1-3: Cybersecurity Risk Management
The OTCC sub-domain 1-3 expands on the ECC 1-5 which states:
“To ensure managing cybersecurity risks in a methodological approach in order to protect the organization’s information and technology assets as per organizational policies and procedures, and related laws and regulations.”
Tenable assists organizations in following a Risk-Based Vulnerability Management (RBVM) approach. RBVM is a process that reduces vulnerabilities across the attack surface by prioritizing remediation based on the risks they pose to the organization. Unlike legacy vulnerability management, risk-based vulnerability management goes beyond just discovering vulnerabilities. RBVM provides the context needed to help organizations understand vulnerability risks with threat context and insight into potential business impact.
Legacy vulnerability management solutions weren't designed to handle the modern attack surface and the increasing threats. The attack surface is no longer just traditional IT assets, but also includes mobile devices, web apps, cloud infrastructure, containers, Internet of Things (IoT) devices and operational technology (OT) assets. In these modern networks, legacy vulnerability management tools can’t deliver complete and timely insights into all of the devices across the entire attack surface. By not identifying these assets and their threat vectors, the organization has unassessed risks and which increases Cyber Exposure.
RBVM reduces guesswork, by taking a risk-based approach to vulnerability management, the security team can focus on the vulnerabilities and assets that matter most and address the organization’s true business risk instead of wasting valuable time on vulnerabilities attackers may not likely exploit.
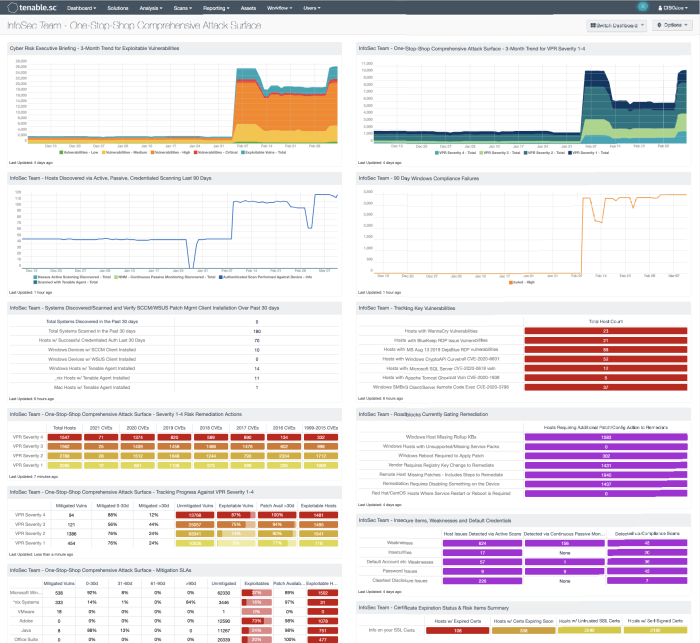
The InfoSec Team - One Stop Shop Comprehensive Attack Surface dashboard in Tenable Security Center helps the InfoSec team maintain a high level of awareness and vigilance. The filters and components are tailored to guide teams in detecting, predicting, and acting to reduce risk across their entire attack surface. Analysts within information security teams are empowered to analyze findings, remediate identified risks, track progress, and measure success against the organization's charter and SLAs. According to sub-domains 1-3-1-2 within the OTCC, and 1-5-4 within the ECC, risk assessments must be done periodically.
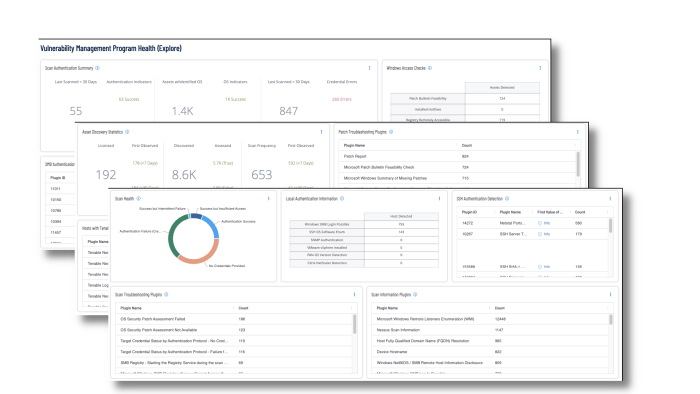
OTCC 1-3 requires risk assessments to be performed on a regular basis, and for most systems that can be actively scanned, this requirement is sustainable; however, in terms of OT devices which can be more fragile systems and cannot be actively scanned, Tenable OT Security can be used to monitor these systems for vulnerabilities and track behaviors. Tenable Vulnerability Management dashboards such as the Vulnerability Management Program Health dashboard, helps security operations teams ensure their scanning program is appropriately maintained for an evolving operational technology landscape aligned with business strategy.
The Output Assets filter is only available when using the Asset Summary Tool. When this tool is selected, you have the option to refine the filters to include specific Asset information.
Credentialed or agent scanning with privileged access provides the most comprehensive and accurate scanning results. Credentialed scans originate from a Tenable Nessus scanner that reaches out to the hosts targeted for scanning, while agent scans run on hosts regardless of network location or connectivity and then report the results back to the manager. Credentialed scanning is more complicated than agent scanning and requires authentication with sufficient privileges to enumerate software, installed applications, patch status, and identify configuration problems. Tenable uses multiple protocols, such as SMB, SSH, HTTPS, and SNMP, to conduct authenticated scans against assets. Analysts can drill into the summary information displayed in the dashboard to troubleshoot upstream scanning problems that can adversely impact downstream reporting to stakeholders.
Very often critical business assets are added to the environment without the knowledge of the security or IT teams. Drilling into the data for assets that are discovered but not scanned can reveal assets with a high criticality rating that are not being scanned.