How Tenable Helps
The Tenable solution starts with a foundation of Tenable Security Center or Tenable Vulnerability Management, for compliance and vulnerability scanning, which include internal and external scanning templates to meet the mandatory PCI scanning requirements of PCI DSS Requirement 11.3.1. Tenable provides specific PCI-DSS 11.3.1 dashboards for Tenable Security Center and Tenable Vulnerability Management, both solutions also provide the ability to gather security data from across your organization using sources such as active and passive monitoring. Next building upon the foundation by adding Tenable PCI ASV, to meet the external vulnerability scanning requirements. Tenable (an Approved Scanning Vendor) can quickly prepare a compliant scan report for merchants and service providers with PCI ASV, streamlining the quarterly external vulnerability scan submission and dispute process as required by PCI DSS. Finally, Tenable Web App Scanning, as a dedicated PCI web app scan, to be combined with Tenable PCI ASV, as needs require the identification of vulnerabilities for public facing applications.
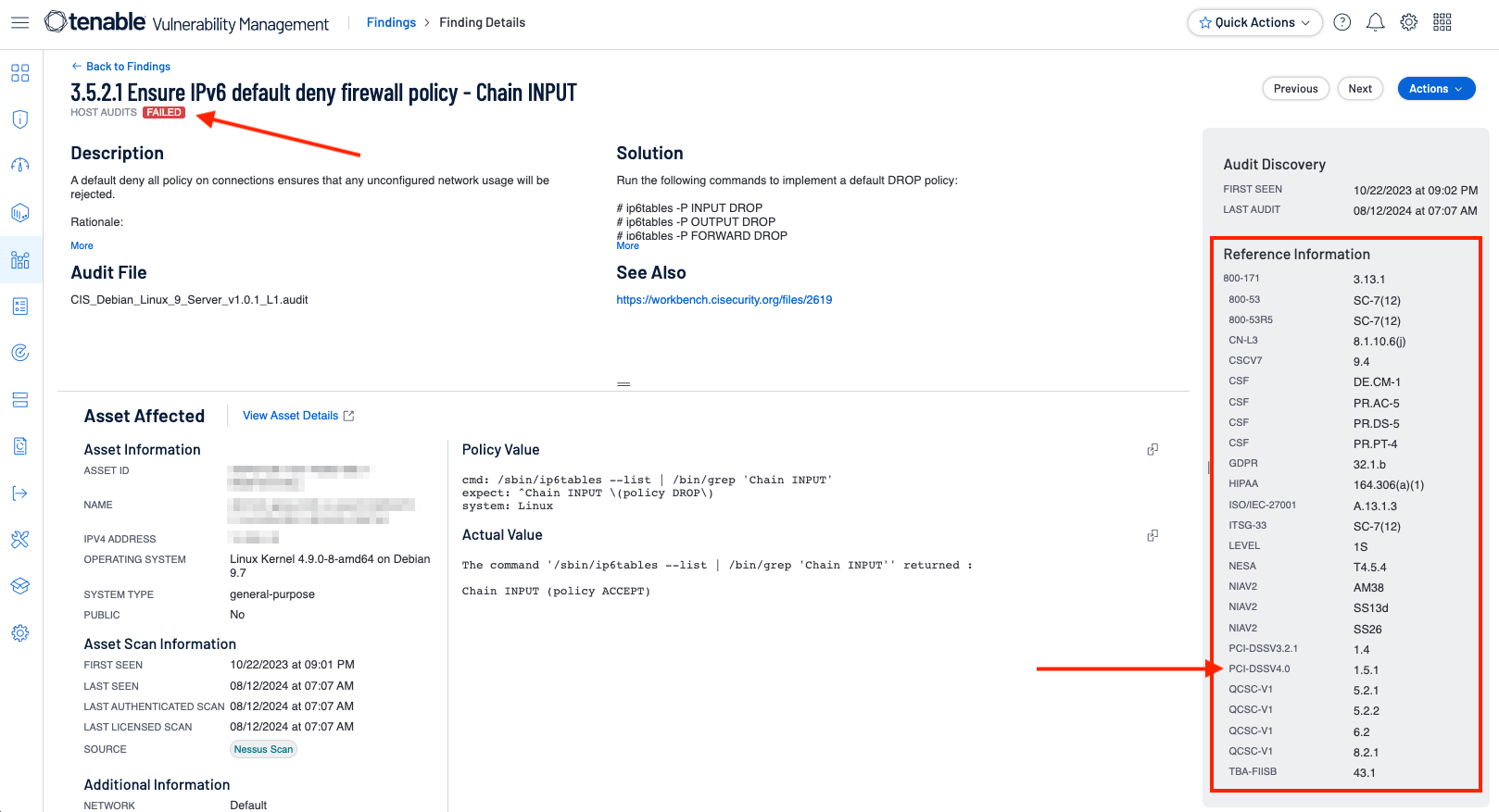
As part of the Vulnerability Management solution, Tenable provides audit files which contain cross references to a wide range of benchmarks, standards, and frameworks. In the following example, a Center for Internet Security (CIS) audit file is utilized in a scan against a Debian server running software version 9.7. Reviewing a single response for policy check CIS 3.5.2.1 - Ensure IPv6 default deny firewall policy, 25 other cross references are mapped, including PCI-DSSv4.0 Requirement 1.5.1. This CIS audit check applies to all the listed cross references, including PCI-DSS 1.5.1. The significance of this specific audit check is if IPv6 is enabled on a system, IP tables should be configured. A default deny-all policy on all connections ensures that any unconfigured network usage will be rejected. If not configured properly, and failure of the check is recorded, as shown here:
This embedded cross reference data is utilized to present and report compliance information within Tenable Vulnerability Management and Tenable Security Center using a variety of dashboards and reports highlighted in this guide.
For more information related to cross references, review the Cyber Exposure Study: Host Audit Data
Note: This document only presents solutions for portions of PCI DSS version 4 that can be measured and validated using automated processes. There are many policy specific items with the PCI DSS rules and guidelines that require organizations to manually create, develop, or review documented procedures, interview personnel, validate training, or examine procedures. These items can not be tested and therefore will not be referenced in this document.