Create an Input
After you complete the configuration for your Tenable Add-On for Splunk, you must create the input for the deployment type you have. The following process outlines input creation if you have a deployment with Tenable Add-On for Splunk.
To create an input:
-
In the left navigation bar, click Tenable Add-On for Splunk.
-
Click the Inputs tab.
-
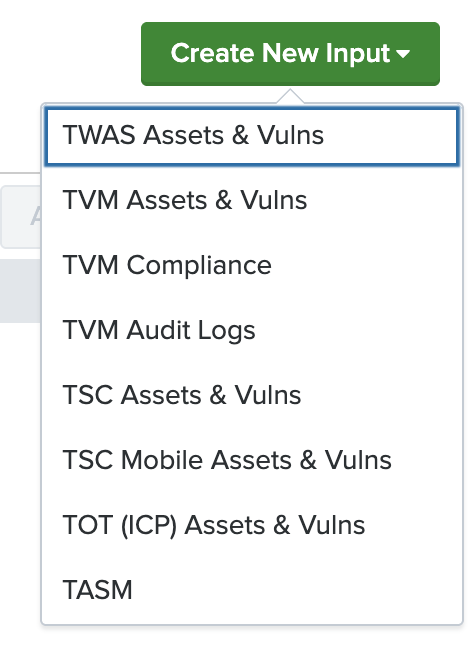
Click Create New Input.
The input drop-down list appears:
-
Select your input type.
-
Provide the following information.
Note: If you don't use the default index, you must update the Tenable Macro.
Tenable Web App Scanning
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again (in seconds). The interval amount must be between 3600 and 86400.
Yes
Index The index in which to store Tenable Vulnerability Management data. Yes
Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes
Start Time The date and time to start collecting data. If you leave this field blank, the integration collects all historical data.
Note: Uses the YYYY-MM-DD hh:mm:ss format.
No
Lowest Severity to Store Select the lowest level of severity to store. Can be Info, Low, Medium, High, or Critical. Yes
Historical Fixed Vulnerability Allows the import of vulnerabilities fixed before the current day. No
TOT (ICP)
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again. This supports seconds (between 3600 and 86400) or a cron schedule. Yes
Index The index in which to store Tenable OT Security data. Yes
Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes
TSC Vulnerability
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again. This supports seconds (between 300 and 86400) or a cron schedule.
Note: Restricting the input to collect data during inactive scan periods with a cron schedule is recommended, especially for large Security Center deployments. For smaller deployments, a minimum interval of one hour (3600) can be used.
Yes
Index The index in which to store Tenable Security Center data. Yes
Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes
Start Time The date and time to start collecting data. If you leave this field blank, the integration collects all historical data.
Note: Uses the YYYY-MM-DD hh:mm:ss format.
No
Sync Plugin Details If selected, the related tags in Tenable assets include plugin details. Yes
Historical Fixed Vulnerability Allows the import of vulnerabilities fixed before the current day. No
Query Name A name for Tenable Security Center vulnerability filter.
Note: The interval must be query type Vulnerability Detail List.
No
TSC Mobile
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again (in seconds). Yes
Index The index in which to store Tenable Security Center data. Yes
Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes
Query Name A name for Tenable Security Center vulnerability filter.
Note: The interval must be query type - Vulnerability Detail List.
No
TVM
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again. This supports seconds (between 3600 and 86400) or a cron schedule. Yes
Index The index in which to store Tenable Vulnerability Management data. Yes
Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes
Sync Plugin Details If selected, the related tags in Tenable assets include plugin details. Yes
Historical Fixed Vulnerability Allows the import of vulnerabilities fixed before the current day. No
Host Vulnerability Start Time The date and time to start collecting host data. If you leave this field blank, the integration collects all historical data. (Enter in this format - YYYY-MM-DD hh:mm:ss.) No
Lowest Severity Score The lowest level of severity stored. No
Historical Fixed Vulnerability Allows the import of host vulnerabilities fixed before the current day. No
Tags Limits host vulnerabilities pulled to host assets that have tags selected. No
TVM Audit Logs
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again. This supports seconds (between 3600 and 86400) or a cron schedule. Yes
Index The index in which to store Tenable Vulnerability Management data. Yes
Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes
Start Time The date and time to start collecting data. If you leave this field blank, the integration collects all historical data.
Note: Uses the YYYY-MM-DD hh:mm:ss format.
No
TVM Compliance
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again. This supports seconds (between 3600 and 86400) or a cron schedule. Yes
Index The index in which to store Tenable Vulnerability Management data. Yes
Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes
Start Time The date and time to start collecting data. If you leave this field blank, the integration collects all historical data.
Note: Uses the YYYY-MM-DD hh:mm:ss format.
No
Tenable Attack Surface Management
Input Parameters Description Required Name The unique name for each Tenable data input. Yes
Interval The interval parameter specifies when the input restarts to perform the task again (in seconds). The interval amount must be between 3600 and 86400. Yes
Index The index in which to store Tenable Vulnerability Management data. Global Account Use one of the accounts from the Create an Account page for the matching Tenable product. Yes Start Time The date and time to start collecting data. If you leave this field blank, the integration collects all historical data.
Note: Uses the YYYY-MM-DD hh:mm:ss format.
- Click Add to create the input.
Note: Asset and vulnerabilities in Splunk might differ from individual scan results since the Splunk integration synchronizes cumulative vulnerability and asset data from the Tenable API endpoints.
Next, configure your application.