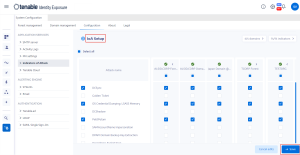
Install Indicators of Attack
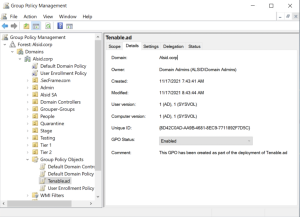
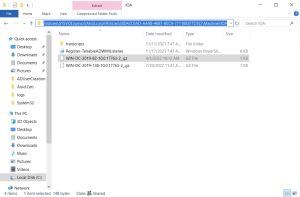
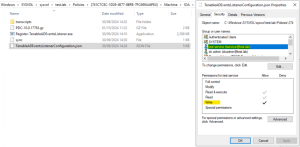
Tenable Identity Exposure's Indicators of Attack (IoA) module requires you to run a PowerShell installation script with an administrative account that can create and link a new Group Policy Object (GPO) to an organizational unit (OU). You can run this script from any machine joined to your Active Directory domain that Tenable Identity Exposure monitors and that can reach domain controllers via the network.
You only have to execute this installation script once for each AD domain, since the GPO created automatically deploys the event listener to all existing and new domain controllers (DCs).
Moreover, enabling the "Automatic Updates" option avoids having to re-execute the installation script, even if you change the IoA configuration.
For more information, see:
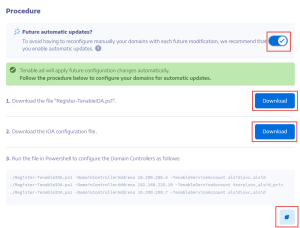
 to copy the Powershell command to configure your domains.
to copy the Powershell command to configure your domains.