Identity Details
The Identities Details page focuses on an individual identity and provides a comprehensive view of an identity's digital footprint, access rights, potential vulnerabilities, and overall security posture within an organization's IT ecosystem.
To access Identity Overview:
-
In the Identity Overview page, click See Details located at the end of the row containing the person's name in the table.
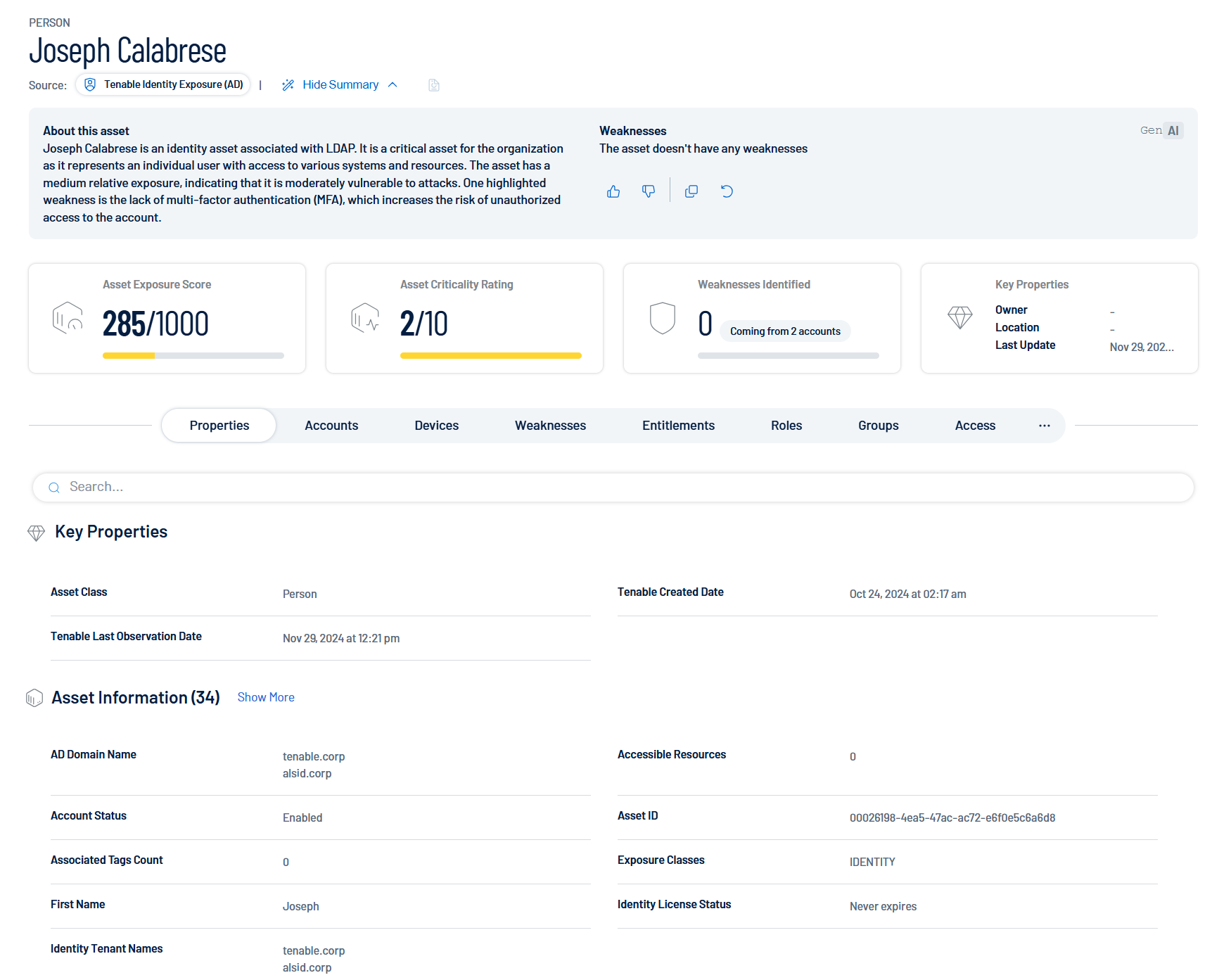
Header and Top Section
-
Identity Name: Displays the name of the identity.
-
Person Icon and Source: Shows the identity's association with specific sources. Hovering over the source icons will reveal the name of the Identity Provider.
-
Summary: A detailed summary about the identity and the weaknesses detected for this identity.
 Generate and view an AI summary of the asset:
Generate and view an AI summary of the asset:
Tenable Identity Exposure allows you to generate a summary of an identity using AI. Summaries are generated at the container level, and only apply to licensed identities within your container.
Note:Tenable Identity Exposure limits the number of summaries you can generate to 100 per hour, with a maximum of 1000 summaries per day.Do one of the following:
-
To generate an AI summary for the asset for the first time, next to No summary generated yet, click the
 button.
button.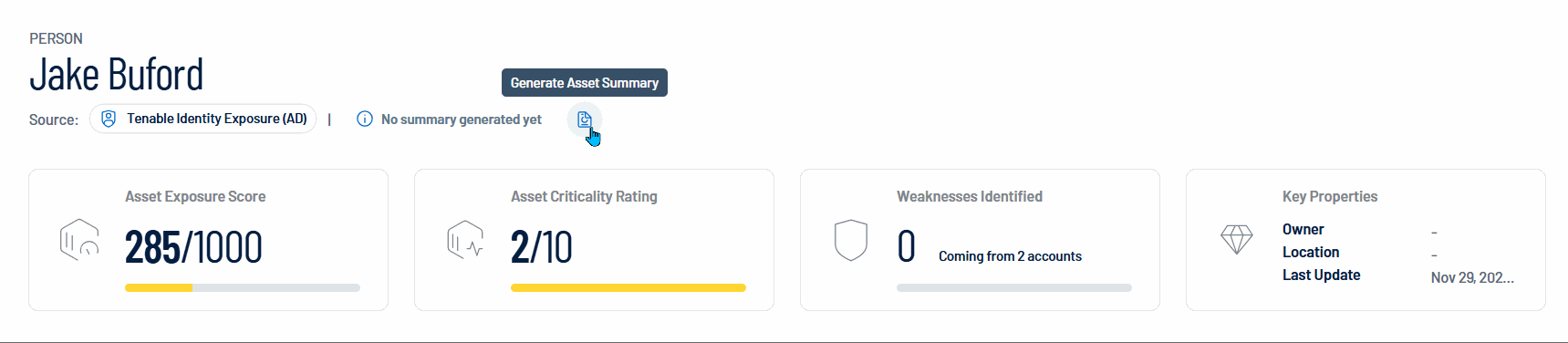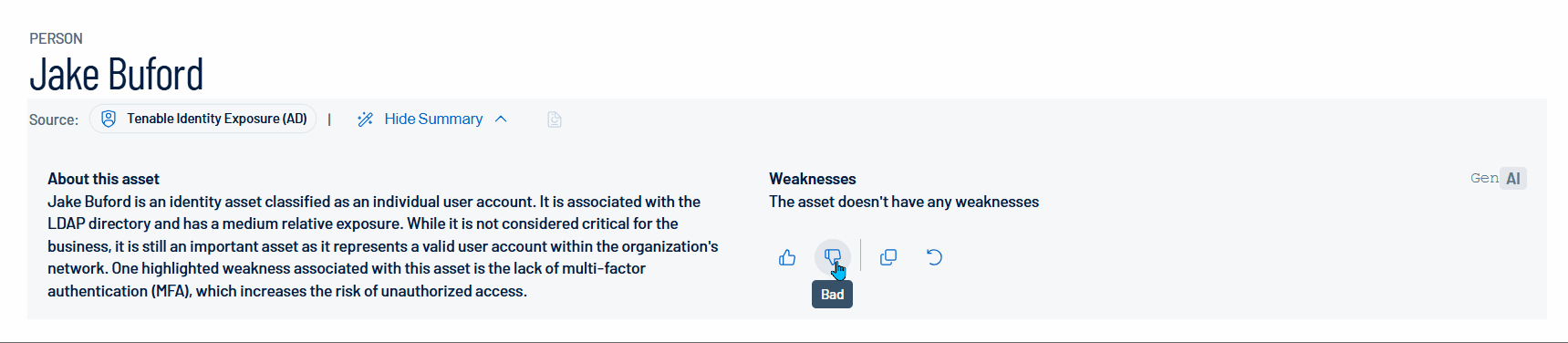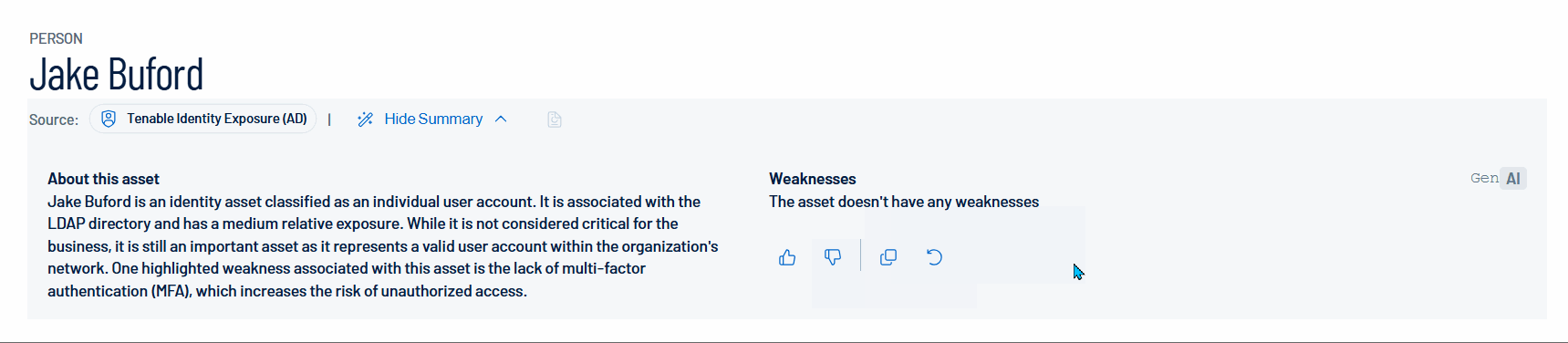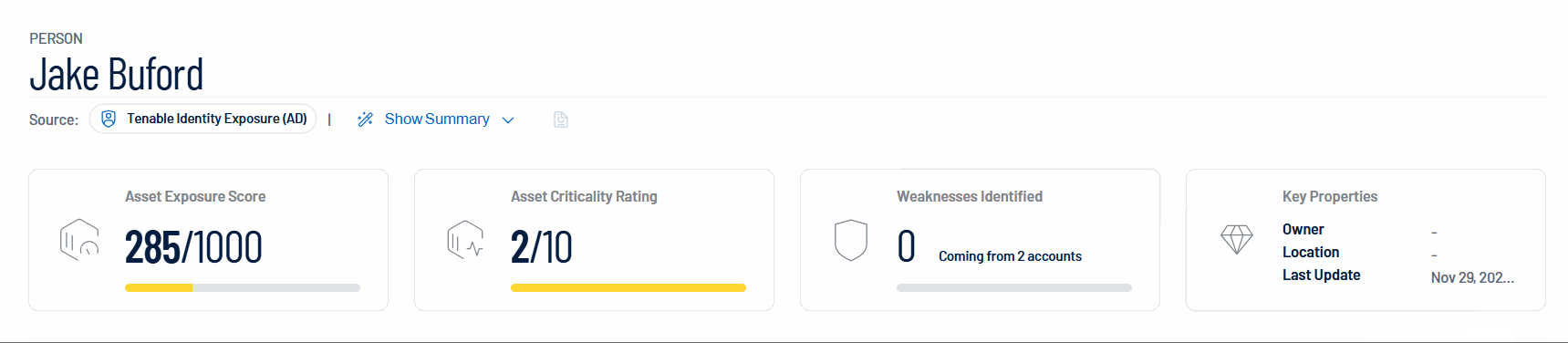
Tenable Identity Exposure uses AI to generate a summary of the asset including general details and specifics about the asset's weaknesses.
-
To regenerate an existing AI summary for the asset, click Show Summary and, at the bottom of the summary panel, click the
 button.
button.Tenable Identity Exposure regenerates the AI summary for the identity.
Tip: Click the button to copy the summary directly to your clipboard. You can also rate the helpfulness of the summary by clicking
button to copy the summary directly to your clipboard. You can also rate the helpfulness of the summary by clicking  or
or  to help improve the quality of AI-generated content within Tenable Identity Exposure in the future.
to help improve the quality of AI-generated content within Tenable Identity Exposure in the future. -
-
Asset Exposure Score: Quantifies the security exposure of the identity, with a maximum score of 1000 representing the highest level of exposure.
-
Asset Criticality Rating:Reflects the importance of the identity within the organization, rated on a scale of 1 to 10, where 10 represents the highest criticality.
-
Weaknesses Identified: Displays the number of identified security weaknesses or vulnerabilities for this specific identity.
-
Key Properties: Lists key information, including the owner, location, and the date of the last update for this identity.
Header Tabs
Below the header, specific tabs offer detailed information specific to its category. See the detailed descriptions for each tab in the section below.
-
Properties: Basic information and attributes of the identity.
-
Accounts: The identity's associated account and network profile.
-
Devices: Electronic devices associated with the identity.
-
Weaknesses: Specific security vulnerabilities or risks.
-
Entitlements: Specific permissions or access right granted to an identity within an organization's IT systems.
-
Roles: A collection of entitlements grouped together based on job functions, responsibilities, or organizational positions.
-
Groups: Organizational units or teams the identity belongs to.
-
Access: An overview of what resources or systems this identity can access.
-
Exposure Cards: Summaries of risk exposure levels.
-
Relationships: Connections to other identities or entities.
Where available, click "See details" to see more granular details in Tenable Inventory.
Properties
The default view shows the "Properties" tab.
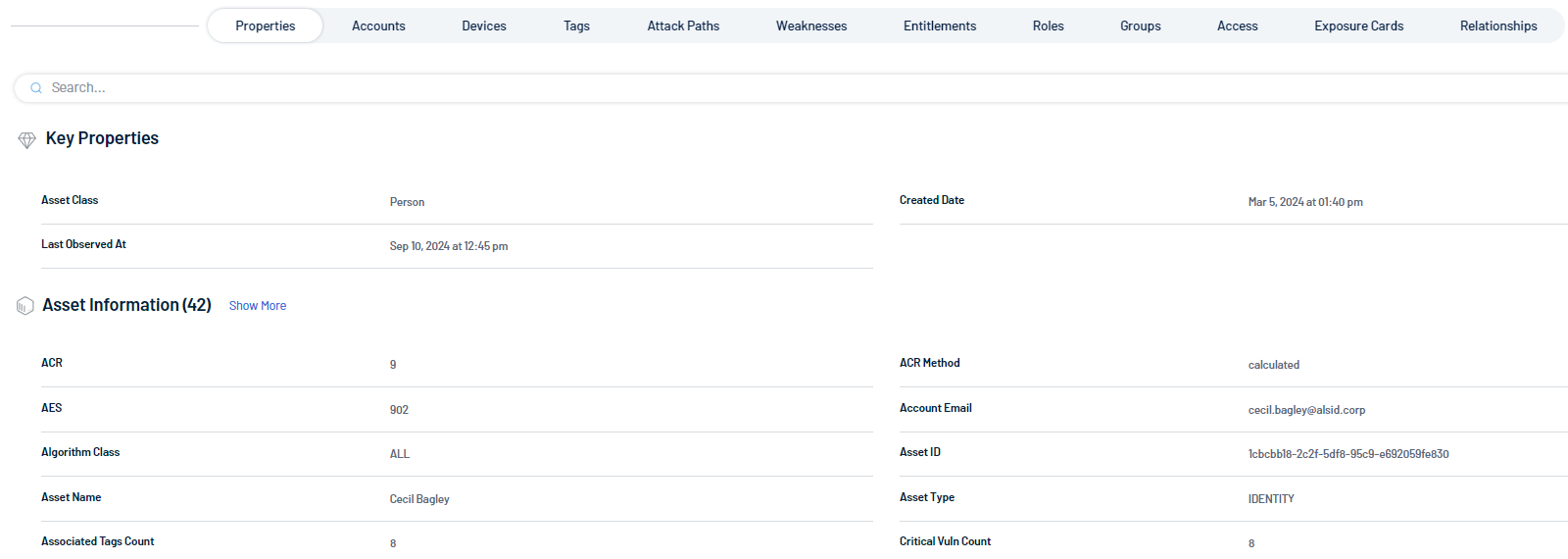
Key Properties
A summary of the most essential attributes related to the asset or identity. It typically includes high-level details such as the asset class, last observation time, and other core information that offers a quick overview of the entity’s status.
Asset Information
A detailed list of specific properties associated with the asset or identity. These may include technical identifiers like ACR, AES, asset name, email, creation date, and more. It provides a comprehensive view of the characteristics and metadata tied to the entity.
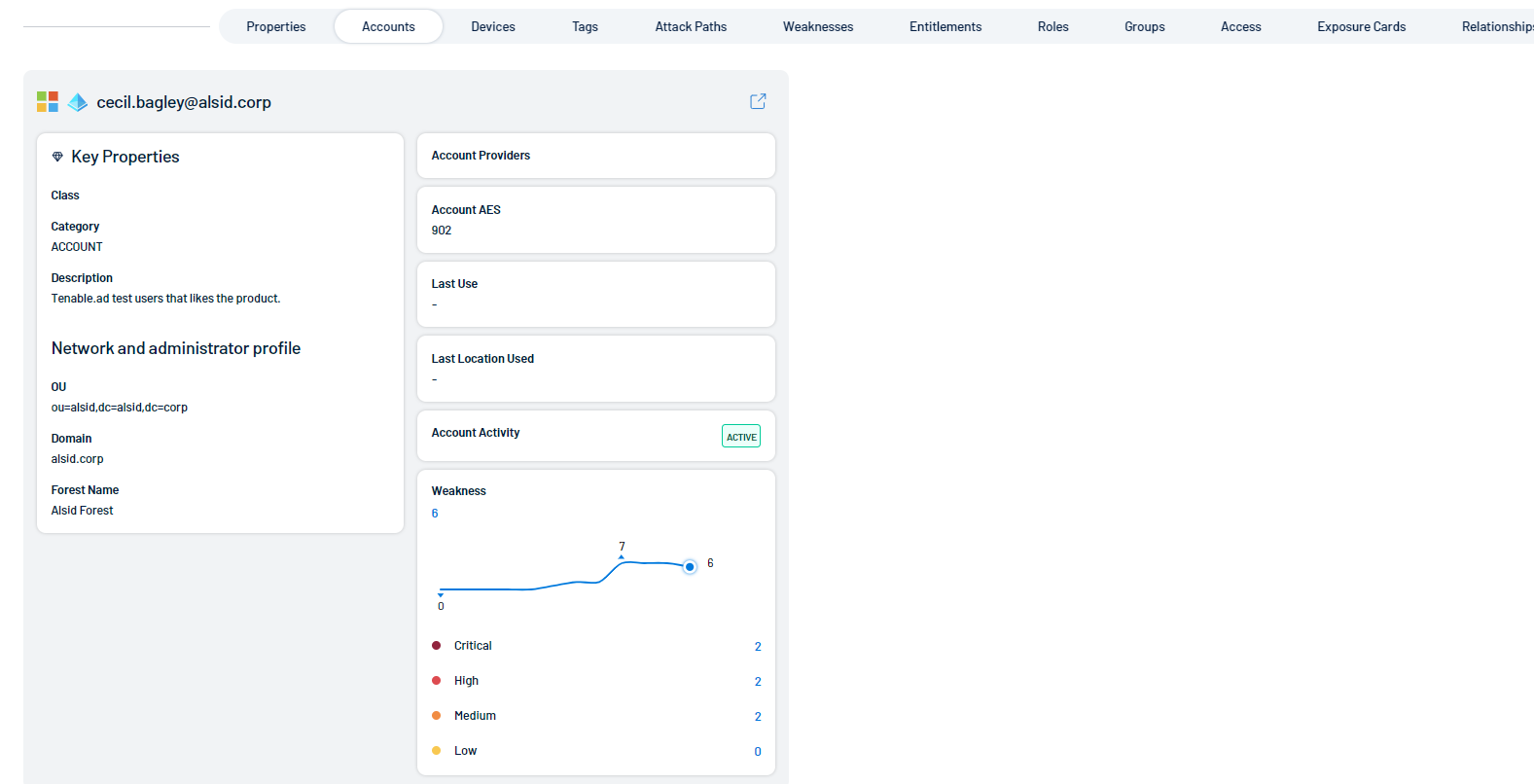
Accounts
The Accounts section provides detailed information about the identity's associated account and network profile.
Key Properties
Includes essential details such as the account Class (type of asset), Category (e.g., ACCOUNT), and a description of the account's purpose or role. The Network and administrator profile section highlights technical details, such as the Organizational Unit (OU), Domain, and Forest Name.
Weakness
Displays a graphical representation of the number of weaknesses found, categorized by severity (Critical, High, Medium, and Low). The graph provides a trendline indicating the progression of weaknesses over time.
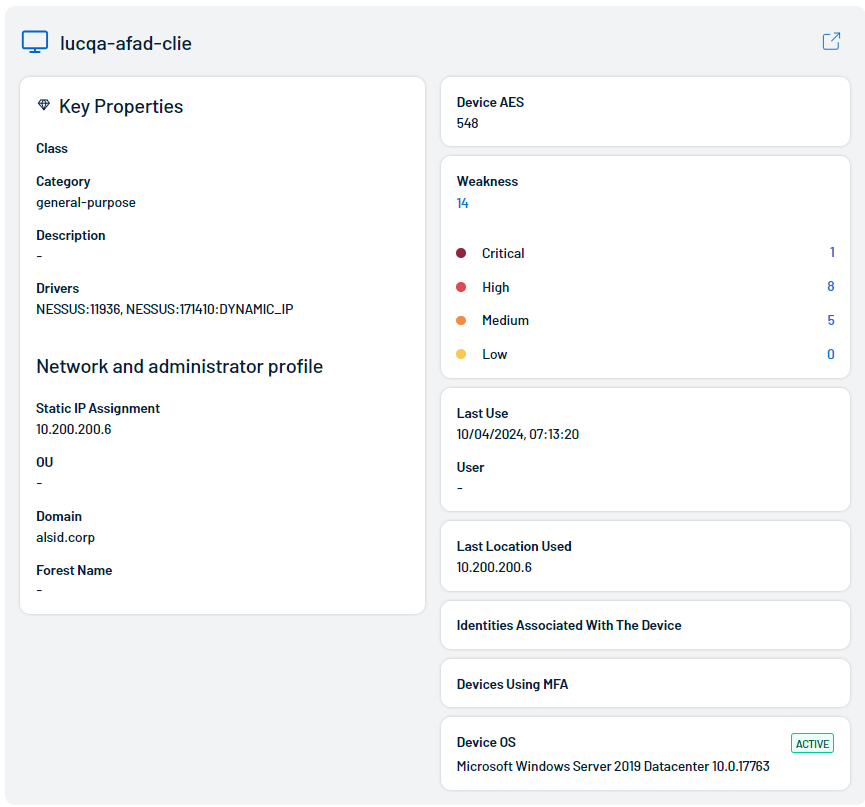
Devices
A device is typically a physical or virtual component that can connect to a network, communicate with other devices, and perform specific functions or tasks that is associated with the identity.
To start seeing this person’s devices, use Tenable Vulnerability Management to conduct a scan of the machines where they log in.
On each tile, you can view the following device information:
-
Key Properties:
-
Class — The asset class associated with the device.
-
Category — The category associated with the device, for example, general-purpose.
-
Description — Where available, a description of the device.
-
Drivers — A list of drivers installed on the device.
-
-
Network and Administrator Profile:
-
Static IP Assignment — The static IP address associated with the device.
-
OU — The Organizational Unit (OU) associated with the device.
-
Domain — The domain associated with the device. For more information, see Domains in the Tenable Identity Exposure User Guide
-
Forest Name — The forest name associated with the device. For more information, see Forests in the Tenable Identity Exposure User Guide.
-
-
Device AES — The overall AES associated with the device. For more information, see Tenable Inventory Metrics.
-
Weakness — A graphical representation of weaknesses on the device. This section includes a line graph and an individual count of each weakness and its criticality.
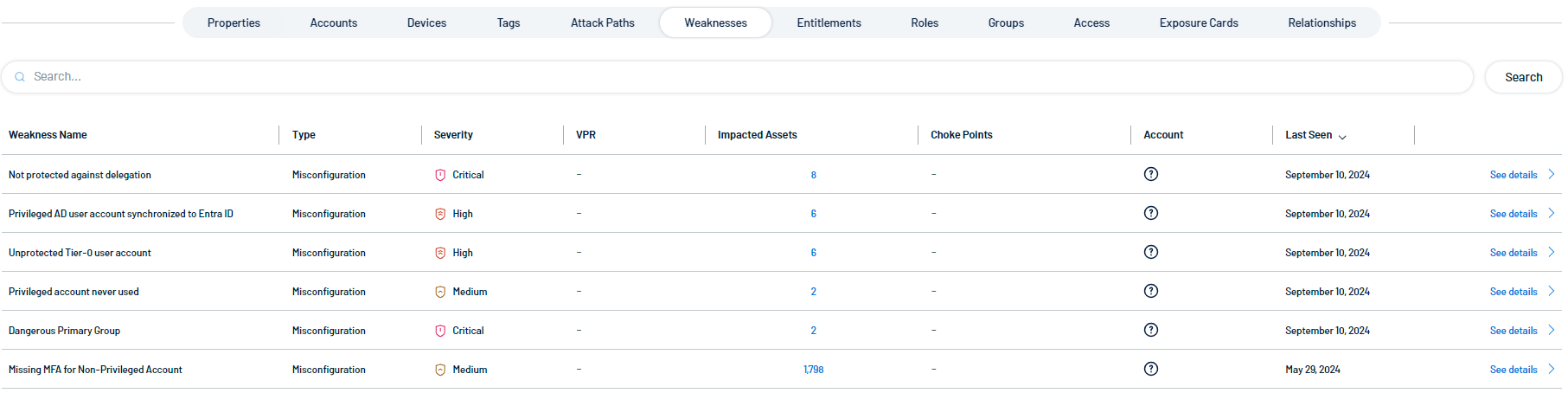
Weaknesses
-
A weakness is an instance that indicates vulnerabilities or security gaps associated with this identity or its accounts.
-
A vulnerability is technical weakness in products or information systems that can be exploited to disrupt or damage economic and social activities.
-
An Indicator of Exposure (IoE) is a detection signature that identifies potential security exposures related to identity within your environment.
-
A Risk Score is a comprehensive metric that assesses identity risks across your organization, factoring in various elements such as weaknesses, entitlements, and other security-related indicators to provide an overall assessment of potential threats.
Tip: To drill down to more granular data about weaknesses, click "See details" to go to the Inventory Weakness Details page.
Note: This page is currently only to Tenable One licensed users.
The tile includes the following information:
-
Name: The specific vulnerability or weakness identified
-
Type: the category or classification of the vulnerability, such as "misconfiguration"
-
Severity: This measures the criticality of the weakness, ranging from low to critical, determining the potential impact if exploited.
-
VPR: (Vulnerability Priority Rating): A score or rank indicating the urgency of addressing the weakness based on its exploitability and potential harm. See Vulnerability Priority Rating.
-
Impacted Assets: Lists the systems, applications, or data that could be affected if the weakness is exploited.
-
Choke Points: Potential areas in the system where you can concentrate mitigation efforts to limit the damage or spread of an attack.
-
Account: The account associated with the identified weakness or vulnerability.
-
Last seen: The date or time when the vulnerability was last detected.
Note: The Identity 360 feature currently displays weakness-related data based on the default Tenable profile and does not automatically reflect the status of deviances on AD objects you whitelisted in other profiles.Therefore:
If you have whitelisted an AD object for a specific Indicator of Exposure (e.g., "Native admin group member"), Identity 360 will still flag it as a security weakness if the default profile identified it as deviant.
This can create the impression that the issue has not been addressed, even though the object has already been whitelisted under a different profile.
If a remediation action (such as removing group membership) is taken based on the Identity 360 display, the object will disappear from the view— but this may not have been necessary if the object was already whitelisted elsewhere.
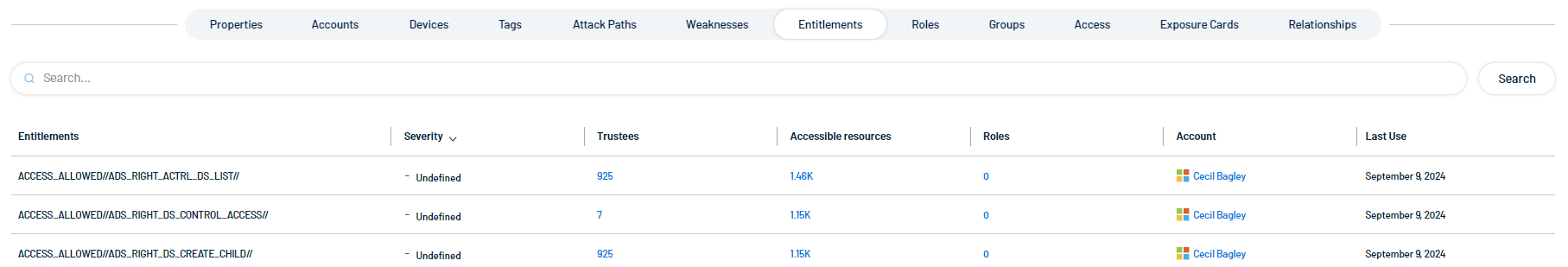
Entitlements
An entitlement is a specific permission or access right granted to an identity within an organization's IT systems. It represents the granular level of access control, defining exactly what actions an identity can perform on a particular resource.
The tile includes the following information:
-
Entitlements: Lists the specific permissions or access rights granted to accounts, such as "ACCESS_ALLOWED" with detailed permissions. These may represent permissions within a system like Active Directory.
-
Severity: Displays the criticality or risk level associated with each entitlement. In this case, it is marked as "Undefined," suggesting no specific risk categorization applies.
-
Trustees: Indicates the number of users or accounts (trustees) granted these entitlements or permissions.
-
Accessible Resources: Shows the number of resources (like files, folders, systems, etc.) that are accessible through the given entitlement.
-
Roles: Displays how many roles are tied to this specific entitlement.
-
Account: Specifies the user or account that is associated with these entitlements. For example, "Cecil Bagley" is listed as the account holder for the permissions shown.
-
Last Use: Provides the last date these entitlements were used, indicating when the account last accessed resources using the specific permissions.
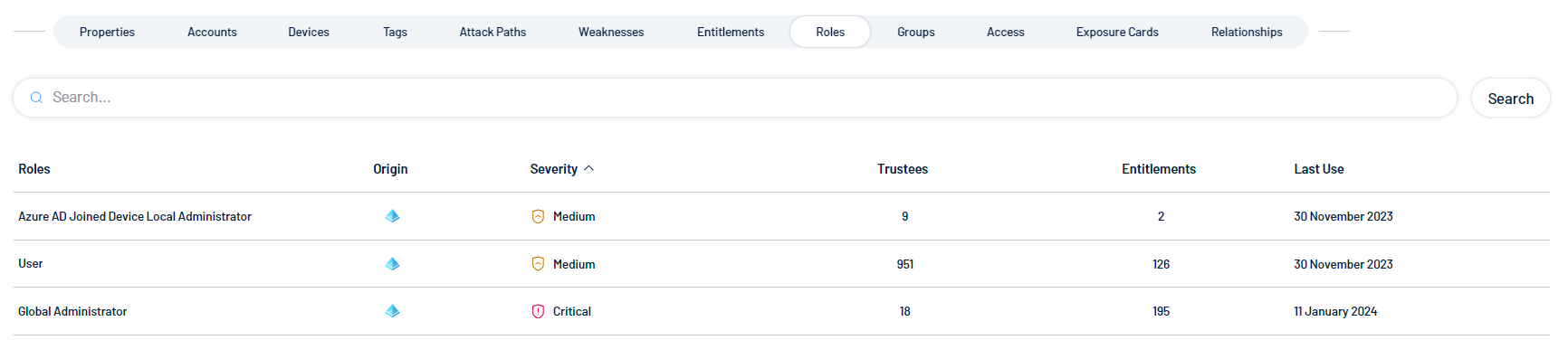
Roles
A role is a collection of entitlements grouped together based on job functions, responsibilities, or organizational positions. Roles provide a way to manage access rights more efficiently by assigning a set of predefined entitlements to multiple users who share similar job functions.
The Roles tile shows all roles assigned to the identity. For example, if this identity has roles assigned in Microsoft Entra ID, their details appear here.
The tile includes the following information:
- Roles — The name of the role assigned to the identity.
-
Origin — An icon that indicates the origin provider of the account.
-
Severity — The overall severity of the asset, for example, Critical.
-
Trustees — The number of trustees associated with the identity's role.
-
Entitlements — The number of entitlements to which the role has access.
-
Last Use — The date on which the role was most recently used on the asset.
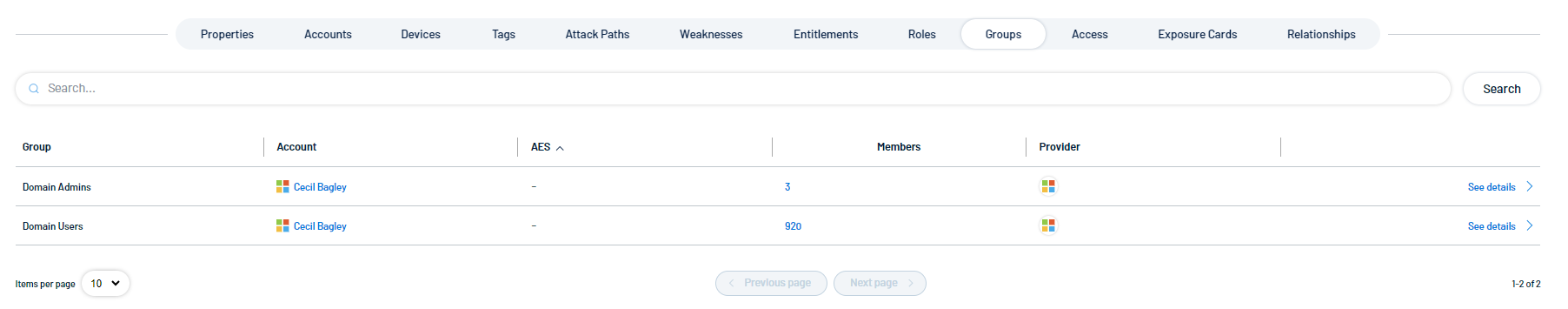
Groups
Groups are collective units or teams that this identity belongs to within the organization.
The tile includes the following information:
-
Group: The name of the group to which users or accounts belong (e.g., "Domain Admins" or "Domain Users").
-
Account: The account tied to a specific user or entity (in this case, "Cecil Bagley"). This could be the administrator or user managing the group.
-
AES: Asset Exposure Score. Tenable calculates a dynamic AES for each asset on your network to represent the asset's relative exposure as an integer between 0 and 1000. A higher AES indicates higher exposure. For more information, see Tenable Inventory Metrics.
-
Members: The number of members in each group (e.g., 3 members in "Domain Admins" and 920 members in "Domain Users").
-
Provider: The identity provider source of the account or group information.
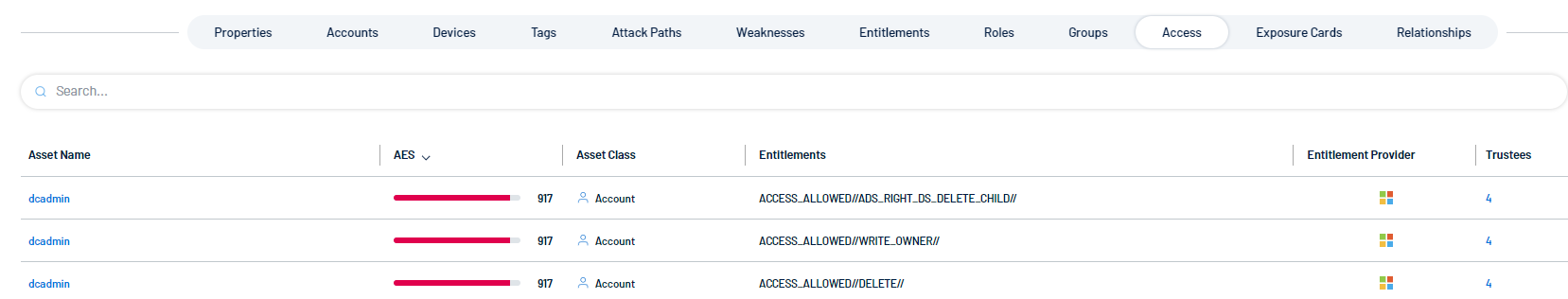
Access
This tab gives an overview of what resources or systems this identity can access.
The tile includes the following information:
-
Asset Name: Lists the names of the managed assets or accounts (e.g., "dcadmin") associated with the identity.
-
AES: Asset Exposure Score. Tenable calculates a dynamic AES for each asset on your network to represent the asset's relative exposure as an integer between 0 and 1000. A higher AES indicates higher exposure. It has a numeric value, here showing 917 with a graphical bar representing a relative measure of security or access. For more information, see Tenable Inventory Metrics.
-
Asset Class: Indicates the type of asset, which in this case is labeled as Account. The listed assets are user or system accounts.
-
Entitlements: Describes the permissions or rights granted to the asset. For example, entitlements like ACCESS_ALLOWED//ADS_RIGHT_DS_DELETE_CHILD//, WRITE_OWNER//, and DELETE// define the specific permissions associated with each asset.
-
Entitlement Provider: Specifies the source or service providing these entitlements.
-
Trustees: Displays the number of trustees associated with the asset, representing individuals or groups that have control over or are responsible for the asset (shown as 4 trustees for each row).
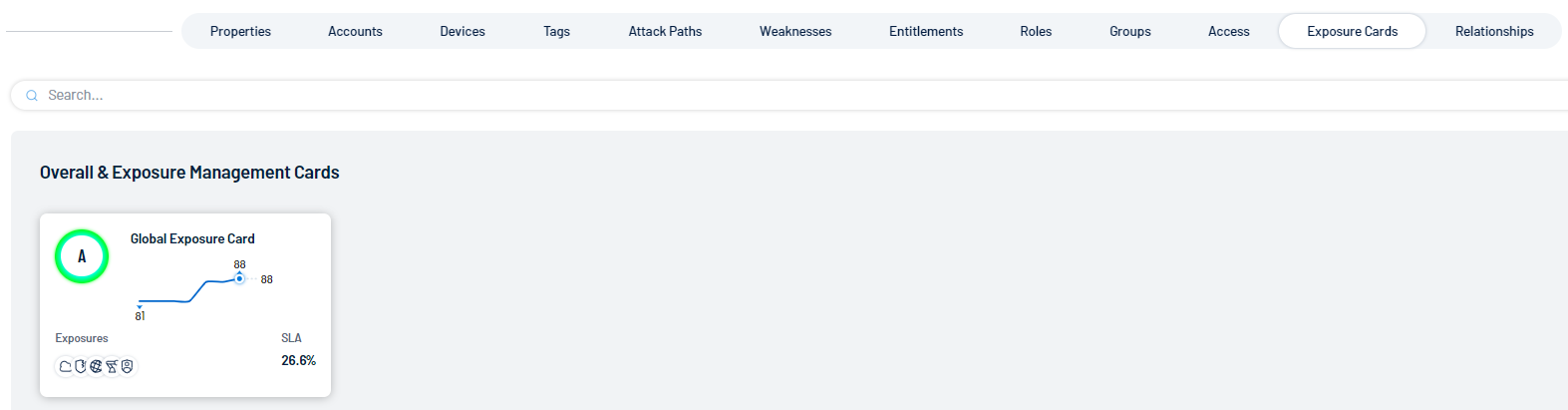
Exposure Card
An exposure card represents the incoming data from your configured tags and data sources. It aggregates and normalizes the data to provide a visualization of your Cyber Exposure Score (CES) and other metrics. Users can create custom cards, or use Tenable-provided cards to gain insight and guidance on what areas need their attention most.
-
Click on any card to navigate directly to the Exposure View in Tenable Exposure Management with the selected card data displayed by default.
Relationships
The Relationships section shows a list of all assets with a known relationship to the current identity for which you are viewing details.
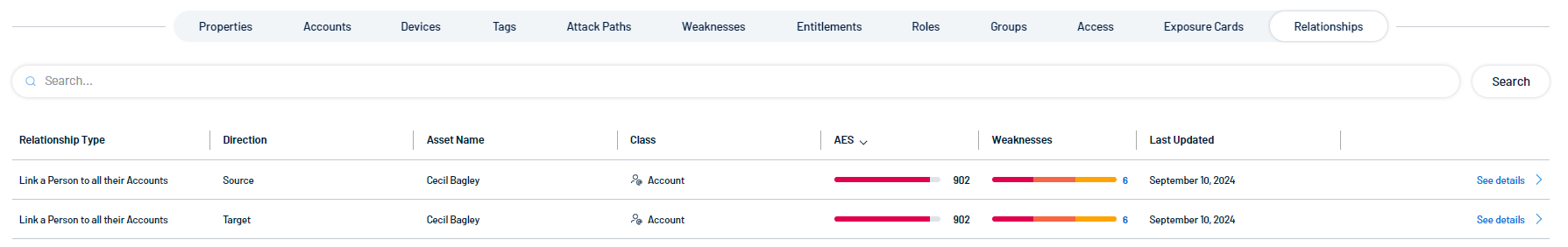
The tile includes the following information:
- Relationship Type — The type of relationship between the two identities.
-
Direction — Indicates whether the related identity is the Source or the Target of the relationship.
-
Asset Name — The asset identifier of the related identity.
-
Asset Class — Indicates the type of asset, which in this case is labeled as Account.
-
AES — Asset Exposure Score. Tenable calculates a dynamic AES for each asset on your network to represent the asset's relative exposure as an integer between 0 and 1000. For more information, see Tenable Exposure Management Metrics.
-
Weaknesses — The weaknesses associated with the asset.
-
Last Updated — The date at which a scan most recently identified the asset.