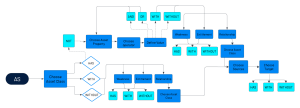
Query Operators, Properties, and Selectors
For more information about Tenable Exposure Management, see the Tenable Exposure Management User Guide.
When you begin a query search, you must first select one of the following items. Expand the + next to each item to view full steps to build that query type.
AS is an alias used to reference a specific object class within the Tenable Exposure Management application. It provides a convenient way to filter and query for assets based on their type. By using the AS alias, you can easily target and manipulate objects of a particular class, such as devices, infrastructure as code, accounts, or people.
![]() Once you select AS, you can then select one or more Asset Class:
Once you select AS, you can then select one or more Asset Class:
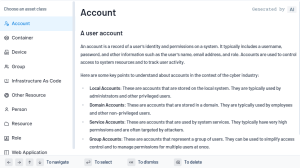
- Account — An account is a record of a user's identity and permissions on a system. It typically includes a username, password, and other information such as the user's name, email address, and role.
- Container — A container is a software package that includes everything needed to run an application: code, runtime, system tools, system libraries and settings.
- Device — A device is typically defined as a physical or virtual component that can connect to a network, communicate with other devices, and perform specific functions or tasks.
- Group — A group is a collection of assets that share common characteristics.
- Infrastructure as Code — Infrastructure as code (IaC) is a method of managing and provisioning IT infrastructure using code. IaC treats infrastructure as a set of resources that can be managed and provisioned using code.
- Other Resource — Other resources are assets that do not fall into any of the other categories. They can include things like software applications, databases, and websites.
- Resource — A resource is a type of asset that can be managed by Tenable Exposure Management. Resources can be physical or virtual, and they can be located on-premises or in the cloud.
- Role — A role is a type of asset that represents a specific function or purpose. For example, a web server role might represent a server that is used to host websites. Roles often include Entitlements.
- Web Application — A web application is a software application that is accessed via a web browser. It is typically hosted on a web server and can be accessed by anyone with an internet connection.
![]() Then, choose one of the following:
Then, choose one of the following:
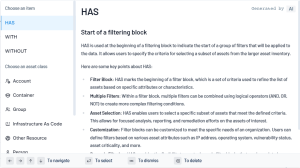
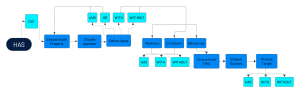
HAS is used at the beginning of a filtering block to indicate the start of a group of filters that will be applied to the data. It allows users to specify the criteria for selecting a subset from the larger inventory.
![]() Once you select HAS, you can optionally select NOT to exclude any items that include your search criteria.
Once you select HAS, you can optionally select NOT to exclude any items that include your search criteria.
![]() Then, select an asset property to use in your query. See Key Asset Properties for a list of examples.
Then, select an asset property to use in your query. See Key Asset Properties for a list of examples.
![]() Once you have selected an asset property, you can further refine your query using the Available Operators.
Once you have selected an asset property, you can further refine your query using the Available Operators.
![]() Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
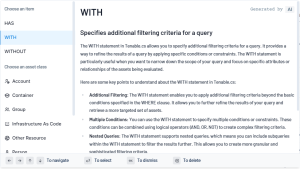
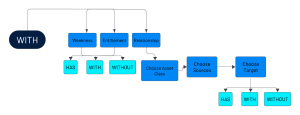
The WITH statement allows you to specify additional filtering criteria for a query. It provides a way to refine the results of a query by applying specific conditions or constraints. The WITH statement is particularly useful when you want to narrow down the scope of your query and focus on specific attributes or relationships of the assets being evaluated.
![]() Once you select WITH, you can then select one of the following cross-references:
Once you select WITH, you can then select one of the following cross-references:
An entitlement is a right or permission granted to an individual or entity to access a specific resource, system, or information. It defines the level of access and the specific actions that the individual or entity is authorized to perform. Entitlements are often used in the context of cybersecurity to control and manage access to sensitive data, systems, or applications.
![]() After you select Entitlement, you can select one of the following options:
After you select Entitlement, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options.
If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options. Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step.
Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A finding is a single instance of a vulnerability (weakness or misconfiguration) appearing on an asset, identified uniquely by plugin ID, port, and protocol.
![]() After you select Finding, you can select one of the following options:
After you select Finding, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples. Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step.
Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A relationship is a connection or association between two or more assets in a network. It represents the logical or physical connectivity and dependencies between assets, providing a comprehensive view of the network infrastructure and its components.
![]() After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
![]() Then, you must select a target. See Relationship Sources and Targets for a list of options.
Then, you must select a target. See Relationship Sources and Targets for a list of options.
![]() After you select a target, you can select one of the following options:
After you select a target, you can select one of the following options:
-
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
![]() Optionally, repeat the steps to include a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query.
Optionally, repeat the steps to include a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query.
![]() Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
Software is a type of keyword used in inventory application to identify and classify assets based on their software components. It allows users to gain insights into the software installed on their devices, including operating systems, applications, and other software packages.
![]() After you select Software, you can select one of the following options:
After you select Software, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain.
If you select HAS, you can select the property that you want the search results to contain.  Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step.
Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A weakness is a flaw or fault in the system that makes it susceptible to attack, compromise, or unauthorized access. Weaknesses can exist in various forms, such as software vulnerabilities, misconfigurations, or human errors. They can be caused by design flaws, implementation mistakes, or inadequate security measures.
![]() After you select Weakness, you can select one of the following options:
After you select Weakness, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples. Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step.
Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
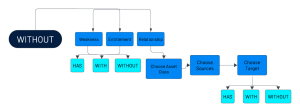
The Boolean operator WITHOUT is used to exclude specific results from a search query. It allows you to refine your search criteria and narrow down the results by eliminating items that meet certain conditions. By using WITHOUT, you can focus on the results that are most relevant to your search and exclude those that are not.
![]() Once you select WITHOUT, you can then select one of the following cross-references:
Once you select WITHOUT, you can then select one of the following cross-references:
An entitlement is a right or permission granted to an individual or entity to access a specific resource, system, or information. It defines the level of access and the specific actions that the individual or entity is authorized to perform. Entitlements are often used in the context of cybersecurity to control and manage access to sensitive data, systems, or applications.
![]() After you select Entitlement, you can select one of the following options:
After you select Entitlement, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options.
If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options. Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step.
Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A finding is a single instance of a vulnerability (weakness or misconfiguration) appearing on an asset, identified uniquely by plugin ID, port, and protocol.
![]() After you select Finding, you can select one of the following options:
After you select Finding, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples. Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step.
Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A relationship is a connection or association between two or more assets in a network. It represents the logical or physical connectivity and dependencies between assets, providing a comprehensive view of the network infrastructure and its components.
![]() After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
![]() Then, you must select a target. See Relationship Sources and Targets for a list of options.
Then, you must select a target. See Relationship Sources and Targets for a list of options.
![]() After you select a target, you can select one of the following options:
After you select a target, you can select one of the following options:
-
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
![]() Optionally, repeat the steps to exclude a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query.
Optionally, repeat the steps to exclude a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query.
![]() Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
Software is a type of keyword used in inventory application to identify and classify assets based on their software components. It allows users to gain insights into the software installed on their devices, including operating systems, applications, and other software packages.
![]() After you select Software, you can select one of the following options:
After you select Software, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain.
If you select HAS, you can select the property that you want the search results to contain.  Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step.
Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A weakness is a flaw or fault in the system that makes it susceptible to attack, compromise, or unauthorized access. Weaknesses can exist in various forms, such as software vulnerabilities, misconfigurations, or human errors. They can be caused by design flaws, implementation mistakes, or inadequate security measures.
![]() After you select Weakness, you can select one of the following options:
After you select Weakness, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples. Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step.
Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
HAS is used at the beginning of a filtering block to indicate the start of a group of filters that will be applied to the data. It allows users to specify the criteria for selecting a subset of assets from the larger asset inventory.
![]() Once you select HAS, you can optionally select NOT to exclude any items that include your search criteria.
Once you select HAS, you can optionally select NOT to exclude any items that include your search criteria.
![]() Then, select an asset property to use in your query. See Key Asset Properties for a list of examples.
Then, select an asset property to use in your query. See Key Asset Properties for a list of examples.
![]() Once you have selected an asset property, you can further refine your query using the Available Operators.
Once you have selected an asset property, you can further refine your query using the Available Operators.
![]() Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
 WITH
WITH
The WITH statement allows you to specify additional filtering criteria for a query. It provides a way to refine the results of a query by applying specific conditions or constraints. The WITH statement is particularly useful when you want to narrow down the scope of your query and focus on specific attributes or relationships of the assets being evaluated.
 Once you select WITH, you can then select one of the following cross-references:
Once you select WITH, you can then select one of the following cross-references: Entitlement
Entitlement
An entitlement is a right or permission granted to an individual or entity to access a specific resource, system, or information. It defines the level of access and the specific actions that the individual or entity is authorized to perform. Entitlements are often used in the context of cybersecurity to control and manage access to sensitive data, systems, or applications.
 After you select Entitlement, you can select one of the following options:
After you select Entitlement, you can select one of the following options:-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options.
If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options. Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step.
Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Finding
Finding
A finding is a single instance of a vulnerability (weakness or misconfiguration) appearing on an asset, identified uniquely by plugin ID, port, and protocol.
 After you select Finding, you can select one of the following options:
After you select Finding, you can select one of the following options:-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples. Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step.
Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Relationship
Relationship
A relationship is a connection or association between two or more assets in a network. It represents the logical or physical connectivity and dependencies between assets, providing a comprehensive view of the network infrastructure and its components.
 After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options. Then, you must select a target. See Relationship Sources and Targets for a list of options.
Then, you must select a target. See Relationship Sources and Targets for a list of options. After you select a target, you can select one of the following options:
After you select a target, you can select one of the following options:-
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Optionally, repeat the steps to include a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query.
Optionally, repeat the steps to include a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query. Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
 Software
Software
Software is a type of keyword used in inventory application to identify and classify assets based on their software components. It allows users to gain insights into the software installed on their devices, including operating systems, applications, and other software packages.
 After you select Software, you can select one of the following options:
After you select Software, you can select one of the following options:-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain.
If you select HAS, you can select the property that you want the search results to contain.  Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step.
Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Weakness
Weakness
A weakness is a flaw or fault in the system that makes it susceptible to attack, compromise, or unauthorized access. Weaknesses can exist in various forms, such as software vulnerabilities, misconfigurations, or human errors. They can be caused by design flaws, implementation mistakes, or inadequate security measures.
 After you select Weakness, you can select one of the following options:
After you select Weakness, you can select one of the following options:-
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Then, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples.
Then, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples. Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step.
Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
 WITHOUT
WITHOUT
The Boolean operator WITHOUT is used to exclude specific results from a search query. It allows you to refine your search criteria and narrow down the results by eliminating items that meet certain conditions. By using WITHOUT, you can focus on the results that are most relevant to your search and exclude those that are not.
 Once you select WITHOUT, you can then select one of the following cross-references:
Once you select WITHOUT, you can then select one of the following cross-references: Entitlement
Entitlement
An entitlement is a right or permission granted to an individual or entity to access a specific resource, system, or information. It defines the level of access and the specific actions that the individual or entity is authorized to perform. Entitlements are often used in the context of cybersecurity to control and manage access to sensitive data, systems, or applications.
 After you select Entitlement, you can select one of the following options:
After you select Entitlement, you can select one of the following options:-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options.
If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options. Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step.
Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Finding
Finding
A finding is a single instance of a vulnerability (weakness or misconfiguration) appearing on an asset, identified uniquely by plugin ID, port, and protocol.
 After you select Finding, you can select one of the following options:
After you select Finding, you can select one of the following options:-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples. Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step.
Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Relationship
Relationship
A relationship is a connection or association between two or more assets in a network. It represents the logical or physical connectivity and dependencies between assets, providing a comprehensive view of the network infrastructure and its components.
 After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options. Then, you must select a target. See Relationship Sources and Targets for a list of options.
Then, you must select a target. See Relationship Sources and Targets for a list of options. After you select a target, you can select one of the following options:
After you select a target, you can select one of the following options:-
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Optionally, repeat the steps to exclude a Finding, Weakness, Entitlement, Relationship, or Software applicatino to the target portion of the query.
Optionally, repeat the steps to exclude a Finding, Weakness, Entitlement, Relationship, or Software applicatino to the target portion of the query. Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
 Software
Software
Software is a type of keyword used in inventory application to identify and classify assets based on their software components. It allows users to gain insights into the software installed on their devices, including operating systems, applications, and other software packages.
 After you select Software, you can select one of the following options:
After you select Software, you can select one of the following options:-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain.
If you select HAS, you can select the property that you want the search results to contain.  Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step.
Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
 Weakness
Weakness
A weakness is a flaw or fault in the system that makes it susceptible to attack, compromise, or unauthorized access. Weaknesses can exist in various forms, such as software vulnerabilities, misconfigurations, or human errors. They can be caused by design flaws, implementation mistakes, or inadequate security measures.
 After you select Weakness, you can select one of the following options:
After you select Weakness, you can select one of the following options:-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples. Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step.
Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
-
The WITH statement allows you to specify additional filtering criteria for a query. It provides a way to refine the results of a query by applying specific conditions or constraints. The WITH statement is particularly useful when you want to narrow down the scope of your query and focus on specific attributes or relationships of the assets being evaluated.
![]() Once you select WITH, you can then select one of the following cross-references:
Once you select WITH, you can then select one of the following cross-references:
An entitlement is a right or permission granted to an individual or entity to access a specific resource, system, or information. It defines the level of access and the specific actions that the individual or entity is authorized to perform. Entitlements are often used in the context of cybersecurity to control and manage access to sensitive data, systems, or applications.
![]() After you select Entitlement, you can select one of the following options:
After you select Entitlement, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options.
If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options. Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step.
Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A finding is a single instance of a vulnerability (weakness or misconfiguration) appearing on an asset, identified uniquely by plugin ID, port, and protocol.
![]() After you select Finding, you can select one of the following options:
After you select Finding, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples. Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step.
Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A relationship is a connection or association between two or more assets in a network. It represents the logical or physical connectivity and dependencies between assets, providing a comprehensive view of the network infrastructure and its components.
![]() After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
![]() Then, you must select a target. See Relationship Sources and Targets for a list of options.
Then, you must select a target. See Relationship Sources and Targets for a list of options.
![]() After you select a target, you can select one of the following options:
After you select a target, you can select one of the following options:
-
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
![]() Optionally, repeat the steps to include a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query.
Optionally, repeat the steps to include a Finding, Weakness, Entitlement, Relationship, or Software application to the target portion of the query.
![]() Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
Software is a type of keyword used in inventory application to identify and classify assets based on their software components. It allows users to gain insights into the software installed on their devices, including operating systems, applications, and other software packages.
![]() After you select Software, you can select one of the following options:
After you select Software, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain.
If you select HAS, you can select the property that you want the search results to contain.  Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step.
Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A weakness is a flaw or fault in the system that makes it susceptible to attack, compromise, or unauthorized access. Weaknesses can exist in various forms, such as software vulnerabilities, misconfigurations, or human errors. They can be caused by design flaws, implementation mistakes, or inadequate security measures.
![]() After you select Weakness, you can select one of the following options:
After you select Weakness, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples. Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step.
Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
The Boolean operator WITHOUT is used to exclude specific results from a search query. It allows you to refine your search criteria and narrow down the results by eliminating items that meet certain conditions. By using WITHOUT, you can focus on the results that are most relevant to your search and exclude those that are not.
![]() Once you select WITHOUT, you can then select one of the following cross-references:
Once you select WITHOUT, you can then select one of the following cross-references:
An entitlement is a right or permission granted to an individual or entity to access a specific resource, system, or information. It defines the level of access and the specific actions that the individual or entity is authorized to perform. Entitlements are often used in the context of cybersecurity to control and manage access to sensitive data, systems, or applications.
![]() After you select Entitlement, you can select one of the following options:
After you select Entitlement, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options.
If you select HAS, you can select the property that you want the search results to contain. See Key Entitlement Properties for a list of options. Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step.
Once you have selected an entitlement property, you can further refine your query using the Available Operators.Note: Some operators depend on the entitlement property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A finding is a single instance of a vulnerability (weakness or misconfiguration) appearing on an asset, identified uniquely by plugin ID, port, and protocol.
![]() After you select Finding, you can select one of the following options:
After you select Finding, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Finding Properties for a list of examples. Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step.
Once you have selected a finding property, you can further refine your query using the Available Operators.Note: Some operators depend on the finding property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A relationship is a connection or association between two or more assets in a network. It represents the logical or physical connectivity and dependencies between assets, providing a comprehensive view of the network infrastructure and its components.
![]() After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
After you select Relationship, you must select one or more sources. See Relationship Sources and Targets for a list of options.
![]() Then, you must select a target. See Relationship Sources and Targets for a list of options.
Then, you must select a target. See Relationship Sources and Targets for a list of options.
![]() After you select a target, you can select one of the following options:
After you select a target, you can select one of the following options:
-
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
![]() Optionally, repeat the steps to exclude aFinding, Weakness, Entitlement, Query Operators, Properties, and Selectors, or Software application to the target portion of the query.
Optionally, repeat the steps to exclude aFinding, Weakness, Entitlement, Query Operators, Properties, and Selectors, or Software application to the target portion of the query.
![]() Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected the operators for any properties you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
Software is a type of keyword used in inventory application to identify and classify assets based on their software components. It allows users to gain insights into the software installed on their devices, including operating systems, applications, and other software packages.
![]() After you select Software, you can select one of the following options:
After you select Software, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain.
If you select HAS, you can select the property that you want the search results to contain.  Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step.
Once you have selected a software property, you can further refine your query using the Available Operators.Note: Some operators depend on the software property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
A weakness is a flaw or fault in the system that makes it susceptible to attack, compromise, or unauthorized access. Weaknesses can exist in various forms, such as software vulnerabilities, misconfigurations, or human errors. They can be caused by design flaws, implementation mistakes, or inadequate security measures.
![]() After you select Weakness, you can select one of the following options:
After you select Weakness, you can select one of the following options:
-
 HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
HAS — Select HAS to select a subset of criteria to include in your query. Optionally, after selecting HAS, you can select NOT to exclude the criteria from the query.
 If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples.
If you select HAS, you can select the property that you want the search results to contain. See Key Weakness Properties for a list of examples. Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step.
Once you have selected a weakness property, you can further refine your query using the Available Operators.Note: Some operators depend on the weakness property that you selected in the previous step. Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:
Once you have selected your operator for the property you included, you can begin your search based on the defined criteria, or you can select more items to add to the query:-
AND — Combine the criteria defined in the query.
-
OR — Return query results that match either of the criteria defined in the query.
-
WITH — Select additional criteria to include with the query.
-
WITHOUT — Select additional criteria to exclude from the query.
-
-
WITH — Select WITH to specify additional filtering criteria to include within the query.
-
WITHOUT — Select WITHOUT to specify additional filtering criteria to exclude from the query.
Example Query Creation
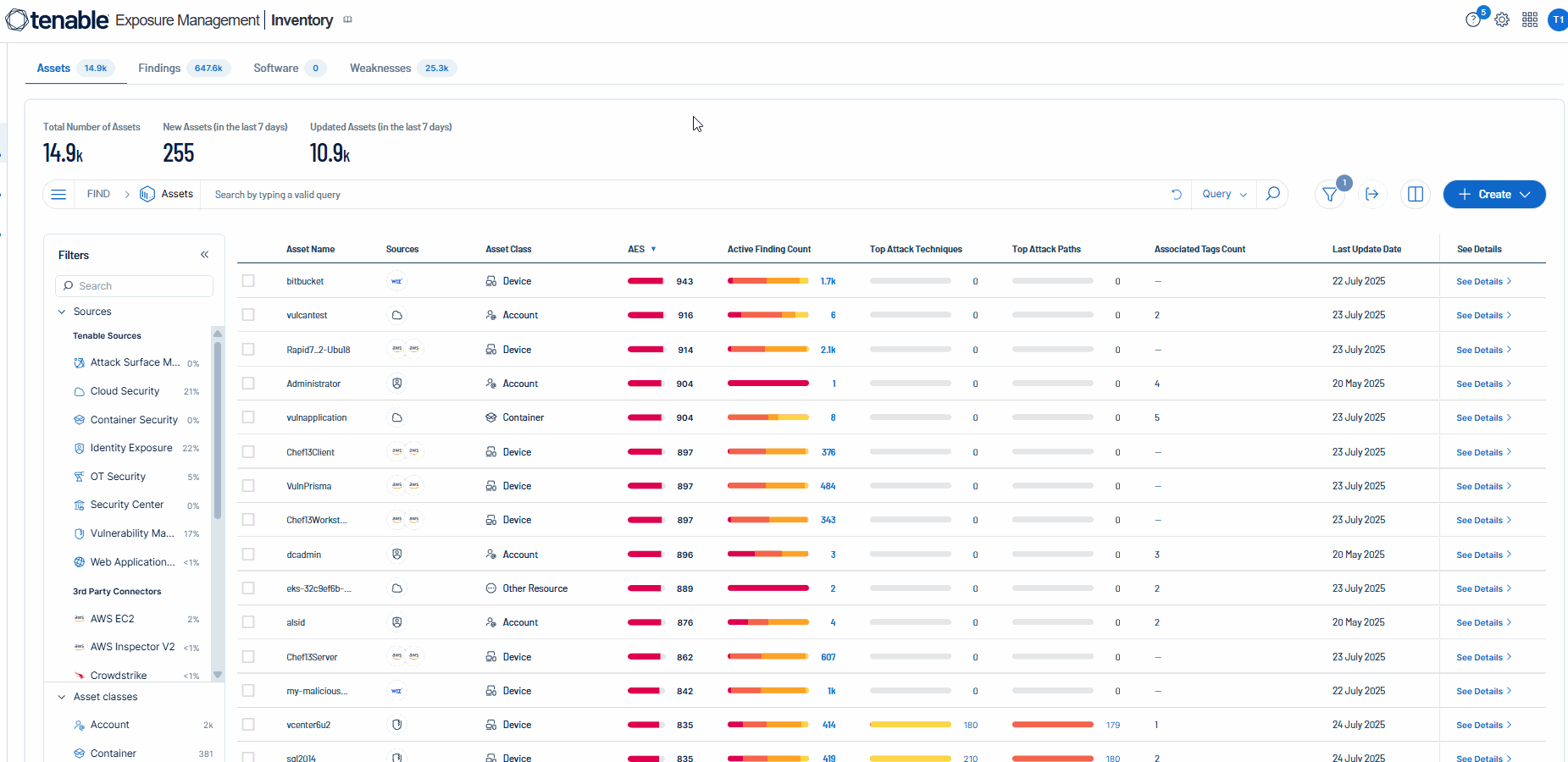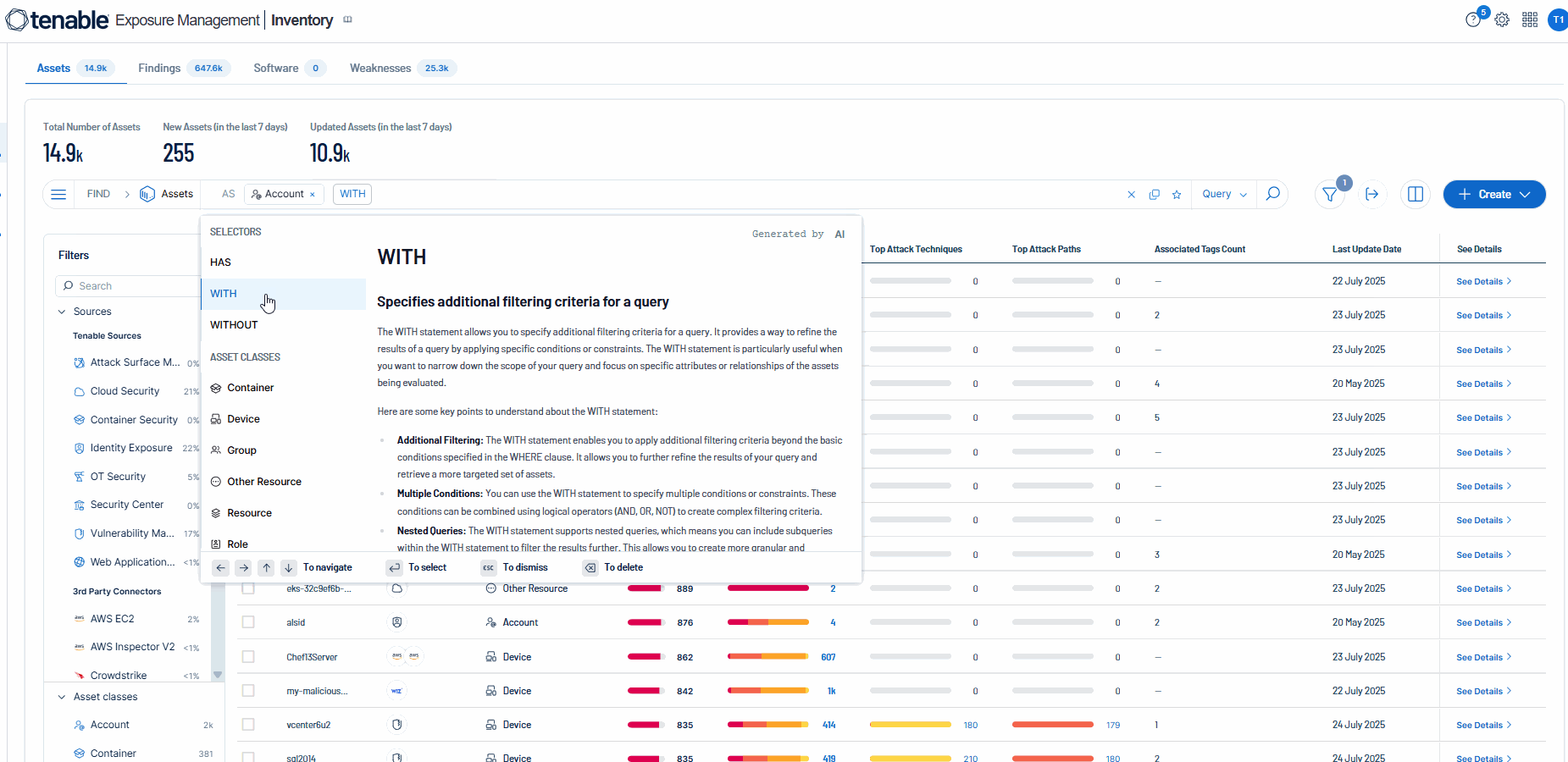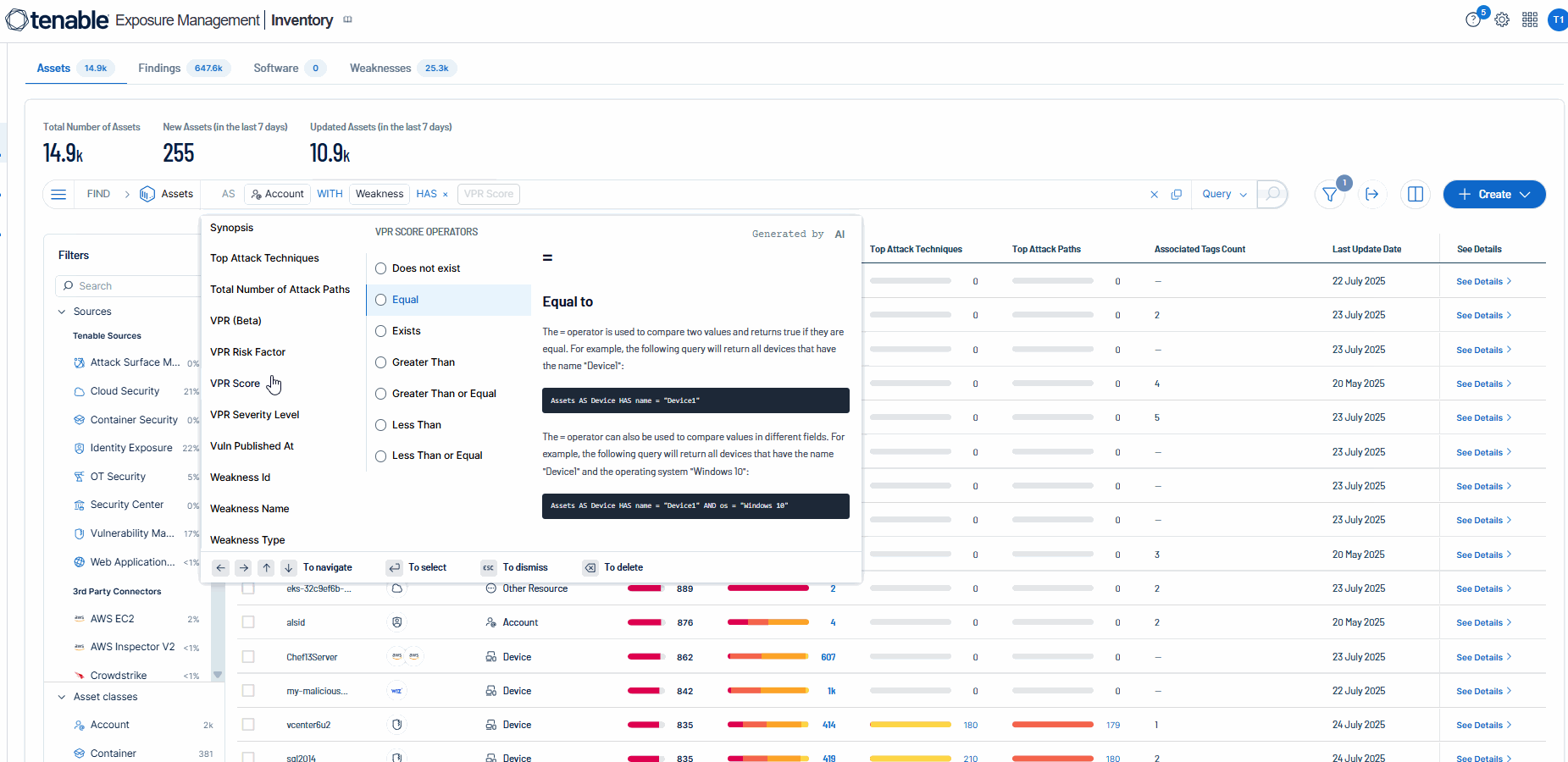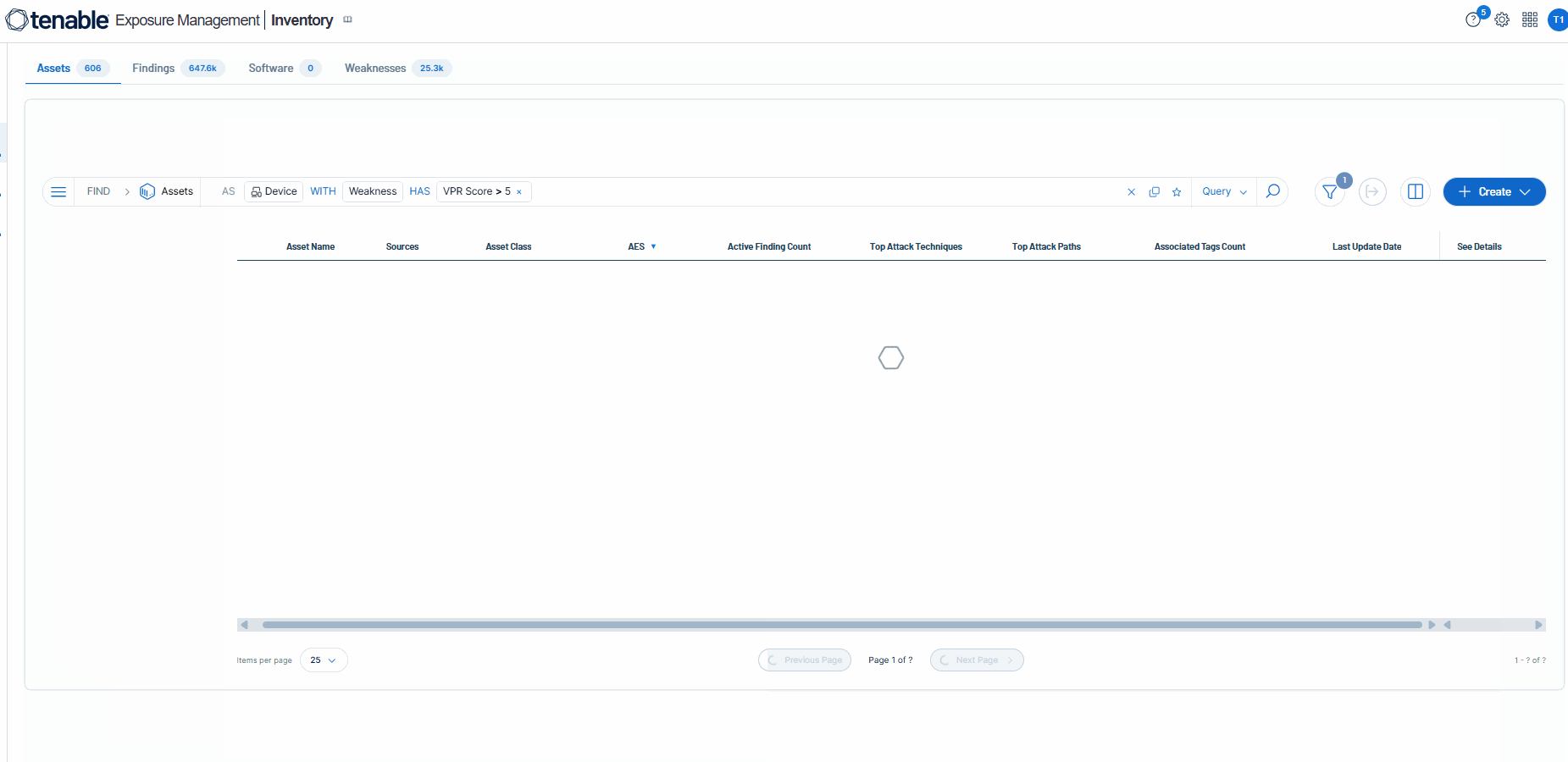
| Asset Property | Definition |
|---|---|
|
Asset ID |
An asset ID is a unique identifier that is assigned to each asset in a cyber asset management system. This identifier can be used to track the asset, its associated vulnerabilities, and its security posture. |
|
Asset Class |
An asset class is a group of assets that share common characteristics. Asset classes can be used to group assets together for reporting, analysis, and other purposes. |
|
Group Name |
The group name is a string that identifies the group to which an asset belongs. Groups can be used to organize assets and to apply policies to groups of assets. |
|
Provider Names |
The provider name is the name of the cloud provider that owns the asset. |
|
Provider Identifier |
A provider identifier is a unique identifier for an asset that is assigned by the asset's provider. This identifier can be used to track the asset and its associated data. |
|
Created Date |
The created date is the date and time an asset was first created in the system. |
|
Last Observed At |
The last observed at property indicates the date and time an asset was last seen by a Tenable scanner. |
|
Cloud Name |
The cloud name is a property that identifies the cloud provider for an asset. It is typically a string value that is unique to each cloud provider. |
|
Host Name |
The host name is a unique name that is assigned to a device. It is used to identify the device on the network and to access its resources. |
| Finding Property | Definition |
|---|---|
|
Finding Name |
The specific identifier or label given to a security finding or alert generated by a vulnerability scan or other security monitoring tools. It helps to distinguish and categorize different types of security events based on their characteristics and potential impact. |
|
Severity |
Indicates the level of potential risk posed by a security vulnerability. It helps prioritize remediation efforts by highlighting the most critical vulnerabilities that require immediate attention. |
|
State |
The current status of the finding, for example Active or Fixed. This status helps you track the progress of remediation efforts and provides insights into the overall security posture. |
|
First Seen (observed) |
The date on which Tenable Exposure Management first identified and added an asset to its inventory. |
|
Last Seen |
The most recent date and time when a specific asset or resource was detected as active or online within your monitored environment. |
|
VPR Score |
The Vulnerability Priority Rating (VPR) of the finding. |
|
Product Code |
A unique identifier assigned to a specific vulnerability or security issue within a software product or system. These codes help in tracking, categorizing, and managing vulnerabilities effectively. |
| Detection Family | A classification or grouping of security findings based on the underlying techniques or methods used to identify potential vulnerabilities or security risks. |
| Weakness Property | Definition |
|---|---|
|
Weakness ID |
A weakness is a vulnerability that can be exploited by an attacker to compromise a system or asset. The Weakness Id is a unique identifier that is assigned to each weakness. |
|
Provider Code |
A provider code is a unique identifier that is used to identify the provider of a weakness. |
|
Product Code |
A product code is a unique identifier for a product. It is typically used to track the product throughout its lifecycle, from development to manufacturing to distribution to sale. |
|
Detection Code |
A detection code is a string of characters that can be used to identify a specific weakness. |
|
Weakness Type |
A weakness type is a category of weakness. It is used to group weaknesses together based on their common characteristics. |
|
Last Updated |
The last updated date and time for a weakness is the date and time when the weakness was last modified or updated. |
|
Severity |
The severity of a weakness is a measure of the potential impact that an exploit of the weakness could have on an organization. |
| Entitlement Property | Definition |
|---|---|
|
Name |
The name of an object is a unique identifier that is used to refer to the object. It can be a string, number, or other type of data. |
|
Type |
The type of an entitlement is a string that indicates the type of resource that the entitlement grants access to. |
|
Provider Type |
The provider type is the type of entity that provides the asset. For example, a cloud provider, an on-premises provider, or a SaaS provider. |
|
Target Asset ID |
The Target Asset ID is a unique identifier for an asset. It is used to track and manage entitlements, and to ensure that the correct permissions are granted to the correct users. |
Relationship Sources and Targets
| Source / Target | Definition |
|---|---|
|
Account |
An account is a record of a user's identity and permissions on a system. It typically includes a username, password, and other information such as the user's name, email address, and role. |
|
Container |
A container is a software package that includes everything needed to run an application: code, runtime, system tools, system libraries and settings. |
| Device | A device is typically defined as a physical or virtual component that can connect to a network, communicate with other devices, and perform specific functions or tasks. |
| Group | A group is a collection of assets that share common characteristics. |
| Infrastructure as Code | Infrastructure as code (IaC) is a method of managing and provisioning IT infrastructure using code. IaC treats infrastructure as a set of resources that can be managed and provisioned using code. |
| Other Resource | Other resources are assets that do not fall into any of the other categories. They can include things like software applications, databases, and websites. |
| Resource | A resource is a type of asset that can be managed by Tenable Inventory. Resources can be physical or virtual, and they can be located on-premises or in the cloud. |
| Role | A role is a type of asset that represents a specific function or purpose. For example, a web server role might represent a server that is used to host websites. |
| Web Application | A web application is a software application that is accessed via a web browser. It is typically hosted on a web server and can be accessed by anyone with an internet connection. |
| Operator | Definition |
|---|---|
| Exists | The Exists operator is used to check if a field is not null. It can be used in queries to filter out results that do not have a value for a particular field. |
| Does not Exist | The Does not Exist operator is used to check if a field is null. This can be used to filter out objects that do not have a value for a particular field. |
| Contains | The Contains operator is used to check if a string contains a specific value. |
| Not Contains | The Not Contains operator is used to exclude a value from a list. It is typically used in queries to filter out specific objects or values. |
|
After/Greater Than |
The After/Greater Than operator is used to compare two values and return true if the first value is greater than the second value. |
| Before/Less Than | The Before/Less Than operator is used to compare two values and return true if the first value is less than the second value. |
| Between | The Between operator is used to compare a value to a range of values. |
| Equal To | The Equal To operator is used to compare two values and returns true if they are equal. |
| Not Equal | The Not Equal operator is used to compare two values and return true if they are not equal. |
| Older Than | The Older Than operator is used to compare date property to a given period from now. |
| Newer Than | The Newer Than operator is used to compare a date property to a given period from now. |
| Within Last | The Within Last operator is used to specify a time range. |