Network Hardening and Monitoring
Questions that this section may help solve:
-
A firewall must be present between DMZ lab and internet. How can I verify this?
-
Disable unencrypted remote admin protocols used to manage network infrastructure (for example, Telnet, File Transfer Protocol [FTP]). What will I do to verify compliance?
-
Disable unnecessary services (for example, discovery protocols, source routing, Hypertext Transfer Protocol [HTTP], Simple Network Management Protocol [SNMP], Bootstrap Protocol).
-
-
I should protect routers and switches by controlling access lists for remote administration, how can I verify compliance.
Quick Overview: Establish, implement, and actively manage (track, report, correct) network devices, in order to prevent attackers from exploiting vulnerable network services and access points.
Much like enterprise assets and software, secure network infrastructure is not secure by default. The out-of-the-box configuration is tailored for ease-of-use and/or ease-of-deployment. This lack of a secure configuration can lead to a network at risk of being breached and exploited. Network infrastructure includes physical and virtualized devices like firewalls, routers, switches, and access points. Open services or older and vulnerable protocols should be vetted and determined whether they should be disabled. Much like in desktop workstations, default accounts and passwords need to also be maintained as they may usually be the first avenue of attack.
Assessing network security is an always changing environment which necessitates regular re-assessment. The regular re-assessment is important because a would-be attacker is constantly looking for gaps or inconsistencies in firewall rule sets, default configurations, routers, and switches that the attacker then uses to nullify the defenses.
Secure network infrastructure is an essential defense against attacks. This includes an appropriate security architecture, addressing vulnerabilities that are oftentimes introduced with default settings, monitoring for changes, and reassessment of current configurations. Network infrastructure includes devices such as physical and virtualized gateways, firewalls, wireless access points, routers, and switches. The attackers hope and take advantage of the fact that network device configurations weaken over time and, therefore, become exploitable. This expectation of a weakening configuration overtime makes regular auditing crucial to stay ahead of the curve and protect enterprise assets and software.
Search Examples
Attempting to confirm compliance with network hardening and monitoring can be done by searching through the audit file for certain related keywords. For example, words like “Access-list”, “packet”, or “Network” can result in audit checks that may be useful to the user. Once again, do not just use the keyword or phrase as the sole filter when querying through the data. Using just the keyword may result in false positives and unrelated results or plugins to come up. The following Keyword table shows just a few common keywords that can be used when trying to focus on Network hardening-related audit checks.
| Keyword | Common Windows Audit Name | Common Unix Audit Name | Common Networking Audit Name |
|---|---|---|---|
| Access-list | N/A | N/A | "3.2.1 Set 'ip access-list extended' to Forbid Private Source Addresses from External Networks - 'Deny internal networks'" |
| Packet | "3.1.2 Ensure packet redirect sending is disabled - sysctl ipv4 all send" |
"9.3.8 (L1) Ensure 'Windows Firewall: Public: Logging: Log dropped packets' is set to 'Yes'" |
"Ensure source routed packets are not accepted - /etc/sysctl ipv4 default accept" |
| Network | "2.3.11.2 Ensure 'Network security: Allow LocalSystem NULL session fallback' is set to 'Disabled'" |
"3.2.1 Set 'ip access-list extended' to Forbid Private Source Addresses from External Networks - 'Deny internal networks'" |
"Ensure events that modify the system's network environment are collected - auditctl /etc/sysconfig/network" |
| firewall | "Windows Defender Firewall: Protect all network connections" | "3.5.1.4 Ensure firewall rules exist for all open ports" | "Ensure default deny firewall policy - Chain OUTPUT" |
Note: When searching a keyword in Tenable Security Center (Plugin Name filter), the plugin type compliance filter should be used along with a cross reference filter to eliminate any false positives in the query.
Related Controls: 800-53r5 AU-9*, 800-171 3.3.*, CIS CSC v7 6.4, 6.5/ CIS CSC v8 8.3, 8.9, CSF PR.DS-4,PR.PT-1, ISO-27001 A.6.1.2,A.9.4.1,A.9.4.5
Tenable Vulnerability Management
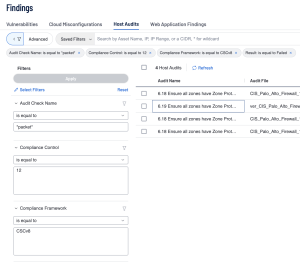
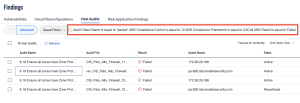
As an example, we can focus on trying to confirm compliance with firewall rules setup. In this example we’ll focus on failed audit checks so we can track what needs to be fixed. In Tenable Vulnerability Management the first filter that we’ll use is the Audit Check Name filter equal to “*packet*”. This filter returns all audit checks that include the word packet. To eliminate any false positives, we can add the two filters: the Compliance Framework filter equal to CSCv8 and the Compliance Control filter equal to “12”. Lastly, to eliminate passed checks the user can use the Result filter equal to Failed.
This query can be replicated by selecting the “Advanced” button within the Host Audits section of the findings page and inputting the following queries:
-
Audit Check Name is equal to *packet* AND Compliance Control is equal to 12 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *Network* AND Compliance Control is equal to 12 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *Access-list* AND Compliance Control is equal to 12 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
Tenable Security Center
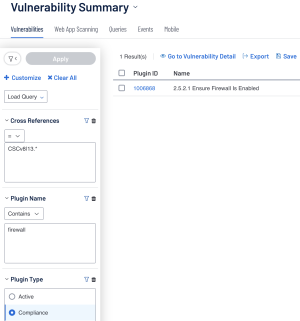
In Tenable Security Center, following a similar example as in the previous section, the user uses the Plugin Name filter contains firewall, along with Plugin Type set to compliance. While the plugin type filter eliminates some false positives, in Tenable Security Center the user can utilize the Cross Reference filter to enhance the query to include only the target compliance framework and control. In this example the Cross Reference filter can be set to equals “CSCv8|13.*”.