2-1: Asset Management
The diverse location of assets makes the process of discover and identify assets very challenging. Understanding where critical assets are and accurately inventorying assets is the crucial first step in RBVM. Through credentialed scanning, assets can be reliably identified and attributes collected, which enables organizations to establish and validate inventory management. Tenable Vulnerability Management helps validate and collect information needed to maintain a healthy asset inventory. As assets are discovered, an organization can begin to establish an inventory, which can be used to assess and mitigate associated risks to the organization.
For domain 2-1, The National Cybersecurity Authority states:
“To ensure that the organization has an accurate and detailed inventory of OT/ICS assets in order to support the organization’s cybersecurity and operational requirements to maintain the production uptime, safe operations, confidentiality, integrity, and availability of OT/ICS assets.”
Attackers are not tied to a specific timezone and are continuously scanning the address space of target organizations, searching for new and possibly unprotected systems to be attached to the network. Transient devices, such as laptops or Bring-Your-Own-Device (BYOD) devices may be out of synchronization with security updates or already compromised providing a ripe attack vector. Often, hardware may be installed on the network one evening but not configured and patched with appropriate security updates until the following day, providing an easy target for exploitation. Devices that are not visible from the internet can be exploited by attackers who have already gained internal access and are hunting for internal pivot points.
Maintaining a comprehensive and up-to-date asset inventory is a fundamental and critical component of RBVM. Modern IT environments encompass on-premises, cloud infrastructure, mobile devices, ephemeral and transient assets, web applications, IoT devices, and more. Asset identification of all connected assets within an organization is a common baseline requirement in Essential Cybersecurity Controls (ECC) and OTCC. Maintaining an asset inventory is also the critical first step in the Discovery phase of RBVM, allowing organizations to be more proactive. This document provides guidance to establish an asset inventory.
The first step of RBVM begins with asset discovery to identify and map every asset across the environment. Devices can be detected through active scanning and analysis with Nessus Tenable OT Security to build a comprehensive list of assets and provide a clear picture of risk in the environment.
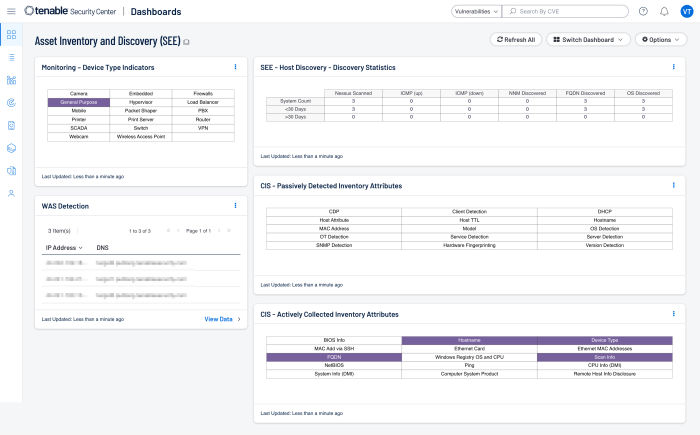
The Asset Inventory & Discovery (SEE) Tenable Security Center dashboard provides guidance to establish an asset discovery, including:
-
Actively and passively detected assets
-
Asset discovery statistics
-
Detected web applications
-
Indications for device types (printers, cameras, routers, firewalls, WAPs)
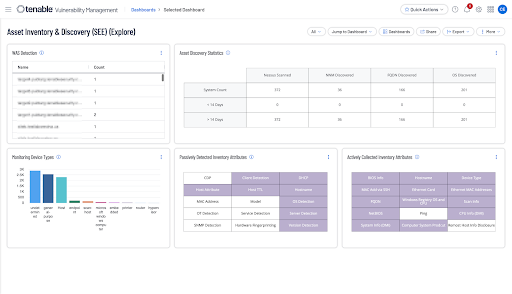
An equivalent to this dashboard also exists within Tenable Vulnerability Management:
In sub-domain 2-1-1-4, asset owners must be identified and must be involved in through all the inventory and management of their assets. Oftentimes organizations have teams that focus on the detailed information relevant to the teams' assets; or operational focus areas, such as Windows, Linux, databases, or network infrastructure. The dashboard components do not require specific asset list filters to be applied before use. However, organizations with teams that focus on a specific group of assets benefit from using custom asset lists. Information security teams can visualize findings against assets that are "owned by" or "assigned to" specific teams within the organization using this method. Additionally, an Output Assets filter can be set to provide greater insight into where additional resources need to be allocated to mitigate vulnerabilities.
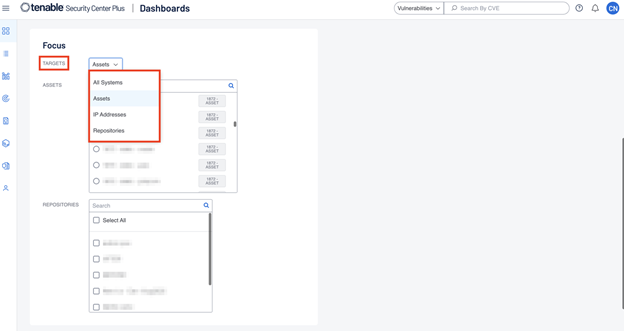
When adding a dashboard in Tenable Security Center from the template library, a focus can be applied to the dashboard to filter the data further. You can change the selection in the Targets drop-down from All Systems to Assets, IP Addresses, or Repositories:
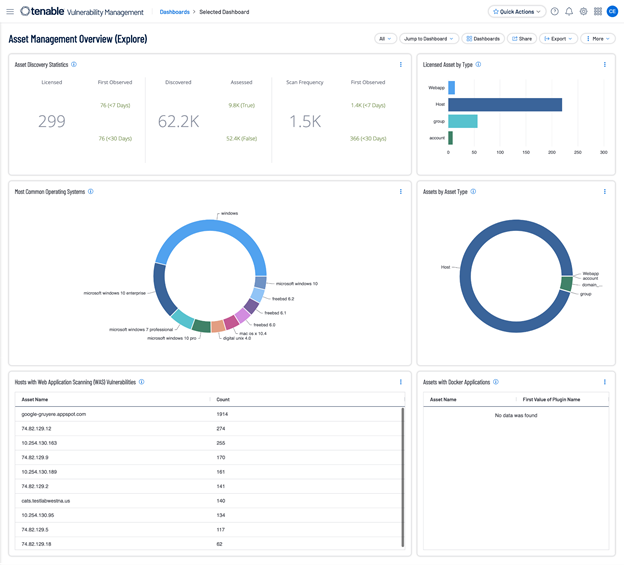
Furthermore, organizations must know the status of critical assets to ensure they are appropriately monitored and protected based on each asset’s business risk rating. The Asset Management Overview dashboard provides summary information about assets in the environment. This information can be leveraged by risk and security managers to ensure the organization’s security program is aligned with current business goals.
According to sub-domain 2-1-1-5 of the OTCC, criticality ratings must be assigned to each asset as well as approved by their owners. Tenable assigns an Asset Criticality Rating (ACR) to each asset on the network. ACR assists in prioritizing each asset based on indicators of business value and criticality. ACR is based on several key metrics such as business purpose, asset type, location, connectivity, capabilities, and third-party data. ACRs range from 0 to 10. Assets with a low ACR are not considered business critical. Assets with a high ACR are considered to be the organization’s most critical and carry the greater business impact if compromised. The ACR can also be adjusted by the user if deemed the rating needs to be different.
Another asset related metric Tenable established is the Asset Exposure Score (AES). Tenable calculates a dynamic AES for each asset on the network to represent the asset's relative exposure as an integer between 0 and 1000. A higher AES indicates higher exposure. The AES score is derived from the current ACR (whether tenable provided or custom) and the Vulnerability Priority Ratings (VPR) associated with the asset.
OT Security's Automated Asset Discovery, Classification, and Management provides an accurate, up-to-date asset inventory by continuously tracking all changes to devices. This simplifies sustaining of operational continuity, reliability, and safety. OT Security also plays a key role in planning maintenance projects, prioritizing upgrades, patch deployments, incident response, and mitigation efforts.
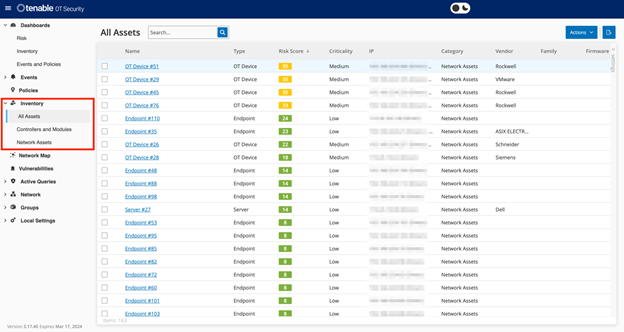
All of the assets in the network are shown on the Inventory screen. Detailed data about each asset is shown, enabling comprehensive asset management as well as monitoring of the status of each asset and its related Events. The data shown in the Inventory screen is gathered using the OT Security Network Detection and Active Query capabilities. The All screen shows data for all types of assets. In addition, specific subsets of the assets are shown on separate screens for each of the following asset types: Controllers and Modules, Network Assets, and IoT. For each of the asset screens (All, Controllers and Modules, Network Assets and IoT), you can customize the display settings by adjusting which columns are displayed and where each column is positioned. You can also sort and filter the Asset lists as well as perform a search.
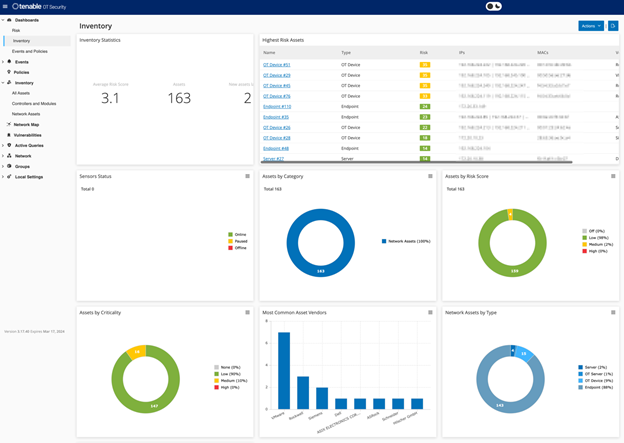
Additionally, there are three dashboards: Risk, Inventory, and Events and Policies. The dashboards contain widgets that offer an at-a-glance view of your network’s inventory and security posture. You can choose a dashboard from the Main Navigation or by clicking on the Dashboards button in the upper right corner, and selecting one from the menu that is shown. The Risk dashboard is the initial default view. However, you can change the default view to a different dashboard.
The Inventory dashboard provides visibility into the asset inventory, facilitating asset management and tracking. The Inventory dashboard shows widgets such as: Highest Risk Assets, Inventory Statistics, Assets by Risk, Controllers, and Modules by Type, Assets by Purdue Level, etc. Clicking on an asset link takes you to the corresponding asset on the Inventory screen.