Tenable Attack Surface Management 2025 Release Notes
Tip: You can subscribe to receive alerts for Tenable documentation updates.
These release notes are listed in reverse chronological order.
December 9, 2025
Configurable Asset Max Age
Tenable Attack Surface Management now allows Business Admin users to control how long unresolved DNS records remain in an inventory. A new Asset max age setting is available in the inventory settings, enabling you to choose how quickly assets that fail DNS resolution are removed.
For more information, see Tenable Attack Surface Management User Guide > Edit Inventory Details > Step 5.
| Bug Fix |
|---|
|
Tenable Attack Surface Management now prevents the Suggestions page from refreshing continuously. |
| Tenable Attack Surface Management now saves the webhook URL correctly when configuring Slack alert settings. |
| Tenable Attack Surface Management now displays the Add Hostname and Add IP Address dialogs with the correct layout in the new UI. |
November 27, 2025
| Bug Fix |
|---|
|
Tenable Attack Surface Management resolves an issue that prevented switching from Tenable Attack Surface Management to Tenable Exposure Management using the Workspace launcher. |
November 20, 2025
Add Top-Level Domain (TLD) as Source
Tenable Attack Surface Management now supports adding Top-Level Domains as a source in the new user interface. You can add one TLD at a time.
For more information, see Add a TLD (Top-Level Domain).
| Improvement |
|---|
|
The new Tenable Attack Surface Management now includes an increased limit for the number of values you can use in the is one of and related filter types. This enhancement allows you to build broader and more flexible filters when working with larger datasets. |
November 3, 2025
Custom Columns in the New UI
Tenable Attack Surface Management now supports Custom Columns in the Explore and Asset Inventory pages on the new user interface.
Note:Managing and filtering custom columns remains available only in the legacy UI.
For more information, see Inventory Columns.
Extended Asset Attribution Timeline
The asset attribution timeline now indicates when an asset has been automatically removed due to failed DNS resolution.
| Bug Fix |
|---|
|
Tenable Attack Surface Management now correctly handles RFC 1918 IP addresses when applying IP range filters. |
October 2, 2025
Bulk Subscription Alerts
Tenable Attack Surface Management now supports managing alerts for multiple subscriptions at once. Previously, alerts could only be modified one subscription at a time, which made it difficult to manage large numbers of subscriptions. With this update, you can select multiple subscriptions and apply alert changes in bulk, similar to existing bulk operations for deleting or copying subscriptions.
Important! Bulk modifications overwrite any existing alert settings for the selected subscriptions.
For more information, see Create Alerts for Subscriptions.
| Improvement |
|---|
|
Tenable Attack Surface Management dashboard view now displays charts for columns even when no data is present, reducing confusion when reviewing asset data. |
|
Tenable Attack Surface Management nightly suggestions job no longer recommends domain names that have already been added to your inventory. |
|
Tenable Attack Surface Management now includes internal performance improvements for running Automation Rules. |
| Bug Fix |
|---|
|
Tenable Attack Surface Management now displays the correct asset count for newly added sources in the sources tree. |
| Tenable Attack Surface Management now displays the export dialog when you click export links in Subscription alert emails. |
| Tenable Attack Surface Management now creates reports without errors. |
September 10, 2025
| Improvement |
|---|
| Tenable Attack Surface Management now runs Automation Rules more efficiently with improved performance. |
| Bug Fix |
|---|
|
Tenable Attack Surface Management now shows only “Asset moved or copied” without the “by: null” field when an asset is moved or copied from another inventory. |
| The Ports tab in the asset overlay now displays an empty list when no open ports are detected for an asset. |
July 14, 2025
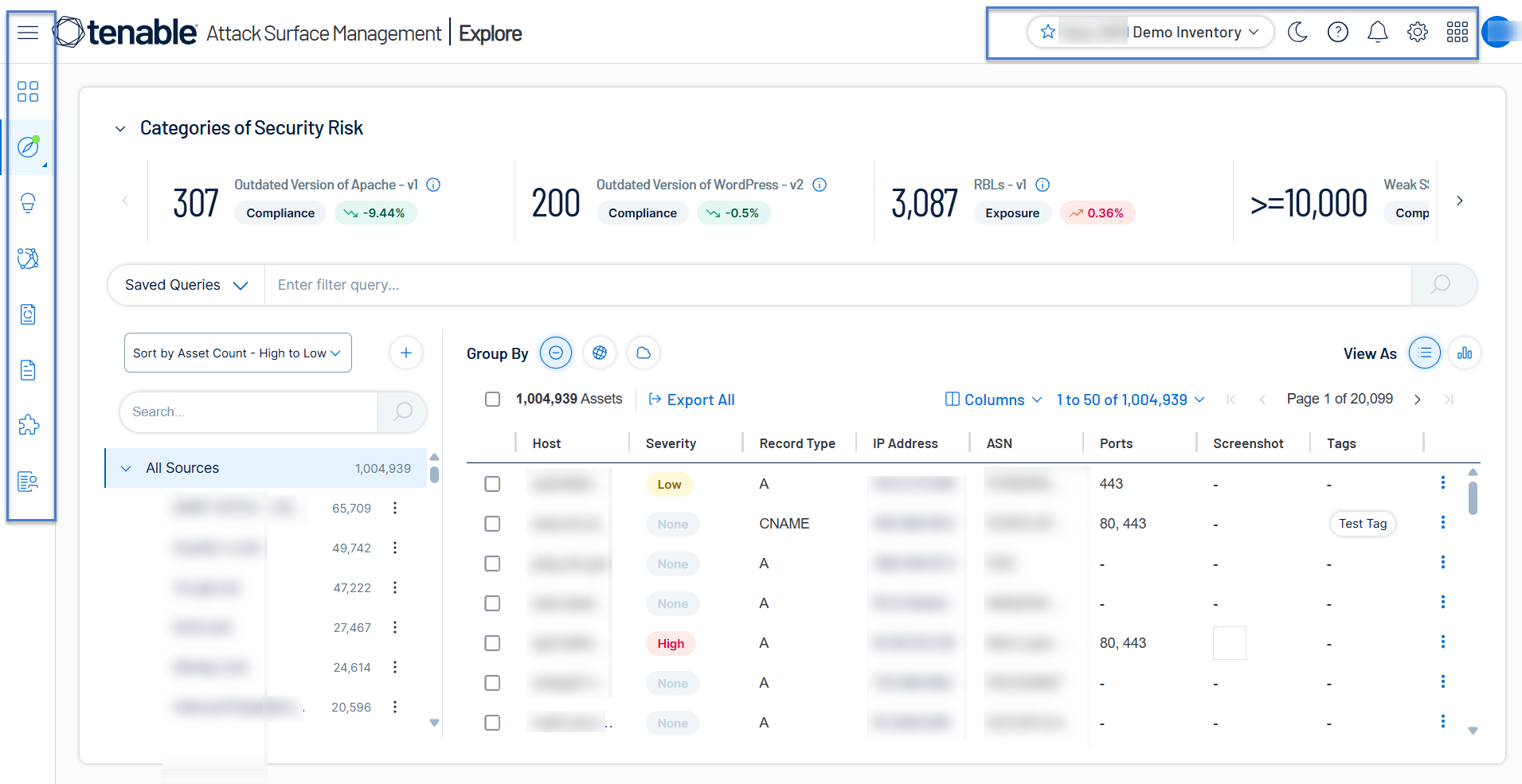
Explore Dashboard
Tenable Attack Surface Management now includes enhanced workflows for discovering and managing externally exposed assets. Key improvements include the new Explore page, which features the following sections:
-
Categories of Security Risk: Filter inventories based on the specific security risk categories that impact them.
-
Saved Queries: Create and save custom queries to filter assets to view specific security risks.
-
Group by: Organize and view assets by hostnames or IP addresses.
-
Manage sources: Add, remove, move sources within your inventory.
-
Export: Export assets in these formats: CSV, XLSX, or JSON.
-
Columns: Customize the display of asset table columns.
-
Manage assets: Add, modify, or remove assets from your managed inventory.
-
Assets view: View assets in either a table format or a chart format.
For more information, see Explore.
Improved User Interface
Tenable Attack Surface Management's improved user interface now match the other Tenable products' interface. Key changes include:
-
New header featuring links to Inventory, Resource Center, Notifications, Settings, and Workspace.
-
Side navigation panel with icons for faster navigation within Tenable Attack Surface Management.
-
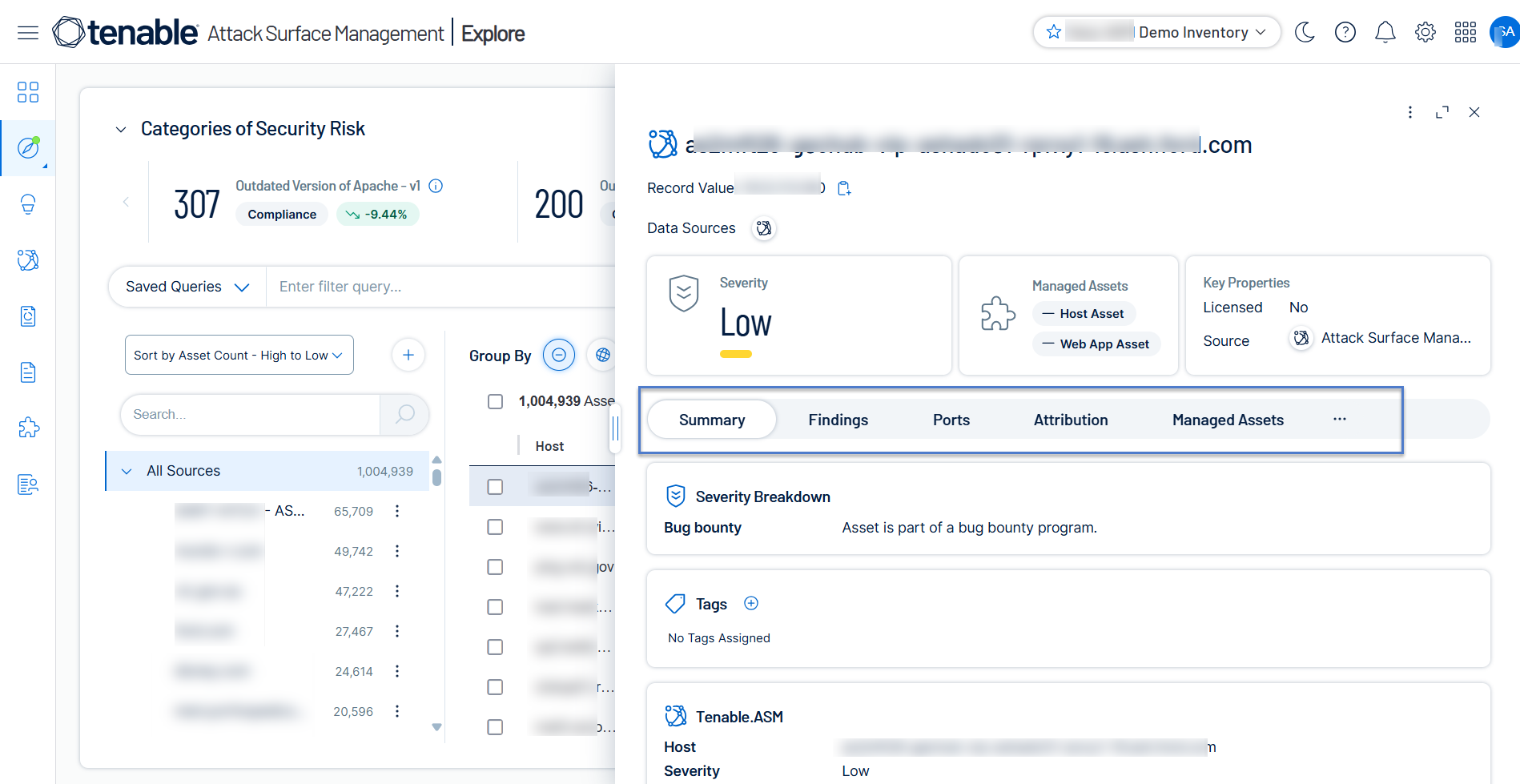
Slider panels on the Inventory page provide detailed asset details. In this panel, Tenable Attack Surface Management organizes the collected metadata into contextual tabs such as Summary, Findings, Ports, Attribution, Managed Assets, HTML.
-
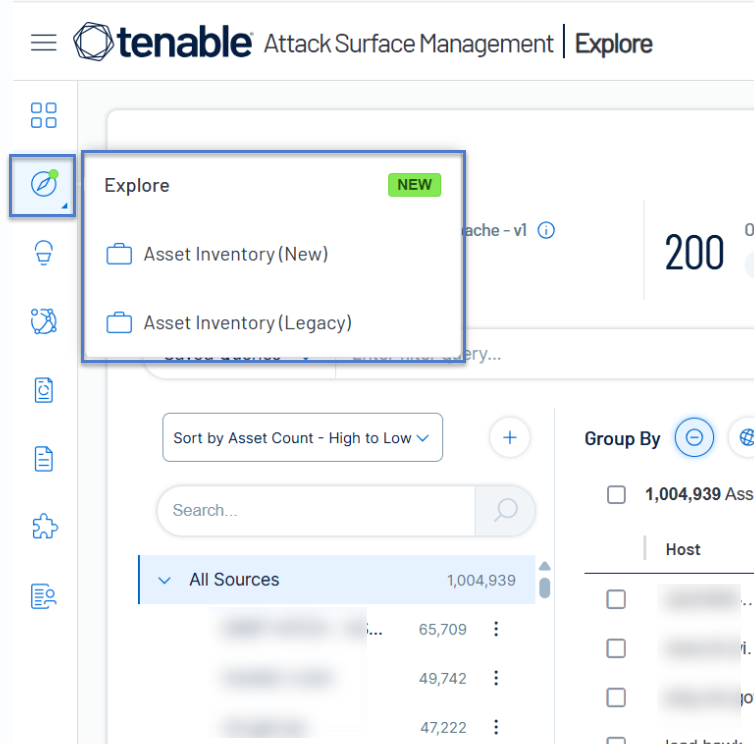
Link to access legacy inventory page.
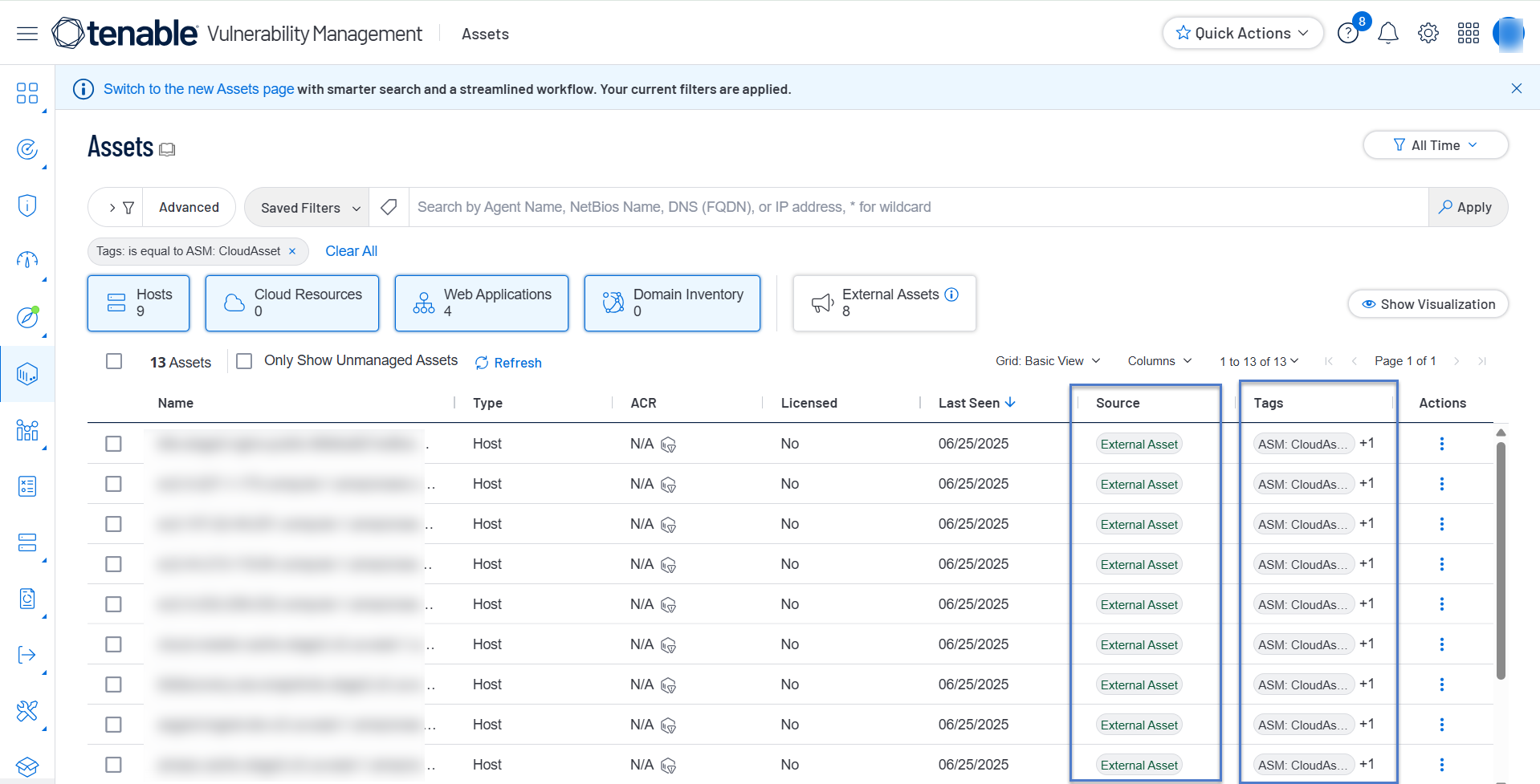
View Cloud Assets in Tenable Vulnerability Management
You can now view all cloud assets detected by cloud connectors in Tenable Attack Surface Management on the Assets page in Tenable Vulnerability Management. In addition to the External Asset identifier in the Source column, all cloud assets show the ASM CloudAsset tag and their corresponding inventory name in the Tags column of the Assets page. For more information, see Cloud Assets.
View Host and Web Application Assets
Tenable Attack Surface Management now provides additional context about Host and Web Application assets on the Asset Details page, including:
-
Asset merge criteria details.
-
Visibility into assets already detected by Tenable Vulnerability Management.
-
Security risk information based on ACR and AES scores.
For more information, see View Asset Details for Host and Web Application Assets.
June 26, 2025
| Bug Fix |
|---|
|
The default filters in the Administrator interface's Users page now include the Cloud Connector Manager role. |
June 2, 2025
Cloud Connector Manager Role
Tenable Attack Surface Management now includes a Cloud Connector Manager role for integrations. This role allows users to manage, add, modify, and delete cloud connectors in addition to the Active User permissions. The Cloud Connector Manager role is mapped to Scan Operator in Tenable Vulnerability Management.
For more information, see Tenable-provided Roles and Privileges and Tenable Attack Surface Management Roles.
May 28, 2025
Integrate with Google Cloud Platform
You can now integrate Tenable Attack Surface Management with Google Cloud Platform (GCP) to add assets from your GCP accounts. For more information, see Integrate with Google Cloud Platform.
Integrate with AWS, Azure, and GCP using Keyless Authentication
Tenable Attack Surface Management now supports integration with AWS, Azure, and Google Cloud Platform accounts using keyless authentication. For more information, see the following:
May 8, 2025
Tenable is thrilled to announce some significant enhancements to your cloud product Workspace! We've redesigned the workspace to provide you with better visibility and access to Tenable products:
-
Improved Product Overview — You can now easily see both the products you've purchased and a range of other products available for exploration.
-
Detailed Product Information — Access More Details to demo the product, giving you in-depth knowledge about each product.
-
Product Utilization — We’ve added a utilization feature that shows the percentage of how much you’re using the subscribed products. It allows you to quickly direct you to the License Information page.
-
Trial Status Visibility — If you are currently evaluating a product or have done so within the past year, you will now see the status of the trial (In Trial or Trial Expired) directly in your workspace.
These changes are designed to help you get the most out of your Tenable solutions and discover new ways to enhance your security posture. To learn more, access the Workspace page via any Tenable cloud application.
April 9, 2025
| Bug Fix |
|---|
| The loading state now appears correctly on the Activity Logs page. |
| For IP ranges, Tenable Attack Surface Management now supports both the hyphen (-) and the longer versions of a dash: the en dash (–) and the em dash (—). |
March 6, 2025
| Bug Fix |
|---|
|
Tenable Attack Surface Management now allows you to export assets that match a valid filter. |
| Tenable Attack Surface Management now validates filter expressions on both the front-end and back-end. Additionally, it shows an error message whenever a user error occurs. |
February 18, 2025
| Bug Fix |
|---|
| Tenable Attack Surface Management now ensures that elements in the Suggestion blocklist items list can be readded after deletion. |
February 4, 2025
| Improvement |
|---|
| The CVEs on the asset details page now links to Common Vulnerabilities and Exposures (CVEs). |
| Tenable Attack Surface Management now shows improved CVE data according to descriptions and scoring. |
| Tenable Attack Surface Management now features enhanced Common Platform Enumeration (CPE) resolutions for CVEs, ensuring more consistent and accurate CVE findings using Tenable sources. |
| Bug Fix |
|---|
| The Reports page in Tenable Attack Surface Management displays correctly. |
| Clicking the close button in the Tenable MSSP Portal impersonation overlay within Tenable Attack Surface Management now redirects to Tenable Vulnerability Management. |
January 14, 2025
| Bug Fix |
|---|
| Tenable Attack Surface Management now ensures that the Suggestion Rules details text correctly displays UTF-8 (non-ASCII) characters. |
| The Workspace launcher now functions correctly when accessing Tenable Identity Exposure from Tenable Attack Surface Management. |
| Links present in Subscription Alerts no longer show access-related errors if a user has proper access and permissions to the inventory. |