Security Hygiene Practices
Information security hygiene refers to a set of practices and behaviours that organisations adopt to maintain their data security integrity. Several sections within the NIS 2 may be best suited to fall into the Risk Assessment category. Those include:
-
Article 21(2) (g): Basic Cyber Hygiene Practices and Cybersecurity Training: Cyber Hygiene.
-
Article 21(2) (h): Policies and Procedures regarding the use of cryptography, and appropriate encryption.
The practice encompasses a series of proactive measures designed to protect systems, networks, and data from threats, vulnerabilities, and unauthorised access. Good security hygiene practices include:
-
Password and Authentication: Using strong, unique passwords, and implementing multi-factor authentication (MFA) where possible.
-
Software Updates and Patching: Regularly updating operating systems, software applications, and firmware to protect against known vulnerabilities.
-
Backup and Recovery: Maintaining secure backups of critical systems and data, to ensure resilience against data loss due to accidents, malware, or ransomware attacks.
-
Network Security: Security networks with firewalls, intrusion detection/prevention systems, and virtual private networks (VPN) to defend against unauthorised access.
-
Awareness and Training: Educating users about security best practices, phishing scams, and social engineering tactics to reduce the likelihood of security breaches.
-
Device Management: Managing endpoint devices with encryption policies and secure configurations.
-
Access Control: Limiting access to sensitive information and resources based on the principle of least privilege to minimise exposure.
-
Incident Response Planning: Establishing protocols and procedures to quickly detect, respond, and recover from security incidents.
-
Compliance and Regulation: Adherence to relevant industry regulations and standards (GDPR, HIPAA) to ensure legal and regulatory compliance of data handling.
Establishing and maintaining good security hygiene practices is essential to mitigate risks and safeguard organisational assets from increasingly sophisticated threats.
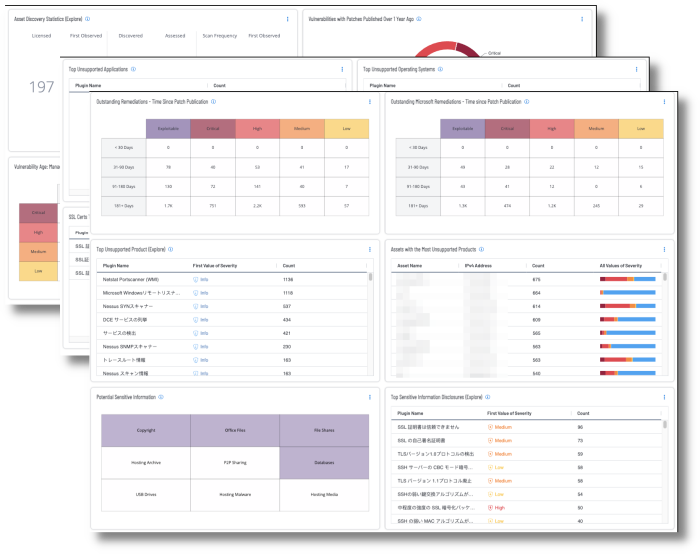
Basic cyber hygiene includes the need to cover basic scenarios, such as knowing what assets are in the environment and asserting what vulnerabilities may lurk within. Without knowing what vulnerabilities are present, analysts cannot ensure that the correct security controls are in place to mitigate or remove the vulnerability. Attackers may use such an opportunity to exploit the vulnerability to steal confidential information. When organisations lack this knowledge or are not aware of other threats such as lack of hardening systems to a common standard, large gaps of security can reside in critical points of infrastructure.
Unsupported products, operating systems and applications are a major cause of data breaches. The proliferation of unsupported and end-of-life (EOL) products is a common security problem experienced across all organisations. As applications and operating systems reach EOL, vendors stop offering support, causing security and stability to decrease over time. A comprehensive summary of unsupported products in the environment is provided.
Another major concern is visibility into the assets in the environment and how effectively vulnerabilities on those assets are managed. As vulnerabilities are identified, remediation must be prioritised and tracked in accordance with organisational goals and Service Level Agreements (SLAs). Reviewing remediated vulnerabilities and the remediation timeframe provides valuable information to the organisation on the effectiveness of the risk remediation program. Vulnerabilities that are known to be exploitable are dangerous, since there are exploit frameworks readily available to exploit them.
Tenable brought together a group of dashboards described in the “Tenable Solutions for the Cyber Hygiene Campaign” technical paper. These dashboards relate to the five actions identified by the Cyber Hygiene Campaign along with helping an organisation fulfil basic security needs such as monitoring.
For Tenable Security Center those dashboards are the Cyber Hygiene Dashboards.
The focus of these Cyber Hygiene dashboards is:
Inventory Authorised and Unauthorised Devices: Identifying systems on the network can be a monumental task, as many organisations have different groups responsible for system inventories. This collection of components provides information to analysts and auditors about systems discovered on the network and device inventory.
Inventory Authorised and Unauthorised Software: A good vulnerability management program requires that an organisation also know the software installed on its systems. This dashboard and its components provide information to analysts about software that is discovered on the network.
Develop and Manage Secure Configurations for all Devices: Hardening and configuration guidelines can be difficult to create and to maintain. There are several industry standards available to organisations such as NIST 800-53, CIS, and CSC. Tenable has the ability to audit system configurations according to the standards. The components in this dashboard use forensic plugins, detections, and compliance checks to provide information about how systems are configured.
Conduct Continuous Vulnerability Assessment and Remediation: Detecting vulnerabilities requires a diligent information security team and the ability to detect vulnerabilities in several ways. Tenable has the ability to monitor for vulnerabilities using active, passive, and event-based detection.
Actively Manage and Control the Use of Administrative Privileges: A common problem found in networks is that too many accounts with administrative privileges exist. Organisations should make an effort to use dual accounts when administrative rights are to be used. This dashboard provides information about which users have administrative control and how this control is used.
For Tenable Vulnerability Management that dashboard is the Fundamental Cyber Hygiene Report Card.
Unsupported products, operating systems and applications are a major cause of data breaches. The proliferation of unsupported and end-of-life (EOL) products is a common security problem experienced across all organisations. As applications and operating systems reach EOL, vendors stop offering support, causing security and stability to decrease over time. A comprehensive summary of unsupported products in the environment is provided.
Another major concern is visibility into the assets in the environment and how effectively vulnerabilities on those assets are managed. As vulnerabilities are identified, remediation must be prioritised and tracked in accordance with organisational goals and Service Level Agreements (SLAs). Reviewing remediated vulnerabilities and the remediation timeframe provides valuable information to the organisation on the effectiveness of the risk remediation program. Vulnerabilities that are known to be exploitable are dangerous, since there are exploit frameworks readily available to exploit them. Details are included on vulnerabilities where a patch to remediate the exposure was available more than a year ago.
Data on secure communication controls for sensitive information is provided. The status on SSL certificates that are aged out or soon to be aged out is shown, along with SSL and TLS insecure communication exposures in the environment. Information about exposure of various types of potentially sensitive information is provided. Many organisations are unaware how much sensitive information is exposed, which enables attackers to tailor an attack path specifically targeting the organisation, leading to data loss exposures.
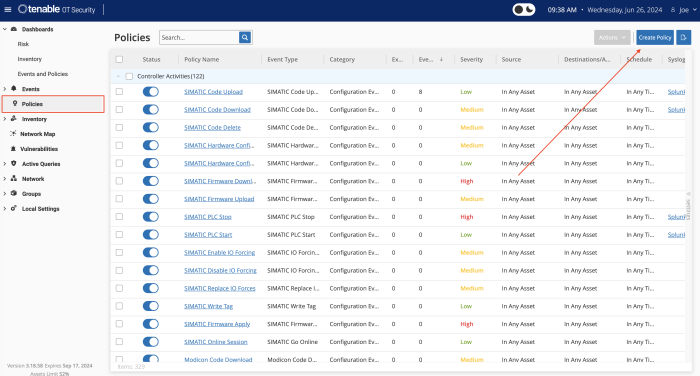
Tenable OT Security includes policies that define specific types of events (aged out certificates, Clear Text transmission, No MFA, and many more) that are suspicious, unauthorised, anomalous, or otherwise noteworthy that occur in the network. When an event occurs that meets all of the Policy Definition conditions for a particular policy, the system generates an event. The system logs the event and sends notifications in accordance with the Policy Actions configured for the policy. Triggered events based on these policies are then available in the Events page, along with additional details and mitigation techniques.
To configure a policy navigate to the Policy Page, then select the Create Policy icon in the top-right area of the dashboard. Follow the prompts to create and then enable the policy. Each policy consists of a series of conditions that define a specific type of behaviour in the network. This includes considerations such as the activity, the assets involved, and the timing of the event. Only an event that conforms to all the parameters set in the policy triggers an event for that policy. Each policy has a designated Policy Actions configuration, which defines the severity, notification methods, and logging of the event.
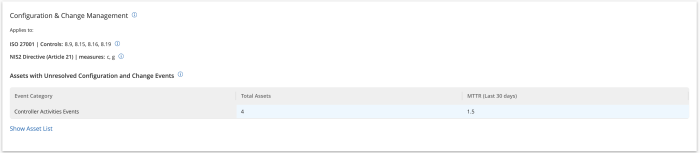
The Configuration and Change Management widget for Tenable OT, located on the compliance dashboard provides an overview of all configuration change events which occur after the baseline for Controller and Modules devices such as PLCs. When a "Baseline" version is set, any changes to the controller configuration are displayed here. When not part of regular operations, a configuration upload can be used as a reconnaissance activity to gather information about the controller’s behaviour. Critical controller status activities are reported, such as when the device is stopped. These change and configuration notifications ensure operational continuity and quick recovery during service disruptions.
For more information on creating policies, and policy configuration options, see the Tenable OT Security documentation on Policy creation located here.
The following cross-reference information is provided to derive a more comprehensive and effective approach to managing information security requirements. NIS 2 Article 21(2) (g) and Article 21(2) (h) references cyber hygiene and cryptography.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2) (g), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Protection
SECURITY SUB-DOMAIN: IT Security Maintenance
SECURITY MEASURE: IT security maintenance procedure
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (g) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for security maintenance. Cyber hygiene is best attributed to proper maintenance as they are a set of practices and tasks an organisation can execute to keep systems, data, and users safe and well-protected. The following cross-references cover the processes and procedures related to cyber hygiene.
CROSS REFERENCES:
The ISO 27001 references sections within Support, Operation, Improvement, and Annex A, Information Security Controls Reference, specifically the following sections:
-
ISO 27001 (7.5.3, 8.1, 10.1, A.11.2.4, A.12.1.2, A.12.6.1, A.14.1.1, A 14.2, A.15.2.2)
The NIST CSF references the following sections within Identify, and Protect.
-
NIST CSF (PR.MA -1, 2, PR.IP -1, 2, 3,4, 7, PR.DS -3, 4, ID.SC -4)
The ISA/IEC 62443 references the following sections within Security Function Verification, Software and Information Integrity, Audit Log, and Network and Security Configuration Settings.
-
ISA/IEC 62443 (SR 3.1, SR 3.3, SR 3.4, SR 3.8, SR 6.1, SR 7.6)
Additionally, the following cross-references are also related to Security Risk Analysis and should be considered as a reference within NIS 2 Article 21(2) (h) for cryptography.
SECURITY DOMAIN: Protection.
SECURITY SUB-DOMAIN: IT Security Architecture.
SECURITY MEASURE: Cryptography.
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (h) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for vulnerability handling and disclosure. The following cross-references cover the processes and procedures related to cryptography.
CROSS REFERENCES:
The ISO 27001 references sections within Annex A, Information Security Controls Reference, specifically the following sections:
-
ISO 27001 (A.10.1, A.18.1.5)
The NIST CSF references the following sections within Identify, and Protect.
-
NIST CSF (ID.GV -3, PR.DS -1, 2, 5, 6, 8, PR.PT -4)
The ISA/IEC 62443 references the following sections within Zone Boundary Protection.
-
ISA/IEC 62443 (SR 5.2)
_thumb_700_0.png)