System Hardening
Services and Apps
Setting up secure configurations of assets and software could include removing or disabling unnecessary services, apps, and/or protocols. Common protocols that may not be used and should be disabled could be: Telnet, FTP, SMTP, etc. The actual services needed depend on the needs and uses of the user of the asset, which also need to be blueprinted. When possible, removing an unnecessary service is preferable to disabling since disabling still allows a malicious user to re-enable the service/protocol and exploit the system further.
Enterprises can also start to secure their configurations by looking at publicly developed, vetted, and supported Security Benchmarks, security guides, or checklists; some examples include the CIS Critical Security Controls, NIST’s National Checklist Program, and SANS Security Policy Templates.
Search Examples
While the detection plugins are useful, they do not provide the complete solution. Credentialed compliance scanning is the correct solution for finding possible services, or clients that shouldn’t be there. For example, CIS Control version 8 4.8 states “Uninstall or Disable unnecessary services on enterprise assets and software”, this means when using CIS audits while scanning, there are audit checks that specifically look and check if there are services, or clients that should be disabled/uninstalled based on recommended secure configurations.
Tenable Vulnerability Management
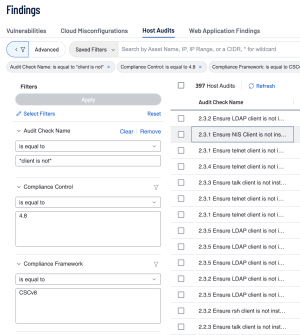
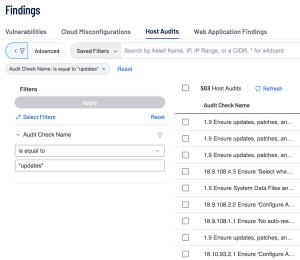
In Tenable Vulnerability Management these audit checks can be found using the Audit Check Name filter and searching for either *service is not* or *client is not*. An example of an audit check that would be returned with this query would be "2.3.1 Ensure NIS Client is not installed".
Another way to efficiently filter the audit results in Tenable Vulnerability Management is by using the Compliance Control Filter. For example, in this case we can search for Compliance Control is equal to 4.8 to display audit checks that relate to CIS 4.8. To further filter out the previous query the Compliance Framework filter can also be used.
Using a combination of the filters can allow the search to be more precise, as some compliance frameworks may have similar numbering, or newer versions of a framework may have renumbered some of the checks. In the previous examples it’s apparent that using the combinations of filters reduced the number of results that came back: 397 Host Audits from the original 533 when only using the Audit Check Name filter. This reduction of Host Audits displays the usefulness of using more than one filter to enhance the search.
The previous query can be replicated exactly by selecting the “Advanced button” within the Host Audits section of the findings page and inputting any of the following queries:
-
Audit Check Name is equal to *client is not* AND Compliance Control is equal to 4.8 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *service is not* AND Compliance Control is equal to 4 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
Tenable Security Center
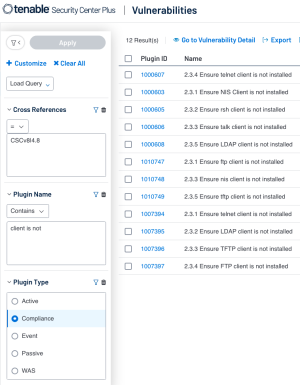
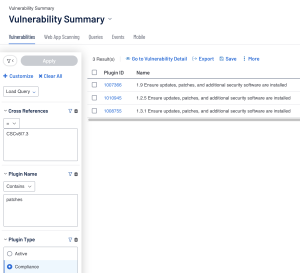
In Tenable Security Center, the Cross Reference filter takes the place of the Compliance Framework filter and Compliance Control filter which are used in Tenable Vulnerability Management. Though, much like within Tenable Vulnerability Management, using other filters to enhance the search is advisable. Instead of an Audit Check Name Filter, in Tenable Security Center a user can use the combination of Plugin Type Filter set to Compliance plugins, and Plugin Name filter to look for the audit check. Tenable Security Center allows a regex match to be used for the plugin name or just a simple *contains* search. A possible query for Plugin Name contains “client is not” along with Plugin Type set to Compliance, and this query would result in audit checks run. Pair the previous two filters with the Cross Reference Filter.
In Tenable Security Center the Cross Reference filter allows the query to filter on audit checks that relate to a specific framework and specific controls within those frameworks. For CIS Control 4 the user can utilize the Cross Reference to equal “CSCv8|4.*” (shown in the above image). The Cross Reference filter expects the desired compliance framework followed by the control and separated by a pipe (|). A valid query could also be “CSCv8|*” if a specific control isn’t needed and all audit checks related to the framework are desired.
Related Controls: 800-171 3.4.2, 800-53r5 CM-7, CSCv7 9.2/CSCv8 4.8, CSF PR.IP-1,PR.PT-3, ISO-27001 A.6.2.2,A.10.1.1,A.13.2.3
| Keyword | Common Windows Audit Name | Common Unix Audit Name |
|---|---|---|
| remote | "5.24 Ensure 'Remote Procedure Call (RPC) Locator (RpcLocator)' is set to 'Disabled'" | "3.5.6 Remote daemon lockdown - rlogind" |
| port |
"18.10.57.3.3.1 Ensure 'Do not allow COM port redirection' is set to 'Enabled'" |
"Loopback on Port 25" |
| Server |
"18.4.4 Ensure 'Configure SMB v1 server' is set to 'Disabled'" |
"2.2.4 Ensure DHCP Server is not installed - isc-dhcp-server" |
| Service | "5.11 Ensure 'Microsoft FTP Service (FTPSVC)' is set to 'Disabled' or 'Not Installed'" | "rsyncd.socket rsyncd.service active" |
| Is installed | N/A | "telnet-server is installed" |
| disabled | "18.5.19.2.1 Disable IPv6 (Ensure TCPIP6 Parameter 'DisabledComponents' is set to '0xff (255)')" | "3.3.3 Ensure IPv6 is disabled" |
Note: When searching a keyword in Tenable Security Center (Plugin Name filter), the plugin type compliance filter should be used along with a cross reference filter to eliminate any false positives in the query.
In Tenable Security Center the Cross Reference filter allows the query to filter on audit checks that relate to a specific framework and specific controls within those frameworks. For CIS Control 4 the user can utilize the Cross Reference to equal “CSCv8|4.*” (shown in the above image). The Cross Reference filter expects the desired compliance framework followed by the control and separated by a pipe (|). A valid query could also be “CSCv8|*” if a specific control isn’t needed and all audit checks related to the framework are desired.
| State | Tenable Security Center Severity | Tenable Vulnerability Management State | Descriptions |
|---|---|---|---|
| PASSED | Informational | Passed | The audit check was within the tested parameters. |
| FAILED | High |
Failed |
The audit check was not within the tested parameters. |
| ERROR | Medium |
Error |
The audit check is not supported on the asset. |
| WARNING | Medium | Warning | The audit check was successful, however compliance cannot be determined and needs to be reviewed manually. |
Updates and Patches
Ensuring enterprise assets and software are up to date by having the latest security patches is also imperative when achieving a secure configuration. Security updates and patches may appear to be tedious at times, but with the ever-evolving cyber landscape new exploits are discovered and need to be patched up. Ensuring settings like automatic updates or configuring a regular schedule for system updates can give the user confidence the system won’t be at risk from a known exploit. Along with regular updates, using regularly maintained and supported operating systems is important. When some operating systems become End-Of-Life, no more security updates are pushed out, therefore, any new exploits after the fact become harder to mitigate. Tenable can assist the user establish a baseline and track compliance by querying results from credentialed scans.
Search Examples
Verifying systems are patched can be done by searching for audit names including keywords like “patches”, “automatic updates” or a combination of “updates” and “security”. Queries using those keywords result in audit check names involving being assured the latest security patches are installed.
The following table provides common keywords that can be used to query audit results in both Tenable Security Center and Tenable Vulnerability Management.
| Keyword | Common Windows Audit Name | Common Unix Audit Name |
|---|---|---|
| Patches | N/A | "6.5 Ensure Applicable Patches Are Applied" |
| Updates + security |
"1.1 Ensure Latest SQL Server Cumulative and Security Updates are Installed" |
"1.8 Ensure updates, patches, and additional security software are installed" |
| Automatic Updates |
"18.10.92.2.1 (L1) Ensure 'Configure Automatic Updates' is set to 'Enabled'" |
N/A |
Note: When searching a keyword in Tenable Security Center (Plugin Name filter), the plugin type compliance filter should be used along with a cross reference filter to eliminate any false positives in the query.
To further focus on relevant audit results we can hone in on related controls. These related controls reside in the reference information element of each item in the audit file and can be queried in Tenable Security Center by using the cross-reference filter and in Tenable Vulnerability Management by using the Compliance Framework Filter, and Compliance Control Filter. In terms of audits relating to security updates and patches, we can search for several related controls.
Related Controls: 800-53r5 SI-2*, 800-171 3.14.1, CIS CSC v7 3.4, 3.5/ CIS CSC v8 7.3, 7.4, CSF ID.RA-1/PR.IP-12, ISO-27001 A.12.6.1
Tenable Vulnerability Management
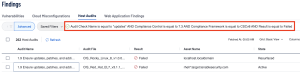
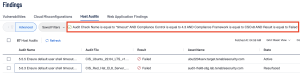
With the related controls in mind, the next step is to navigate to Tenable Vulnerability Management’s Findings page. In the Host Audits section of the Findings the user can use the Audit Check Name filter to find relevant audit results. When searching for patch-related controls, the Audit Check Name may contain keywords like patches or updates.
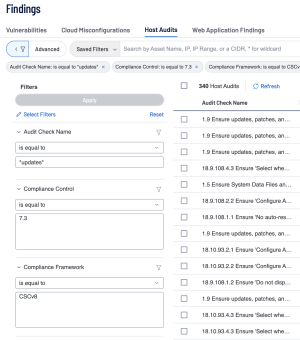
To further enhance the query, the Audit Check Name filter can be used in combination with the Compliance Framework Filter and the Compliance Control Filter. This combination ensures a more targeted search is performed.
The previous query can be replicated by selecting the “Advanced button” within the Host Audits section of the findings page and inputting the following queries:
-
Audit Check Name is equal to *updates* AND Compliance Control is equal to 7.3 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *patches* AND Compliance Control is equal to 7 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *Automatic Updates* AND Compliance Control is equal to 7 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
Tenable Security Center
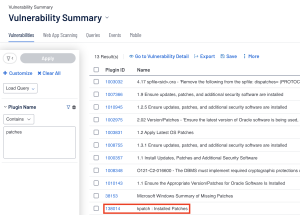
In Tenable Security Center a user will want to navigate to the Analysis page for their queries. When querying in Tenable Security Center, the audit check name becomes the plugin name. This means that just searching for keywords in a plugin name alone would result in possibly many false positives being returned.
In the previous example, searching for Plugin Name contains “patches” results in a false positive which can adversely affect compliance tracking. To reduce the number of possible false positives, the user will want to use other filters like the Plugin Type filter set to compliance, and the Cross Reference filter to grab only results related to the relevant framework and control. These filters enhance the query to enable the user to establish a focused and precise search.
Account Management
Account Management is also imperative, as enterprise assets and software are just as secure as the users that use them. The most common methods of attack tend to be targeting the users of the systems themselves, as the user’s access may lead the attacker to other assets and systems. Ensuring that users only have the appropriate level of permissions and access to certain file directories can help secure the accounts themselves. An administrator user should also have an account with appropriate and non-admin level privileges if they also use the system outside of admin duties. The presence of default accounts and passwords may be targets for attackers. This should be prevented by removing them entirely. Another configuration settings that can be set are screen lock and logout settings, as these can greatly increase the security of workstations.
Dealing with user passwords is also an important aspect in account management that will help set up a secure configuration. Password length and complexity requirements should help eliminate default passwords and ensure that user passwords are not as easily identified. Interactive logon is a necessity in many security guidelines including CIS benchmarks, as well as the implementation of time between login attempts or a set number of consecutive failed attempts before an account is locked. These password requirements make it tougher for threat actors to utilize password guessing tools which try many different combinations and/or dictionaries of passwords to gain access to the user account.
Questions that this section may help solve:
-
A screen lock or a logout should be implemented to the workstations when leaving the work area. Which audits will help identify this?
-
Screensaver should be protected by a password with a timeout period. Can tenable assist in verifying this?
-
Only authorized persons should access the systems. How can I verify this? (permissions/access level)
-
Administrator group should be verified and maintained. How can I verify this?
Search Examples
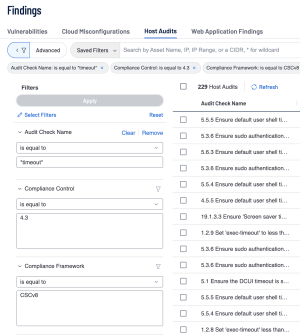
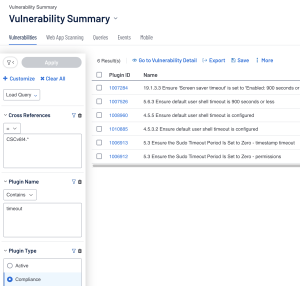
The Audit Check Name filter in Tenable Vulnerability Management and the Plugin Name filter in Tenable Security Center are useful filters that allow a user to be specific with which checks they want to look at. For example, Control 4.3 is “Configure Automatic Session Locking on Enterprise Assets.” Some example audit checks are; "5.5.5 Ensure default user shell timeout is 900 seconds or less", "1.4.1 Ensure 'Idle timeout' is less than or equal to 10 minutes for device management", and "5.4.5 Ensure default user shell timeout is 900 seconds or less - /etc/profile". These audit checks show us a common word that is used often when testing for CSCv8 4.3 compliance… “timeout”.
| Keyword | Common Windows Audit Name | Common Unix Audit Name |
|---|---|---|
| Rename | "2.3.1.4 Configure 'Accounts: Rename administrator account'" | "10.5 Rename the manager application - host-manager/manager.xml" |
| Guest Account |
"2.3.1.2 Ensure 'Accounts: Guest account status' is set to 'Disabled'" |
"2.3.1.5 Configure 'Accounts: Rename guest account' - Accounts: Rename guest account" |
| timeout |
"Ensure 'Screen saver timeout' is set to 'Enabled: 900 seconds or fewer, but not 0'" |
"5.5.5 Ensure default user shell timeout is 900 seconds or less" |
| timeout |
"Ensure 'Screen saver timeout' is set to 'Enabled: 900 seconds or fewer, but not 0'" |
"5.5.5 Ensure default user shell timeout is 900 seconds or less" |
| Interactive Log |
"2.3.7.4 Ensure 'Interactive logon: Machine inactivity limit' is set to '900 or fewer second(s), but not 0'" |
N/A |
| Lockout |
N/A |
"4.4 Ensure account lockout is set to 15 minutes" |
| Lock |
"18.9.87.1 Ensure 'Sign-in and lock last interactive user automatically after a restart' is set to 'Disabled'" |
"1.8.4 Ensure GDM screen locks when the user is idle" |
| Screen saver |
"19.1.3.2 Ensure 'Password protect the screen saver' is set to 'Enabled'" |
N/A |
Note: When searching a keyword in Tenable Security Center (Plugin Name filter), the plugin type compliance filter should be used along with a cross reference filter to eliminate any false positives in the query.
Tenable Vulnerability Management
With the keywords in mind, the user can head over to the Findings -> Host Audit page in Tenable Vulnerability Management and utilize the Audit Check Name Filter in combination with the Compliance Control Filter and Compliance Framework filters to find similar audit checks. The Query could be like: “Audit Check Name eq *timeout*Compliance Control is equal to 4.3, and Compliance Framework equals CSCv8.”
The previous query can be replicated by selecting the “Advanced button” within the Host Audits section of the findings page and inputting the following queries: “Audit Check Name is equal to *audit log* AND Compliance Control is equal to 8.3 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed.”
-
Audit Check Name is equal to *audit log* AND Compliance Control is equal to 8.3 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *Interactive Log* AND Compliance Control is equal to 8 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *Lockout* AND Compliance Control is equal to 8 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
Tenable Security Center
When targeting audit checks that will include checks run related to account management, we can use the Cross Reference filter in Tenable Security Center to target specific controls within a framework. In this case the focus would be Critical Security Controls v8 (CSCv8) Control 4. In Tenable Security Center the query could be “CSCv8|4.*” This would cover all the audit checks related to control 4. The query can be even more targeted by specifying the control further: for example, “CSCv8|4.7” would result in checks dealing with the management of default account on enterprise assets.
Resource Control
Having secure configuration can also include setting file permissions to their appropriate values based on the user. File permissions that are incorrectly setup can lead to directories being exposed to modification from certain users that shouldn’t have access. These exposed directories can lead to unintentional or intentional breaches. To remedy this issue, the security team can ensure denying read access to certain files or entire directory trees; this will ensure the confidentiality of the files. To protect the integrity of the file system, write access can also be removed for users not needing it. Lastly, removing the execution privilege or limiting privilege to administrative users can assist in preventing a possibly compromised user from taking advantage.
It is also possible to create virtual environments that will contain server processes or user actions within them, so the overall integrity of the system can be more easily maintained. One example of this in Unix is utilizing the “chroot” command which will move the current running process from the apparent root directory. With the command the process is unable to access any files outside of the environment.
Search Examples
Questions that this section may help solve:
-
Principle of least privilege… How can tenable help verify this?
| Keyword | Common Windows Audit Name | Common Unix Audit Name |
|---|---|---|
| permissions | "1.4.2 Ensure permissions on bootloader config are configured - grub.cfg" | "2.3.10.7 Ensure 'Network access: Let Everyone permissions apply to anonymous users' is set to 'Disabled'" |
| files |
"20.61 Ensure 'Software certificate installation files must be removed'" |
"1.1.1.1 Ensure mounting of cramfs filesystems is disabled - modprobe" |
| Environment |
"2.2.32 Ensure 'Modify firmware environment values' is set to 'Administrators'" |
"5.2.10 Ensure SSH PermitUserEnvironment is disabled - sshd output" |
Note: When searching a keyword in Tenable Security Center (Plugin Name filter), the plugin type compliance filter should be used along with a cross reference filter to eliminate any false positives in the query.
Tenable Vulnerability Management
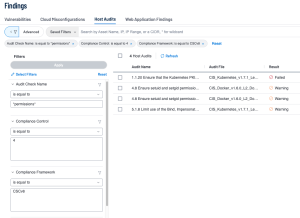
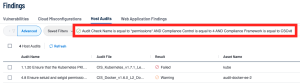
Taking into account the need for permissions to be correctly set within accounts, the user can use the keyword “permissions” to focus on permissions related audit checks. With the keyword in mind, the user can input the keyword in Tenable Vulnerability Management using the Audit Check Name filter. After using the Audit Check Name filter the user can benefit from using the Compliance Framework filter and/or the Compliance Control; both of these filters can specify which audit checks the query filters by only including the desired framework and/or control. In this case, the user sets the Compliance Framework filter equal to “CSCv8” and the Compliance Control filter equal to 4. This query ensures all Audit Checks that include the word “permissions” in the name and are part of the CIS CSCv8 Control 4 are shown.
The following Advanced Query can be replicated by selecting the “Advanced button” within the Host Audits section of the findings page and inputting the following queries: “Audit Check Name is equal to *permissions* AND Compliance Control is equal to 4 AND Compliance Framework is equal to CSCv8”.
-
Audit Check Name is equal to *permissions* AND Compliance Control is equal to 4 AND Compliance Framework is equal to CSCv8
-
Audit Check Name is equal to *files* AND Compliance Control is equal to 4 AND Compliance Framework is equal to CSCv8
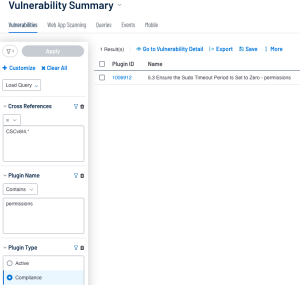
Tenable Security Center
Following the previous example, the user can query the same results in Tenable Security Center. Instead of the Audit Check Name filter, Tenable Security Center has the Plugin Name filter, and for the compliance-related filters the user can use the Cross Reference Filter. In this case the user sets the Plugin Name Filter to contain “permissions." Much like in Tenable Vulnerability Management, just using the keyword to filter out the results may lead to false positives. So, to combat the false positives with searching by plugin name, the user can use the Plugin Type filter set to Compliance, and the Cross Reference Filter set to equals “CSCv8|8.*”. This query also ensures that all Audit Checks that include the word “permissions” in the name and are part of the CIS CSCv8 Control 4 are shown.