Scanning for a Specific Vulnerability
Certain key vulnerabilities may present themselves from time to time. These vulnerabilities, typically called zero-day vulnerabilities, are a flaw or weakness in software, hardware, or firmware unknown to the vendor and does not immediately have a patch available. These vulnerabilities are called zero-day vulnerabilities because once the vulnerability is discovered or exploited, there are zero days to address the issue before potential attacks occur.
These vulnerabilities are highly valuable to attackers because they can launch targeted attacks before a patch is released. Teams must work quickly to analyze their environments and implement a mitigation strategy to minimize the impact of the vulnerability.
To assist organizations with these vulnerabilities, Tenable Research delivers world class exposure intelligence, data science insights, zero day research, and security advisories. Our Security Response Team (SRT) in Tenable Research tracks threat and vulnerability intelligence feeds to make sure our research teams can deliver sensor coverage to our products as quickly as possible. The SRT also works to dig into technical details and author white papers, blogs, and additional communications to ensure stakeholders are fully informed of the latest cyber risks and threats. The SRT provides breakdowns for the latest critical vulnerabilities on the Tenable blog.
When security events rise to the level of taking immediate action, Tenable - leveraging SRT intelligence - notifies customers proactively to provide exposure information, current threat details, and how to use Tenable products and capabilities to accelerate remediation.
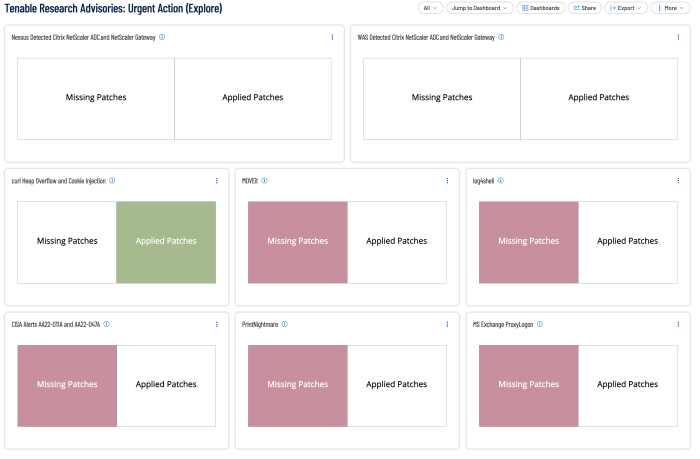
Tenable Vulnerability Management and Tenable Security Center contain a Tenable Research Advisories: Urgent Action dashboard.
This dashboard contains indicator style components to highlight any vulnerabilities related to the Tenable Research Advisories where Tenable issues customer guidance that immediate remediation was of paramount importance to all affected organizations. Tenable recommends addressing missing patches as identified in the dashboard components.
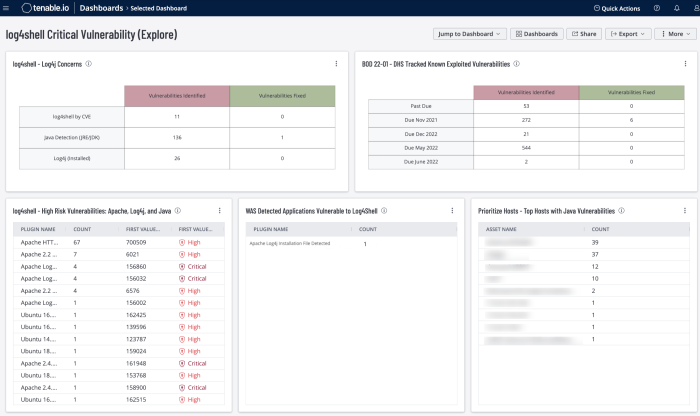
Additionally, dashboards exist which focus on specific zero-day vulnerabilities for Tenable Vulnerability Management and Tenable Security Center, such as Heartbleed, Log4shell, and more. Whereas the Tenable Research Advisory dashboard provides an indicator that identifies if the vulnerability is present or has been patched, these focused dashboards provide a higher level of information.
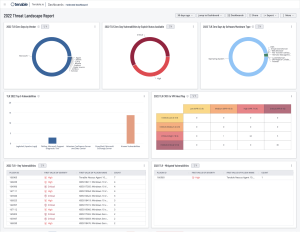
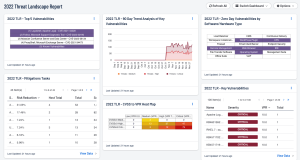
The Tenable Threat Landscape Report (TLR) inspects key aspects of the cybersecurity landscape and describes how organizations can revise their programs to focus on reducing risk. A new TLR is released at the end of each year and highlights the previous 12 months of vulnerabilities and trends.
Dashboards are available for Tenable Security Center and Tenable Vulnerability Management.
The TLR covers:
-
Significant vulnerabilities disclosed and exploited throughout the year, including how common cloud misconfigurations can affect even large tech companies.
-
The continuous transformation of the ransomware ecosystem and the rise of extortion-only threat groups.
-
Ongoing risks, vulnerabilities, and attacks within the software supply chain.
-
Tactics used by advanced persistent threat groups to target organizations with cyber espionage as well as financially motivated attacks.
-
Breach factors and the challenges in analyzing breach data, given the limited information available and lack of detailed reporting requirements.
-
Details of the key vulnerabilities affecting enterprise software.
Using Scan Templates to Scan for a Specific Vulnerability
Scan templates contain granular configuration settings. Team members can use Tenable scan templates to create custom scan configurations for your organization. Then, scans can run based on Tenable scan templates or defined custom configurations' settings. There are three scanner template categories in Tenable Nessus:
Discovery — Tenable recommends using discovery scans to see what assets are on your network and associated information such as IP address, FQDN, operating systems, and open ports if available. With this list of assets, analysts can choose what hosts to target for a specific vulnerability scan.
Vulnerabilities — Tenable recommends using vulnerability scan templates for most of the organization's standard day-to-day scanning needs. Tenable also publishes vulnerability scan templates that allow scanning of the network for a specific vulnerability or group of vulnerabilities. Tenable frequently updates the Tenable Nessus scan template library with templates that detect the latest vulnerabilities of public interest, such as Log4Shell.
Compliance — Tenable recommends using configuration scan templates to check whether host configurations are compliant with various industry standards. Compliance scans are sometimes referred to as configuration scans. For more information about the checks that compliance scans can perform, see Compliance and SCAP Settings.
When a vulnerability is released, organizations immediately begin to ask questions such as:
-
Are we vulnerable to this CVE? If so, what assets are vulnerable?
-
How do we prioritize our assets?
-
How do we validate our patching progress?
Scanning for specific vulnerabilities such as Log4J, can be accomplished using a Scan Template in Tenable Vulnerability Management, within Tenable Security Center (example in the following image) with Scan Policy Templates, or by using a Scan Template in Tenable Nessus.