Identity and Access Control
Identity and access control are fundamental concepts within information security and system management. Identity refers to the digital representation of a person, device, or entity accessing a system or network. Examples include usernames, email addresses, and digital certificates. Access control is the process of regulating and restricting access to resources or services based on the identity of users or devices. Access control ensures that only authorised users, processes, or systems can access certain resources or perform specific tasks.
Concepts within identity and access control include identity management which is the process and technologies used to create, manage, and authenticate identities throughout the identity lifecycle. Access control typically includes mechanisms such as authentication, authorization, and auditing. These mechanisms verify the identity of users, determine what resources are available to authorised users, and monitor access for security and compliance purposes.
Identity and access control work together to ensure that the correct individual or systems have the appropriate access to resources, while safeguarding against unauthorised access and potential security breaches. These concepts are crucial for maintaining the confidentiality, integrity, and availability of information within the organisation's network.
The following sections within the NIS 2 may be best suited to fall into the Identity and Access Control category:
-
Article 21(2) (j): Use of Multi-Factor Authentication or Continuous Authentication Solutions: Multi-factor Authentication (MFA)
Tenable Identity Exposure provides various methods to access the information collected through the Indicators of Exposure (IoE) and Indicators of Attack (IoA) panes. Tenable Vulnerability Management provides the ability to use the Explore Findings through the use of dashboards and reports.
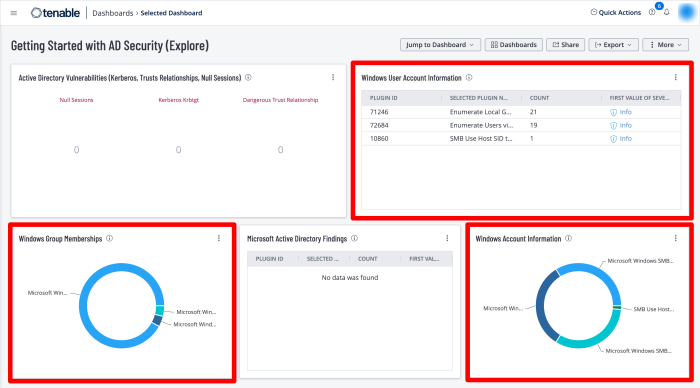
To begin taking control of the organisation’s Identity Management, every account within the environment must be enumerated. The level of access for each account must also be determined. All accounts must be uniquely identified and assigned to particular entities, such as users and applications.
The Getting Started with AD Security dashboard in Tenable Vulnerability Management contains widgets to enumerate user accounts.
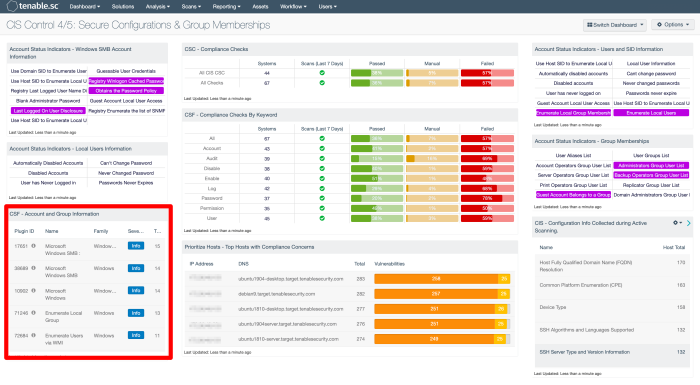
Organisations can also use the CSF - Account and Group Information widget located in the CIS Control 4/5: Secure Configurations & Group Memberships dashboard in Tenable Security Center, which leverages plugins that enumerate Windows account information.
Operating Systems and applications are often distributed with service and default accounts that are either not password-protected or having a default password that is well known. Tenable Nessus and Tenable Identity Exposure help identify these accounts, enabling organisations to review and disable any unnecessary accounts to reduce the attack surface. Organisations can leverage the following Nessus plugins to enumerate service and default accounts:
-
Plugin Family: Default Unix Accounts – This plugin family contains over 170 Nessus plugins that check for the existence of default accounts/passwords on a number of devices. In addition, there are many plugins that check for simple passwords such as “0000”, “1234”, and more commonly identified password combinations for “root” or administrator accounts.
-
171959 Windows Enumerate Accounts – This plugin enumerates all Windows Accounts
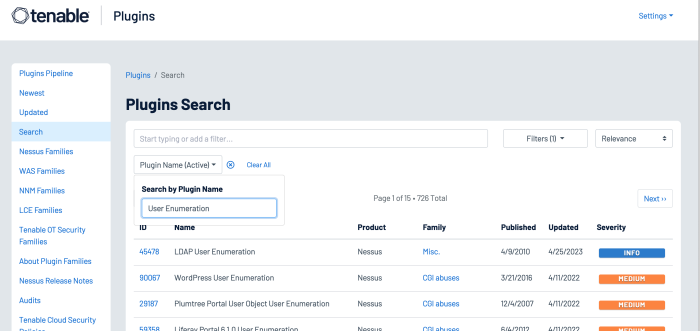
Several hundred plugins can be identified by searching for “Default Account” from the Nessus Plugins Search page using the Enable Default Logins filter. Nessus default account plugins are available for Databases, Web Servers, SCADA devices, Unix/Linux devices, Cisco devices and more. Many of the plugins are associated with the Default Unix Account Nessus family, however, many are in other families as well.
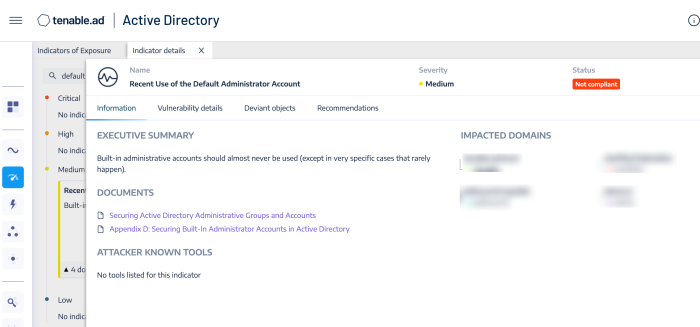
In addition, Tenable Identity Exposure provides the ability to determine if a default administrator account was recently used in the environment, as shown in the image below:
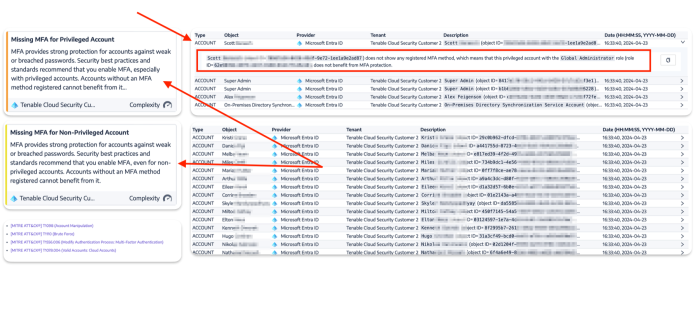
Tenable Identity Exposure is also able to determine if items such as MFA are being used. In this example, a privileged account with a Global Administrators role does not have a registered MFA method. The user account and detailed information on the vulnerability are present to assist organisations mitigate the identified concerns.
Depending on the threat level of the misconfiguration, the Indicator of Exposure (IOE) will rise in a different category: Critical – High – Medium – Low. This provides the context required to minimise distractions. Organisations are able to effectively investigate incidents, hunt for threats, and manage and prioritise security challenges that pose the greatest threats.
For more information on Tenable Identity Exposure review the documentation located here.
For more detailed information review the Identity and Access Management Cyber Exposure guide found here.
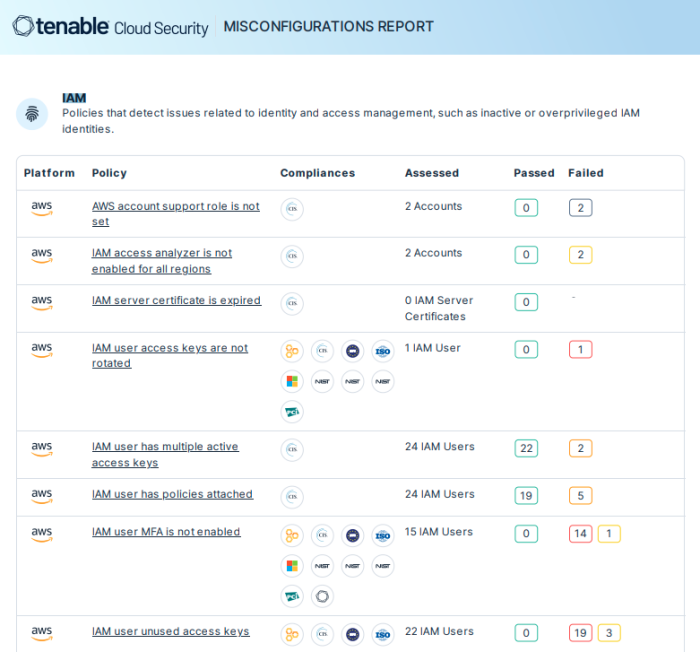
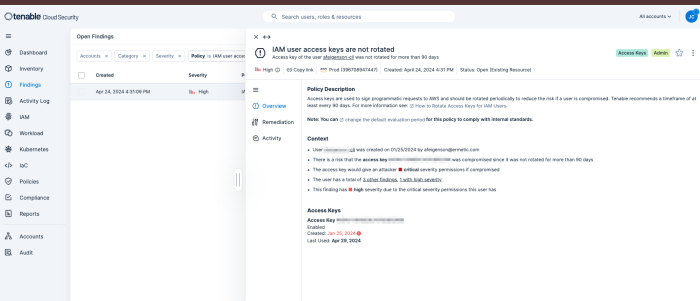
Tenable can discover Identity assets and check access policies violation, or excessive privileges on both on-premises AD/EntraID and public clouds (AWS, Azure, GCP) Tenable Cloud Security provides this information via misconfiguration reports for identity and access management, as shown below.
Details within each policy violation contain an overview, policy violation details, and policy remediation strategies, as well as defining any impacted resources. Policies are used to identify misconfigurations and vulnerabilities present on cloud resources. Tenable Cloud Security has built-in policies for cloud and IaC resources that define the compliance standards for your cloud and IaC infrastructure. Related policies are combined within a policy group. A policy can support multiple benchmarks. Therefore, a policy group includes all the benchmarks supported by the policies in the group.
A full list of Tenable Cloud Security policies is available online located here.
For more information on getting started with Tenable Cloud Security, see the Tenable Cloud Security User Guide.
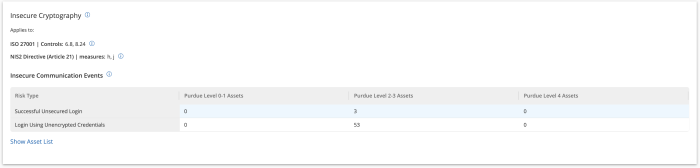
The Insecure Cryptography widget for Tenable OT, located on the compliance dashboard provides an overview of suspicious unauthorised activities at the network’s different levels. This widget assists organisations monitor and detect insecure cryptographic events to prevent compromise of sensitive information and service disruption. Key items displayed are Successful Unsecured Logins and Logins Using Unencrypted Credentials, and high risk assets with these events.
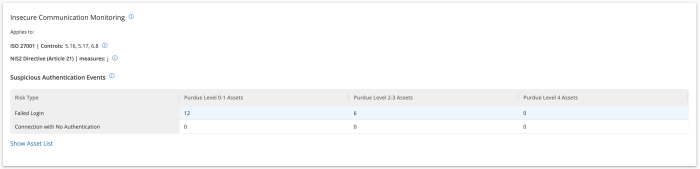
The Insecure Communication widget also for Tenable OT, located on the compliance dashboard assists organisations in avoiding any insecure communications and suspicious unauthenticated access. Insecure communications can leave sensitive information or critical assets vulnerable to interception and exploitation by attackers. Unauthenticated access may be a trigger to alert organisations to problems resulting from a potential breach, misconfigured security settings, or unauthorised activity. Key items displayed are Failed Logins and Connections with No Authentication.
The following cross-reference information is provided to derive a more comprehensive and effective approach to managing information security requirements. NIS 2 Article 21(2) (j) references security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2) (j), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Protection
SECURITY SUB-DOMAIN: Identity and access management
SECURITY MEASURE: Authentication and identification
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (j) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for identity and access management. The following cross-references cover the processes and procedures related to identity, access management, and authentication and identification.
CROSS REFERENCES:
The ISO 27001 references sections within Annex A, Information Security Controls Reference, specifically the following sections:
-
ISO 27001 (A.9.1, A.9.3, A.9.4.1, A.9.4.2, A.9.4.3)
The NIST CSF references the following sections within Protect.
-
NIST CSF (PR.AC-1, 4,6, 7, PR.DS -5)
The ISA/IEC 62443 references several sections related to Identification and Authentication, Use Control, and Zone Boundary Protection.
-
ISA/IEC 62443 (SR 1.1, SR 1.2, SR 1.3, SR 1.4, SR 1.5, SR 1.6, SR 1.7, SR 1.8, SR 1.9, SR 1.10, SR 1.11, SR 1.12, SR 1.13, SR 2.1, SR 2.2, SR 2.3, SR 2.4, SR 2.5, SR 2.6, SR 2.7, SR 5.2)