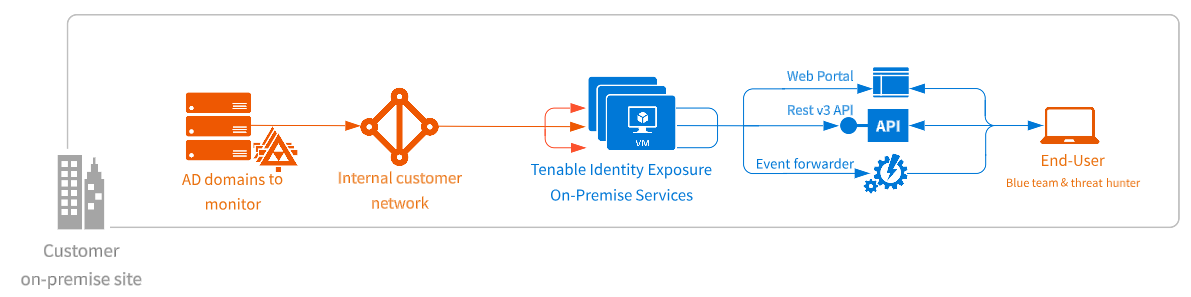
On-Premises Architectures
The Tenable Identity Exposure platform relies on several Windows services hosted on virtual machines (VMs). Your environment must support the following infrastructure:
The Tenable Identity Exposure platform consists of the following components:
-
The Storage Manager: Providing hot and cold storage support, the Storage Managers oversee serving data to the Directory Listeners and the Security Engine Nodes. This component is the only one that must remain persistent to save information. Internally, they use Microsoft MS SQL Server to store internal data and configuration.
-
The Security Engine Nodes: Hosting analysis-related services, the security engine nodes support the Tenable Identity Exposure security engine, internal communication bus, and end-user applications (such as the Web portal, the REST API, or the alert notifier). This component builds on different isolated Windows services.
-
The Directory Listener: Working closely with the monitored domain controllers, the Directory Listeners receive real-time Active Directory flows and apply several treatments to decode, isolate, and correlate security changes.
For the number and sizing of these components, see Resource Sizing.
Architectures
Tenable Identity Exposure's on-premises solution uses a software package hosted in a dedicated Windows Server environment that you provide and manage, based on the following architectures:
Centralized Architecture
The centralized architecture hosts all Tenable Identity Exposure components in the same network zone.
-
The main components (Secure Relay, Directory Listeners, Security Engine Nodes, and Storage Managers) work side by side and can communicate with each other without any network filtering.
-
To ensure proper network security, Tenable recommends that you secure this architecture with a firewall at the entrance to the zone. The following illustration shows the ingoing and outgoing network flows as described in the Network Flow Matrix.
Advantages — This architecture offers the best balance between manageability and security:
-
Each Tenable Identity Exposure service is at the same logical place behind a unique firewall.
-
Each service flow (Active Directory, end-users, alerts, etc.) goes through the same network equipment.
-
This architecture links new Active Directory domains easily because it does not need service or extra configuration on the targeted domains.
Disadvantages — The centralized architecture can consume bandwidth because it must transfer each Active Directory flow from the monitored domain controllers to the Tenable Identity Exposure network zone.
Distributed Architecture
The distributed architecture places Directory Listeners in the same network zone as the domain controllers, and hosts the Security Engine Node and the Storage Manager in another network zone, as shown in the following illustration:
Advantages
-
Bandwidth reduction: Active Directory flows can be significant when monitoring large directories. By filtering relevant security changes and compressing the objects, the Directory Listeners reduce the bandwidth that the platform uses.
-
Better network filtering:
-
An Active Directory infrastructure requires the use of numerous TCP and UDP ports which can be targets during a cyberattack. Following the principle of least privilege, Tenable recommends that you expose only these network ports when it is strictly necessary.
-
By placing Directory Listeners in the same network zone as the domain controllers, Tenable Identity Exposure does not need to expose Active Directory ports to another network zone.
-
-
Isolated infrastructure: Specific contexts sometimes require a complete isolation of the Active Directory infrastructure from the rest of the information system. Using the distributed architecture, Tenable Identity Exposure’s platform only requires one inbound and one outbound network flow, which preserves the security of the isolated infrastructure.
-
Network security: Tenable Identity Exposure’s Directory Listeners use a specific host-based firewall. Tenable also recommends that you use a specific firewall at the entrance of the zone hosting the Security Engine Nodes and Storage Managers. For more information on inbound and outbound network flows, see Network Flow Matrix.
Disadvantages — Tenable only recommends this architecture for highly sensitive environments that require high-level network isolation.
-
The distributed architecture is more complex to deploy and to maintain because it requires multiple network configurations in different network locations.
-
This architecture is also less flexible since it requires the deployment of new Directory Listeners each time the customer wants to add a new domain to monitor.