Determining Software Authorization and Support
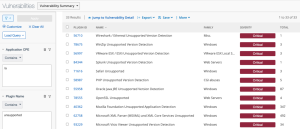
Once software is enumerated, there are additional plugins that can help determine how many instances of each version of software are running in the environment. This data helps determine software authorization and support. Tenable plugins can enumerate unsupported operating systems, databases, web servers, browsers, and other software. FINRA Rules forbid financial institutions from using any digital communication applications that cannot preserve records of business-related communications, such as WhatsApp, Signal, or Telegram. Tenable plugins can be used to detect these applications, saving the organization from large fines levied by the Securities and Exchange Commission (SEC). The following is a sample search using CPE to find a commonly used chat and collaboration application.
Packet capture software such as Wireshark and tcpdump tend to be authorized for a small group of users within the organization. Tenable’s software enumeration plugins can assist in discovering the use of this type of software and reducing the number of authorized installations.
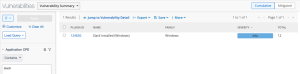
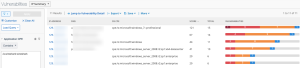
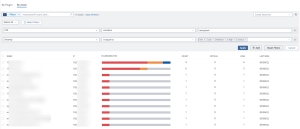
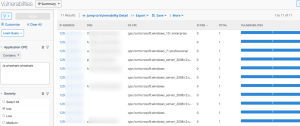
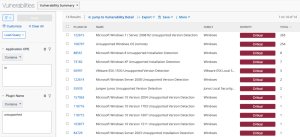
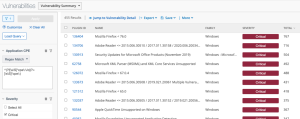
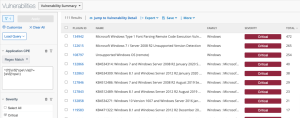
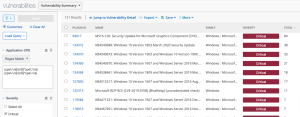
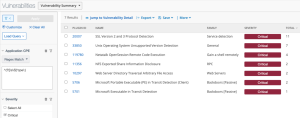
The following images display results matching the filter: CPE contains wireshark. The Wireshark CPE is /a:wireshark:wireshark, so the full CPE can be searched as well. When using only the CPE contains filter, the results include Wireshark vulnerabilities as well as an informational plugin for the detection of the Wireshark software. Typically, detection-only plugins are Info severity, so the Severity filter for Info can also be applied to display a list of assets with Wireshark installed.
Wireshark Software & Vulnerability Detection in Tenable Security Center
Wireshark Software & Vulnerability Detection in Tenable Vulnerability Management
Wireshark Software Detection in Tenable Security Center
Wireshark Software Detection in Tenable Vulnerability Management
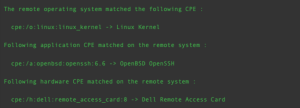
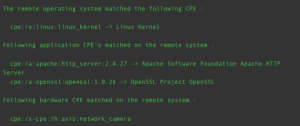
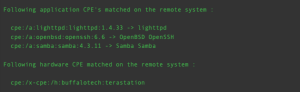
The output of the Common Platform Enumeration (CPE) (45590) plugin provides CPE syntax for operating system and application names that can be used in searches using the CPE filter in Tenable Vulnerability Management and the Application CPE filter in Tenable Security Center. The cpe:/a: syntax represents an application CPE, the cpe:/o: syntax represents an operating system CPE, p-cpe:/ is used for Linux package checks, cpe:/h: represents a type of hardware, and x-cpe:/ is used when NIST does not have a defined CPE. The following is a sample of some of the CPEs from plugin 45590:
- cpe:/a:microsoft:.net_framework:3.0 -> Microsoft .NET Framework 3.0
- cpe:/a:microsoft:.net_framework:4.8
- cpe:/a:microsoft:ie:11.0.9600.19596
- cpe:/a:microsoft:internet_information_services:7.5.7600.16385
- cpe:/a:microsoft:remote_desktop_connection:6.1.7601.24543
- cpe:/a:microsoft:system_center_endpoint_protection:4.10.0209.0
- cpe:/a:mozilla:firefox:79.0.0
- cpe:/a:oracle:jre:1.8.0_171
- cpe:/a:tenable:nnm:5.6.0
- cpe:/a:vmware:vcenter_converter:6.2.0
- cpe:/a:vmware:vmware_tools:10.2.0.1608
- cpe:/a:vmware:vsphere_client:
- cpe:/a:apache:http_server:2.4.48 -> Apache Software Foundation Apache HTTP Server
- cpe:/a:apple:safari:15.1 -> Apple Safari
- cpe:/a:openbsd:openssh:8.6 -> OpenBSD OpenSSH
- cpe:/a:redhat:ansible -> Red Hat Ansible
- cpe:/a:vmware:tools:11.2.6.28747 -> VMWare Tools
- cpe:/a:::6.2.3.15-39
- cpe:/a:apache:http_server -> Apache Software Foundation Apache HTTP Server
- cpe:/a:cisco:firepower_threat_defense:6.2.3.15.39 -> Cisco Firepower Threat Defense (FTD)
- cpe:/a:cisco:firepower_threat_defense:6.2.3.15_(build_39) -> Cisco Firepower Threat Defense (FTD)
- cpe:/a:openbsd:openssh:7.4 -> OpenBSD OpenSSH 7.4
- x-cpe:/a:microsoft:dhcp_server:6.1.7601.24498
- x-cpe:/a:tenable:log_correlation_engine_client:windows:5.0.1.0
- x-cpe:/a:slack:slack
- cpe:/o:apple:mac_os_x:12.0.1 -> Apple Mac OS X
- cpe:/o:cisco:ios_xe
- cpe:/o:linux:linux_kernel:4.4
- cpe:/o:cisco:ios:15.5 -> Cisco IOS
- cpe:/o:cisco:ios_xe:16.6.3 -> Cisco IOS XE
- cpe:/h:dell:remote_access_card:8 -> Dell Remote Access Card
Plugin Output for Plugin ID 45590 in Tenable Security Center
The Unsupported Product Summary - Applications and Unsupported Product Summary - All OSes Tenable Security Center Dashboard Components use the following filters to report unsupported operating systems and applications:
- Application CPE contains /o
- Plugin Name contains unsupported
- Application CPE contains /a
- Plugin Name contains unsupported
Apps Only: Application CPE Regex Match ^(?![\s\S]*cpe\:\/o)(?=[\s\S]*cpe\:)
OS Only: Application CPE Regex Match ^(?![\s\S]*cpe\:\/a)(?=[\s\S]*cpe\:)
OS & Apps: Application CPE Regex Match (cpe\:\/a[\s\S]*cpe\:\/o)|(cpe\:\/o[\s\S]*cpe\:\/a)
No CPE: Application CPE Regex Match ^(?![\s\S]*cpe\:)