Control Objective 3: Maintain a Vulnerability Management Program
This objective focuses on proactively updating antivirus software, maintaining secure systems and applications, and implementing strong access control methods. All systems that are susceptible to malware are protected with antivirus software. All antivirus software should be kept up to date. Malware detection scans are run periodically, and all infected systems should be remediated. Patches and updates should be installed within one month of release for critical systems. Maintaining a strong vulnerability management program ensures that security concerns are addressed before they can be exploited, safeguarding cardholder data and meeting PCI DSS compliance standards.
This control objectives covers the following PCI DSS requirements:
Requirement 5: Protect all systems and networks from malicious software.
Requirement 6: Develop and maintain secure systems and software.
PCI Requirements Under This Objective Supported by Tenable
PCI Requirement 5: Protect All Systems and Networks from Malicious Software
Malicious software, often referred to as malware is any software that is designed to harm, exploit, or otherwise compromise the confidentiality, integrity, or availability of a computer system, network, or device. Included are a variety of tactics such as viruses, ransomware, spyware, and adware. Malware can enter the environment through many business approved activities, such as email, or the approved use of storage devices. Using antivirus or anti-malware software, combined with a robust vulnerability scanning program helps address these concerns. Performing periodic scanning or continuous monitoring of the environment will help ensure that previously undetected malware is identified. Scans should include all systems in the CDE.
When protecting systems and networks is paramount, Tenable has a comprehensive security solution that provides continuous visibility, critical context and actionable intelligence. These products provide purpose built PCI compliance dashboards, Assurance Report Cards (ARCs) to assist organizations in monitoring ongoing compliance with PCI DSS.
Web Application Scanning
Tenable Web App Scanning provides comprehensive vulnerability scanning for modern web applications. Accurate vulnerability coverage minimizes false positives and false negatives to ensure that security teams understand the true security risks in their web applications. Tenable Web App Scanning provides safe external scanning so that production web applications do not experience disruptions or delays. Information presented allows organizations to categorize findings and remediate vulnerabilities quickly.
Tenable Security Center
There are a series of PCI dashboards for Tenable Security Center that assist in supporting an organization's PCI compliance journey. These dashboards focus on PCI control objectives. The information contained within the dashboards provide insight to help organizations secure their systems against vulnerabilities that could lead to data breaches.
Within the Access Control dashboard, user account focused widgets are provided to help analysts see activities detected in the organization around user accounts. All user accounts such as regular user accounts and administrative accounts should be monitored for unusual activity. Multiple industry recommendations from standards such as PCI and NIST CyberSecurity Framework (CSF) are provided to help analysts see potential malicious indicators around user accounts. Examples of these indicators, such as privilege changes and group membership changes, alert analysts as changes may not be expected and should be validated. Analysts can use these widgets to help determine what typical activity should be on a network and then be more aware of when abnormal activity takes place within the organization.
The PCI Scan Monitoring dashboard provides security teams with detailed insight into their organization and vulnerability management posture. Vulnerabilities are filtered by severity and exploitability to identify at-risk hosts. Detailed information about remediation opportunities and risk issues are presented. Indicator matrices alert to the detection of specific exploitable vulnerabilities and patch management details. Nessus scans are monitored for progress and errors, and vulnerability trend data is presented. By effectively monitoring the network for vulnerabilities and remediation options, security teams can better ensure network integrity and security.
The PCI Configuration Audit dashboard presents extensive data about the configuration status of the network based on the available data. The dashboard can be used to gain insight into all configuration results, or can be modified to focus exclusively on the results related to the cardholder data environment (CDE). Organizations can configure repositories or asset lists in order to tailor the focus of the dashboard.
The PCI Quarterly Internal Vulnerability Scanning dashboard presents extensive data about the vulnerability status of the network based on the available data. The dashboard can be used to gain insight into all vulnerability results, or can be modified to focus exclusively on the results related to the cardholder data environment (CDE). Organizations can configure repositories or asset lists in order to tailor the focus of the dashboard.
A similar series of dashboards exist for Tenable Vulnerability Management.
Tenable Vulnerability Management
Tenable Vulnerability Management PCI-DSSv4.0 Audit Summary dashboard.
Antivirus
There are a number of plugins available which detect if an antivirus product is installed, running, and up-to-date. These include:
-
24232 BitDefender Check
-
20284 Kaspersky Anti-Virus Check
-
12107 McAfee Anti Virus Check
-
21608 NOD32 Antivirus System Check
-
12106 Norton Anti Virus Check
-
12215 Sophos Anti Virus Check
-
20283 Panda Antivirus Check
-
21725 Symantec Anti Virus Corporate Edition Check
-
16192 Trend Micro Anti Virus Check
-
24344 Windows Live OneCare AntiVirus Check
PCI Requirement 5.3 requires that anti-malware mechanisms and processes are active, maintained, and monitored. For anti-malware solutions to be effective, they need to be functional, and have the latest updates and signatures. The above plugins only report an issue if a problem is found with the detected antivirus solution. Nessus also has plugin #16193 which aggregates the results from these and other plugins. This is useful if you are in a multiple anti-virus solution environment and just want to find hosts that have a solution installed and operational. While the individual product detect plugins only report an issue if a problem is found with the detected antivirus solution, plugin 16193 reports if a system does have a known working anti-virus solution. Further details can be viewed by reviewing the plugin output. In this example, the plugin output for 16193 displays the antivirus application, file path, version, antivirus engine version, and antivirus signature version.
Requirement 6: Develop and Maintain Secure Systems and Software
Bad actors are always searching for vulnerabilities which can provide an easy method for gaining access to systems and networks. Keeping systems updated and patched mitigate the majority of these potential entryways. PCI DSS requires that all system components have all the appropriate software patches installed to protect against the exploitation and compromise of account data. Appropriate patches are defined by PCI DSS as those patches which have been evaluated and tested sufficiently to determine that the patches do not conflict with existing security configurations.
Prioritizing patches for critical infrastructure will ensure that high priority systems and devices are protected from vulnerabilities as quickly as possible after a vendor releases an update. Public facing websites are primary targets for attackers and should be tested for vulnerabilities on a regular basis.
Tracking updates for the constantly changing landscape of assets is important to identify legacy code and asset footprint. The Outstanding Remediations Tracking dashboard, shown below for Tenable Vulnerability Management and Tenable Security Center, focuses on legacy patches and assets to reduce management effort and reactive firefighting. Organizations can identify parts of their network that have been missed by patching cycles, or where traditional mitigation methods no longer apply.
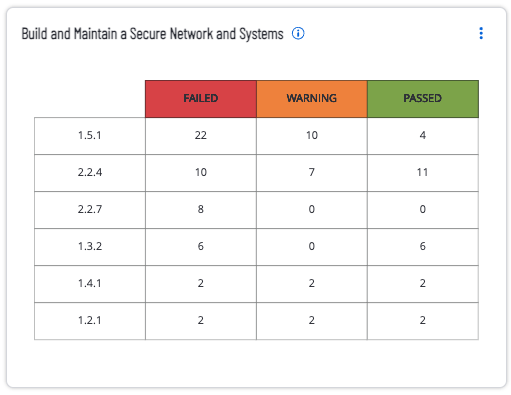
The Maintain a Vulnerability Management Program widget for Tenable Vulnerability Management focuses on the category Maintain a Vulnerability Management Program, which covers topics within PCI requirement 5 and 6. Both of these requirements cover the need for maintaining a vulnerability management program to protect systems against malware, and develop and maintain secure systems and applications. This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control. The specific controls being referenced are: 5.3.1 | 6.5.3 | 6.3 | 5.3.3 | 6.3.1 | 6.3.3 | 5.3.2 | 5.2.1
For example, reviewing the details of the cell for failed checks, in the row for PCI Requirement 6.3, clicking within the cell will drill down into the details. The next screen presented is the findings page, shown below:
Checking the filters presented allows verification of the data being presented. In this case, Compliance Framework PCI-DSSv4.0, the PCI Objective is to Maintain a Vulnerability Management Program, Results are Failed audit items, and the PCI Requirement is 6.3. Selecting an Audit Item (1.2.5 Ensure updates, patches, and additional security software are installed) presents additional details at the bottom of the page, including the results from a yum check-update command. Nessus ran the command during the audit to check for updates to any installed packages. The results were captured and logged. Those results are available in the Audit Output tab. Since there are a number of updates that are available, this check has failed. Once updates are applied, this audit item will then be displayed in the pass column.