Control Objective 1: Build and Maintain a Secure Network and Systems
This objective includes installing and maintaining firewalls, and firewall configurations to protect cardholder data, and not using vendor supplied credentials (default credentials) for system passwords or security parameters. This control objective covers the following PCI DSS requirements:
Requirement 1: Install and maintain network security controls
Requirement 2: Apply secure configurations to all system components
The PCI Security Standards Council defines network security controls (NSCs) as firewalls and other network security technologies, which typically control network traffic between two or more logical or physical network segments (or subnets) based on predefined policies or rules. Traditionally, this function has been provided by firewalls, but may be provided by virtual devices, cloud access controls, virtualization/container systems, and other software-defined networking technologies.
PCI Requirements Under This Objective Supported by Tenable
Requirement 1: Install and maintain network security controls
Firewalls, routers, and cloud virtual networks are configured with access control lists to control network traffic flowing inbound and outbound from the CDE. Ensure only acceptable ports, and protocols are being used. Configuration standards may outline what is acceptable and permitted on the network.
Examine configuration settings for all NSCs and verify that only approved services, protocols, and ports are in use. Compromises often occur due to insecure services such as telnet and FTP. Unsecure or unmanaged ports, services, and protocols can not only give attackers a point of entry, but they are additionally often overlooked and unpatched. By identifying all ports, protocols, and services, entities can ensure that unnecessary ports, protocols, and services that do not have a defined business need are disabled or removed.
Any network configuration setting changes are identified. Changes should not introduce misconfigurations, insecure services, or unauthorized network connections. Changes include the addition, removal, or modification of any connection, and include changes to the component and the components security functionality.
Security controls are implemented on any computing device, including company and employee owned devices, (desktops, laptops, tablets, smart phones, and any other mobile computing device) that connects to both untrusted networks (including the internet) and the CDE. Ensure that security controls are implemented and running, (firewall software or other endpoint protection solutions). Split Tunneling is a VPN technology that supports VPN clients to send only specific traffic over the VPN, while the rest travels over the local network to the internet. This setting is often used with remote workers or associated with remote sites. Split Tunneling is very dangerous, as the malicious users are given the ability to maneuver over the VPN tunnel and grain access to protected resources. Because of the risk exposed when split tunneling, the PCI requirement suggests strictly prohibiting the use of split tunneling of all employee-owned, corporate-owned, and mobile devices.
Tenable has published several audit files that have checks for split-tunneling in Juniper and Cisco devices:
-
DISA_Juniper_SRX_Services_Gateway_VPN_v2r2_STIG.audit
-
DISA_STIG_Cisco_IOS_XE_Router_RTR_v2r9.audit
-
DISA_Juniper_EX_Series_Switches_Router_v1r3_STIG.audi
-
DISA_STIG_Cisco_IOS_XE_Switch_RTR_v2r5.audit
-
DISA_STIG_Cisco_IOS-XR_Router_RTR_v2r4.audit
Requirement 2: Apply secure configurations to all system components
Default passwords are well known allowing bad actors (both external and internal) often use default passwords and other default vendor settings to compromise systems. Changing default passwords, removing unnecessary software, accounts, and services, reduces the attack surface.
Many operating systems and applications have known weaknesses by default. System configuration standards should be analyzed, and verified as being updated as new vulnerabilities are identified and immediately after a system is connected to a production environment. Keeping up to date with current industry standards will help maintain secure configurations. Numerous security organizations such as Center for Internet Security (CIS), International Organization for Standardization (ISO), and the National Institute of Standards and Technology (NIST), have established standards, recommendations, and system hardening guidelines.
Organizations should ensure that only necessary services, protocols, daemons, and functions are enabled on systems. Unnecessary functionality may include scripts, drivers, features, subsystems, file systems, interfaces (both USB and Bluetooth), as well as unnecessary web servers. Encrypted communications should be used, and all clear text protocols should be avoided (HTTP, Telnet, etc). Certificates should be trusted, using strong encryption methods, and should not fall back to weaker insecure protocols or methods. Wireless Access Points, if used, should not have default encryption keys, SNMP defaults, or vendor defaults.
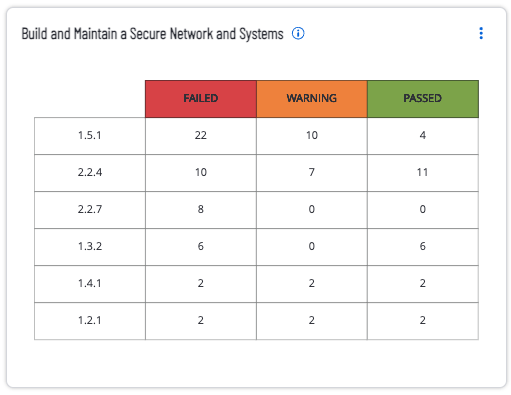
For Tenable Vulnerability Management the Build and Maintain a Secure Network and Systems widget provides details on each of the compliance controls for the compliance family group being referenced.
This widget focuses on the category Build and Maintain a Secure Network and Systems, which covers topics within PCI requirement 1 and 2. Both of these requirements cover installing and maintaining a firewall configuration to protect cardholder data, and the use of vendor supplied default credentials. This widget provides the count of audit checks according to the checks result. The compliance control reference number is followed by a count, and compliance result for the compliance control displaying a count of passed, failed, and warning.
Compliance results are a product of Tenable Compliance audit files. Audit files contain tests for file permissions, configurations and access control. Audit files compare an organization's configuration to a secure standard, such as those available by the Center for Internet Security (CIS). A wide variety of audit files can be downloaded here.
Clicking on the cell within the matrix, allows the user to drill down into the compliance data, opening the findings page and displaying the results (1). In this instance drilling down into the failed items under Requirement 1.5.1, the analysis is presented with the 22 failed compliance concerns. Selecting the first item opens a details pane (2), for that particular finding. The detail pane includes an overview as well as the actual audit output.
The specific PCI-DSSv4 requirements referenced in this widget are: 1.4.3 | 2.2.2 | 1.5.1 | 1.2.1 | 1.3.1 | 2.2.3 | 1.4.2 | 1.4.5 | 2.2.4 | 1.4.1 | 1.3.2 | 1.1.2 | 2.2.7.
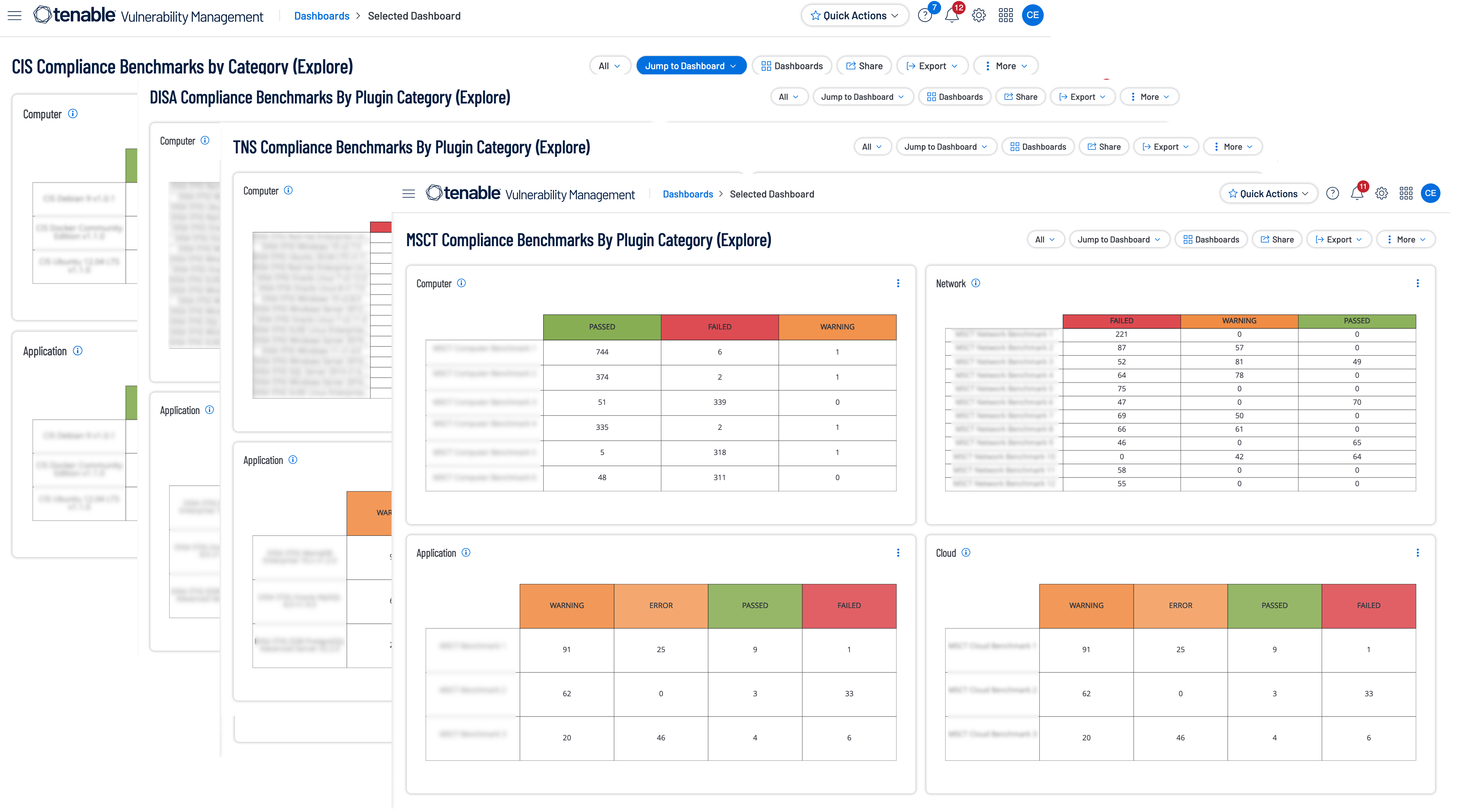
Dashboards such as the Compliance Benchmarks by Category dashboards, available for:
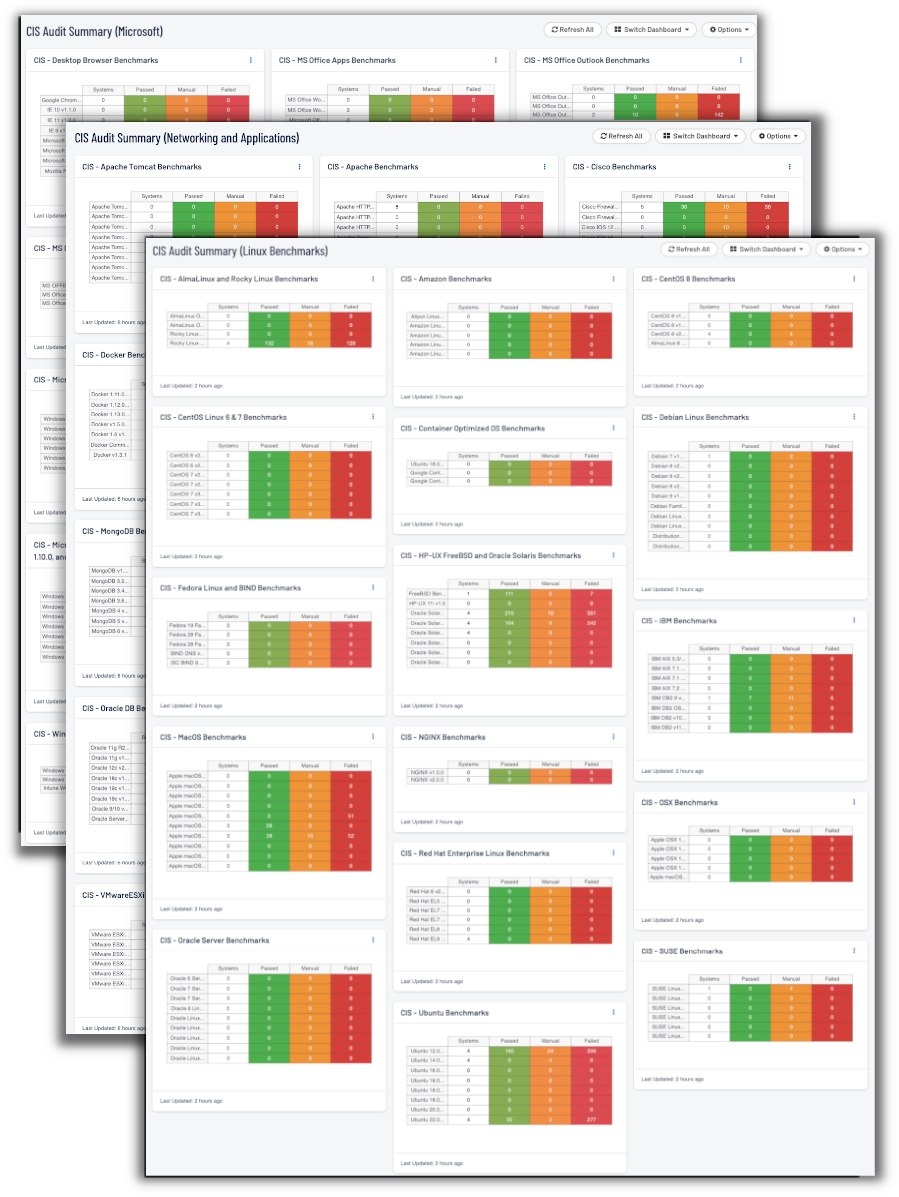
These dashboards for Tenable Vulnerability Management focus on best practice checks for the following four categories, Computer, Network, Application, and Cloud. This information allows organizations to review information related to secure systems configuration and systems hardening related to a specific set of compliance standards. Similarly, the CIS Audit Summary Dashboard for Tenable Security Center provides compliance results for numerous devices.
Cloud Environments
Cloud services are an integral part of business operations, offering scalability, flexibility, and accessibility. Cloud environments store vast amounts of sensitive data, including personal information, financial records, intellectual property, and proprietary business data. Ensuring robust security measures protects this information from unauthorized access, breaches, or theft.
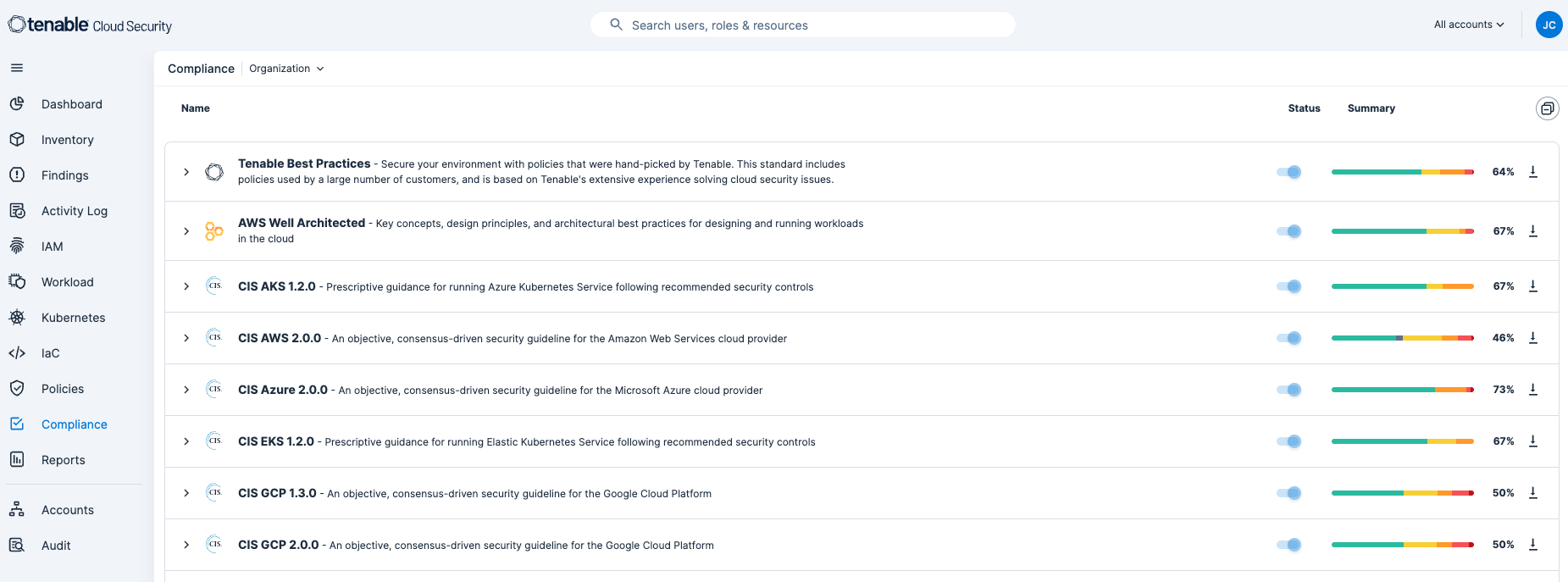
Protecting cloud environments is vital for protecting data, ensuring compliance with regulatory requirements, maintaining operational continuity, managing risks, and optimizing business efficiency. Tenable Cloud Security provides out-of-the-box, continuously updated support for all major compliance frameworks, and best practices. Tenable Cloud Security provides the ability to create customized frameworks to meet the exact needs of your organization. Using customized reports, communicate with stakeholders on internal compliance, external audit and daily security activities.
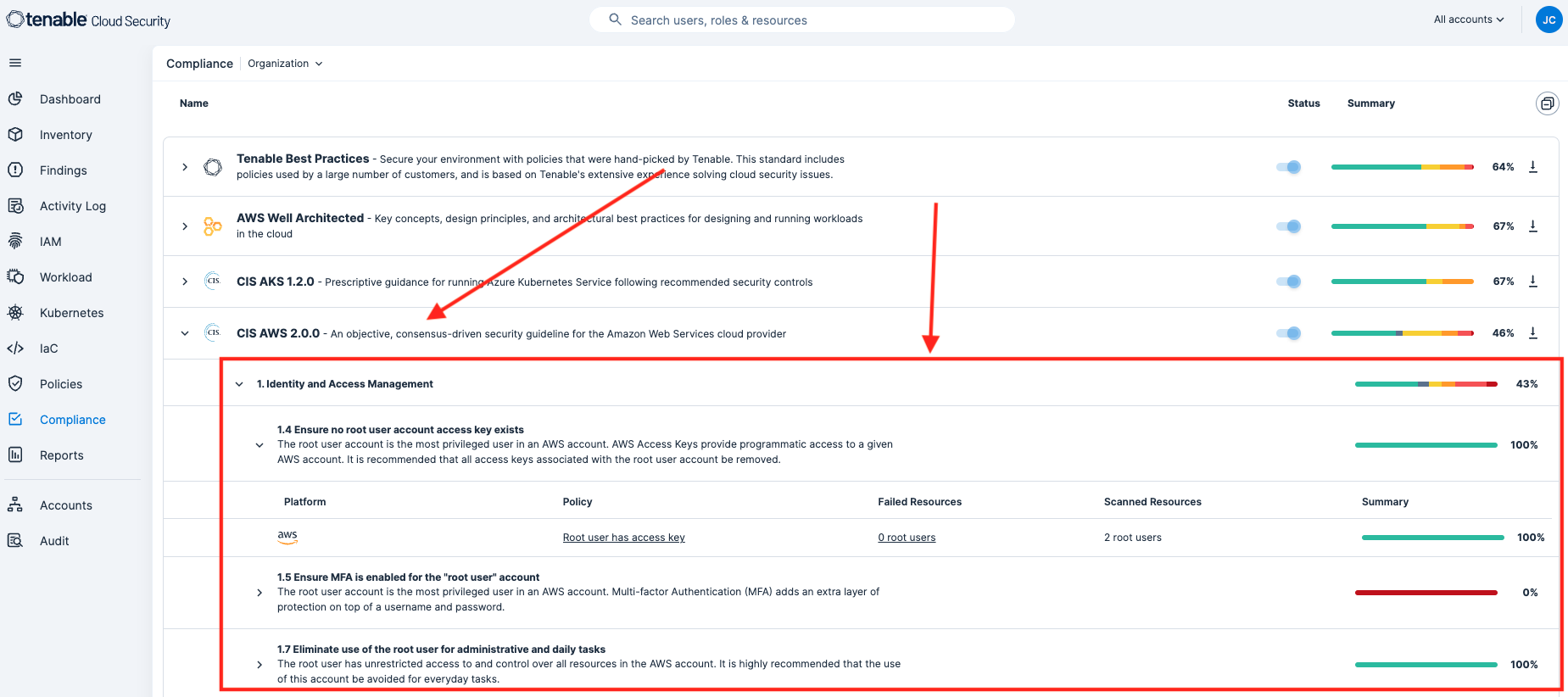
Compliance reporting is available by navigating to the Compliance tab. On the Compliance dashboard, analysts have the option to select the appropriate compliance benchmark from the list. By default, this dashboard reports compliance details for all Benchmarks combined if no option is selected.
To view details, analysts can drill down into any of the findings. In this example, drilling down into the CIS AWS 2.0.0 item provides details on the root account.