2-9: Vulnerabilities Management
The objective for domain 2-9, The National Cybersecurity Authority states:
“To ensure timely detection and effective remediation of technical vulnerabilities to prevent or minimize the probability of exploiting these vulnerabilities to launch cyber-attacks against the organization.”
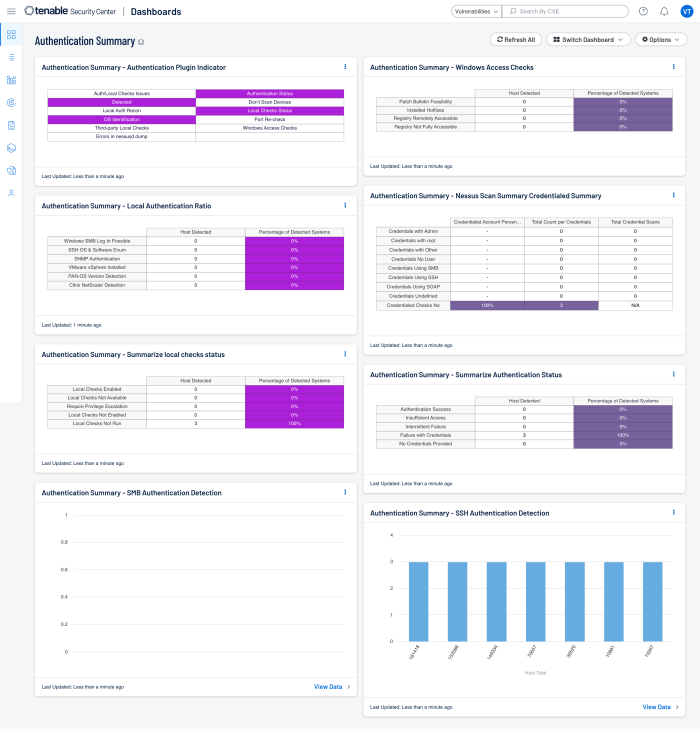
Understanding Cyber Exposure requires that the data collected by Tenable Vulnerability Management is trusted and verifiable. Tenable Vulnerability Management and Tenable Security Center provide several plugins that assist in determining scan status and provides a level of trust for risk managers. The Authentication Summary Tenable Security Center dashboard provides a clear and simplified method to track and troubleshoot authentication-related problems. The dashboard groups authentication plugins into diagnostic contexts to show administrators areas of concern to focus on.
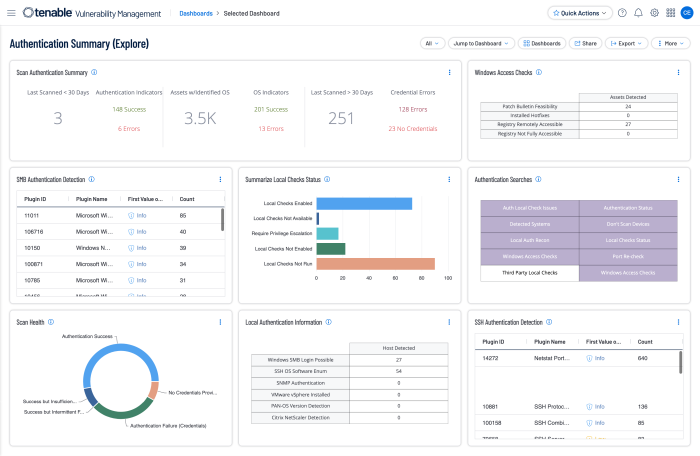
The Authentication Summary (Explore) Tenable Vulnerability Management dashboard brings together all the plugins used to verify successful authentication of assets during vulnerability scans, providing security administrators visibility into areas of concern so that the appropriate actions can be taken.
Local checks are required to ensure that scans are complete and accurate. Users enable local checks by providing credentials with elevated privileges, or administrative access, or by deploying Nessus Agents. Tenable Vulnerability Management requires privileged access to provide a comprehensive assessment of risk on an asset. The more access to a system Tenable Vulnerability Management has, the more complete the vulnerability detection.
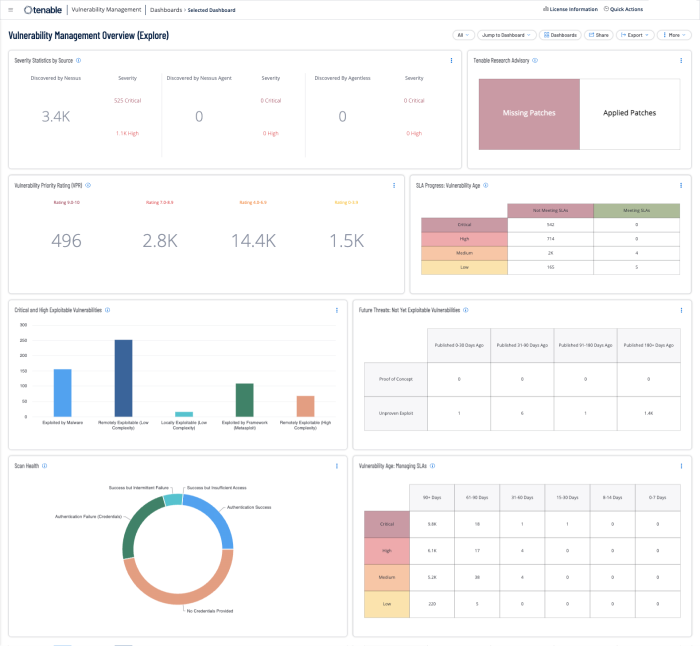
The Vulnerability Management Overview Tenable Vulnerability Management dashboard provides executive management a summary of risk information at a glance, while enabling security analysts to drill down into technical details by clicking on the widgets.
The widgets in this dashboard provide detailed information on vulnerability severity and mitigation status. Information is provided to help Risk Managers determine compliance with Service Level Agreements. Security Analysts can use the information in the Scan Health widget to determine if scans are running as intended to ensure the accuracy of scan data. Executive Management and Security Analysts can leverage the information provided in this dashboard to ensure their vulnerability management program aligns with organizational goals.
Organizations cannot begin to fix systemic problems within their security program without first being able to analyze the data collected by the vulnerability scanning tool. OTCC 2-9 requires the monitoring of vulnerabilities and identification of OT/ICS unsupported software. Tenable Security Center uses active and passive detection methods to bring continuous visibility and provide prioritization actions based on business risk and asset discovery.
As networks converge between Information Technology (IT) and Operational Technology (OT), organizations struggle to have complete visibility of the network. Using Tenable OT Security and Tenable Vulnerability Management or Tenable Security Center together, the complete picture of a network is visible to risk managers and CISOs. Both Tenable Vulnerability Management and Tenable Security Center are able to connect with Tenable OT Security and incorporate risk scores such as VPR and Common Vulnerability Scoring System (CVSS) vectors to fully understand risk.
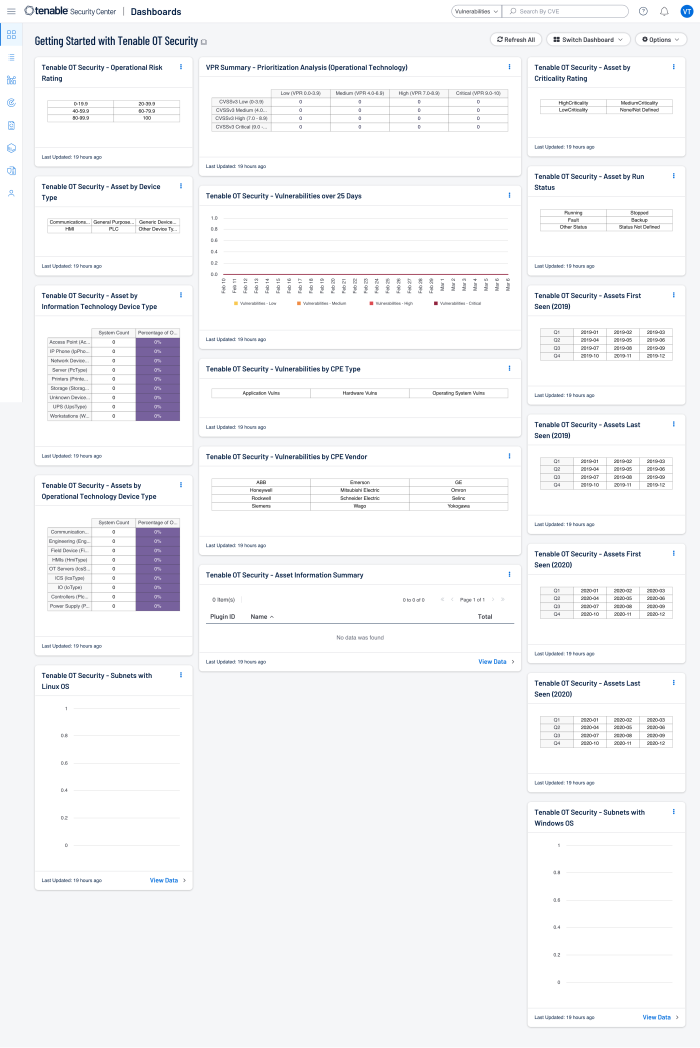
Tenable Security Center has a dashboard called Getting Started with Tenable OT Security:
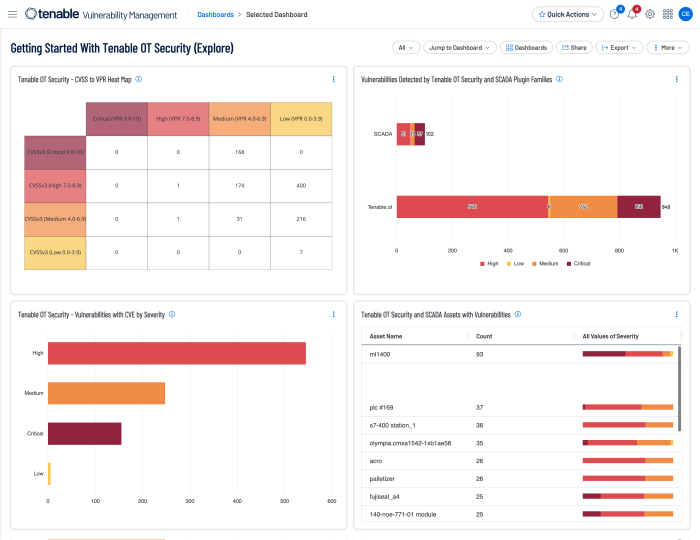
In the first row of components, the dashboard provides the added value of combining the two systems together. By showing the correlation of the Risk Ratings, CVSS, VPR, and criticality ratings, the risk managers are able to gain a clear understanding of the overall IT/OT risk.
On the left side of the dashboard there are two components that show the percentage of systems with respect to IT and OT asset classification type. Each component has a column for the system count and overall percentage. The components in the middle of the center column use the Common Platform Enumeration (CPE) detections. This attribute is part of the vulnerability plugin and can denote hardware, applications, or operating system vulnerabilities. In addition, the CPE contains manufacture information.
System managers can use this information as a starting point for vulnerability analysis and patch management efforts. In the right-hand column, there are four components that track when an asset is first discovered on the network and when last seen. These two attributes help asset managers track when new systems are detected and if the system is in current use. The bottom components use the Asset Identification plugins to show a summary of the device types detected, and the operating systems used.
Organizations are afforded the opportunity to perform risk analysis based on OT and IT data in a single unified platform with Tenable OT Security and either Tenable Vulnerability Management or Tenable Security Center. In the top row of The Getting Started with Tenable OT Security dashboard in Tenable Vulnerability Management, the CISO is able to quickly see the status of OT assets by the total number of assets detected, critical, and high severity vulnerabilities, and the criticality rating and run status. The criticality rating is established by default per the device type; however, this rating can be modified as needed.
As the role of the risk manager expands to include OT devices, the next row of widgets presents the data in a more vulnerability management-based view. The ring chart shows the most common vulnerabilities based on the total count of affected assets, and the matrix shows a heat map view aligning CVSS and VPR. By viewing the correlation of the Risk Ratings, CVSS, VPR, and criticality rating, risk managers are able to gain clear understanding of their overall IT/OT risk.
The Cyber Exposure Lifecycle begins with the Discovery phase, where the objective is to map and identify assets across the organization. The next two rows provide counts and summary lists of assets by discovery classifications, such as the Purdue Levels, Device Type, OT Type, and IT Type.