reference Information of the Vulnerability Detail List tool, you can see the auditFile value. When adding a filter for the audit file type, the XREF Type, left side of the pipe (|), is the auditFile type. To the right of the pipe (|), the XREF ID is placed. For example, “auditFile|bluecoat” would locate any audit check used to audit a Bluecoat configuration. There are currently 47 auditFile types:
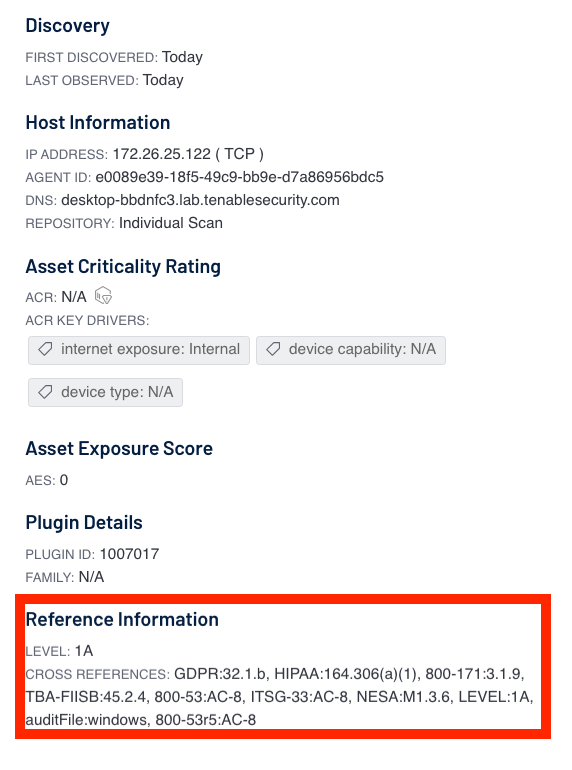
It is important to note that when looking at the cross references in the Vulnerability details section, the cross reference appears to be separated using a colon (GDPR:32.1b); to search for this specific cross reference you would replace the colon with a pipe (GDPR|32.1b).
Understanding Reference Count
An important note analysts should be aware of when using Compliance Framework and Compliance Control (aka Cross-References) to filter host audit findings, is the count that is displayed. Displayed counts in widgets vs. findings can be off from each other depending on how the data is grouped in the widget. This is not an error, but rather the method that is used to filter and display the information.
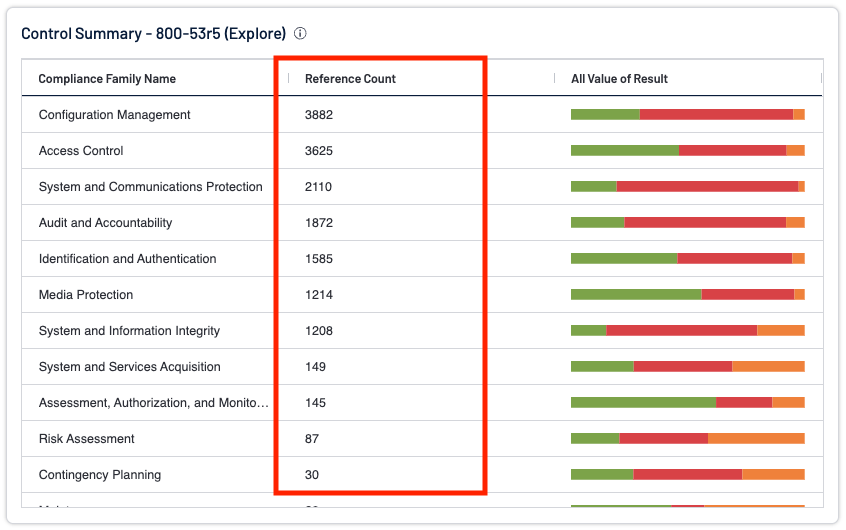
Depending on the specific platform and context, a general "Reference Count" field might be available to count the total number of linked references. The reference count field is commonly found on the “Control Summary” widgets within Tenable Vulnerability Management.
Analysts should understand that this reference count is a direct correlation between the Control Summary Family and the number of references identified. The Reference Count may be a different number than what is displayed in the Findings page when you drill down into the results. In order to explain this behavior the analyst should completely understand how and where this count is generated.
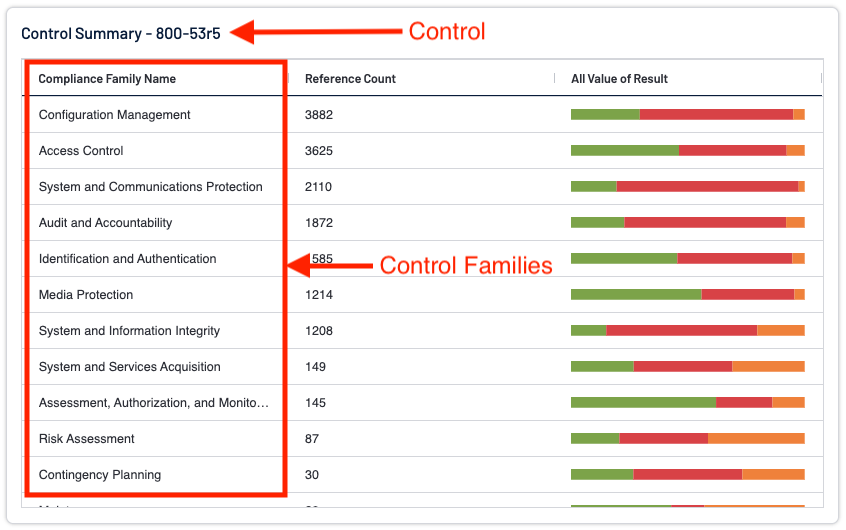
For this example, the NIST 800-53r5 Control is broken down into over 1,000 Controls and 20 specific Control Families. The Control and Control Families for NIST 800-53r5 are shown below.
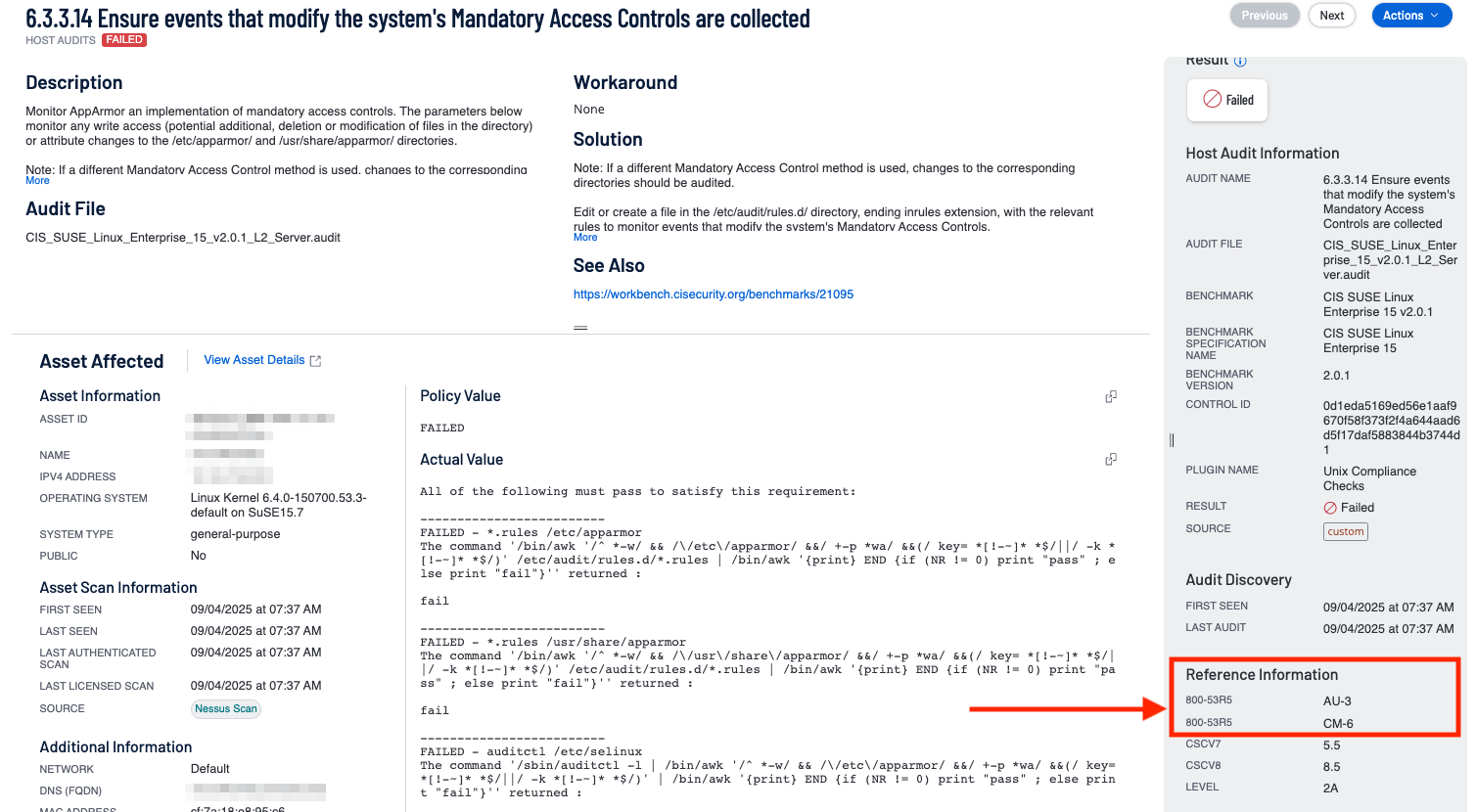
If we select to drill down into Configuration Management we can see this easily when we expand a Finding and review the details.
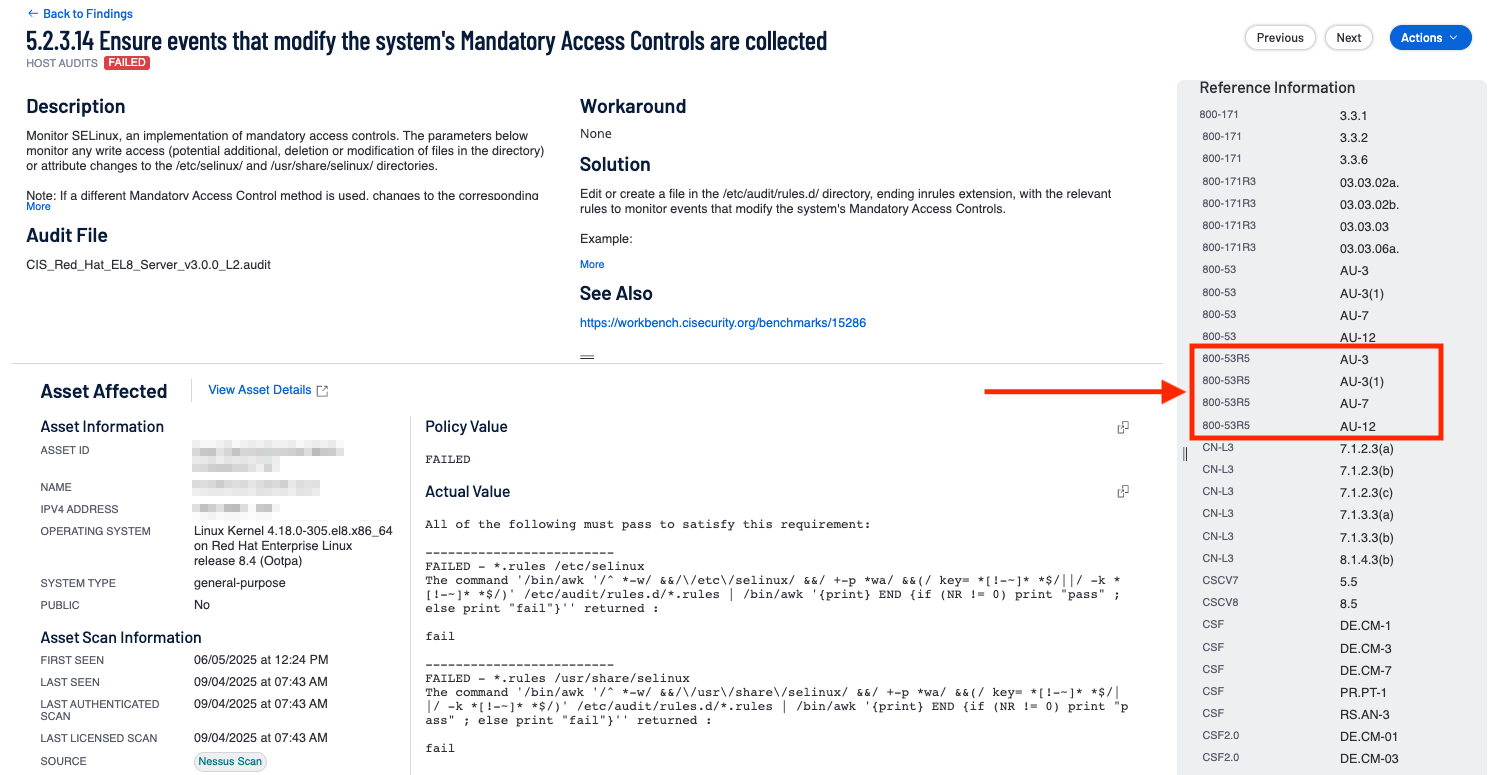
In the case above, the analyst will note that there are two references listed in the reference section for 800-53r5. One for AU-3 (Content of Audit Records Control), which we will call Reference One, and one for CM-6 (Configuration Settings), which we will call Reference Two. This means that this finding is associated with both AU-3, and CM-6 controls of the 800-53r5 specification, even though there is only a single audit check finding. This finding would be present in the drill down and Reference Count on the Control Summary widget in both the Configuration Management and Audit and Accountability Control Family. Yet this is a single finding.
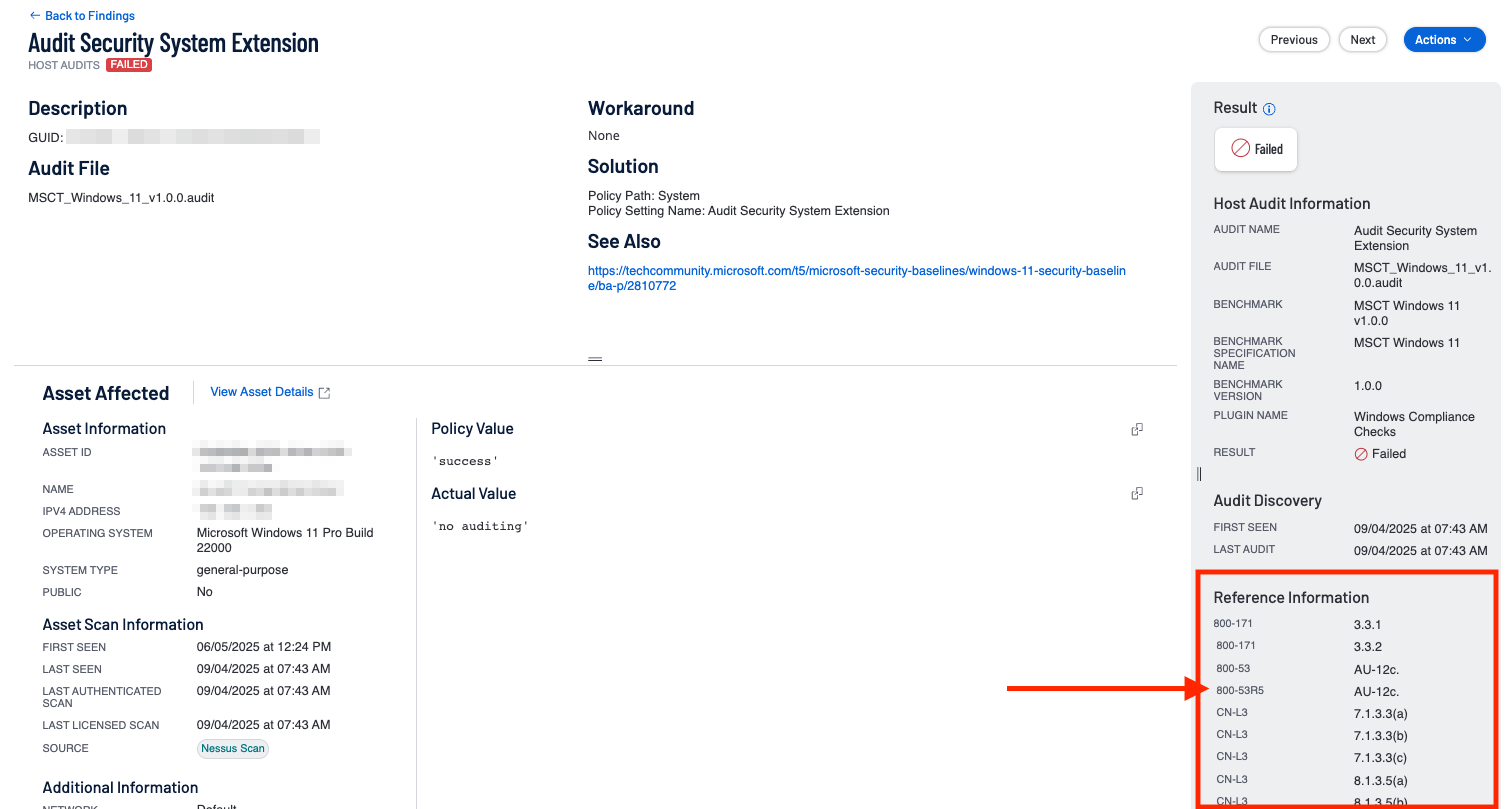
In some cases there may be only a single Control Family being referenced. On this particular finding for the ‘Audit Security System Extension’, a single reference is listed for 800-53r5 AU-12c (Audit Record Generation, specifically their standardized format).
When more than one reference is present, the corresponding count displayed in the Reference Count column will be cumulative. In the following example there are multiple (4) references for the Audit and Accountability family for this single finding.
In this example, the reference count would display a count of 4 in this family, but clicking into the findings will only display a single finding.
In many cases, when attempting to meet requirements set forth by specific standards, the most beneficial data to have is the number of pass/fail or attributable findings which are associated with a specific reference. For example, “How do we look against 800-53r5 AU-3?” Therefore the Reference Count filter is commonly used to present this information.