Weaknesses
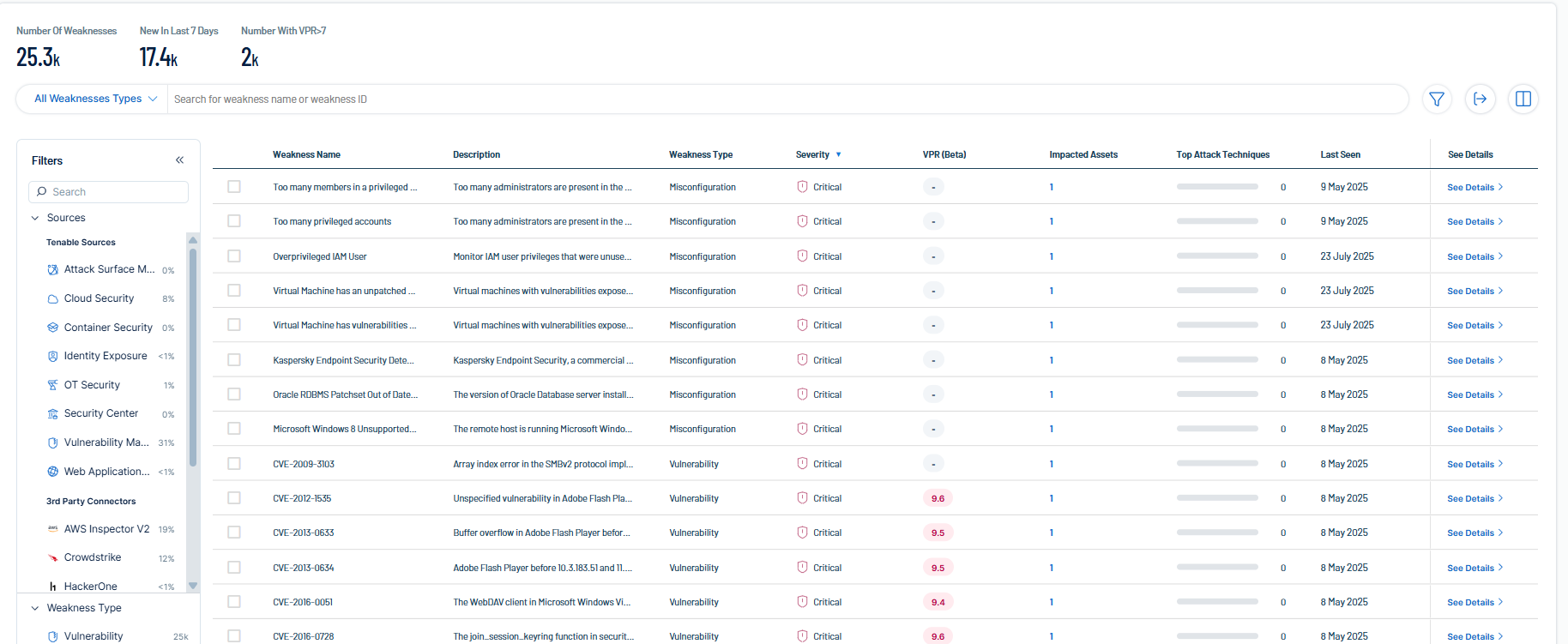
Weaknesses are vulnerabilities and misconfigurations on your assets. The Weaknesses tab on the Inventory page highlights weaknesses on your assets and provides useful insights into those weaknesses, including descriptions, assets affected, criticality, and more.
To access the Weaknesses tab:
Required User Role: Basic, Scan Operator, Standard, Scan Manager, Administrator, or Custom Role
-
Do one of the following:
-
In the left navigation menu, click Inventory > Weaknesses.
-
At the top of the Inventory page, click the Weaknesses tab.
The Weaknesses tab appears.
-
On the Weaknesses tab, you can:
-
View the total number of weaknesses on assets within your container.
-
View the total number of new weaknesses discovered within the last 7 days.
-
View the total number of new weaknesses with a Vulnerability Priority Rating (VPR) greater than 7.
-
In the weakness type drop-down, filter the list by the following weakness types:
-
All Weakness Types
-
Misconfigurations
-
Vulnerabilities
The weakness numbers at the top of the page and the weakness list update accordingly.
-
-
Use the Search box to search for a specific weakness in the list.
-
View a list of your weaknesses, including the following information:
-
Weakness Name — The Common Vulnerability Exposure (CVE) ID associated with the weakness.
-
Description — A brief description of the weakness.
-
Weakness Type — The type of weaknesses: Misconfiguration or Vulnerability.
-
Severity — The severity of the weakness, for example, Critical.
Note: At this time, Tenable Exposure Management does not include information for Info level severity weaknesses.Note: Because Tenable Exposure Management calculates CVEs using VPR and Tenable Cloud Security calculates using CVSS, you may notice a difference in severity across weaknesses between these applications. -
VPR (Beta) — The vulnerability's vulnerability priority rating using VPR (Beta) scoring.
Tip: For more information, see the Scoring Explained Quick Reference Guide. -
Impacted Assets — The number of assets impacted by the weakness. For more information, see Assets.
-
Top Attack Techniques — Instances of MITRE Att&ck techniques associated with this asset that are used in attack paths leading to critical assets. For more information, see Top Attack Techniques.
Tip: Click a choke point to navigate directly to the Attack Techniques tab on the Attack Path page, filtered automatically by techniques that feature the weakness.Note: Because Tenable Exposure Management aggregates techniques by cause (for example, CVE, CWE) a single choke point may have multiple sources/targets. This may cause discrepancies in technique counts between the Weaknesses tab and the sum of choke points within the Top Attack Techniques tab. -
Last seen — The date at which the weakness was last seen in a scan on the asset.
-
Sources — The application the weakness' asset originated from, for example, Tenable Vulnerability Management.
-
Click See details to view more details about a weakness. For more information, see Weakness Details.
-
You can also manage the page in the following ways:
Filter the Weakness List
Required User Role: Basic, Scan Operator, Standard, Scan Manager, Administrator, or Custom Role
To filter the weakness list:
-
Click the
 button.
button.The Add filter
 button appears.
button appears. -
Click Add filter
 .
.A menu appears.
-
Do one of the following:
-
To search the weakness list by tag, click Tags.
-
To search the weakness list by property, click Properties.
-
-
In the search box, type the criteria by which you want to search the list.
Tenable Exposure Management populates a list of options based on your criteria.
-
Click the tag or property by which you want to filter the weakness list.
A menu appears.
-
Select how to apply the filter. For example, if you want to search for a weakness whose name is CVE-0000-0000, then select the contains radio button and in the text box, type CVE-0000-0000.
-
Click Add filter
 .
.The filter appears above the asset list.
-
Repeat these steps for each additional filter you want to apply.
-
Click Apply filters.
Tenable Exposure Management filters the list by the designated criteria.
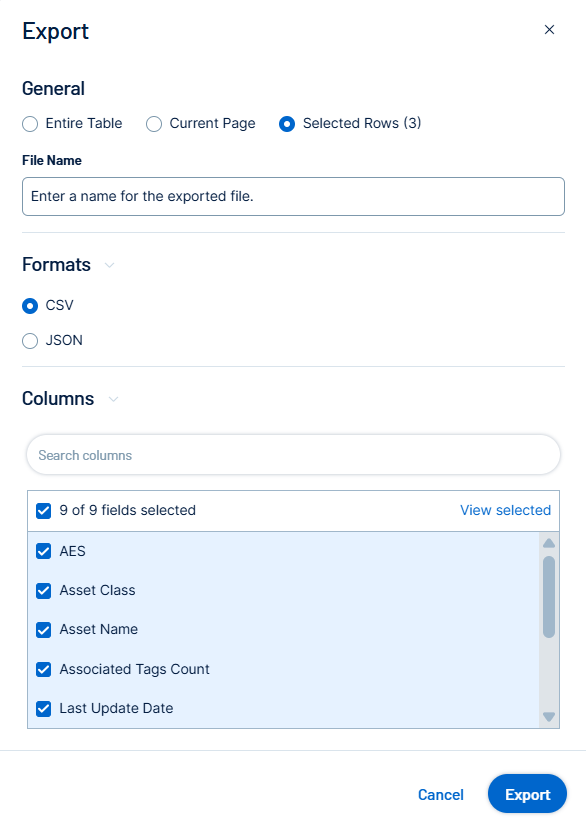
Export the Table or the Page
Required User Role: Administrator or Custom Role
To export the data on the table or the page:
-
(Optional) To export only specific table rows, in the table, select the check box next to the rows you want to export.
-
Click the
 button.
button.The Export window appears.
-
Do one of the following:
-
To export the entire table, select the Entire Table radio button.
Note: When you export the entire table, Tenable Exposure Management only includes the first 50 columns. To view asset data for a larger number of assets, use the Search Assets API call. -
To export the current page, select the Current Page radio button.
-
To export the selected rows, select the Selected Rows radio button.
-
-
In the File Name text box, type a file name to give the exported file.
-
In the Formats section, select the format in which you want to export the data.
-
In the Columns section, select the check box for each column you want to include in the export file.
-
Click Export.
Tenable Exposure Management downloads the export file to your computer. Depending on your browser settings, your browser may notify you that the download is complete.
Customize the Columns in the Table
Required User Role: Basic, Scan Operator, Standard, Scan Manager, Administrator, or Custom Role
To customize the columns in the table:
-
Click the
 button.
button.The Customize columns window appears.
-
(Optional) In the Reorder added columns section, click and drag any column name to reorder the columns.
-
(Optional) In the Show/Hide section, select/delesect the check boxes to show or hide columns in the table.
-
(Optional) In the Remove section, click the
 button to permanently remove a column from the table.
button to permanently remove a column from the table. -
(Optional) To add columns to the table, click Add Columns.
The Add columns to table window appears.
-
(Optional) Use the search bar to search for a column property.
The list of column properties updates based on your search query.
-
Select the check box next to any column or columns you want to add to the table.
-
Click Add.
The column appears in the Customize columns window.
-
-
(Optional) Click Reset to Defaults to reset all columns to their defaults.
-
Click
 Apply Columns.
Apply Columns.Tenable Exposure Management saves your changes to the columns in the table.