Split Security Engine Node (SEN) Services
The standard architecture for the Tenable Identity Exposure on-premises platform uses three virtual machines (VMs) by default for the Storage Manager, Security Engine Node, and Directory Listener.
However, if the environment that you monitor has more than 150K users, you can split the Security Engine Node (SEN) over five different machines to improve performance.
The installation process installs the following Tenable Identity Exposure components:
| VM # | vCPU (per instance) |
Memory (per instance) |
Disk Space (per instance) |
Recommended Service | Service Description |
|---|---|---|---|---|---|
| 1 | 8 cores — at least 2.6 GHz | 16 GB of RAM | 1 TB | RabbitMQ | A message broker between services. |
| 2 | 8 cores — at least 2.6 GHz | 16 GB of RAM | 100 GB | Attack Path | Computes attack path relations and maintaining them over time. |
| 3 | 12 cores — at least 2.6 GHz | 32 GB of RAM | 300 GB | Cephei | Computes values for different analytics used for the Tenable Identity Exposure dashboards. |
| CetiBridge | Communication plugins and service in charge of communicating with the Active Directory. | ||||
| Electra | Manages web sockets to update information without reloading the user interface. | ||||
| Enif | Authenticates web users. | ||||
| Eridanis | Connects to the SQL Server; ensures the exactness of Tenable Identity Exposure's information. | ||||
| Eltanin | Sends data to the Tenable Cloud, if enabled in Tenable Identity Exposure. | ||||
| Health Check | Alerts configuration anomalies leading to connectivity or other issues in the infrastructure. | ||||
| Kapteyn | Runs in the end user's browser to show the user interface. | ||||
| 4 | 16 cores — at least 2.6 GHz | 16 GB of RAM | 100 GB | Cancri | Decodes raw information; fetches delta between events; computes event type. |
| EventLogsDecoder | Decodes information related to IOA events. | ||||
| 5 | 16 cores — at least 2.6 GHz | 32 GB of RAM | 100 GB | Cygni | Computes deviances and attacks. |
For more information, see Resource Sizing for requirements.
SEN Installation on Several Machines
To install the Security Engine Node on several machines, you select the services to install on each specific virtual machine.
Public Key Infrastructure (PKI) Certificate
To use peer verification, your PKI certificate must include the IP addresses or DNS of all the machines used to install Tenable Identity Exposure.
Example
The following example shows an installation of RabbitMQ and Attack Path on one virtual machine.
To install the RabbitMQ and Attack Path services on a VM:
-
On the local machine, run the installation file Tenable.ad_v3.19.x.exe.
The Setup Wizard appears.
-
Select the Expert Mode check box.
-
Click Next.
The Custom Setup window appears.
-
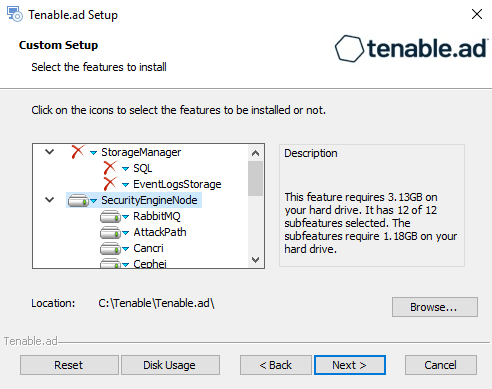
Deselect the Storage Manager and Directory Listener components.
-
Deselect all SEN services except for RabbitMQ and AttackPath.
-
(Optional) Click Browse to change the installation folder location. Change only the drive letter.
-
Click Next.
The TLS Options window appears.
-
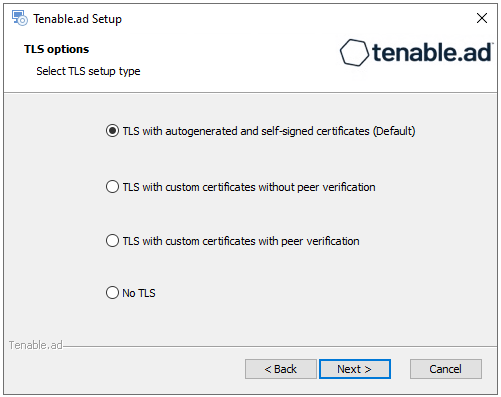
Select the TLS with autogenerated and self-signed certificates (Default) option.
-
Click Next.
The Storage Manager window appears.
-
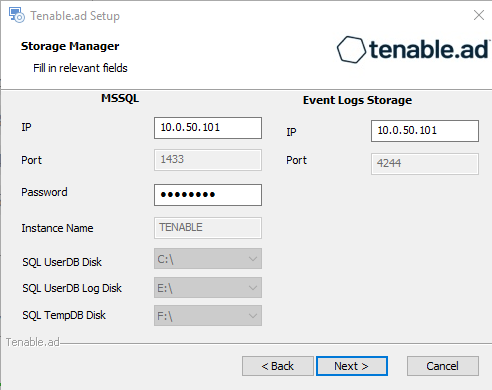
Provide the following information:
-
In the MSSQL box, type the IP address of the Storage Manager.
-
In the Password box, type the service account password for the MSSQL database defined in the Storage Manager installation.
-
-
Click Next.
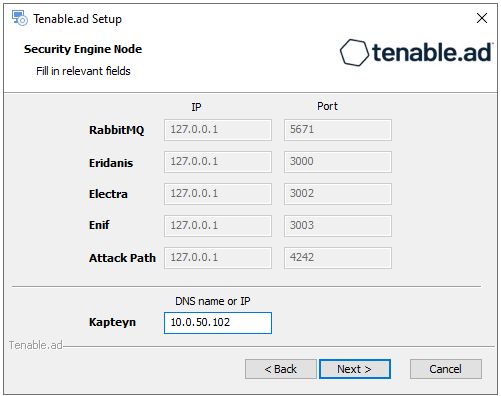
The Security Engine Node window appears.
-
In the DNS name or IP box, type the DNS name (preferred) or IP address of the web server that end users enter to access Tenable Identity Exposure.
Note: By default, the installation process creates a self-signed certificate with the DNS name or the IP address that you entered. For more information, see Change the IIS Certificate.
-
Click Next.
-
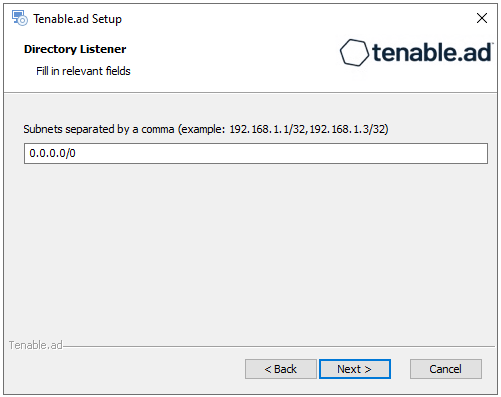
The Directory Listener window appears.
-
In the Subnets box, type the subnet address for the Directory Listener. For multiple subnets, use a comma to separate the addresses.
-
Click Next.
The Ready to Install window appears.
-
Click Install to begin the installation.
After the installation completes, the Completing the Tenable.ad Setup Wizard window appears.
-
Click Finish.
A dialog box asks you to restart your machine.
-
Click No.
Caution: Do not restart the machine until after you install the Directory Listener. -
Repeat this procedure to install the remaining SEN services.
See also
-
Resource Sizing for Security Engine Node
-
Install Tenable.ad