CIS Control 3: Continuous Vulnerability Management
The focus of this control is to have an established vulnerability management program that is configured to conduct regular, comprehensive, credentialed scans across the organization. The most effective vulnerability scanning programs not only identify vulnerabilities, but also evaluate and report on a number of other critical concerns such as:
- Security configurations of systems
- Misconfigurations
- Unauthorized changes
- Patch levels of systems
Vulnerability assessment tools should follow industry recognized vulnerability, configuration, and platform classification schemes such as:
-
Vulnerability Priority Rating (VPR)
-
Common Vulnerabilities and Exposures (CVE)
-
Common Configuration Enumeration (CCE)
-
Open Vulnerability and Assessment Language (OVAL)
-
Common Platform Enumeration (CPE)
-
Common Vulnerability Scoring System (CVSS)
-
Extensible Configuration Checklist Description Format (XCCDF)
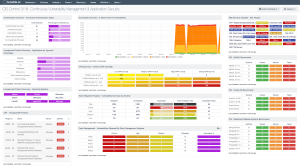
In addition, identified concerns should be reconciled/mitigated in a timely manner, using follow up vulnerability scanning as validation. For CIS Control 3, Tenable products allow organizations to effectively address, report, and follow up on these industry standards via active, credentialed scanning, across all three Implementation Groups. A number of dashboards, reports, and Assurance Report Cards (ARC) are readily available to provide organizations with real time continuous vulnerability monitoring and reporting, such as the CIS Control 3/18 Continuous Vulnerability Management and Application Security Dashboard.
For more information about the CIS Control 3 dashboard, see CIS Control 3/18: Continuous Vulnerability Management & Application Security.
The CIS states this Control is critical:
“Cyber defenders must operate in a constant stream of new information: software updates, patches, security advisories, threat bulletins, etc. Understanding and managing vulnerabilities has become a continuous activity, requiring significant time, attention, and resources. Attackers have access to the same information and can take advantage of gaps between the appearance of new knowledge and remediation. For example, when researchers report new vulnerabilities, a race starts among all parties, including: attackers (to “weaponize,” deploy an attack, exploit), vendors (to develop, deploy patches or signatures and updates), and defenders (to assess risk, regression-test patches, install).
Organizations that do not scan for vulnerabilities and proactively address discovered flaws face a significant likelihood of having their computer systems compromised. Defenders face particular challenges in scaling remediation across an entire enterprise, and prioritizing actions with conflicting priorities, and sometimes uncertain side effects.”
The journey of implementing the CIS Controls continues with continuous vulnerability management. Credentialed Active Scanning and monitoring with products such as Nessus, Tenable Vulnerability Management, and Tenable Security Center allows organizations to continuously acquire, assess, and take action on new vulnerability information in order to identify and remediate risks. Thereby, the organizations can reduce the window of opportunity for attackers. Tenable Security Center provides an on-premise solution for organizations to better understand vulnerability management. By facilitating the interactions with patch management solutions, which is required by sub control 3.4 & 3.5, Tenable Security Center allows all 3 IG levels to better understand risk and mitigate threats.
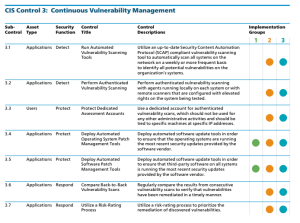
The CAS provides guidance on how to assess the organization's progress in this journey. This guide illustrates how the CISO can effectively measure cybersecurity success. Shown below are the CIS Control 3 IG levels and requirements.
As shown above, the IG1 organization is required to implement Sub-Controls 3.4 - Deploy Automated Operating Systems Patch Management Tools, and 3.5 - Deploy Automated Software Patch Management Tools. Some useful methods to collect data to meet these requirements include:
Credentialed Active Scanning, specifically:
-
Identify operating systems/software/applications that are installed on hosts
-
Identify patching/version information on detected operating systems/software/applications